Tidywarden.store ads (fake) - Free Instructions
Tidywarden.store ads Removal Guide
What is Tidywarden.store ads?
Tidywarden.store promotes fake virus infection messages
Tidywarden.store is one of many malicious websites that show fake virus infection messages in order to profit from affiliate sales on software. Most people enter this dubious site after clicking a booby-trapped link on torrent and similar high-risk websites, although this is not necessarily a rule – adware could also be the reason for unexpected redirects.
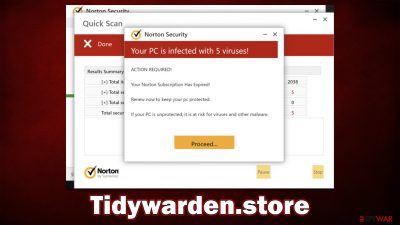
Once on the site, people are shown a security scan that soon shows alarming results: the device is infected with five viruses! The warning comes from Norton, a prominent security vendor. However, everything about this is fake – the vendor has nothing to do with Tidywarden.store, and it was created by cybercriminals. The scan results are also fake, and their main purpose is to frighten users and make them purchase software they don't need.
| Name | Tidywarden.store |
| Type | Scam, phishing, adware, redirect virus |
| Distribution | Compromised websites, pop-up ads, potentially unwanted applications |
| Scam content | Claims that the subscription for security software has expired and that it needs to be renewed immediately. Asks to download malicious software and enable push notifications |
| Dangers | Financial losses due to fake subscriptions; redirects to other malware-laden, scam websites; installation of potentially unwanted or malicious software |
| Removal | Do not interact with links or other content of a scam site. Instead, check your system with SpyHunter 5Combo Cleaner security software |
| Other tips | After you eliminate all unwanted/malicious software from your system, make sure you clean your web browsers and repair system files. You can do that automatically with FortectIntego or refer to our manual guide |
Scam operation explained and tips not to get tricked
The main goal of fake messages online is to profit from ads, software downloads, or subscriptions to various services. While selling software or services is a completely legitimate practice used by many websites and advertisers, it becomes the opposite when highly misleading messages are used to promote it.
Upon entering Tidywarden.store, users are presented with a fake anti-malware scan, which immediately comes back with the following fake result:
Your PC is infected with 5 viruses!
ACTION REQUIRED
Your Norton Subscription Has Expired!
Renew now to keep your PC protected.
If your PC is unprotected, it is at risk for viruses and other malware.
Since the website uses pop-ups, flashing detection triggers, and alarming scan results, some users may get frightened by the prospect that their systems are in grave danger, and scared users are more likely to make mistakes and fall for the scam. They are afraid that their personal information might have been stolen or that their systems were compromised beyond repair. All of these elements are fake and are simply a part of a social engineering[1] scheme.
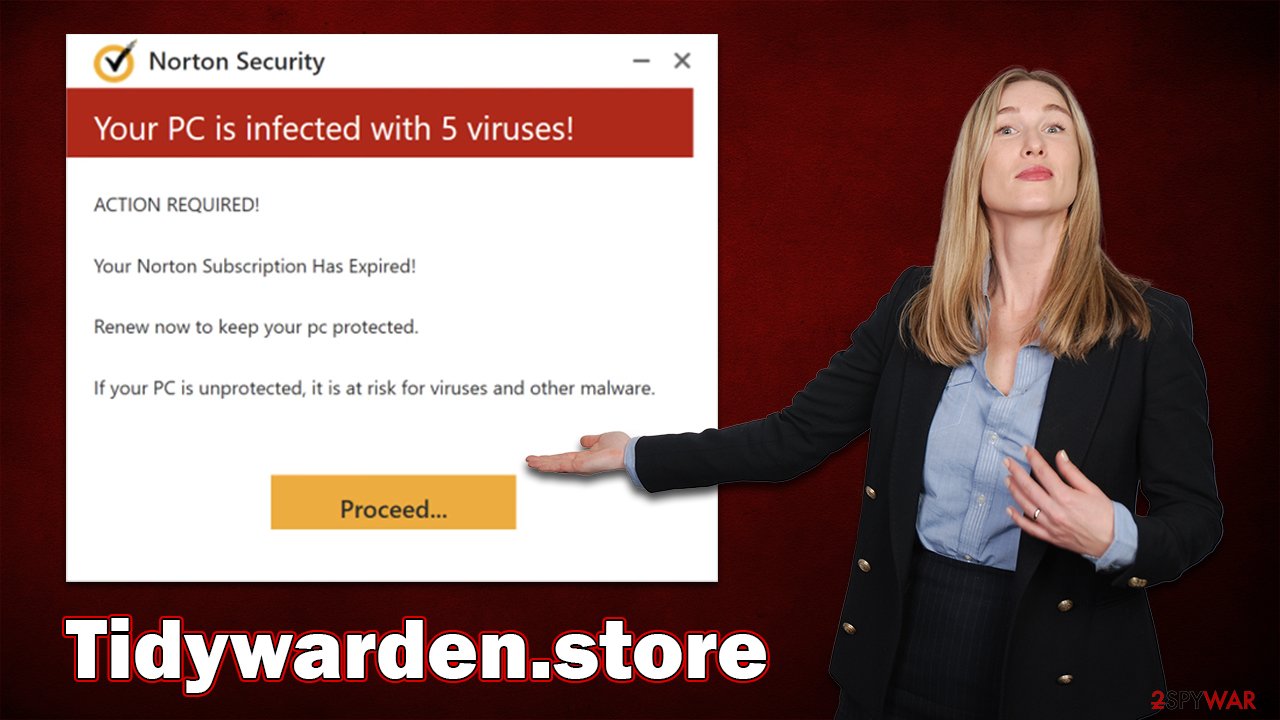
Crooks use various tricks to convince users that Tidywarden.store ads are true. In this case, they are using the name, the logo, and the design of application windows of Norton – a reputable security vendor known for many. Keep in mind that all visual components can be faked, so you shouldn't believe them straight away. Instead, look for the URL of the website showing you these questionable messages, and you'll see they have nothing to do with any legitimate company.
