Trojan.Kotver!Ink (Free Guide)
Trojan.Kotver!Ink Removal Guide
What is Trojan.Kotver!Ink?
The peculiarities of Trojan.Kotver!Ink malware
Trojan.Kotver!Ink virus is surely not the kind of malware anyone would like to deal with. It is classified as a trojan horse. Alternatively, Symantec products may label it as a Kovter trojan horse. Generally, this sort of computer of threats causes goosebumps for many users due to their technical peculiarities.
They are capable of passing themselves as legitimate files and then cause a series of severe outcomes; starting from false notifications to reboot the system to locked data. Thus, the capabilities of the infection are also unlimited. However, there is no computer threat that cannot be ceased in one or another way.
| name | Trojan.Kotver!Ink virus |
|---|---|
| Type | Malware, trojan |
| Risk level | High |
| Distribution | File-sharing platforms, fake Flash Player updates |
| Elimination | Use security software to remove this threat permanently |
| System fix | Employ the FortectIntego PC repair tool to fix virus damage |
As you may have already guessed, this trojan might be another variation of notorious Kovter ransomware and Kovter.C trojan horse. Besides the former possessing the characteristics of a trojan, it behaved as a file-encrypting virus as well. Such a phenomenon is not uncommon among trojan horses since their technical features grant them flexibility.
Unfortunately, due to that, some anti-virus applications struggle to detect on time. In the case of current malware, fortunately, major security companies manage to spot it on time before it extracts itself fully. Depending on the antivirus you are using, the trojan might be found as:
- Win32/Kovter.C
- trojan.GenericKD.3112101 (B)
- trojan.Win32.Kovter.evv
- Trojan.GenericKD.3112101
- Ransom_.956D2004
- trojan.GenericKD.3112101
- TR/Kovter.352313, etc.
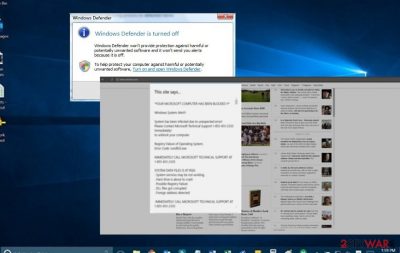
In any case, the malware is not a mere PUP. If you do not own a proper security application, and the virus sneaks into the system, for a while, you might not have the slightest suspicion that a severe threat has occupied the system. After a while, you might notice false alerts of disabled Windows Defender or alerts asking to restart the device.
Needless to say, the PC starts underperforming incapable of opening some applications or simply loading them for several minutes. In addition, you might also get denied do access to certain websites due to false alerts. The reason behind such behavior is simple: the malware collects personal information, including login passwords and banking account credentials.
It may also get access to valuable documents and family photos and leak them to a remote proxy server. It might be just a matter of time when hackers receive such data and misuse it. However, there might be even a worst-case scenario – encrypted data.
Therefore, while you are reading this, make a rush to remove Trojan.Kotver!Ink from the device. You can do it with the help of Malwarebytes or SpyHunter 5Combo Cleaner. Check whether the application is updated and start the scan right away. It is crucial to initiate its removal as soon as possible.
Since the infection might have altered various system files and core system settings, we highly advise scanning your device with the FortectIntego system diagnostics tool. It will ensure that the Registry and other essential system settings are in order.
The distribution of the malware
While you might escape such threats as browser hijackers or adware simply by unmarking unwanted tools during the installation process, speaking of Kovter trojan, things are more complicated. It may disguise itself under an ordinary mini-game or in a torrent file. In short, the trojan might hide anywhere.
Alternatively, some of such threats are dispersed via botnets, networks of machines that are programmed to send out infections. That is why it is crucial to have a powerful updated anti-virus tool. You can also reduce the risk of encountering malware by staying away from suspicious web pages and P2P file-sharing domains.
How can I remove Kotver!Ink trojan?
Needless to say, that manual elimination might not work in this case. Since the virus spreads its registry and executables throughout the system locating them all might be just a futile activity. Therefore, you should entrust Trojan.Kotver!Ink removal to a security application (we recommend SpyHunter 5Combo Cleaner or Malwarebytes). Luckily, the majority of both, anti-virus and anti-spyware, applications are able to deal with this trojan.
Usually, they only take up a couple of minutes to remove a virus completely. Afterward, restart the device for the changes to take effect. Keep in mind these prevention means and keep your security tools in check to reduce the risk of a trojan assault. When your device is virus-free, employ the FortectIntego to repair any damage that the infection caused to system files and settings.
How to prevent from getting trojans
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
