Rivd ransomware (virus) - Decryption Steps Included
Rivd virus Removal Guide
What is Rivd ransomware?
Rivd ransomware is a virus that demands payment of $980 but offers a discount of 50% to trick people
Rivd virus is the file-locker aiming to scare victims into transferring the money to their account by lying about the decryption tool. In most cases, these payments do not result in any data recovery because criminals behind the threat do not care about users' belongings at all. This ransomware belongs to a Djvu ransomware family that is known to release new versions without particularly changing anything about the threat. The last ones include .maql, .rugj, and .zaps. This variant encrypts files and appends the unique .rivd extension on their filenames, for example renaming 1.jpg into 1.jpg.rivd. Documents, audio, video files, images all can get encrypted right after the infiltration.
It is always best to avoid malicious tricks. They might claim they have decryption tools available in order for you to pay a ransom, but this is not true. There can be offers for test decryption and the discount of the payment for the first victims. The choice of contacting these criminals is not the best since attackers can send you another piece of malware instead of the decryption tool.
These days, avoiding malware infections is crucial since hackers are increasing the amount of payment they ask for in return for file recovery. Only certain decryption programs would allow victims to regain access back onto their devices once again without having lost everything irreparably broken beyond repair already. Criminals behind the Rivd ransomware claim to have such a tool and promises to provide it for the victim once the Bitcoin payment is transferred. However, there is no reason to trust the criminals at all.
| Name | Rivd virus |
|---|---|
| Type | Ransomware, cryptovirus, file-locker |
| Family | Djvu/STOP ransomware |
| File marker | .rivd appendix comes after the original file name and type indication |
| Amount demanded | $490/$980 |
| Contact emails | manager@mailtemp.ch, supporthelp@airmail.cc |
| Ransom note | _readme.txt |
| Distribution | Torrent websites, malicious file attachments from emails, pirating platforms, and game cheats or software cracks |
| Removal | The best way to fight malware like this is proper system cleaning. Without AV tools you cannot clear the threat and can risk getting files permanently damaged |
| Recovery | The best way to repair the system – FortectIntego because this tool can solve issues regarding virus damage. Then you can move to encrypted file recovery |
The _readme.txt file, which is the ransom note for this ransomware virus, provides contact and payment information to its victims. The price of a decryption tool depends on how fast they will contact the cybercriminals behind this campaign. In full, it is $980, but the first 72 hours have the $490 sum. Note that users can get their data damaged soon after too! Even when you took less than 72 hours following an attack in contacting them with these criminals.
The Rivd virus is a form of ransomware that aims to get money from victims, so it starts with locking your files once the system is infected. The process can be done quickly, so the victim is not noticing the infiltration. The process of encryption uses powerful algorithms that help to alter the original code of the data. This is why the filenames are changed, and the file becomes unopenable.
The ransom note of the Rivd ransomware gets placed in various folders that have encrypted files and on the desktop for the victim to find right away. The message from criminals reads the following:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with
strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-pk3SGFlmek
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
manager@mailtemp.chReserve e-mail address to contact us:
supporthelp@airmail.ccYour personal ID:
The best way to deal with the ransomware would be to remove the infection, clear any traces of the threat and recover the system performance to a proper state. It can be done with anti-malware programs like SpyHunter 5Combo Cleaner or Malwarebytes and the full system scan during which the threat pieces get detected.[1]
Encryption scrambles files right away
Once locked by this type of malware, documents become useless and cannot be opened without decryption services. The ransom note informs victims that files cannot be accessed without the right decryption tool and unique key. However, the real decryption tool might not even exist. It takes researchers a lot of time to make a tool like this that could restore files after a ransomware attack.
The previous versions were for a while decryptable. Right now, only a few victims can get their files restored with the previously developed tool. Unfortunately, flaws in coding got quickly fixed, and the encryption algorithms were altered to be more powerful and less likely breakable. Victim Id forming methods significantly affect the decryption possibility because the C&C server connection[2] ensures that there are no identical decryption keys and people need to pay to get the proper decryptor.
If your computer got infected with one of the Djvu variants, you should try using Emsisoft decryptor for Djvu/STOP. It is important to mention that this tool will not work for everyone – it only works if data was locked with an offline ID due to malware failing to communicate with its remote servers.
Even if your case meets this condition, somebody from the victims has to pay criminals, retrieve an offline key, and then share it with security researchers at Emsisoft. As a result, you might not be able to restore the encrypted files immediately. Thus, if the decryptor says your data was locked with an offline ID but cannot be recovered currently, you should try later. You also need to upload a set of files – one encrypted and a healthy one to the company's servers before you proceed.
- Download the app from the official Emsisoft website.
- After pressing Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe should show up – click it.
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
![Rivd ransomware Rivd ransomware]()
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Rivd ransomware Rivd ransomware]()
- Press Decrypt.
The distribution and other actions of the Rivd virus
Distribution of malware and holding property for ransom are criminal acts in many countries, so it means that you shouldn't ignore them. We encourage all victims who have been victimized by these crimes to report their experience with law enforcement as it helps us determine how best to investigate such activity.
Such agencies and malware researchers can sometimes find the people responsible and stop their activities. Also, once the criminal is caught, decryption keys can be released to the public and help restore those files that get encoded by the threat malicious actors release. However, in most cases, such scenarios are not common, so you need to learn how to avoid infections like Rivd ransomware instead.
