SpartCrypt ransomware (Virus Removal Guide) - Improved Instructions
SpartCrypt virus Removal Guide
What is SpartCrypt ransomware?
SpartCrypt ransomware – a file-encrypting malware string that comes from the HiddenTear family
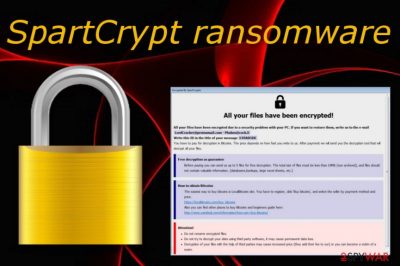
SpartCrypt ransomware is a ransom-demanding cyber threat that seems to have relations with the HiddenTear ransomware family line. The first one to discover this malware strain was a cybersecurity researcher known as S!Ri who posted the findings on Twitter.[1] This ransomware virus targets English-speaking users, infiltrates the Windows computer system, modifies entries, and performs encryption on all data files found. Later on, SpartCrypt ransomware drops the How_To_Restore_Your_Files.txt ransom note on the affected computer screen and also adds the suspicious message to each folder that holds encrypted data. Criminals urge for a ransom payment in order to receive the decryption tool for locked files. Also, these people try to prove the existence of this software by allowing victims to send 5 files that do not go over the limit of 10 MB combined altogether via the phabos@cock.li or lordcracker@protonmail.com email address.
| Name | SpartCrypt ransomware |
|---|---|
| Type | Ransomware virus/file-encrypting malware |
| Family | According to research, this notorious malware string comes from the HiddenTear ransomware family and holds a similar ransom message |
| Danger level | The virus ranks the danger level of very high. Despite the almost permanent file encryption process, the ransomware can modify numerous entries and processes on your computer system, cause software damage, and even install additional malware such as trojans |
| Extension | Once the data files and documents are locked by using unique ciphers, the ransomware virus appends the .Encrypted appendix to each filename of encrypted documents |
| Ransom note | How_To_Restore_Your_Files.txt is the ransom message that has been provided by SpartCrypt virus developers and encourages users to pay for the decryption tool as it is the “only way” to restore locked data |
| Email addresses | Regarding the information provided in the ransom note, the cybercriminals add the phabos@cock.li and lordcracker@protonmail.com email addresses as ways to reach them |
| Founder | This ransomware's appearance was first announced by a cybersecurity expert named S!Ri on the Twitter social platform |
| Removal | You should remove the cyber threat ASAP. For this purpose, use only trustworthy antivirus tools |
| System repair | If the malware has damaged some system components, you can try repairing them with a tool such as FortectIntego |
SpartCrypt ransomware uses unique encryption keys to lock up data files and stores both encryption and decryption keys on a remote server that is accessible only for the spreaders themselves. The malware developers might also try to harden the decryption process for users by inserting a particular module that provokes the ransomware virus to run specific PowerShell commands and eliminate the Shadow Volume Copies[2] of all locked documents/files.
Continuously, there might be a lot more that SpartCrypt ransomware might be capable of. For example, some file-locking threats also compromise the Windows hosts file[3] after installation on a particular computer system. This is a way to prevent users from accessing cybersecurity-related websites and forums that might help the person to find valuable information on how to remove SpartCrypt ransomware from his infected computer system.
In addition, you will supposedly find modified entries and processes in the Windows Registry and Task Manager. SpartCrypt ransomware might make changes to these locations in order to run automatically every time the user boots the computer or to avoid detection by some antivirus software. Remember that once you opt for the elimination process of the malware, SpartCrypt ransomware removal should also include the cleaning of all infected directories. Also, do not forget to delete the modified hosts file, otherwise, you will still be banned from security-related web pages.
Also, we recommend uninstalling SpartCrypt ransomware only with reliable antimalware products, otherwise, you might not be able to completely succeed in the process or might even cause more damage. Furthermore, if the malware has damaged some particular objects in your system, you also have a chance of repairing them with software such as FortectIntego, SpyHunter 5Combo Cleaner, Malwarebytes. Even though there is no 100% guarantee that a tool will work, it is definitely worth giving a try to.
