HiddenTear ransomware / virus (Virus Removal Guide) - updated Feb 2019
HiddenTear virus Removal Guide
What is HiddenTear ransomware virus?
Hidden Tear is a first-ever open source ransomware trojan that allows even inexperienced devs to lock victims' files

Hidden Tear is an open-source ransomware project that was initially developed for educational purposes[1] back in 2015 by Turkish researcher Utku Sen. However, cybercriminals did not wait too long to adapt the code and use it for money extortion purposes, infecting Windows computers and locking files with a sophisticated AES algorithm. Hidden Tear has a modifiable ransomware kit, meaning that even novice hackers could use the code. It resulted in a massive outbreak of viruses that are based on HiddenTear code, such as Winsec virus, BlackRose,[2] Karmen, Kampret, Mora Project, Educrypt, Sorry, SorpionLocker, etc. The viruses appended a variety of different file extensions (.lock, .cerber, .LoveYou, .Lime, etc.), and prevented victims from accessing them unless they pay for the decryption key. Nevertheless, most crypto-locker's variants can be decrypted with the help of two official tools released by security researchers.
| Name | HiddenTear |
|---|---|
| Type | Ransomware (open-source) |
| Versions | Winsec, BlackRose, Karmen, Kampret, Mora Project, Sorry, etc. (full list below) |
| Symptoms | Personal files locked, ransom note created on the desktop |
| Distribution | Spam email attachments, backdoor |
| Decryptable? | Yes. Decrypt Hidden Tear locked files with Decrtyptor 1 (link) or Decryptor 2 (link) |
| Danger level | High. Initiates multiple system's changes, including Windows Registry and Boot. Can result in permanent data loss |
| Elimination | Use reputable anti-malware tools |
| Recovery | To recover from system damage caused by Hidden Tear ransomware, use FortectIntego |
Hidden Tear author, Turkish programmer named Utku Sen, uploaded the payload in GitHub page for the first time in 2015.[3] Whether he anticipated the virus to evolve into such malware pattern helping other hackers to make money remains a rhetoric question entirely. Since its introduction, cybercriminals have been actively exploiting the programming code for their malicious intentions.
A few French[4] versions were detected. Unlike other counterparts, the first variation contains very detailed payment site. After finishing the encryption procedure, it appends .locked file extension. Further instructions are delivered in READ_IT_FOR UNLOCK.txt and Tutoriel.bmp files.
The second variation appends the same file extension, but it introduces itself as VideoBelle ransomware. Interestingly, while the ransom note is written in French, it still demands 150 British pounds as a ransom.
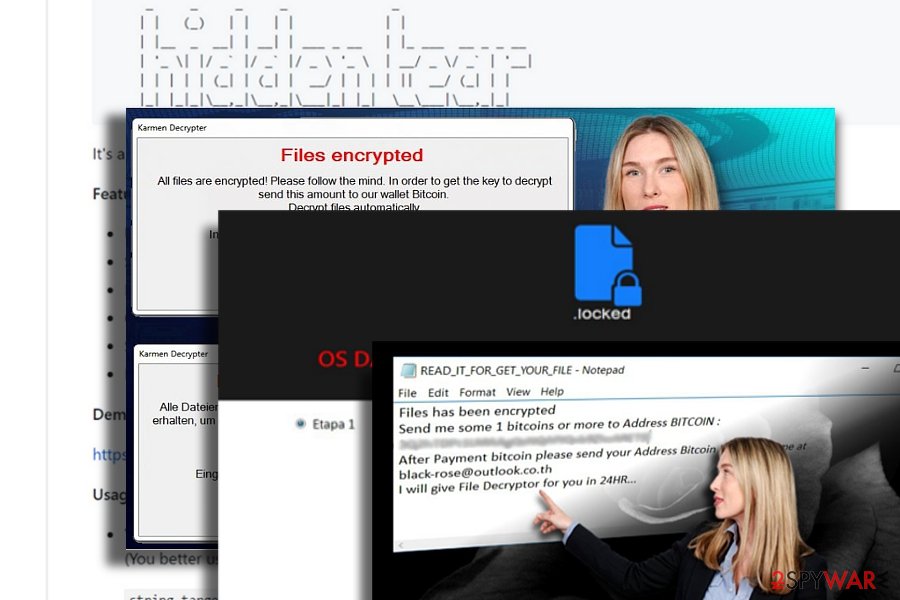
While the majority of Hidden Tear variations are created to extort money, some versions of this malware are designed for fun. One of the recent variations uses a photo of a famous virus researcher called Karsten Hahn. Luckily, this version does not encrypt files.