The infection mainly spreads using malicious files with the code for ransomware payload. These pieces can be attached to the email or be directly added to the message via a link. This particular ransomware family is mainly relying on pirating services and torrent sites. Experts[3] note that the payload of ransomware can come with the game cheat package or cracks for a particular software. Users online report that this particular version was spread using various pirated programs like Photoshop or Adobe applications.
Most often, gamers catch the ransomware while trying to get something via pirating platforms. The Rivd virus infiltration happens quickly and unnoticed. Sometimes criminals mask the behavior of the malware and the encryption process in particular with the fake Windows Update pop-up message.
Unfortunately, once a computer is infected with malware, its system is changed to operate differently, too. For example, an infection can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is.
Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstallation is required. Therefore, we highly recommend using a one-of-a-kind, patented technology – FortectIntego. Not only can it fix Rivd virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
By employing the proper tool, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Alternatives for decryption and ways to restore encoded files
Do not trust anyone who claims they can decrypt your files for a fee or even for free. These people are either scam artists or criminals who will overcharge you and lie about it to get what they want from victims – money. The main issue with such file-lockers is the fact that cryptocurrency extortionists are the ones behind it.
In some cases, it is possible to recover access to those files without paying a ransom: when victims have copies of their data, and when there is a decryption tool on the Internet. It is not recommended that you pay cybercriminals for such tools because they might never provide them. It is also important to make sure all data on infected computers have been completely erased before recovering files. Otherwise, the Rivd virus could encrypt more files or infect other devices in addition to your main system.
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether Rivd ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
If you have difficulty when trying to remove Rivd ransomware it might be because the virus managed to alter some settings, preferences, or even disable features or programs on the machine directly. It is common for ransomware to stop security tools, anti-malware programs, and other system features that are related to security or file repair.
If that happens, you might need to enter the Safe Mode with Networking before you can launch the SpyHunter 5Combo Cleaner or Malwarebytes on the computer. The guide below shows how to do so. Also, these instructions can show how to manage the infection, stop additional processes and malware activities yourself.
We understand that the Rivd file virus encrypted files are the main concern for you, but you need to avoid quick decisions since the system can get damaged if the ransomware runs another round of encryption on the same set of files. Be cautious about virus leftovers and run FortectIntego to ensure that the system is clear.
Getting rid of Rivd virus. Follow these steps
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Restore Windows "hosts" file to its original state
Some ransomware might modify Windows hosts file in order to prevent users from accessing certain websites online. For example, Djvu ransomware variants add dozens of entries containing URLs of security-related websites, such as 2-spyware.com. Each of the entries means that users will not be able to access the listed web addresses and will receive an error instead.
Here's an example of “hosts” file entries that were injected by ransomware:
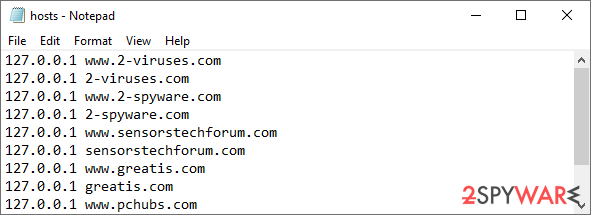
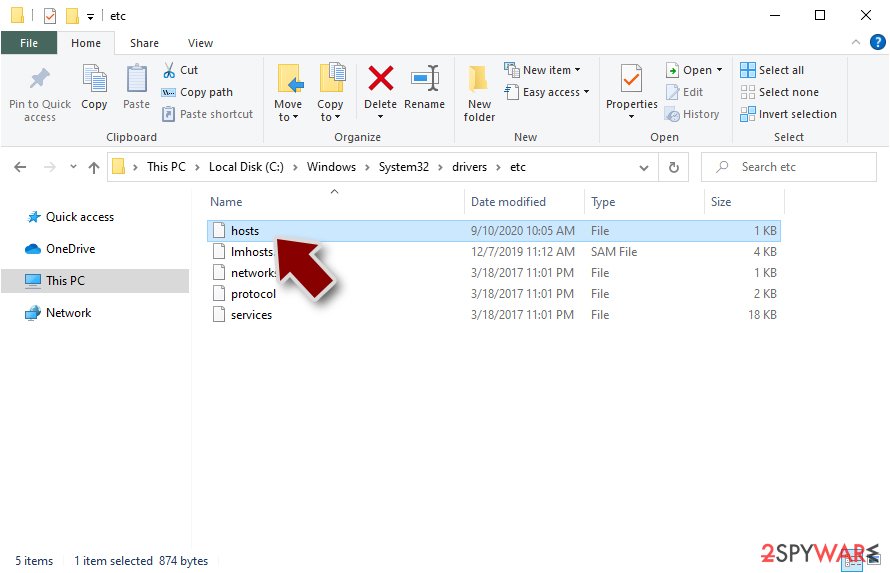
In order to restore your ability to access all websites without restrictions, you should either delete the file (Windows will automatically recreate it) or remove all the malware-created entries. If you have never touched the “hosts” file before, you should simply delete it by marking it and pressing Shift + Del on your keyboard. For that, navigate to the following location:
C:\\Windows\\System32\\drivers\\etc\\
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Rivd and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Rate f the virus detection. VirusTotal. Online malware scanner.
- ^ David Bisson. Threat Actor Using C&C Server to Host Ransomware. Securityintelligence. IT and cyber security news.
- ^ Virusai. Virusai. Spyware removal guides.