Winxvykljw ransomware (virus) - Recovery Instructions Included
Winxvykljw virus Removal Guide
What is Winxvykljw ransomware?
Winxvykljw ransomware is a dangerous computer virus that might result in personal file loss
Winxvykljw is a malicious Windows program designed by cybercriminals for money extortion purposes. First discovered in the wild in the second half of September 2022, the virus began attacking computers just like any other variant of Snatch – a well-established malware family it belongs to.
The main danger of a ransomware infection is that its impact on the files might be permanent. Upon infiltration, the virus would scan the affected system for documents, databases, pictures, and other personal files and, once found, would lock them with a potent encryption algorithm (usually AES),[1] which appends each of them with the .winxvykljw extension. This data can no longer be altered or even opened, making it essentially useless.
It is worth noting that ransomware does not corrupt files: it uses a complex key unique to each affected computer. This key is stored on cybercriminals' servers, and is only accessible to them, which makes it a perfect opportunity for money extortion.
According to the ransom note HOW TO RESTORE YOUR FILES.TXT, it is claimed that victims should write an email to Toni.morrison13@tutanota.com.com or Frank.Sinatra1010@protonmail.com to negotiate the recovery fee, to be paid in bitcoin. We do not recommend contacting cybercriminals as they may never fulfill their promises. Rely on alternative methods for data recovery – we provide them below.
| Name | Winxvykljw virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .winxvykljw appended to each of the personal files |
| Ransom note | HOW TO RESTORE YOUR FILES.TXT |
| Malware family | Snatch |
| File Recovery | The only method to recover files is through data backups. If such is not accessible, or if it has also been encrypted, your options for recovery are extremely limited, although we recommend trying them |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Malware can damage system files upon entry, which, if not repaired, may cause all sorts of stability issues, including crashes, errors, slowdowns, etc. To remediate the device, we recommend using the FortectIntego repair application |
Ransom note analysis
Most malware is rather sneaky: they use deceptive infiltration methods to make an unexpected entry and then often run silently behind users' backs, harvesting personal data or performing other malicious tasks in the background. Ransomware is quite a bit different in that regard.
While ransomware does spread using similar distribution methods as any other malware (spam emails or infectious torrent installers, for example), it makes it clear to users that what happened, happened within a message that's delivered in a text file or a pop-up window. In some cases, ransomware also changes the background wallpaper to make users see what has actually happened to their files.
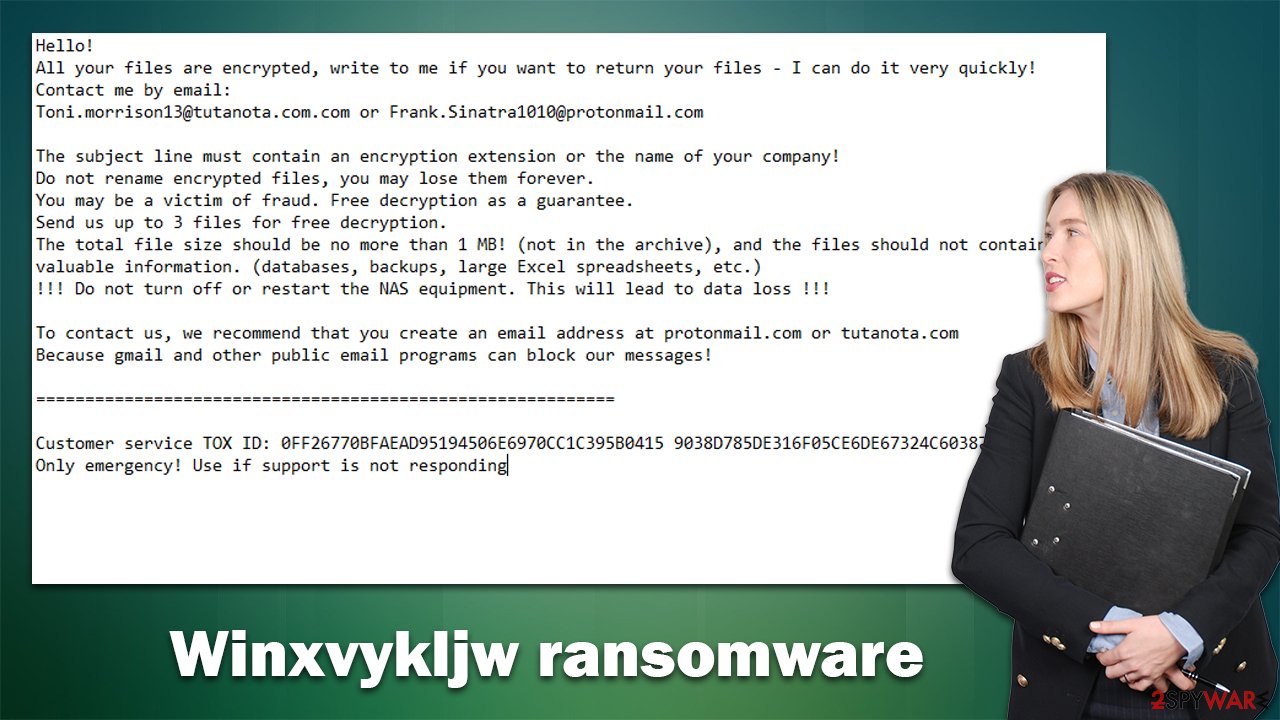
Ransom notes are very important for any cybercriminal gang running an illegal ransomware business – it allows them to provide a lot of detailed information to users, explaining what the demands are and what to do next to fulfill them. In the case of the Winxvykljw virus, users are presented with the following message that can be opened using Notepad:
Hello!
