Tail Box browser hijacker (Free Guide) - Chrome, Firefox, IE, Edge
Tail Box browser hijacker Removal Guide
What is Tail Box browser hijacker?
Tail Box is a browser-hijacking app that tracks user data and shows ads
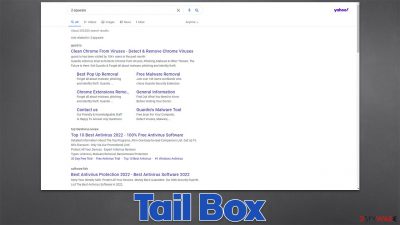
Tail Box is one of many potentially unwanted applications[1] that one could find installed on Google Chrome, Mozilla Firefox, MS Edge, or another browser. It comes in the form of an extension – a type of software that attaches itself to the web browser to function. The app specializes in the so-called hijacking, where it takes over the browser in order to implement its own settings in order to perform its activities.
How the hijacker operates
The deceptive aspect of the Tail Box hijacker starts with its distribution. While some users might install the extension intentionally, believing that it might be useful, others never remember installing it in the first place. This happens due to software bundling – a distribution technique that tricks many people into accepting optional programs during the installation process of the freeware.
Once installed, the browser hijacker would immediately change the homepage and the new tab function by appending tailsearch.com to them. By doing so, it forces users to use its modified search box or the URL box, which would guarantee that the searches are performed via alternative routes or measures.
First of all, users would immediately notice that the search results are no longer being produced by Google but rather Yahoo instead. While the provider is trustworthy, it is known for its affiliate programs which are adapted by many browser hijackers and other potentially unwanted programs. Many users begin to worry when their browsers suddenly begin redirecting to Yahoo.
While the situation is not considered to be dangerous, Tail Box hijack is much more significant than one might believe. Besides the changed search provider, the app inserts plenty of ads and sponsored links at the top or other locations whenever users try to use their browsers. Without a doubt, this can greatly change which websites are being visited, which links are clicked, or even which products or services are being purchased.
It is important to note that advertising content is not always accurate, useful, or even safe, as hijackers tend to advertise other potentially unwanted programs quite often. Therefore, we recommend you avoid any sponsored links as long as the app is installed on your browser.
| Name | Tail Box |
|---|---|
| Type | Browser hijacker, potentially unwanted browser extension |
| Distribution | Software bundling, malicious ads, redirects from other websites |
| Symptoms | Unknown extension installed on the browser; intrusive ads at the top of search results; redirects to potentially dangerous websites; homepage and a new tab is set to tailsearch.com, which forwards searches to Yahoo |
| Dangers | Redirects to malicious websites can result in intrusive notifications, personal information disclosure to cybercriminals, financial losses, installation of other potentially unwanted programs/malware |
| Uninstall | To remove the unwanted browser extension, you should access your browser's settings section. Checking the system with SpyHunter 5Combo Cleaner security software can also ensure that there is no adware or malware running in the background |
| Other tips | After you eliminate the hijacker, you should also clean your web browsers to avoid tracking and other issues. You can use FortectIntego as a quick solution |
The unwanted data tracking
Another concerning trait of many potentially unwanted programs, Tail Box included, is data tracking practices. The main goal of such applications is not to provide some sort of useful function for users (hence many PUPs employ superficial features or fail to deliver anything useful whatsoever) but instead expose as many users to ads as possible, monetizing the process through pay-per-click[2] and similar schemes.
In order to be successful in it, potentially unwanted applications commonly track users – which websites they visit, links they click, how long they spend on certain websites, which ads they interact with, which search queries do they type, among other details. This provides the developers of PUPs to ensure that they can deliver more targeted ads to users, making them more likely to interact with them.
The side effect of this activity (even though the collected data is mostly anonymous) is that the information is regularly sold or shared with service providers, affiliate networks, and other third parties. Without a doubt, this can negatively impact users' privacy, as there are no guarantees that all the collected information isn't private and that third parties are adequately protecting it from theft or leaks.
Therefore, if you want to regain the function of your browser, you should remove the hijacker and all the other potentially unwanted applications from your system immediately. Below you will find a thorough explanation of how to do just that.
How to remove Tail Box
In most cases, potentially unwanted applications are more nuisances than a real threat, as they are accustomed to tracking anonymous user data and display ads. However, this might not always be the case, and we have seen plenty of browser extensions or programs that might seem innocent initially only to later start performing illegitimate actions, such as tracking personal data or promoting malicious ads.
Thus, even if it seems that the app is not really doing anything, it might not be the case in the background. This is precisely the reason why you should immediately, after noticing unexpected browser behavior scan your system with powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes – this would ensure that the most aggressive PUPs and malware are deleted.
However, you should also check the section of the installed browser extensions manually, as they might not always be removed automatically. Please follow these instructions:
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
MS Edge (legacy)
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.
![Remove extensions from Edge Remove extensions from Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Clean your browsers to protect your privacy
As we have previously explained, potentially unwanted applications are set to track user data for profits and the ability to show more relevant ads. These actions are performed with the help of various cache files that are placed by the hijacker as soon as it is implemented – cookies[3] are a prime example of this.
Cookies and other tracking elements are not and can't be malicious. They are small and simply do not have the capabilities or performing malicious actions on the device. Their main function is to store various preference and setting information, as well as session information – they are the primary reason why you can log in to all your accounts automatically every time you visit the same website without having to enter your credentials.
However, this feature, while useful, also poses some dangers due to a dangerous attack known as session hijacking, where cybercriminals could take over users' sessions, accessing their accounts in the process. Security experts strongly recommend learning browser caches from time to time in order to avoid this and unexpected loading errors.
To clean the web data, you would either have to access browser settings and do it manually or use an alternative method –FortectIntego scan, which can automatically remove all the leftover files from your system and fix malware-related system damage.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
MS Edge (legacy)
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.
![Clear Edge browsing data Clear Edge browsing data]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
How to prevent from getting browser hijacker
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Chris Hoffman. PUPs Explained: What is a “Potentially Unwanted Program”?. How-To Geek. Site that explains technology.
- ^ Pay-per-click. Wikipedia. The free encyclopedia.
- ^ What are Cookies?. Kaspersky. Resource Center.










