Tpwrldnws.com ads (fake) - Free Instructions
Tpwrldnws.com ads Removal Guide
What is Tpwrldnws.com ads?
Tpwrldnws.com is a malicious website that tries to scam users
Tpwrldnws.com operates as an online scam aiming to manipulate users into permitting push notifications. This, in turn, grants the website access to display unwanted advertisements directly on the users' desktops. Many users stumble upon Tpwrldnws.com unintentionally, often due to an inadvertent click on a misleading link while browsing the web. Once on the site, they are presented with a craftily designed prompt, coaxing them to press the “Allow” button, which may be disguised as serving another, more benign purpose.
After succumbing to this deception, users experience a barrage of persistent Tpwrldnws.com ads. These can appear unpredictably, irrespective of the user's ongoing online tasks or the software in use. The primary concern with these push notifications lies in the potentially malevolent content they promote. This can range from phishing tactics and fraudulent virus infection alerts to counterfeit prize declarations and various other deceptive materials.
It is imperative that users abstain from engaging with any content or links showcased by this dubious website. For optimal digital safety and protection of personal data, it is recommended to follow specific steps to put an end to these intrusive notifications.
| Name | Tpwrldnws.com |
| Type | Push notifications, pop-ups, ads, scam |
| Distribution | When the user clicks Allow in the push notification, the website has immediate access to send push notifications |
| Symptoms | Pop-ups show up regularly on the screen – these ads often include inappropriate, scam, phishing, or other similar content |
| Risks | You might suffer from monetary losses, install malware or potentially unwanted programs, or disclose sensitive data to cybercriminals |
| Removal | Push notifications can be stopped by blocking the web address of the malicious website via browser settings. Checking the device with SpyHunter 5Combo Cleaner security software is also recommended |
| Other tips | We recommend using FortectIntego to fix any virus damage that might have occurred due to a system infection. The app can also remove various trackers for better privacy |
Staying vigilant is the most important thing when dealing with online fraud
Over recent years, push notification scams have notably gained traction, with their deceptive techniques effectively persuading users to enable push notifications. The primary strategy for these scams, reminiscent of tactics used by sites like Tpwrldnws.com, involves drawing users to their scamming platform. Frequently, these scams exploit weak ad networks and sites with insufficient security protocols.
Many unsuspecting users might find themselves on these scam sites after clicking on links embedded within high-risk platforms, such as torrent download sites. These sites often employ deceptive tactics like misleading “Download” buttons or utilize malicious scripts that redirect users to the scam site upon clicking on unrelated page elements. Given the inherent risks, it's prudent for users to avoid unverified or potentially harmful websites, opting instead for trusted platforms that emphasize user security.
In some cases, the unwarranted redirection to scam sites like Tpwrldnws.com can be attributed to adware stealthily installed on users' devices. Such software often infiltrates systems bundled within legitimate software packages, or through other deceptive means, leaving users oblivious to its existence. The stealthy nature of these schemes highlights the critical need for users to adopt vigilant software installation and browsing practices, thus reducing the likelihood of succumbing to such scams.
Mechanics behind the Tpwrldnws.com deception
Tpwrldnws.com is a masterfully designed snare, often catching users off-guard due to its unexpected appearance. This unexpected encounter marks the inception of a meticulously structured scam aimed at duping users into enabling unwanted notifications on their devices.
Here are some typical misleading prompts showcased by Tpwrldnws.com to coax users into hitting the “Allow” button:
- Click Allow to confirm that you are not a robot
- If you are 18+, click Allow
- Can't play this video! Perhaps your browser doesn't allow video playback. Please click the Allow button to watch the video
- Your file is ready to download – press Allow to continue.
- Click “Allow” to win the prize and get it in our shop!
