Red Cross Antivirus (Removal Instructions)
Red Cross Antivirus Removal Guide
What is Red Cross Antivirus?
Red Cross Antivirus –
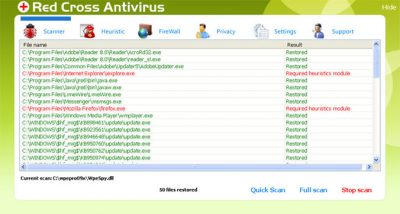
Red Cross Antivirus is a rogue antivirus program that reports false system security threats to make you think that your computer is infected with severe malware. Recently, this rogue program is being distributed through the use of the fake Microsoft Security Essentials Alert Trojan.
Red Cross Antivirus is a typical rogue program, just like Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, or AntiSpy Safeguard. Once installed, it will pretend to scan your computer, and after that, it will list numerous infections that supposedly can delete your important files or steal your sensitive information.
Don't worry, the scan results are false. You can safely ignore them. This also applies to fake warnings and pop-ups shown by the fake security tool. Some of those fake alerts will state that your computer is under attack from a remote computer and that the RedCrossAntivirus has blocked a remote login attempt to your computer. Please don't purchase this bogus program. Instead, remove it either manually or automatically.
| name | Red Cross Antivirus |
|---|---|
| Type | Fake security software, rogue antispyware |
| Purpose | Deceive users into thinking their computers are infected with malware to sell its paid version |
| Risks | Money loss, real malware infections |
| Distribution | Fake online virus scanners, software bundles, deceptive ads |
| Elimination | Scan the computer with proper security software to remove this parasite |
| System fix | With PC tune-up tools like the FortectIntego app, you can restore any damages caused by cyber infections |
While Red Cross Antivirus is running, it will also block legitimate programs and security-related websites, including 2-spyware.com. It will probably block Task Manager and Registry Editor too. Also, note that you shouldn't use system restore to remove this virus.
Of course, it might be an option, but usually, rogue programs infect system restore points as well. If you find that your computer is infected with Red Cross Antivirus malware, please uninstall it from the system upon detection. If you have already purchased the rogue program, then please contact your credit card company and dispute the charges.
We strongly recommend using an automatic removal tool to remove the rogue program and any related malware from the computer. Proper, time-proven security software will protect your computer from such threats and hazardous malware. Once the rogue antispyware removal is completed, run system diagnostics with appropriate software to repair system-related issues.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Red Cross Antivirus. Follow these steps
Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Red Cross Antivirus registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting rogue antispyware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.