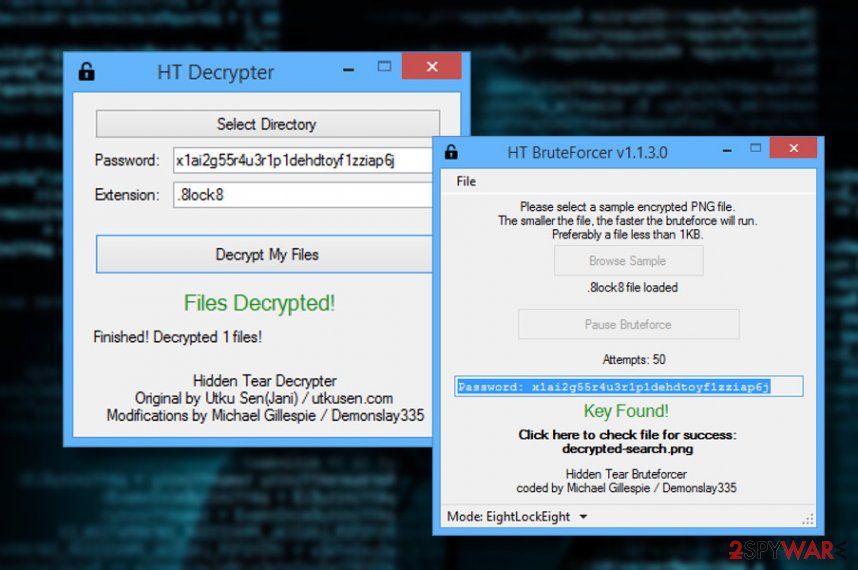
Within such short period of existence, the heir of the malware – HiddenTear 2.0 dwells on the web as well. Indeed, it has developed into one of the biggest cyber issues. On the other hand, IT professionals have already presented a decrypter for this malware and several other viruses which are based on this code. Note that HiddenTear removal must be performed before jumping to a file-decrypting procedure. FortectIntego or Malwarebytes is capable of completing efficient termination.
One of the main factors, which have determined such wide-spread of the Hidden Tear, was its accessibility on the world wide web. The GitHub page with the pattern of the malware is accessible for everyone and does not require the access to Tor or dark web. According to its author, Hidden Tear malware uses the standard AES encryption method. It generates a public key which is additionally transmitted to a remote Command and Control[5] server. In order to decrypt files encoded with this tool, a special private key is required.
On the other hand, a certain level of programming knowledge is also needed. A web server, which supports Python, PHP, JavaScript and other variations of programming languages, is necessary to complete the configuration of HiddenTear malware.
Despite warnings not to use this malware for other than educational needs, a string of Hidden Tear-based viruses have emerged. Exceptional feature unifying these threats is that they do not have GUI or Graphical user Interface. In other words, once the virus fully occupies the system, it creates a .txt file. Depending on the author, the ransom note may include an extensive description of the virus and detailed instructions on how to get rid of the virus.
Usually, victims are required to pay a ransom which should encourage the bad guys to recover victims' files. However, such cases are quite rare. Elaborating on GUI feature,[6] WinSec ransomware sample negates the rule as it presents its unique interface in the Portuguese language.
Thus, it suggests that the availability of Hidden Tear ransomware also gives room for crafting more exquisite versions. One of the versions even targeted Pokemon Go players in Central Asia a while ago[7].
Hidden Tear variants
HiddenTear 2.0 ransomware virus. This version of ransomware encrypts files and provides data recovery instructions in README.txt file. The ransom note tells that victims have to use a password in DecryptPassword.txt file that has been hidden somewhere in the targeted computer. However, the file is located in My Documents folder. Once you decrypt your files, you should also scan the computer with reputable security software.
Faizal ransomware virus. Malware spreads as a fake installer package of “Street Racing Club” game which is popular in Southeast Asia. However, ransomware mostly aims at Indonesian computer users. To the encrypted files, it appends .gembok file extension. Following data encryption, the virus delivers a ransom note called PENTING !!!.htm where cyber criminals ask to send a voucher code of 100.000 Indonesian Rupees to leprogames777@gmail.com. Nevertheless, the size of the ransom is not high (about $7.50); paying is not recommended.
