Udacha ransomware (virus) - Free Guide
Udacha virus Removal Guide
What is Udacha ransomware?
Udacha ransomware asks users to contact its authors via Telegram or email
Udacha is a type of malware that belongs to the ransomware category – one of the most devastating threats in the wild. First spotted in late September 2021, it does not seem to belong to any previously known malware family, and its prevalence is yet relatively low. Nonetheless, cybercriminals are actively trying to monetize on those who were unfortunate enough to be infected.
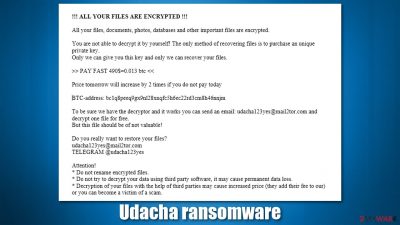
Once installed on the system, the virus uses a sophisticated encryption algorithm to lock all personal files on the Windows system, including documents, pictures, videos, and more. During this process, all files receive a .udacha extension, which also removes their original icons, and blanks are shown. This is a clear indication of a ransomware infection, and all data marked in such a way can no longer be opened or modified.
As soon as the encryption is finished, malware delivers a ransom note titled ReadMe_Instruction.mht, which can be opened using a browser or another application. This item can be placed on a desktop and all the folders where the locked files are located. Its main goal is to inform users about what happened to their computers and files and how to proceed next.
According to the ransom note, victims are required to pay a ransom of 0.013 BTC (an equivalent of approximately $490), a sum that doubles only after one day. Hackers claim that, as soon as the money is sent to a particular Bitcoin address (bc1q8peeq9gx9nl28xnqfc5h6ec22rd3cm8h46nnjm), they will deliver a decryption key that will restore all the files back to their original form, allowing users to use them once again.
Cybercriminals also provide two methods to contact them in case victims want to send an encrypted file for test decryption – udacha123yes@mail2tor.com and Telegram account name @udacha123yes. We strongly advise against contacting or cooperating with ransomware operators, as there is no guarantee that they will keep their promises.
| Name | Udacha virus |
|---|---|
| Type | Ransomware, data locking malware, cryptovirus |
| Malware family | No connections found sofar |
| File extension | .udacha, appended at the end of each personal file |
| Ransom note | ReadMe_Instruction.mht |
| Ransom demand | $490/0.013 BTC, which doubles to $980/0.026 BTC after 24 hours |
| File Recovery | If no backups are available, recovering data is almost impossible. We recommend you try alternative methods, which we list below |
| ransomware removal | Remove ransomware with robust security software such as SpyHunter 5Combo Cleaner |
| System fix | Malware can seriously tamper with Windows systems, causing errors, crashes, lag, and other stability issues after it is terminated. To remediate the OS and avoid its reinstallation, we recommend scanning it with the FortectIntego repair tool |
Why you shouldn't pay
As mentioned at the beginning, there have been no connections to prevalent malware strains found by researchers so far. However, the similarities to a prominent Djvu ransomware are rather undeniable, at least when it comes to the ransom demands. Here is the full message from the attackers:
!!! ALL YOUR FILES ARE ENCRYPTED !!!
All your files, documents, photos, databases and other important files are encrypted.
You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique private key.
Only we can give you this key and only we can recover your files.>> PAY FAST 490$=0.013 btc <<
Price tomorrow will increase by 2 times if you do not pay today BTC-address: bc1q8peeq9gx9nl28xnqfc5h6ec22rd3cm8h46nnjmTo be sure we have the decryptor and it works you can send an email: udacha123yes@mail2tor.com and decrypt one file for free. But this file should be of not valuable!
Do you really want to restore your files?
udacha123yes@mail2tor.com
TELEGRAM @udacha123yesAttention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
In all the versions of Djvu, malware authors also demand $490 for a decryptor, and this sum doubles after a set amount of time. The rest of the message is relatively typical of much other malware out there, so one can only guess whether the authors of the new strain are related in any way. Most likely, they are just copying producers of a very successful ransomware family – Koom, Efdc, Wiot, and many other versions infected thousands.
As it is typical, Udacha virus authors offer alleged test decryption. This is not a sign of goodwill but rather a deceptive method to make users trust the crooks and send them the money. They are talking about security firms allegedly scamming people, all while breaking into people's computers and preying on their misfortune. Simply remember that these attackers are not your friends, and they don't really care about anyone or anything apart from money – it's just business to them.
Therefore, do not trust the hackers and avoid any contact with them. They might send you an infected file (which would result in your PC being infected with even more malware) or never contact you back. This is especially relevant due to to the fact that the ransomware strain is very new, and not much is known about its developers, i.e., no examples of successful decryption from victims. In this scenario, you might not only lose your files but also money, which is the worst.
