RedLine Malware (virus) - Free Instructions
RedLine Malware Removal Guide
What is RedLine Malware?
RedLine malware can steal your passwords, banking information, and cryptocurrency wallets

RedLine malware was first observed in 2020. It is an information stealer mainly targeting Windows users. It steals victims' passwords, autofill data, cryptocurrency wallets, browser information, FTP connections,[1] and OS information such as system hardware, time zone, IP address, geolocation, OS version, and default language.
Cybercriminals can use this information to access various accounts, like social media, email, and banking. They can deceive people into transferring money and making fraudulent purchases. The malicious program can also infect victims' machines with other malware like ransomware, cryptocurrency miners, trojans, etc.
It shows up in users' systems as AddInProcess.exe which was flagged by 50 security vendors and 3 sandboxes as malicious. It also acts as a Trojan because it does not show any particular symptoms and performs tasks in the background. Most people may not even know that they have been infected by this malware.
Usually, people will notice that something is wrong if they suffer from financial losses or identity theft. If malware causes the installations of other malicious programs that can also be the point where users notice the infection. Otherwise, a lot of time can pass before users find out about the threat.
| NAME | RedLine |
| TYPE | Trojan virus; malware |
| SYMPTOMS | No particular symptoms are noticeable to the victims as the malware acts in the background |
| DISTRIBUTION | Email attachments, torrent websites, deceptive advertisements, social engineering |
| DANGERS | Users' passwords, banking information, and other sensitive data can be stolen, which could lead to monetary losses, identity theft, and the victims' computers being added to a botnet |