Kindest ransomware virus. It’s an educational version of Hidden Tear ransomware. Instead of encrypting files, ransomware asks to show a YouTube video about file-encrypting viruses. Once people finishes watching the video, malware is supposed to delete itself. However, we also recommend scanning the computer with reputable security software to make sure that virus is gone.
FailedAccess ransomware virus. Also known as CryptoSomware virus, this cyber threat appends .FailedAccess file extension and demands to pay the ransom. However, victims of the ransomware can use StupidDecryptor and restore corrupted files for free. Thus, after the attack, the only thing you need to do is to perform virus removal.
Mordor ransomware virus. The virus uses AES-256 cryptography to damage files on the targeted computers. Once all files have the .mordor extension, it opens a ransom note from READ_ME.html file. Written in English, Japan, Italian, Chinese, Indian, Portuguese, French and German languages, the ransom note says that victims have to pay 0.07066407 BTC in order to recover the files. Undoubtedly, instead of paying, you should get rid of the virus.
Ruby ransomware virus. Behind this crypto-malware stands a hacker named Hayzam Sheriff. The virus is designed to append the .ruby file extension to each of the targeted data. Once this hazardous task is done, malware automatically opens a ransom note rubyLeza.html. However, author of the virus does not reveal how much Bitcoins victims have to transfer. Thus, there‘s nothing else left to do, just remove Ruby from the PC.
GruxEr ransomware virus. This variant of HiddenTear uses three executables to run different malicious programs on the affected computer: TEARS.exe, WORM.exe, and GRUXER.exe. Nevertheless, malware encrypts numerous file of types; the priority is JPG files. Cyber criminals provide data recovery instructions in READ_IT.txt file and run a program window. In order to decrypt corrupted data, victims are asked to pay $250 in Bitcoins.
Decryption Assistant ransomware virus. This malware spreads as a fake Adobe Flash Player update. Once victim installs it, ransomware starts encrypting files and appending the .pwned file extension to each of them. Then it runs a program window that includes data recovery instructions and the timer that shows how much time left to pay the ransom. However, you‘d better hurry up with virus removal.
MoWare H.F.D ransomware virus. The significant feature of the ransomware is added file extension – .H_F_D_locked file extension. Then malware informs about the possibility to obtain decryption software for 0.02 Bitcoins. However, if users do not take this offer within 4 days, the size of the ransom will increase to 0.05 Bitcoins. After transferring the money, victims need to contact hackers via heyklog@pronmail.com and send their Bitcoin transaction ID. However, following these instructions may lead to financial loss.
Crying ransomware virus. This file-encrypting virus enters the system as ECRYING.exe file and starts encrypting files with AES cryptography. After encryption, all targeted files have .crying file extension. It also installs a ransom note called READ_IT.txt and runs a program window where authors of Crying malware gives Bitcoin wallet address where victims have to transfer the ransom.
R3store ransomware virus. The virus marks targeted files with .r3store file extension that prevents victims from using them. It downloads a ransom note called READ_IT.txt to each folder that includes encrypted data. The ransom-demanding message reveals that data recovery with hackers‘ software costs $450. However, no one can guarantee that this tool is actually working.
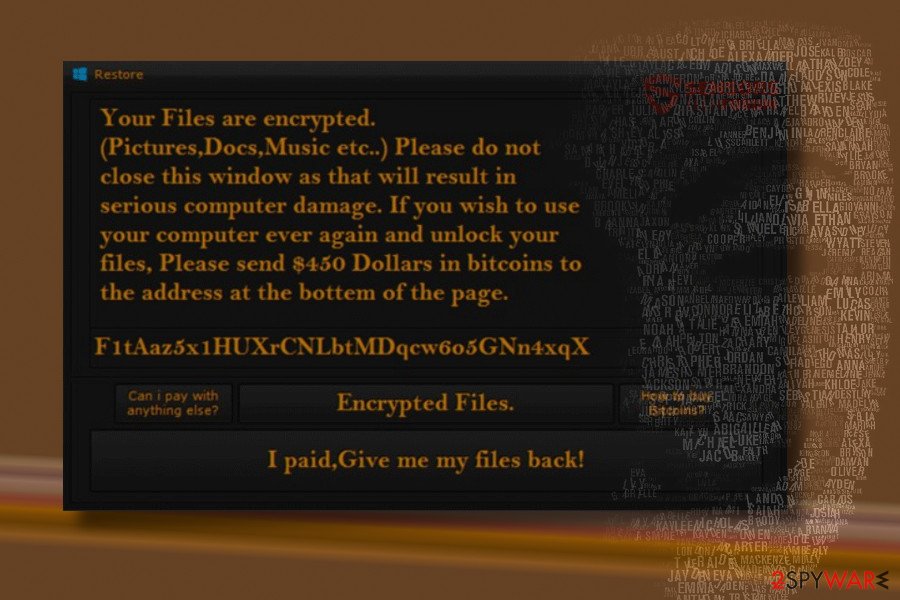
Resurrection ransomware virus. It encrypts files with AES-256 cipher and adds .(random).resurrection file extension to the targeted data. Once it‘s done, ransomware opens the README.html file in browser‘s window. Here cyber criminals ask to contact them via resurrection777@protonmail.com and transfer 1.77 Bitcoin in order to get a decryption key.