Is my system infected?
Since users encounter scam websites accidentally, they are often caught off guard. Some recognize deception straight away, while others oblige and get tricked by the scam. There are also people who wonder whether their systems got infected after they entered Tidywarden.store, whether they clicked links on it or not.
The likely scenario to get infected is by installing programs or browser extensions promoted on these rogue sites. There is a small chance malware could be installed automatically, although your browser needs to be vulnerable,[2] and the page needs to host an exploit matching it. Thus, this scenario is highly unlikely.
Whether you interact with the scam site or not, you should still make sure that your system is not infected, as adware is a well-known catalyst for unexpected redirects to phishing websites and an increased number of advertisements.
Make system checks
First of all, we recommend you scan your device with Malwarebytes or SpyHunter 5Combo Cleaner security software. These apps can easily check your device and remove everything suspicious – from trojans to potentially unwanted programs. Nonetheless, if you want to perform removal manually, you can follow the provided instructions below.
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
While moving apps into Trash is usually how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
After you uninstall all the suspicious programs/applications from your system, it is time to check your browsers. First of all, you should click the “Extensions” button next to the settings menu on your browser and uninstall everything you find suspicious. Sometimes, it is more difficult to determine what causes the disruptive activity if numerous add-ons ate installed at once. In this case, we recommend removing everything.
Finally, you should take care of your privacy. After entering a dubious website or after installing questionable software, cookies[3] and other trackers are placed on your device. They may remain there for a very long time unless they are deleted. You can employ FortectIntego for this job or follow the steps below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
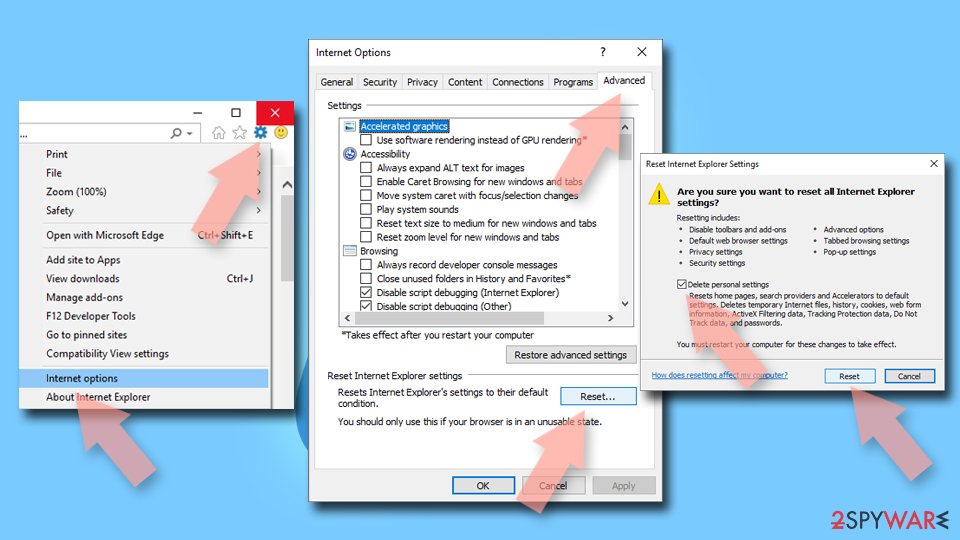
Internet Explorer
- Click on Gear icon > Internet options and select the Advanced tab.
- Select Reset.
- In the new window, check Delete personal settings and select Reset.
![Reset Internet Explorer Reset Internet Explorer]()
Stop the unwanted push notifications
Phishing websites like Tidywarden.store often ask users to enable push notifications as soon as they enter. This practice is common because users may click the “Allow” button by accident and permit the site to deliver notifications. Unsurprisingly, the push notification contents would also contain various dubious advertisements and links to malicious websites. This way, crooks can expand their operations by not only selling software but also receiving revenue from ads.
If you have enabled push notifications on the site, the activity won't stop until you block the URL on the “Allowed” list within the site settings. Note that you can use the instructions for any other website you would like to stop notifications from.
Getting rid of Tidywarden.store ads. Follow these steps
Stop browser notifications
Remove unwanted notifications from Google Chrome (desktop):
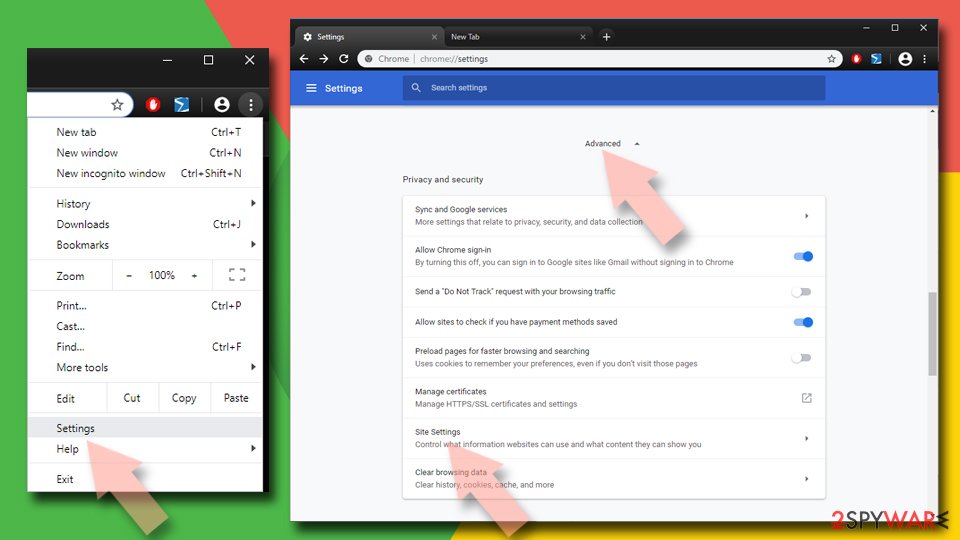
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate Privacy and security section and pick Site Settings > Notifications.

- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.

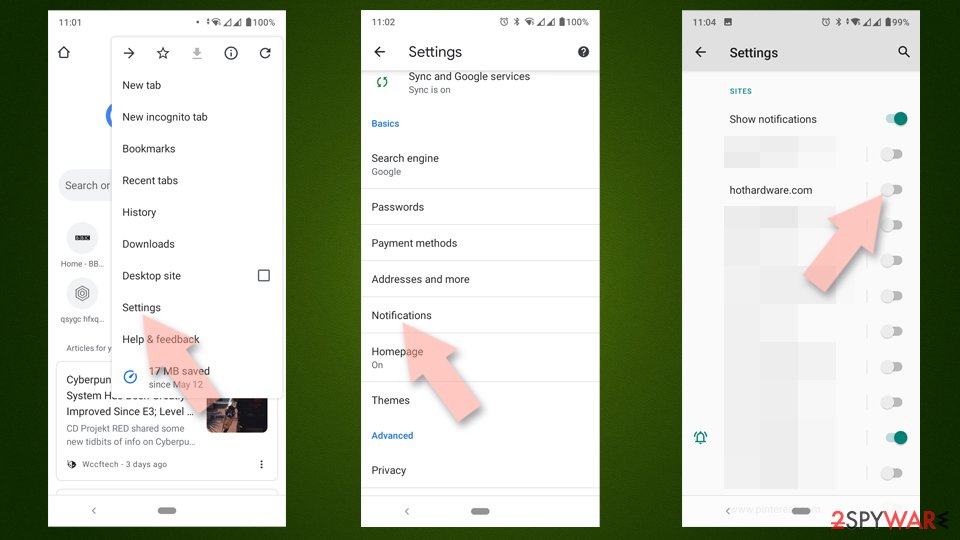
Remove unwanted notifications from Google Chrome (Android):
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).