| ELIMINATION | Professional security tools should eliminate the threat completely with all the related files |
| FURTHER STEPS | Use a maintenance tool like FortectIntego to fix any remaining damage and optimize your machine |
Distribution techniques
Currently, the RedLine malware is advertised on various cybercriminal forums as a MaaS (Malware-as-a-Service)[2] model. The malicious program can be purchased through the Redline telegram official channel. The threat actors offer a monthly, weekly, and lifetime subscription for the prices of 100$, 150$, and 800$ respectively. They accept payment in Bitcoin, Ethereum, XMR, LTC, and USDT.
Those who buy the subscription use various methods to spread RedLine malware. Healthcare was one of several industry sectors affected by this threat in the last few months. Crooks take advantage of the global pandemic by using it in their social engineering scams. A spam email was found to distribute RedLine Stealer by disguising it as the Folding@home application:
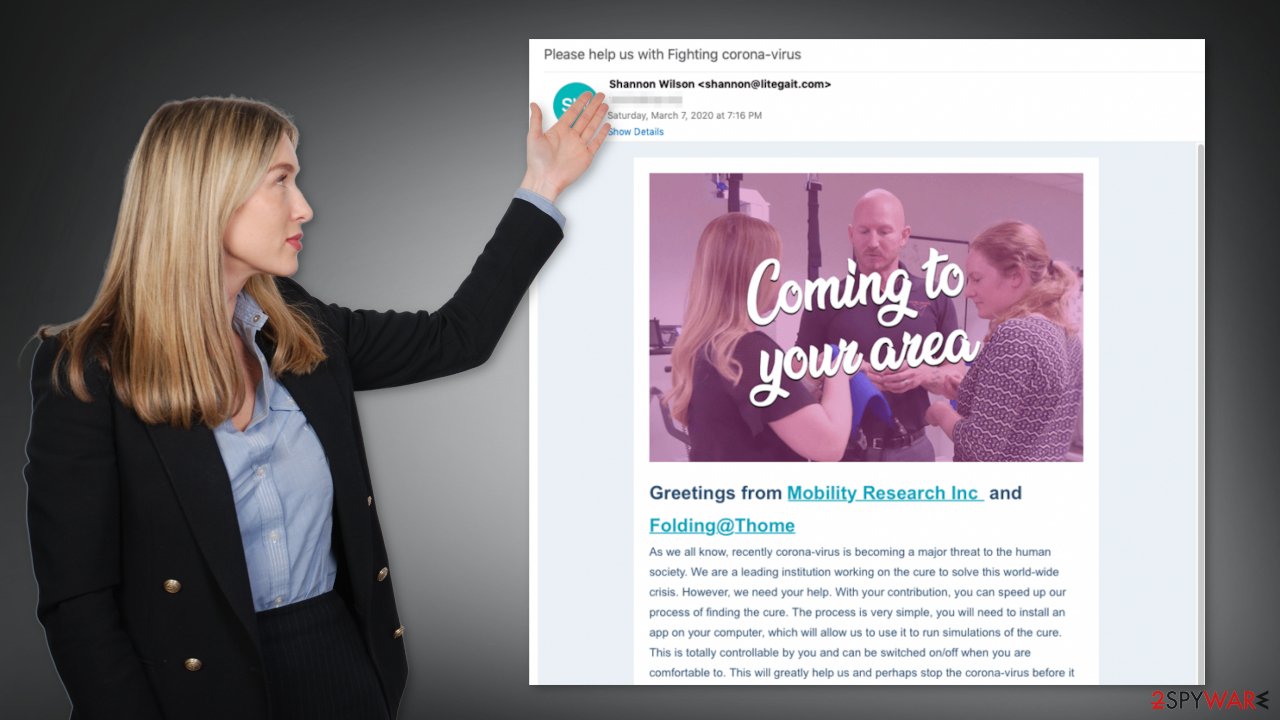
The email comes from Shannon Wilson who claims to be working for Mobility Research Inc. It is a company providing rehabilitation solutions for physically disabled patients. The email urges recipients to help the company find a cure for the coronavirus by enrolling in the Folding.@Thome program.
Mobility Research does in fact have a project known as Folding@home, which lets participants donate computing power for disease research and computational drug design by downloading a particular app. As you can see the social engineering tactics the cybercriminals use are very clever. Even if victims did go online and tried to confirm the information in the email, they would not suspect a thing.
Researchers also found a scam website mydigitalcoin.info that was used to promote the malicious program:
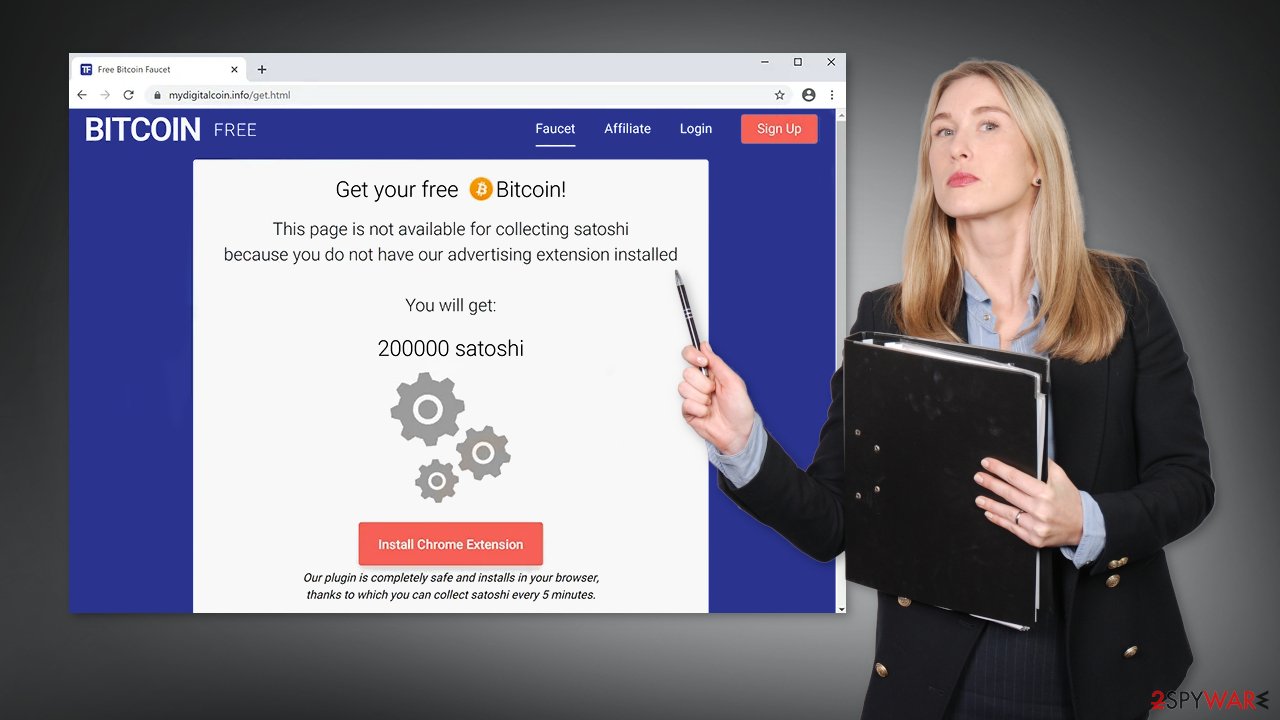
Here users are tempted with an attractive offer:
Get your free Bitcoin!