Executioner ransomware virus. It’s a Turkish version of Hidden Tear malware. It appends a random file extension to encrypted files and provides ransom payment instructions in .txt and .html files. The Sifre_Cos_Talimat.html informs that victims have to contact attackers executioner.ransom@protonmail.com and send 150 in Bitcoins. However, doing this is not necessary because malware is decryptable.
KKK ransomware virus. Malware spreads as an obfuscated Facebook.exe file. Undoubtedly, the file name is tricky and misleading. Once this payload is downloaded to the system, malware starts data encryption and adds .KKK file extension to targeted files. Then malware runs an “Information” window that provides instructions how to redeem encrypted files. To get back their files, people have to transfer 0.05 bitcoins (not recommended).
BeethoveN ransomware virus. The virus is designed to encrypt files using a combination of AES and RSA ciphers. It appends .beethoveN extension to each of the targeted file. Once it's done malware delivers ransom payment instructions in the FILEUST.tx file and program window. Victims are supposed to transfer the ransom within 168 hours (not recommended).
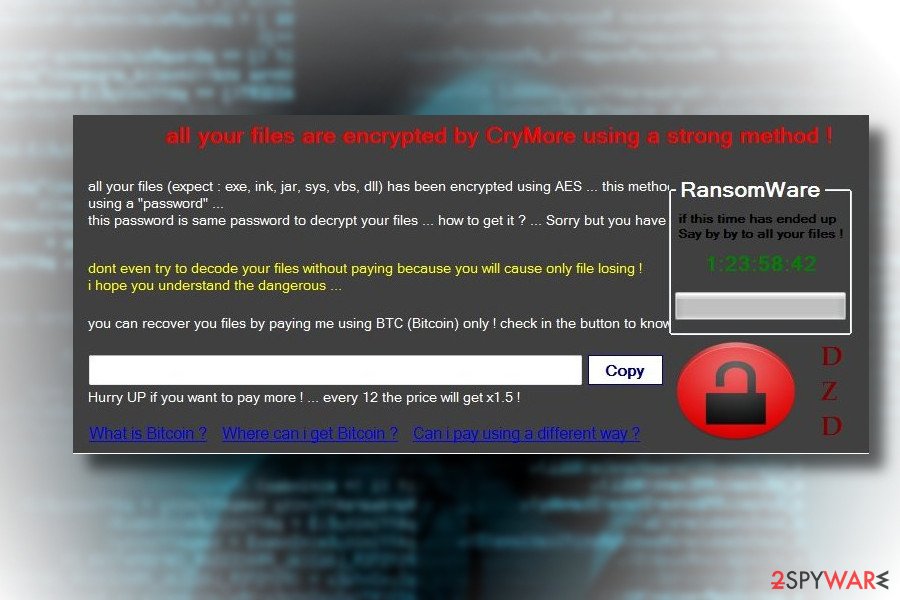
CryMore ransomware virus. The hacker named “TMC” was inspired by WannaCry and make a virus which name resembles the infamous cyber threat. Ransomware uses AES encryption to lock the most popular types of files on the affected computer. In the poorly written ransom note, victims are asked to pay the ransom within 12 hours. Later the demanded sum of money will increase.
CryptoGod ransomware virus. During data encryption, the virus adds .payforunlock file extension to each of the targeted document, audio, video, image and other files. The ransom note tells of paying 0.03 BTC for data recovery. The size of the payment will increase up to 0.05 Bitcoins after provided deadline. After the transaction, victims have to send an email to cryptogod@airmail.cc. However, you may not receive an answer and help to restore your files.