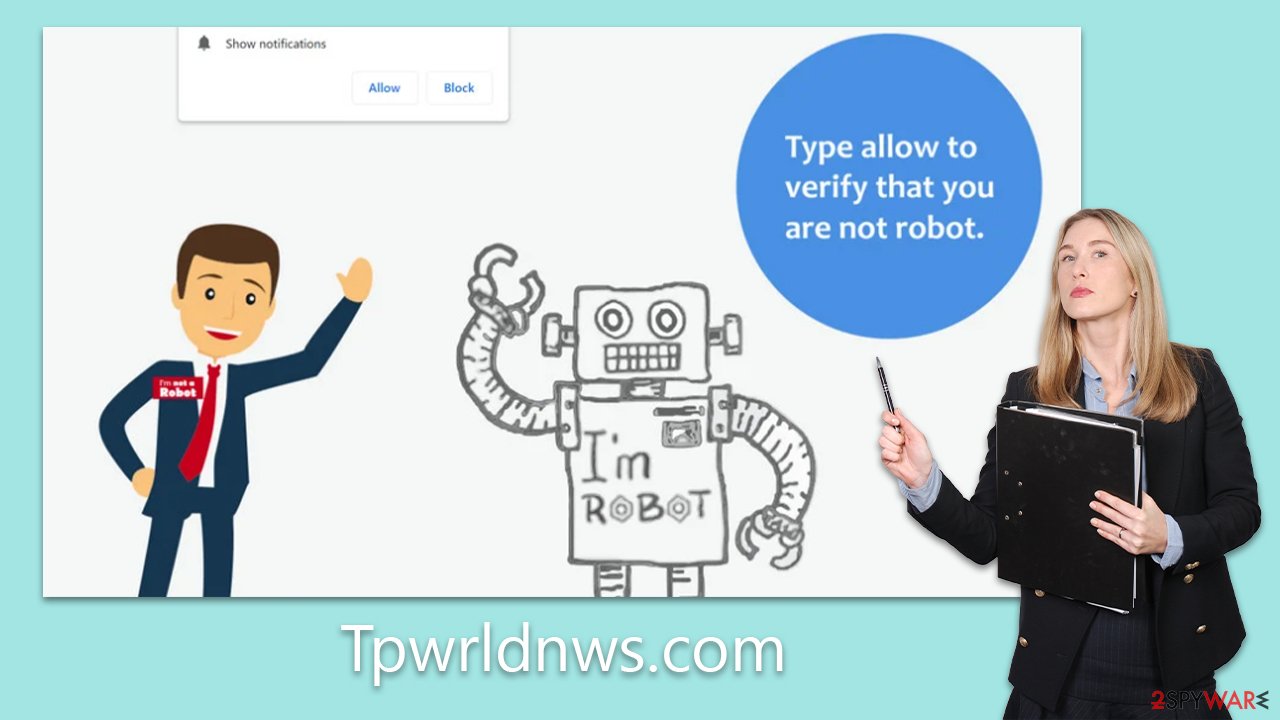
Such messages are strategically crafted to induce users to interact under the impression of a benign request. These prompts tap into a user's innate curiosity, sense of urgency, or perceived obligation to adhere to certain protocols or guidelines. It's vital to recognize that these cues are mere bait to lure users into opting for the site's intrusive push notifications.
Once deceived into pressing “Allow,” users unintentionally grant Tpwrldnws.com permission to dispatch push notifications, often brimming with obtrusive and potentially hazardous ads, straight to their devices. These can emerge unpredictably, interrupting web sessions and putting users at risk of encountering malevolent content. Grasping the mechanics of this deceptive operation is essential for sidestepping potential pitfalls.
Why you should check your system for infections
If you consistently experience being redirected to the website Tpwrldnws.com or similar sites, it is highly probable that your system has been infiltrated by adware. Adware is a type of software intentionally designed to inundate a user's screen with intrusive advertisements, with each click on these ads benefiting the developers.
From its questionable distribution methods to its unscrupulous data tracking practices, this software falls far short of being desirable. The advertisements it delivers can be overly invasive, often displaying misleading or harmful content that is difficult to ignore. Furthermore, the presence of malicious or unwanted programs may remain concealed due to the various techniques employed by the developers.
For example, a harmful application may not appear in the list of installed programs and can exploit existing processes. It may also create scheduled tasks to reactivate malicious processes or modify registry settings to ensure it loads every time the system starts.
We recommend conducting a thorough system scan using reliable anti-malware software such as SpyHunter 5Combo Cleaner, Malwarebytes, or any other efficient option. These programs can swiftly identify and remove all detected threats, providing you with peace of mind. After eliminating all harmful applications, it is essential to clear your browser caches and remove any remaining files. Fortunately, FortectIntego can assist in this cleanup process by autonomously identifying and eliminating these remnants.
