Trg ransomware (virus)
Trg virus Removal Guide
What is Trg ransomware?
Trg ransomware is a dangerous virus that locks all private files on the target Windows system
Trg ransomware is a type of malware that specializes in money extortion. Upon illegally accessing the affected machine, it may penetrate the network and spread laterally, resulting in significant damage. The main goal of the virus is to encrypt all files on the affected system, which would render them useless. One of the most significant ransomware infection symptoms is that all files are appended a particular extension, in this case – “.trg.”
After the malware finishes the data locking process, it immediately drops a ransom note, “КАК РАСШИФРОВАТЬ ФАЙЛЫ.txt” written in Russian, which claims that victims need to write to nikminch@bk.ru in order to restore the locked files. Cybercriminals also claim that if they don't hear from users within a day, they will destroy the decrytpion key.
| Name | Trg virus |
|---|---|
| Type | Ransomware, file-locking malware, cryptovirus |
| File extension | .trg |
| Ransom note | КАК РАСШИФРОВАТЬ ФАЙЛЫ.txt |
| contact | nikminch@bk.ru |
| Family | Xorist |
| Data Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, SpyHunter 5Combo Cleaner or other anti-malware tools should be used |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
The malware family
Provided how effective ransomware operations have been in previous years following a worldwide pandemic, it appears that this pattern will not change anytime soon. As a result, businesses and average PC users should take all reasonable precautions to shield their systems from this terrible threat.
Trg ransomware belongs to the malware strain known as Xorist, which was launched back in 2012. Since then, it has accumulated numerous new versions of the virus infecting thousands of users worldwide. Its previous variants include Flying Dutchman, Bruhnet, Key group, and many others.
Operation
The virus's main objective is to locate and encrypt every non-system file on a Windows computer and any others linked to the infiltrated network. Cybercriminals may occasionally employ management software that is installed locally to attack backup systems as well. Additionally, there are several alternative ways for malware to be installed on the computers of everyday computer users, including software vulnerabilities, spam emails, malicious advertisements, fake updates, etc.
Before proceeding with the data locking process, Trg ransomware makes a lot of changes to the system in order to be successful in its main task: deletes Shadow Copies,[1] creates new tasks, modifies the registry, drops numerous malicious files, etc. After these changes, it uses the TEA[2] or another encryption algorithm (depending on the version) to lock files.
In this variant, malware authors provide a message written in Russian, which reads as follows:
Внимание! Все Ваши файлы зашифрованы!
Для того что бы расшифровать свои файлы напишите нам на почту:
nikminch@bk.ruЖдем ответа сегодня ,если не получим ответа сегодня, после удаляем ключи расшифровки.
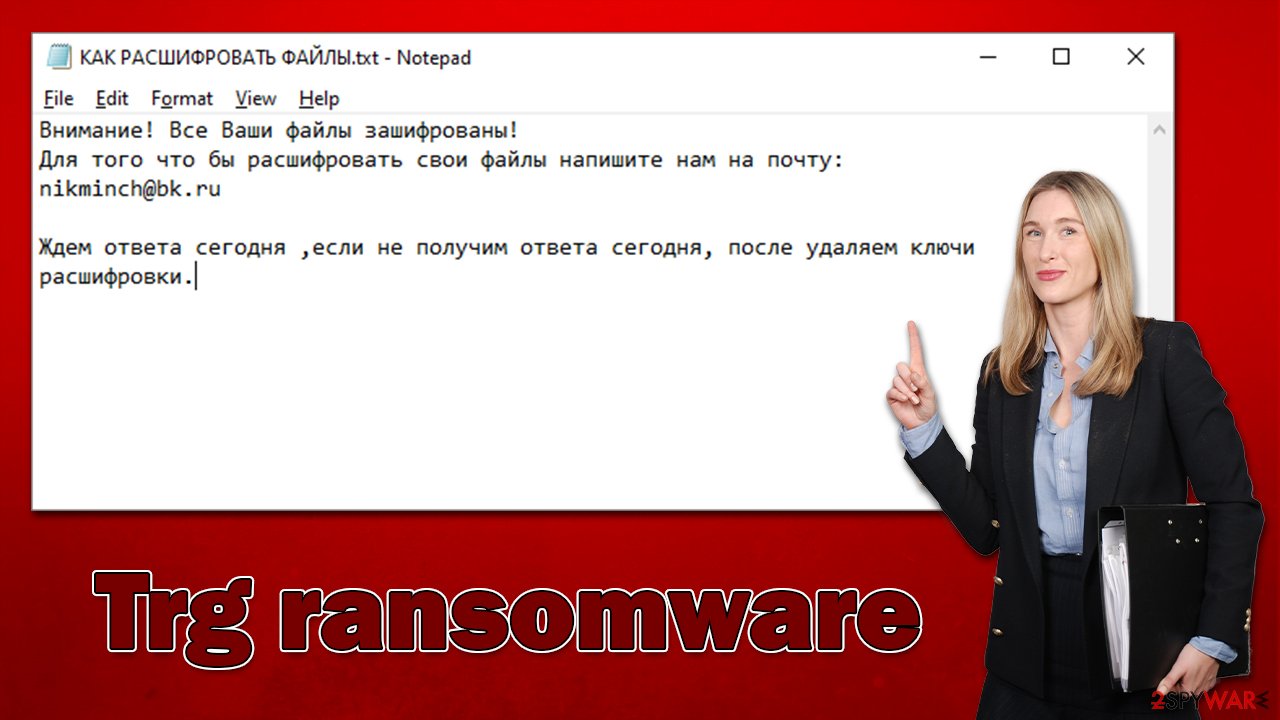
It is claimed that files have been encrypted and that users have a day to contact cybercriminals, or they would simply delete the decryption key, making data recovery almost impossible. This is a simple psychological manipulation at play, where users are given a chance to restore files at a certain timeframe, which makes some people consider paying.
In addition to the TXT file, a pop-up window titled “Error” would also show up, which would include the exact same message. However, those without the Cyrillic installed on their systems would only see gibberish instead of text.