All your files are encrypted, write to me if you want to return your files – I can do it very quickly!
Contact me by email:
Toni.morrison13@tutanota.com.com or Frank.Sinatra1010@protonmail.comThe subject line must contain an encryption extension or the name of your company!
Do not rename encrypted files, you may lose them forever.
You may be a victim of fraud. Free decryption as a guarantee.
Send us up to 3 files for free decryption.
The total file size should be no more than 1 MB! (not in the archive), and the files should not contain valuable information. (databases, backups, large Excel spreadsheets, etc.)
!!! Do not turn off or restart the NAS equipment. This will lead to data loss !!!To contact us, we recommend that you create an email address at protonmail.com or tutanota.com
Because gmail and other public email programs can block our messages!===========================================================
Customer service TOX ID: 0FF26770BFAEAD95194506E6970CC1C395B0415 9038D785DE316F05CE6DE67324C6038727A58
Only emergency! Use if support is not responding
The ploy of hackers is rather simple: their main goal is to convince victims that they are their best option to go about this. While it is true that only they possess the decryption key, it is not worth trusting them. Ransomware developers never care about users or their files, hence they might never provide the decryptor after payment.[2] This way, you risk losing your money in addition to your files.
We recommend you remove Winxvykljw ransomware instead and use alternative methods for data recovery. Please bear in mind that the order of the actions is important, so make sure you follow the instructions below.
Remove malware from the system
While some ransomware tends to self-destruct after completing its main task of data encryption, this is not always the case. The moment ransomware infiltrates a system, it creates a link with a remote Command and Control[3] server, which criminals can use as a central location to store encryption and decryption keys. They can utilize it to remotely send commands, such as stealing user data or even sending more harmful payloads.
So, you first need to turn off this connection by unplugging your computer from the network and the internet. To do this, either use the WiFi icon in the taskbar or unplug your Ethernet cable from the computer. Alternatively, you can disconnect multiple computers at once as follows:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Once you're certain the system isn't linked to any networks, run a thorough system scan using powerful anti-malware software. Any secondary payloads that may be present can be found and eliminated from the system using tools like SpyHunter 5Combo Cleaner or Malwarebytes. Besides, security software is your number one protection from incoming ransomware and other malware attacks.
Recover your data
Files that have been encrypted cannot be read without a key, which is frequently kept on a server that is run by hackers. They can then determine which key decrypts which victim's data using the user ID. Since each victim is given a unique key, there is no universal password in this scenario.
Data encryption and virus infection are two distinctive occurrences that require independent treatment. This means that by using antivirus software to check your computer, you will get rid of any potentially harmful files that might otherwise stay active and encrypt any incoming documents, for example. At the same time, .winxvykljw files would remain locked.
Instead of communicating with the attackers, we recommend you use alternative methods of data recovery, and while they may not work for everyone or restore all the encrypted files, it is always worth trying. Before proceeding, you should always make copies of encrypted files if you have no working backups available.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Winxvykljw ransomware Winxvykljw ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Security researchers' work may potentially result in the creation of decryption tools for certain ransomware variants. In some cases, reputable security companies help competent authorities seize the servers of criminal organizations and make their keys available to the public. The following links will help you to find what you're looking for (keep in mind that decryptor creation is never a guarantee):
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

System repair
Once malware gains access to the system, it ceases to function as it once did. Some files may be changed or even damaged during virus cleanup or malware operation. Some users may therefore begin experiencing system crashes, software malfunctions, and other technical problems. Therefore, we recommend you repair damaged system files with a repair tool as follows:
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Encryption. Investopedia. Sharper insight, better investing.
- ^ Lawrence Abrams. UltraCrypter not providing Decryption Keys after payment. Launches Help Desk. Bleeping Computer. Cybersecurity and Technology News.
- ^ Command and Control [C&C] Server. Trend Micro. Security blog.












