Your iPhone has been compromised - 2020 update
Your iPhone has been compromised Removal Guide
What is Your iPhone has been compromised?
Your iPhone has been compromised is an iPhone scam that directs users to insecure software downloads
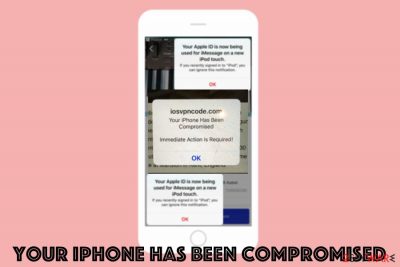
Your iPhone has been compromised is the scam that delivers fake alerts to obtain personal information (credit card credentials, account logins) or direct users to bogus software download sites. This is achieved by scaring people into revealing their information for scammers behind these alerts. The fake alert can be classified as a part of the broader iPhone virus family which targets mobile Apple devices.
There are many versions and tactics, but this one is based on the social engineering attack method.[1] Many users even complained about the campaign that shows fake alerts and causes tons of redirects to questionable sites and also installation of rogue tools and applications.[2] People stated that misspelling the website's URL could cause these redirects. Under no circumstances should you click on Your iPhone has been compromised scam buttons, provide personal details, or download the suggested software.
| Name | Your iPhone has been compromised |
|---|---|
| Type | Rogue websites |
| Category | Scam |
| Version of | iPhone/Apple virus |
| Affects | Apple devices |
| Distribution | Deceptive websites, insecure downloads |
| Elimination | Clean the machine with anti-malware tools. You can remove message with a mobile antivirus application |
Your iPhone has been compromised scam campaign delivers fake pop-up messages with system alerts stating that the device is infected by malware or has issues regarding the system. It shows up on the browser, in most cases, and the message redirects to other suspicious pages with possibly malicious content, where the user can get even more dangerous malware. The full message reads as follows, although it can slightly vary:
iosvpncode.com
You iPhone Has Been Compromised
Immediate Action is Required!
OK
When you encounter Your iPhone has been compromised pop-up, you can try to exit the browser window and avoid any infiltration of the cyber threats like PUPs or malware. In some cases, users claimed that they were unable to close down the alert. In such a case, you should press the circular Home button and swipe up – this will close down the browser.
However, when these pop-ups and redirect appear constantly, it is a sign of an adware-type infection that could be running on the OS. You should note that having anything similar to this virus on the device can lead to more damage than you think. In most cases, scammers behind these campaigns mainly focus on getting user credentials and other valuable data.
Your iPhone has been compromised message is a hoax, and this pop-up is not from the official Apple support. The alert says that you need to take immediate action – this is a persuasion technique that is commonly practiced in online scams. Experts [3] recommend closing down the page displaying the popup and not interacting with it in any way. Clearing cache and browser data can also help you to remove iPhone has been compromised and similar messages for good.
Another tip that we can give you when dealing with this virus is to react as soon as possible, so all the potentially unwanted applications are eliminated comprehensively. For that, you should use anti-malware tools such as SpyHunter 5Combo Cleaner or Malwarebytes and scan the device thoroughly. For system fixing, we recommend FortectIntego.
While Your iPhone has been compromised scam is most commonly encountered by accident (for example, after clicking a suspicious link on another site), adware apps are known as the culprits of persistent redirects. Therefore, if you noticed that suspicious notifications and redirects happen to you more often than not, you should be concerned. In most cases, potentially unwanted applications get installed without asking for direct permission and commonly come in a software bundle.
Precisely for this reason, you should choose your download sources carefully. Apple usually warns users about apps that are not approved by the App Store, so you should consider that every time.
Nevertheless, you can delete this virus from the machine entirely with proper anti-malware tools. You need to employ an antivirus program, run a full system scan, and follow suggested steps that allow thorough PUP elimination.
You may additionally need to fix settings changed by this Your iPhone has been compromised virus or clean the machine further if the AV tools cannot detect all infections. However, you also need to check all the web browsers for additional unwanted content that PUPs can install behind your back.
Pay closer attention to software sources and installation setups
You can quickly get cyber infections from deceptive advertising sites, commercial redirects, and pop-ups that appear on the screen out of nowhere. Unfortunately, the only thing that these scams need is visits and views on their sites, so you get often tricked into clicking on pop-ups, banners.
When you get updates, applications, and software, choose the official provider and developer site because only this way you can be sure that there are no PUPs added besides the application you need. Also, if you choose Advanced or Custom installation options, you can see included programs and remove unwanted or suspicious ones.
Pay attention to all the processes and the legitimacy of the pages you visit. Also, remember that official Apple support or any software provider doesn't send such alerts directly to the screen. Don't fall for such scams.
Eliminate the virus and other possible threats
You cannot be sure that you avoided infiltration of the additional PUP or a malicious program. However, you can check if the system is infected and remove Your iPhone has been compromised alerts at the same time. For that, you only need an automatic anti-malware program that can scan the system thoroughly and clean all the possible threats.
Automatic removal using AV tools gives the advantage of seeing all the issues and programs or files that are useless or even cause damage to the machine. During a full system scan, the anti-malware program indicates and detects PUPs, malware, system errors and cleans your device entirely.
To Clean Safari on your iPhone and prevent further scam messages in the future, perform the following actions:
- On your iPhone, pick Settings
- Select Safari
- Tap on Clear History and Website Data
- To confirm, select Clear History and Data.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Your iPhone has been compromised. Follow these steps
Delete from macOS
Make sure to check all the crucial parts of the system and remove Your iPhone has been compromised scam
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Your iPhone has been compromised registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting mac viruses
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Social engineering. Wikipedia. The free encyclopedia.
- ^ Can an iPhone be hacked? Weird pop up came up on safari.. Reddit. Online community forum.
- ^ Dieviren. Dieviren. Spyware related news.