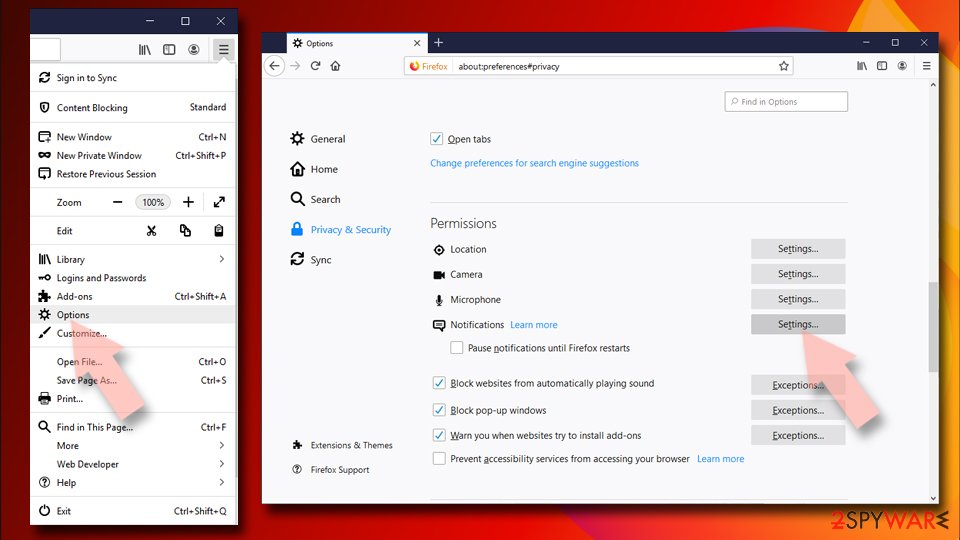
Remove unwanted notifications from Mozilla Firefox:
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.

- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.

Remove unwanted notifications from Safari:
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

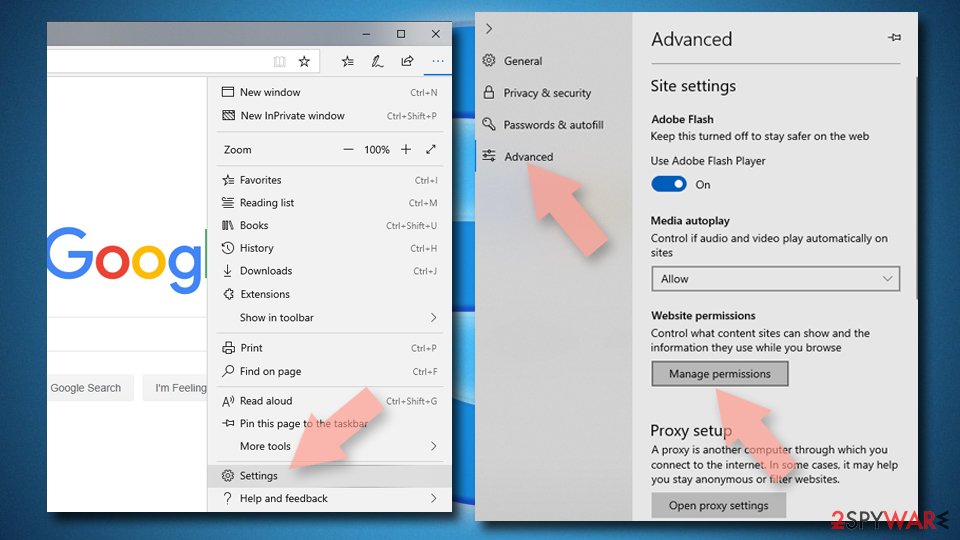
Remove unwanted notifications from MS Edge:
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
- Under Website permissions, pick Manage permissions and select the URL in question.

