Skynet ransomware (Free Guide) - Recovery Instructions Included
Skynet virus Removal Guide
What is Skynet ransomware?
Skynet ransomware is a malicious program that locks all data on a Windows system and then demands a ransom for its return
Skynet is a ransomware-type virus that infiltrates users' PCs and encrypts all their personal files using a sophisticated encryption algorithm,[1] making all photos, videos, documents, databases, and other important data unusable (each of the files is appended with a random string of characters, for example, “.br84”). This damage can be really significant to those who had no backups and held important files on their systems.
Cybercriminals behind the attack are well aware of this, that's why they ask users to pay a ransom so that the data can be recovered. They are not willing to giveaway the decryptor for free and are asking to pay in bitcoin, promising a discount of 50% if contacted within 24 hours of the infection.
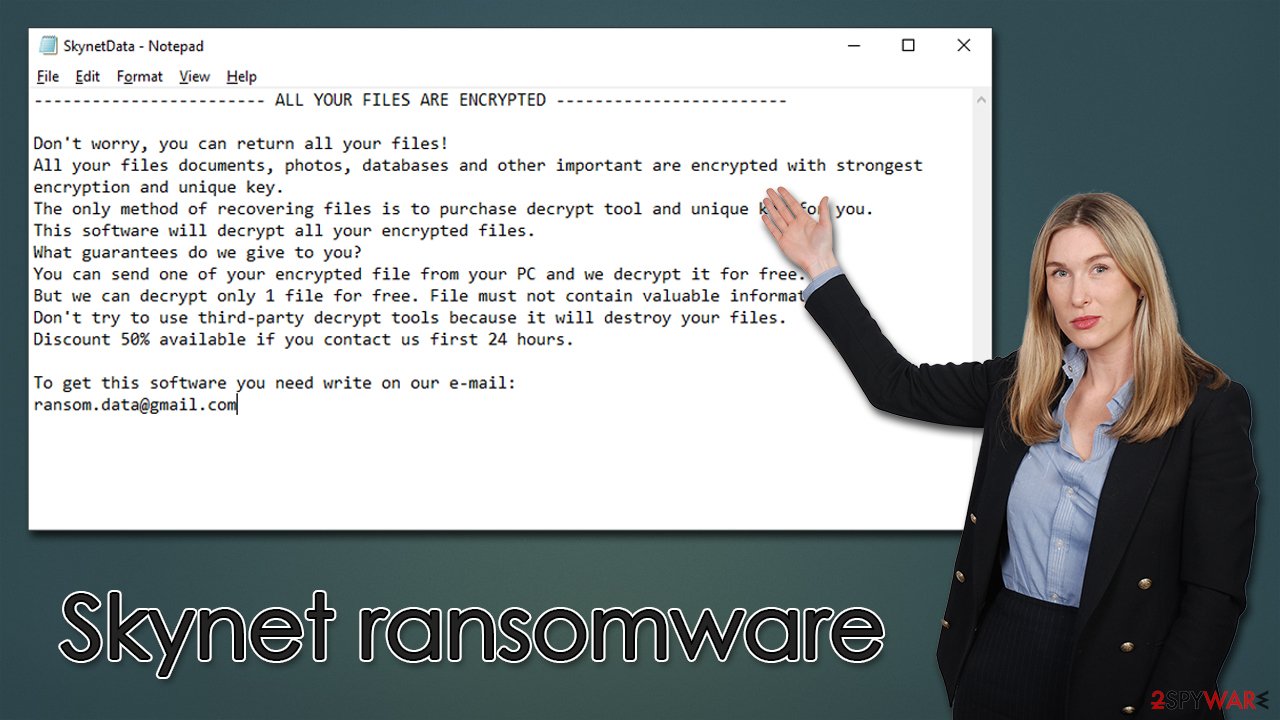
For communication purposes, hackers provide a contact email ransom.data@gmail.com within a ransom note SkynetData.txt. We strongly recommend avoiding any contact with Skynet virus authors and instead choosing alternative methods of file recovery we cover below.
| Name | Skynet virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .[random] |
| Malware family | Chaos |
| Ransom note | SkynetData.txt |
| Contact | ransom.data@gmail.com |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
Skynet virus and how to approach it
Skynet ransomware stems from a rather established malware family known as Chaos – we have already covered numerous of its previous versions, including Ritzer, BlackToxic, Odaku, and a few others. It was originally derived from the infamous Ryuk, and some of its versions are known to work as wipers, resulting in permanent data corruption.