$usyLocker ransomware virus. This variant of HiddenTear is executed from VapeHacksLoader.exe. After infiltration, malware encrypts data and appends .WINDOWS file extension. In the ransom note called READ_IT.txt criminals inform that victims have to pay 0.16 Bitcoins. However, it’s a risky business that may lead to money loss.
CryForMe ransomware virus. The virus pretends to be related to the infamous WannaCry ransomware. Malware is executed from CryForMe.exe. On the affected device it starts data encryption procedure immediately. When all targeted files are secured, the malware runs a blue ransom-demanding window. Cyber criminals ask to pay €250 in bitcoins within 7 days time.
Mora Project ransomware virus. This variant of Hidden Tear prevents victims from opening their files by appending .encrypted file extension. People are suggested to use The-decrypter.exe program to recover their files for $40.000. However, following the instructions provided in ReadMe_Important.txt file is not recommended.
FlatChestWare ransomware virus presents a few interesting features. While the operation mode does not differ much from its previous versions, as it encodes files and appends .flat file extension to the affected data, it displays a fake Windows UAC message.
After you open the FlatChestWare.exe file gets executed, the malware will prompt a User Account Message asking you to restart the system in order for the supposed Windows update to complete successfully. Note that there the genuine Windows Update messages slightly differ. Latest messages do not remind you to save data.
Furthermore, in Windows 10 systems such messages do not appear anymore. A similar message appeared due to the bug in 2918614. It seems that the developer – the fan of anime – failed to make the malware a full-fledged malware as this version is decryptable.
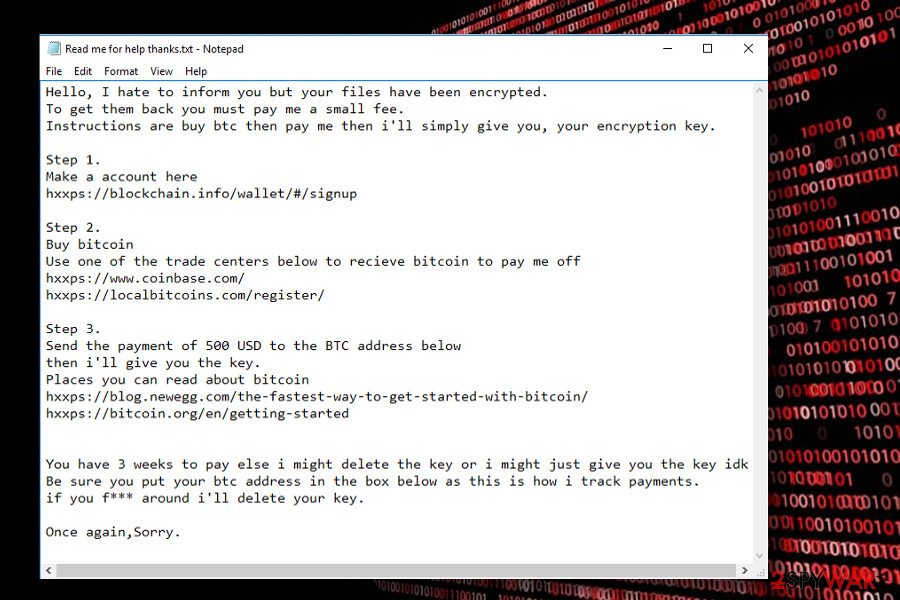
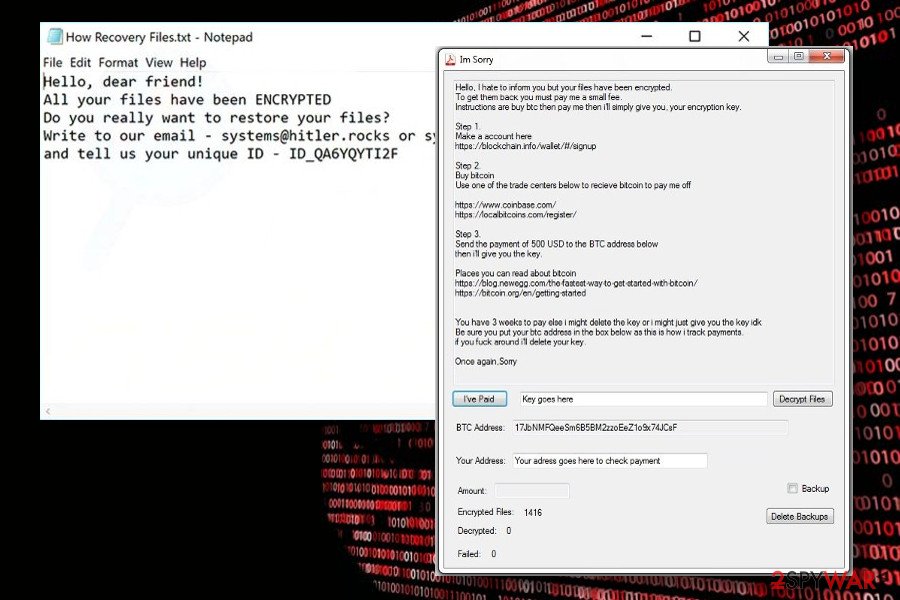
Sorry ransomware. Detected at the end of March, 2018, it's the latest variant based on this open-source ransomware project. Upon successful infiltration, the ransomware runs a task called John Cena, schtasks.exe file, which is responsible for rooting, and releases multiple cmd.exe scripts, including the one that commands to remove Volume Shadow Copies.
