Windows Security has been Compromised (Free Instructions) - Tech Support Scam
Windows Security has been Compromised Removal Guide
What is Windows Security has been Compromised?
Windows Security has been Compromised is a fake message trying to trick people into purchasing useless security tools
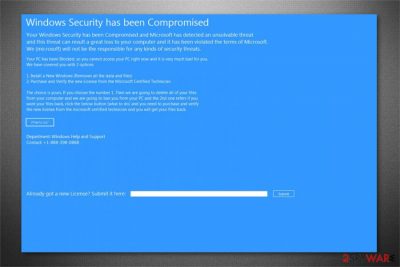
Windows Security has been Compromised is a deceptive notification which appears on the screen during browsing sessions and prevents users from using their browser. The screen-locking feature allows tricking people into believing that their computers are infected, and they must take immediate actions. For that, cybercriminals offer to purchase a new Microsoft License via an inbuilt button on the pop-up[1] window. However, experts note that your system is not infected and you should not click on any content in the message since it is a technical support scam[2].
| Name | Windows Security has been Compromised |
|---|---|
| Type | Malware |
| Danger level | Medium. Includes a screen-locking feature |
| Distribution | Spreads via bundling method |
| Symptoms | Locks the screen and displays a fake message saying that Windows security has been compromised |
| Indicated number | +1 888 398 0888 |
| Removal | Get a professional malware removal software to get rid of “Windows Security has been Compromised” virus. Later, we advise scanning the computer with FortectIntego to fix the damage |
Windows Security has been Compromised message indicates that an adware program sneaked into your system. Usually, you might unconsciously install it while installing third-party applications from unreliable developers. As soon as it settles, this ad-supported program modifies browser settings to redirect users to a website showing this fake notification.
Here is the fraction of Windows Security has been Compromised alert:
Windows Security has been Compromised
Your Windows Security has been Compromised and Microsoft has detected an unsolvable threat and this threat can result a great loss to your computer and it has been violated the terms of Microsoft. We (microsoft) will not be the responsible for any kinds of security threats.
Your PC has been Blocked, so you cannot access your PC right now and it is very much bad for you. We have covered you with 2 options
Furthermore, the criminals behind Windows Security has been Compromised virus claim that users and re-install Windows but that would lead to data loss. They indicate another option — purchase a new license key by clicking on “What to do?” button below the message.

We want to warn you that “Windows Security has been Compromised” message is a scam, and you should never fall for this fake technical support trick. Your computer is not infected, and you do NOT need to pay for a supposedly new Microsoft license key. In fact, you only need to uninstall the adware redirecting you to this message.
Keep in mind that you should NOT call via the indicated +1 888 398 0888 number either. Usually, cybercriminals ask to give remote access to the computer to clean the infections allegedly. In reality, hackers install numerous potentially unwanted programs (PUPs) to force you to keep using their services and paying.
Our experts say that the easiest way to remove Windows Security has been Compromised message is download and install a robust antivirus software. You just need to scan your computer and let it detect all components which are related to the adware and other PUPs.
Additionally, a wise decision is to run a full system scan with FortectIntego after Windows Security has been Compromised removal as it can help you eliminate virus damage and restore any modifications that were previously made.
Adware programs are bundled with freeware to help them spread
Most commonly, adware and similar potentially unwanted program (PUPs) come in a bundle with freeware so users might not notice how it was installed on their computers. Therefore, it is essential to pay close attention during the installation of third-party applications if you want to keep your system safe.
For that, you should reject the Quick/Recommended installation mode once it is offered. Instead, pick Custom/Advanced and attentively follow the steps. Usually, adware appears as a pre-selected checkmark that should be de-selected. Always look for those additional components and reject them.
Learn how to get rid of Windows Security has been Compromised message
As we have already mentioned, you should start Windows Security has been Compromised removal by downloading and installing a professional security tool. You will find our recommended ones below this article. Although, feel free to use any reliable antivirus of your choice.
However, you can also remove Windows Security has been Compromised manually. This method requires specific IT knowledge. Thus, experts[3] recommend it only for advanced computer users. Check the guidelines presented at the end of this article.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Windows Security has been Compromised. Follow these steps
Uninstall from Windows
Get rid of suspicious programs from Windows OS first:
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
You have to delete unverified entries from Mozilla Firefox and reset your browser.
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Get rid of Windows Security has been Compromised message from Chrome by uninstalling unknown extensions.
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Windows Security has been Compromised registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.


