This particular version came out in mid-July 2022 and did not differ much from its predecessors, although this time, malware appends a randomly-generated extension, which is appended to each of the personal files on the system. Suchlike modified files also lose the original icon – these two are the main symptoms of a ransomware infection.
Other signs include a changed desktop wallpaper, which shows a red triangle on the black background and says “Skynet Cyberdyne Systems.” Unsurprisingly, the malware drops a ransom note on the desktop and other locations and then opens it up automatically. The message inside reads as follows:
———————— ALL YOUR FILES ARE ENCRYPTED ————————
Don't worry, you can return all your files!
All your files documents, photos, databases and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees do we give to you?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information
Don't try to use third-party decrypt tools because it will destroy your files.
Discount 50% available if you contact us first 24 hours.To get this software you need write on our e-mail:
ransom.data@gmail.com
As per usual, crooks attempt to convince victims that paying the ransom is the best way out of this. However, you should keep in mind that ransomware creators are not your friends, and they don't care whether or not you receive your files, even after the asked bitcoins are sent to them. Trusting them is not recommended. Instead, we advise proceeding with Skynet ransomware removal and alternative ways of data recovery.
Malware removal
Most users who get hit by ransomware are first-timers, meaning that they usually know little about the infection and how it works. Ransomware is a rather unique malware, as its component of data encryption does not go away after the virus is eliminated. There are also many peculiarities that many users don't know about, thus, making incorrect moves might result in permanent data corruption.
Therefore, it is vital to perform malware removal in a correct manner. Your first task is to ensure that the virus can not communicate with a remote Command & Control[2] server, which the attackers commonly use to send commands for execution. In some cases, additional payloads could be sent to your machine, resulting in further compromise.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Once you are sure that the system is not connected to the network, you should use sophisticated anti-malware software and perform a full system scan with it. Security software, such as SpyHunter 5Combo Cleaner or Malwarebytes, can find and remove all the malicious components from the system at once and any secondary payloads that might be present.
Data recovery and system fix
Despite popular belief, the encrypted data would not be reverted to its previous state after malware is eliminated from the system and its affected network. This is because the deciphering process requires a unique key, which is the possession of ransomware creators.
While restoring files successfully without it is quite unlikely, we recommend trying a third-party recovery tool that might work in some cases or restore at least some of the lost data:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Skynet ransomware Skynet ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Some ransomware is simply programmed much worse than others and contains several bugs.[1] By finding them, cybersecurity researchers can sometimes create a working decryptor that victims can use for free. Keep in mind that this might or might not happen at all, or it might take a while. We recommend checking the following links for the decryptors regularly:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Ransomware is one of the most devastating infections out there, which means that its impact on the operating system can be significant. Not only do these types of malware spread in bulk with other infections, but they might also inject code or damage existing Windows components.
Once malware is eradicated with security software, some of the system files might be damaged or get corrupted. As a result, users might start experiencing system crashes, application errors, slowdowns, and other stability issues. To remediate this, you can employ a PC repair tool that can easily solve all these problems for you automatically.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
After all these steps are completed, you should ensure to prepare backups of your personal files to avoid devastating ransomware attack consequences. Likewise, reporting the incident to the authorities can help it to tackle cybercrime and increase the probability of cybercriminals' server seizures.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Encryption. Investopedia. Sharper insight, better investing.
- ^ John Bogna. What Is a “Command and Control Server” for Malware?. How-to Geek. Site that explains technology.