We recommend not communicating with the attackers and not paying the ransom. While data is difficult to recover without the decryptor in cybercriminals' possession, there is simply no guarantee that you'd get what you need after payment. Thus, you would be risking your money as well. Instead, remove Trg ransomware and seek alternative solutions for data recovery we discuss below.
Malware removal and data recovery
Malware may connect to a remote Command & Control server as soon as it has access to the system. This enables attackers to instruct the malware to carry out additional tasks, update itself, or even distribute new payloads. Therefore, before starting the ransomware removal process, it is crucial to disconnect your computer from the internet (and, if appropriate, the network).
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
You may then begin Trg ransomware elimination after disconnecting the computer. For this, you need to use professional security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. Access Safe Mode and run a thorough system scan from there if malware is attempting to obstruct the removal process so that it may stay on the computer for as long as possible. Keep in mind that before doing this, you should upgrade your security software to the newest version.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
We also advise scanning the system with FortectIntego PC repair utility, as some system files might get corrupted due to malware infection. This way, you can get rid of troubles such as BSODs,[3] crashes, errors, and other stability issues without having to reinstall the operating system.
Data recovery
Some users think that .trg files can be brought back after the computer is scanned with security software. Contrary to popular belief, data encryption is actually quite permanent – unless the unique key is applied. Also, encrypted files are not damaged beyond repair, as some people may think.
The encryption technique is, in fact, incredibly secure and cannot be deciphered even by the most advanced supercomputers. However, it does not necessarily mean that the data is damaged; rather, it just requires a special key kept on the attacker's servers.
The greatest strategy to mitigate ransomware attacks is to prepare backups of your personal files. Data that has been encrypted by ransomware may be exceedingly difficult to restore if backups have not been made. If you don't have backups, your options are to employ data recovery software or to wait till a decryptor is available. It should be noted that you should make copies of encrypted data if you don't have functional backups in order to prevent file corruption during the recovery procedure.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Trg ransomware Trg ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders which you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
If some errors are encountered during this process, security experts may exploit them in order to create a decryptor. This has previously happened to numerous prominent ransomware strains, although success is not guaranteed. That being said, we recommend checking out the following websites from time to time:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Shadow Copies and Shadow Copy Sets. Microsoft. Official website.
- ^ Tiny Encryption Algorithm. Wikipedia. The free encyclopedia.
- ^ Chris Hoffman. Everything You Need To Know About the Blue Screen of Death. How-to Geek. Site that explains technology.