Remove the unwanted pop-ups
Eliminating undesirable push notifications is a relatively simple task, even though it may appear intimidating to those who are not well-versed in the procedure. Many users, in fact, may not have encountered the need to disable these notifications until this point, as this feature has been in existence for some time, and it often goes overlooked. To put an end to the inundation of unsolicited advertisements on your screen, you can follow the following steps:
Google Chrome (desktop)
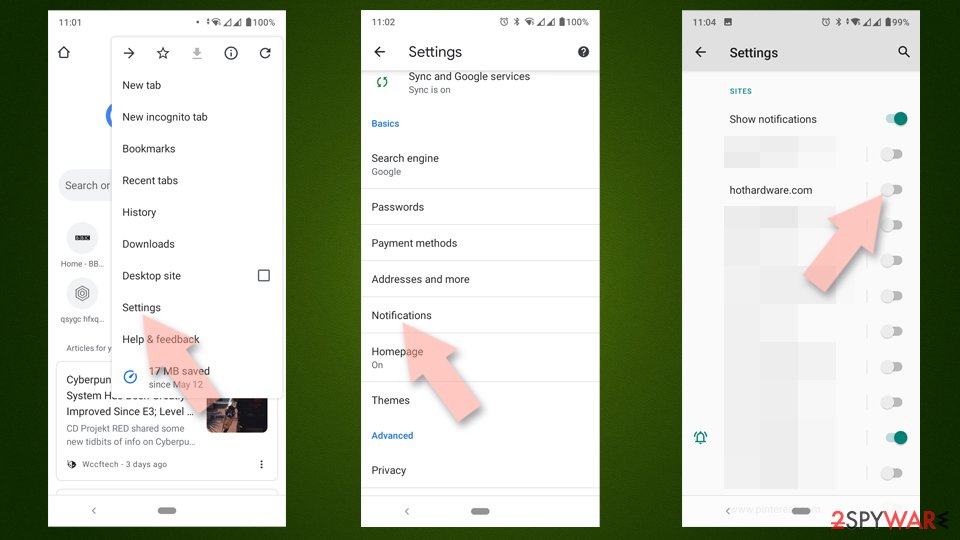
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Google Chrome (Android)
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).
![Stop notifications on Chrome Android Stop notifications on Chrome Android]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
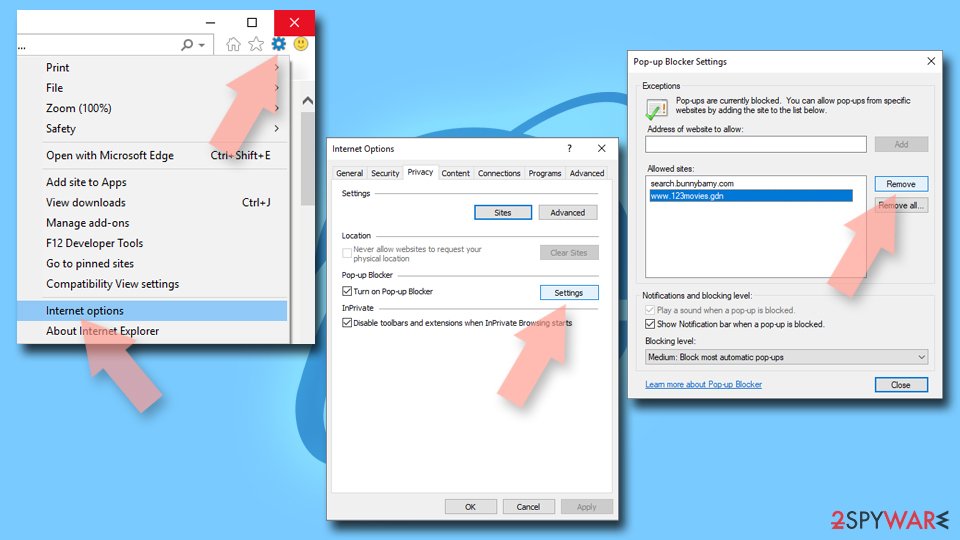
Internet Explorer
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
![Stop notifications on Internet Explorer Stop notifications on Internet Explorer]()
- Locate the web address in question under Allowed sites and pick Remove.
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.