Another thing we want to warn users about is that SpartCrypt ransomware developers might appear also to be scammers. This means that you should avoid paying ransom demands even if these people are hardly trying to convince you to transfer money by threatening you that using other data recovery products might relate to permanent file loss:
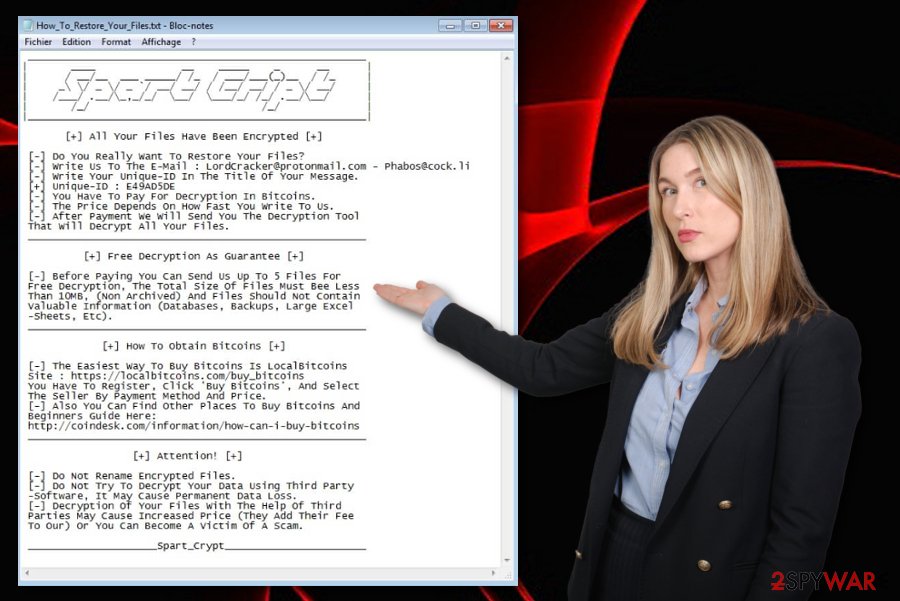
Spart Cript
_______________________________________________________
[+] All Your Files Have Been Encrypted [+] [-] Do You Really Want To Restore Your Files?
[-] Write Us To The E-Mail : LordCracker@protonmail.com – Phabos@cock.li
[-] Write Your Unique-ID In The Title Of Your Message.
[+] Unique-ID : XXXXXXXX
[-] You Have To Pay For Decryption In Bitcoins.
[-] The Price Depends On How Fast You Write To Us.
[-] After Payment We Will Send You The Decryption Tool
That Will Decrypt All Your Files.
_______________________________________________________
[+] Free Decryption As Guarantee [+] [-] Before Paying You Can Send Us Up To 5 Files For
Free Decryption, The Total Size Of Files Must Bee Less
Than 10MB, (Non Archived) And Files Should Not Contain
Valuable Information (Databases, Backups, Large Excel
-Sheets, Etc).
_______________________________________________________
[+] How To Obtain Bitcoins [+] [-] The Easiest Way To Buy Bitcoins Is LocalBitcoins
Site : https://localbitcoins.com/buy_bitcoins
You Have To Register, Click ‘Buy Bitcoins’, And Select
The Seller By Payment Method And Price.
[-] Also You Can Find Other Places To Buy Bitcoins And
Beginners Guide Here:
http://coindesk.com/information/how-can-i-buy-bitcoins
_______________________________________________________
[+] Attention! [+] [-] Do Not Rename Encrypted Files.
[-] Do Not Try To Decrypt Your Data Using Third Party
-Software, It May Cause Permanent Data Loss.
[-] Decryption Of Your Files With The Help Of Third
Parties May Cause Increased Price (They Add Their Fee
To Our) Or You Can Become A Victim Of A Scam.
_____________________Spart_Crypt_______________________
Even though the developers of SpartCrypt virus have not given a particular amount of money to be paid, the sum mostly varies from $100 to $2000 and needs to be transferred in some type of cryptocurrency, for example, Bitcoin. The criminals urge for cryptocurrency transfers as these types of payments allow them to stay safe and untrackable in case the victim decides to report the malicious ongoing activities.
Additionally, SpartCrypt ransomware might bring additional malware to your computer system, e.g. Trojan viruses. This way the crooks can even benefit more with two different viruses in their hands. Be careful and do not postpone the removal process of the ransomware virus as if you receive some additional malware, you can experience the risk of money loss directly from your banking account or identity theft if the infection accesses any personal information on your PC.
According to information posted by VirusTotal, around 49 AV engines out of a total of 69 detect SpartCrypt ransomware. Take a look down below and find out the detection names by which the malware is found by popular antivirus tools:[4]
- Win32:RansomX-gen [Ransom] (Avast and AVG).
- Gen:Heur.Ransom.REntS.Gen.1 (B) (Emsisoft).
- Ransom.SpartCrypt (Malwarebytes).
- HEUR:Trojan-Ransom.MSIL.Encoder.gen (Kaspersky).
- Gen:Heur.Ransom.REntS.Gen.1 (BitDefender).