Instead, you should remove Udacha ransomware from your system using security software and use alternative methods to recover your files. While it is true that no free decryptor is available for this malware, the risk of losing money is just way too great, although it is up to you what you want to do next – just be warned of the consequences. Below you will find the instructions on how to proceed after being infected.
Remove the virus from your PC
While most ransomware self-delete after the encryption is complete, there is no guarantee that this is the case for the Udacha virus. Besides, if your computer already was compromised, there is a chance that there is other malware installed, as ransomware can open a background connection to your computer, which allows crooks to execute remote commands. Ransomware can also drop various modules designed to steal user data or perform other malicious tasks. In some cases, malware will continue encrypting all the incoming files until it is deleted.
In order to remove the infection, you should use SpyHunter 5Combo Cleaner or another reputable anti-malware software, just make sure it is updated before you do so. In fact, security software is your first line of defense when it comes to protection from malware, so you should always have it running in the background, and never ignore its warnings. According to Virus Total, this virus can be detected under the following names:[1]
- Artemis!49FB0E5A3415
- Mal/Generic-R + Troj/Agent-BHTK
- Ransom.FileCryptor
- Trojan:Script/Phonzy.C!ml
- Trojan.GenericKD.37610923, etc.
If malware is interfering with antivirus software, you should instead access Safe Mode with Networking and perform a scan from there. If you need help on how to do that, check the instructions at the very bottom of this post.
As soon as you are done with malware elimination, you should employ a PC repair tool FortectIntego to take care of potentially broken system files, which might cause Windows to crash or show errors. The app can fix registry errors and replace damaged system files with brand new ones to ensure that the OS won't have to be reinstalled.
How to recover .udacha files?
Many of the infected people have no clue about what ransomware actually is or how it works. Other malware, such as data-stealer, can also be devastating when it comes to personal safety (it might steal your passwords, logins, Social Security Number, etc., resulting in identity fraud or theft), it can be wiped out with anti-malware tools.
However, when it comes to ransomware, people get surprised when they find that a scan with anti-malware does not restore their encrypted files. This is to be expected, as security software is not designed for that – a special decryption tool designed for this particular ransomware needs to be used in order to be successful in this process. In short, Udacha removal will not bring your files back, and they will remain locked.
So, what options do you have? First of all, you need to decide whether you want to pay for a decryption tool, which we are strongly against. Instead, you should make a copy of the locked data – use an external HDD, a flash drive, or back up on a virtual drive. Next, try the following:
1. Use recovery software
It is not immediately possible to tell whether third-party recovery software will work for you or not, as it depends on many factors. The best thing to do is to try it out yourself:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Udacha ransomware Udacha ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
2. Look for a decryptor
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Additional tips
If you have been a victim of ransomware, it must be devastating – important work documents or personal photos might have incredible value. You are not alone – there are thousands of users who become victims every day, and most of them haven't even heard about what it actually is. Unfortunately, malware infections cannot be undone, although what you can do is improve your security practices to avoid a similar scenario in the future.
After you remove malware from your system, you could contact your local authorities and report the incident, providing as many details as possible. These reports are valuable, as the whole operation of the crooks might be dismantled, and keys to victims released[2] in the future – this happened many times before. Here are a few links you could use:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

Additionally, make sure you backup your files going forward. While anti-malware is your first line of defense against the infection, a backup can always save you from the devastating consequences of ransomware. Below we provide tips on how to do that on cloud services such as Google Drive or OneDrive.
Finally, be more critical of suspicious files, such as the ones that randomly get downloaded once accessing a website. Never visit torrent or similar websites, as these are commonly used by cybercriminals to spread malware (many users ignore warnings from security software believing that it is a false positive[3] once a crack or a pirated installer is flagged). Update all your software on the system, and never allow macros on MS Office documents (acquired from a suspicious email) to be run on your system.
Getting rid of Udacha virus. Follow these steps
Access Safe Mode to remove malware from Windows
If malware is not letting you use antivirus in normal mode, access Safe Mode and perform a full system scan from there.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.
- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.

Once you reach Safe Mode, launch SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable antivirus, update it with the latest definitions, and perform a full system scan to eradicate malware and all its malicious components.
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ f2a155473c06ecad973676f1e2a8d228ab4a8adf32a87477c716f31fddf6cbaf. Virus Total. File and URL analysis.
- ^ Chris Brook. Keys for Dharma Ransomware Released. ThreatPost. The first stop for security news.
- ^ Cybersecurity 101: What You Need To Know About False Positives and False Negatives. Infocyte. Data protection and incident response.





