This page is not available for collecting satoshi because you do not have our advertising extension installedYou will get:
200000 satoshiInstall Chrome Extension
Our plugin is completely safe and installs in your browser, thanks to which you can collect satoshi every 5 minutes.
Supposedly, all that users have to do is just install a simple Chrome extension and they will receive free Bitcoin for doing nothing. With the craze of cryptocurrencies rising, threat actors use it to their advantage. There is no doubt that if you would click the Install button on this website you would open the doors for the virus to enter your system.
That is why you should be very careful while surfing the web, especially with email. If you do not know the person who sent the email, do not open any attachments or click on any links. Sometimes crooks do very good research and disguise the email as it was sent from one of your contacts. So if the email came from someone on your friend list but you were not expecting it, it would be beneficial to double-check with them through a different platform.
The removal process
It can be very difficult to detect and remove RedLine on time because it usually operates without showing any visible indications of its presence. It may take weeks, or even months for the victim to notice the effects of the virus activity. If you want to prevent such threats from entering your machine in the future, you should use professional security tools.
A PC without an antivirus is like a house without a door. Anti-malware tools can remove the intruders before they can do any changes to your system. SpyHunter 5Combo Cleaner and Malwarebytes are great tools that you can use for the full elimination of RedLine. We do not recommend performing the removal manually as you can leave some traces behind which could result in the renewal of the infection.
Some Trojan-based programs can block your security software and prevent you from accessing the settings for malware removal. If malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.
![Update & Security Update & Security]()
- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
![Press F5 to enable Safe Mode with Networking Press F5 to enable Safe Mode with Networking]()
Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions and perform a full system scan to eradicate malware and all its malicious components.
Repair the damaged operating system
Performance, stability, and usability issues, to the point where a full Windows reinstall is required, are nothing unusual after a malware infection. These types of intruders can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files,[4] etc. Once a system file is damaged, antivirus software cannot fix it.
Manual troubleshooting of such damage is also very complicated and can take a long time. This is why FortectIntego was developed. It can fix a lot of the damage caused by an infection like this. Blue Screen errors,[5] freezes, registry errors, damaged DLLs, etc., can make your computer completely unusable. By using this useful maintenance tool, you could prevent yourself from having to reinstall Windows completely.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
If you experience setting changes in your browsers, like the homepage, new tab address, redirects, or push notifications, you can look for instructions on how to deal with those issues below this article. There is a big chance that the malware automatically installed other threats that could cause unwanted symptoms in your browsers. Guides are available for Google Chrome, Mozilla Firefox, MS Edge, and Internet Explorer.
Getting rid of RedLine Malware. Follow these steps
Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Swati Tawde. What is FTP?. Educba. Software Development Tutorials.
- ^ Samuel Gush. What Is Malware-as-a-Service?. Makeuseof. Home Security.
- ^ What is Bitbucket?. Confluence. Evaluator Resources Support.
- ^ What is a DLL. Microsoft. Documentation.
- ^ Blue screen of death. Wikipedia. The free encyclopedia.