- Toggle the switch to the left to turn notifications off on Microsoft Edge.

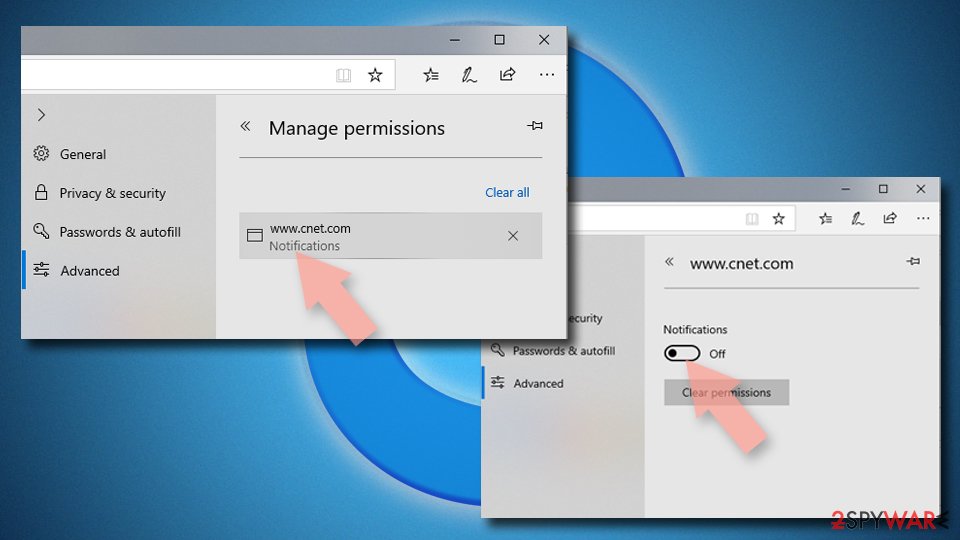
Remove unwanted notifications from MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.

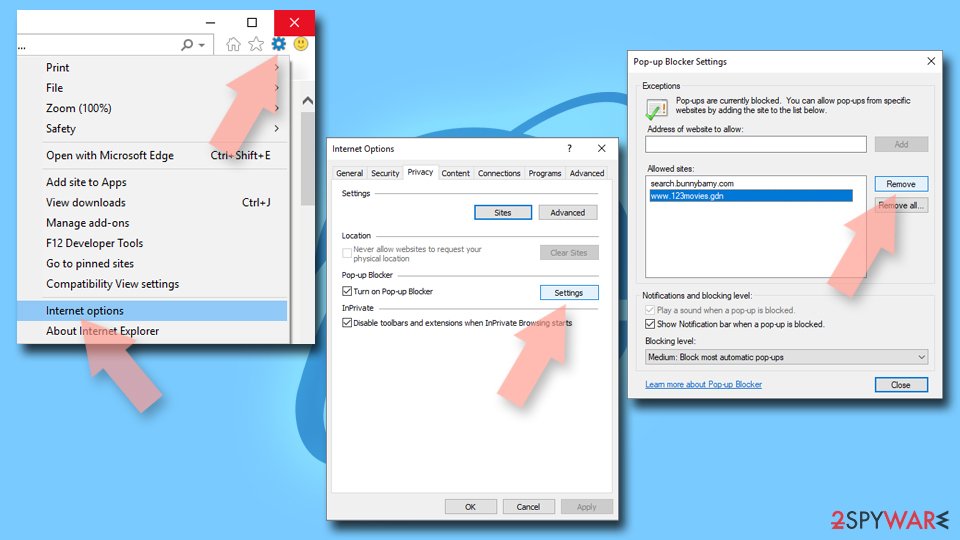
Remove unwanted notifications from Internet Explorer:
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
- Locate web address in question under Allowed sites and pick Remove.

How to prevent from getting adware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Social Engineering. Imperva. Application and data security.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Science Magazine.
- ^ HTTP cookie. Wikipedia. The free encyclopedia.