After that, Sorry virus changes the extensions of the most files to .sorry and creates a ransom note c:\Windows\hrf.txt. To render personal files useless, it renders symmetric encryption algorithm (AES) cryptography model, which can be cracked only by entering a personal ID number. The victim of the Sorry ransomware is demanded to pay the ransom, which currently ranges from $500 to $1500 in Bitcoins.
To get a guidance on how the payment has to be transmitted, the victim is asked to write a personal ID on emails svchostport@tutanota.com or cjhost@tuta.io. Nevertheless, we do not recommend paying the ransom. Instead, Sorry Randomwar3e and try to decrypt files using a free HiddenTear decryptor.
Distribution methods remain the same
Another feature for the malware which contributed to the success of the malware was its transmission techniques. Mainly, it traveled as an email attachment appended to “urgent” and “highly important” emails. Some users may even get alarmed with fake notifications from a tax institution or the FBI.
Thus, do not rush to unwrap such attached file before verifying the sender. You may also pay attention to certain details which hint the origin of the message: grammar mistakes, types and altered credentials.
Furthermore, trojans also facilitate Hidden Tear hijack. In order to reduce the risk of such infiltration, combine your anti-virus app with anti-spyware software. Regardless of the claims about the immunity to AV programs, the majority of HiddenTear variations are detectable[8].
Steps to terminate HiddenTear infection
When it comes to the original version of Hidden Tear virus or a derivative version, brush aside the idea to terminate it manually. The malware is capable of disguising its source files and processes so manual eradication may not be successful. Thus, let a cyber security application remove HiddenTear.
While the original version hardly behaves as a screen locking threat, some of the newer ones may disable specific system functions which result in a lock screen. In that case, benefit from the below instructions. Once you regain full control, continue Hidden Tear removal with the help reputable security software.
Getting rid of HiddenTear virus. Follow these steps
Manual removal using Safe Mode
Recover the access to all computer functions with Safe Mode function.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove HiddenTear using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of HiddenTear. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove HiddenTear from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by HiddenTear, you can use several methods to restore them:
Data Recovery Pro method
This program claims to be able not only recover the encrypted files but lost emails as well.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by HiddenTear ransomware;
- Restore them.
The benefit of ShadowExplorer
Despite the popularity of HiddenT ear virus, it hardly deletes shadow volume copies – the tool for Shadow Explorer to recover your encoded data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Hidden Tear Decrypter
You can now decrypt the majority of viruses originating from this malware. There are two alternative versions:
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from HiddenTear and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ hidden-tear. GitHub. Built For Developers.
- ^ BlackRose Ransomware. ID Blogspot. malware reviews.
- ^ Hidden Tear Project: Forbidden Fruit Is the Sweetest. Tripwire. The state of security.
- ^ Eliminate computer threats. Lesvirus. IT News and Malware Removal Guides in French.
- ^ Adam Rice and James Ringold. Command-and-control servers: The puppet masters that govern malware. SearchSecurity. Information Security information, news and tips.
- ^ Vangie Beal. GUI - graphical user interface. Webopedia. Online Tech Dictionary.
- ^ Hidden Tear Ransomware Targets Arabic Pokémon GO Players. NewsBTC. Bitcoin News, Price and analysis.
- ^ Simona Atanasova. The Newly-Discovered Crypton Ransomware Is ‘A Good One’. VirusGuides. Powered By Knowledge.





















