Windows Accelerator Pro - Mar 2021 update
Windows Accelerator Pro Removal Guide
What is Windows Accelerator Pro?
Windows Accelerator Pro – a malicious program designed to trick users into spending money on it
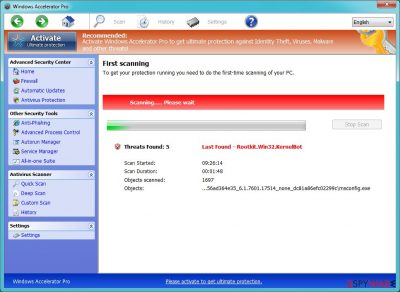
Windows Accelerator Pro is a dangerous program that mimics real antivirus software. It intends to deliberately mislead victims into believing that their systems are infected with various malware and are in exceptionally bad shape, regardless of the real situation.
This is all done to manipulate users and make them buy a licensed version of Windows Accelerator Pro. However, you should never do it. Not only will you be giving your money away to scammers, but you will also remain unprotected from real threats that could seriously harm your computer and compromise your personal safety.
| Name | Windows Accelerator Pro |
| Type | Rogue antivirus, malware |
| Distribution |
|
| Alleged functionality | It attempts to mimic real anti-malware software by showing fake scan results – users can often find hundreds of entries after each of the scans |
| Dangers | Monetary loss due to non-existent program's functionality, further malware infection due to inadequate system protection |
| Elimination | While you can attempt to uninstall the app manually, it is likely not going to work. Instead, perform a full system scan with a real antivirus program |
| System fix | Windows Accelerator Pro can damage Windows system functions. To repair the OS automatically after the infection is eliminated, we recommend using FortectIntego |
As soon as it infiltrates computers, it displays fake alerts that all announce different problems. Of course, these problems are invented and seek to steal people’s money. Beware that Windows Accelerator Pro can show up on your computer out of nowhere because it, just like any other rogue anti-spyware, is distributed with the help of Trojans.
In other words, it is rogue application that should never used as means for your system to be protected from threats such as:
- Ransomware
- Trojans
- Rootkits
- Adware
- Backdoors, etc.
To make it look like the app is legitimate, Windows Accelerator Pro tries hard to imitate legitimate Windows UI components, such as links on the side panel, as well as fonts and other attributes. This is a known social engineering technique designed to invoke users and make them believe that the app is genuine. It is not – it is a simple scam.
To make matters worse, the virus makes various changes to the Windows operating system – not in a good way. Even after removal, these changes might cause severe performance and stability issues. Thus, if you encounter them, we recommend you try FortectIntego to fix them.
According to experts who researched this threat:
This Trojan modifies the system and helps Windows Accelerator Pro start its work every time users reboot their computers.
As a result, the victim begins noticing fake alerts that promote the program’s full version. If you don’t want to support scammers and lose your money, stay away from this rogue!
To remove the virus, you should perform a full system scan with anti-malware software, such as SpyHunter 5Combo Cleaner. While manual elimination is possible, it is important to delete all malware-related components from the system.
Rogue antivirus spreads as a Trojan
Windows Accelerator Pro can infect your computer with a help of Trojans. These Trojans hide inside insecure websites, spam or fake alerts that offer downloading useless updates.
So, in order to avoid them, you should stay away from these things and also make sure that your PC is protected by the latest versions of anti-virus and anti-spyware. As soon as trojan infiltrates computer, it starts imitating the work of legitimate antivirus program: it shows how it scans computer and then ‘detects’ tens of different viruses. For example:
Error
System data security is at risk!
To prevent potential PC errors, run a full system scan.
Be sure that these problems are invented and the only real virus is Windows Accelerator Pro. If your PC is infected, follow a guide below and remove this virus from the system.
Remove Windows Accelerator Pro using a robust anti-malware tool
If you want to remove Windows Accelerator Pro, you should scan your computer with updated anti-spyware and remove malicious files. If you can't launch any of them, use these instructions:
- Reboot your computer to Safe Mode with Networking. Just reboot your PC and, as soon as it starts booting up, start pressing F8 repeatedly.
- Login as the same user as you were in normal Windows mode.
- Now click on IE or other browser and select 'Run As' or 'Run As administrator', enter your Administrator account password (if needed).
- Download SpyHunter 5Combo Cleaner or another anti-malware on your desktop. Launch it to kill the malicious processes and remove its files.
Finally, to fix virus damage and ensure that the Windows system is not damaged, scan it with FortectIntego.
How to prevent from getting rogue antispyware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