- W32.Trojan.Gen (Webroot).
Spreading techniques of ransom-demanding viruses
Regarding experts from Virusai.lt findings,[5] ransomware infections can be intensively distributed by using multiple deceptive techniques. However, the most popular way to spread ransomware is by adding the malicious payload to a spam email message. Usually, it comes in the form of an executable file, word/PDF document, or something similar.
Continuously, ransomware infections are also commonly distributed via software cracks from websites such as The Pirate Bay, eMule, and other torrenting networks. You can accidentally download malware from infected downloading hyperlinks and launch the ransomware-related payload straight on the computer system.
In addition, you might find ransomware viruses spread via malicious software updates that pretend to be regular program upgrades. Also, the hazardous payload can come in infected advertisements and hyperlinks on unsecured third-party networks.
Avoid ransomware infections for proper computer protection
We have already introduced you to ransomware spreading techniques and now its time to teach you how to protect yourself from the infections properly. First of all, you should carefully manage all of your email letters, verify the sender and look for grammar mistakes in the message text. Be aware that the crooks might even pretend to be from reputable shipping companies such as FedEx or DHL just to give you a look of legitimacy.
To continue, do not download software, videos, or files from unsecured downloading sources, avoid p2p networks as these websites do not hold a good reputation. Also, always make sure that you have reliable antimalware protection running while you are completing online and computing actions as this software is capable of spotting sneaky threats that the user himself might not be able to see.
Last but not least, you should also think about the safety of your data files and documents. In order to avoid possible encryption, have your data always backuped. For this purpose, purchase a removable USB flash drive or transfer copies of important data to some remote servers such as iCloud or Dropbox. The more storage places you have, the better the protection will be. However, keep in mind that you need to keep the USB drive unplugged from the machine while you are not using it as if the device is connected the ransomware can reach it also.
SpartCrypt ransomware elimination guidelines
If you have been struggling to get rid of SpartCrypt virus, we are here to help you. First of all, do not try to eliminate the malware completely on your own as if you are not a highly-skilled computer user, you might find yourself struggling with the process and making more damage than there is done already.
Opt for the automatical SpartCrypt ransomware removal process that requires downloading and installing reputable antimalware products. This way you will have the ability to clean your computer system and erase the cyber threat without making additional damage and be sure that the entire task has been carried out quality-full.
Once you remove SpartCrypt ransomware from your Windows PC, you have to go in search of possibly-corrupted components, filers, and software. If you discover some compromised or damaged objects on the machine, you can try fixing them with automatical programs such as FortectIntego, SpyHunter 5Combo Cleaner, or Malwarebytes. Also, you can keep one of them running as antivirus protection that will alert you of possible system problems in the future.
Getting rid of SpartCrypt virus. Follow these steps
Manual removal using Safe Mode
To decline malicious processes on your Windows computer system, you have to boot the machine into Safe Mode with Networking. Accomplish this type of task by completing the following.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove SpartCrypt using System Restore
To prevent malware-laden activities from operating on your infected machine, bring it back to a previous state by launching the System Restore feature.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of SpartCrypt. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove SpartCrypt from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Below you will find some methods that might be helpful with .Encrypted files recovery. Even though there is no 100% guarantee that these techniques will work, carrying them out is still a way better than agreeing to pay the demanded ransom.
If your files are encrypted by SpartCrypt, you can use several methods to restore them:
Employ Data Recovery Pro and try restoring some encrypted files.
Try using this tool if you have discovered some files that have been modified, corrupted, or locked by the ransomware virus.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by SpartCrypt ransomware;
- Restore them.
Try using Windows Previous Versions feature to succeed in the data recovery process.
Opt for this feature if you are having trouble with encrypted data. However, you need to ensure that System Restore has been already activated before you try performing this file restoring method.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer might help you with file restoring.
If the ransomware infection has not damaged the Shadow Volume Copies of your locked files, you can definitely give this tool a try as it might allow you to restore some data back to its previous state.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, the official SpartCrypt ransomware decryptor is not available yet. We will try to inform all users as fast as possible if there are any changes.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from SpartCrypt and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ S!Ri. #ransom SpartCrypt . Twitter.com. Social platform.
- ^ What is Volume Shadow Copy Service (VSS)?. Quora.com. Relevant questions and answers.
- ^ Bradley Mitchell. What Are Windows Hosts Files?. Lifewire.com. And independent news source.
- ^ Spart_E.exe. 49 engines detected this file. VirusTotal. File information.
- ^ Virusai.lt. Virusai. Spyware and security news source.





















