IPhone virus - Jan 2021 update
iPhone virus Removal Guide
What is iPhone virus?
iPhone virus is a group of dangerous apps that attack iOS devices and trigger their unusual behavior

iPhone virus – the mobile threat that can get downloaded from malicious sources and installed inadvertently. Even though iOS's sandbox structure should prevent these malware attacks and hackers from accessing the applications and devices, there are some features that allow bypassing various security measures and malicious pieces of software manage to find the way on users' machines.
Hackers cannot (or very hardly) break the iOS itself, so the most common strategies of malicious actors are to crack developer kit and gain the ability to redirect victims to dodgy sites. Misbehaving applications and jailbroken iPhones can be the main reasons for the infection, so you should backup working files before you restore the device to factory settings if you have used a jailbreaking tool. Altering settings can be the worst thing that malware triggers, so you can repair the system and security of the machine going through them properly.
iPhone virus is a malware designed to attack iOS users. While users are still convinced that hackers haven't launched malware for iOS, cybercriminals keep presenting malicious software for macOS and iOS. Of course, the percentage of Mac virus is still much lower than the one designed for Windows and Android. However, there is no doubt that the amount of malware directed towards Apple users has been increasing dramatically; thus, denial of the problem will not solve it. Despite Mac OS being loved by many users, it is still far less popular than Windows OS.[1] Therefore, the amount of malware created to abuse this operating system is also smaller. However, people show to take all precautionary measures to prevent the iPhone virus on their device.
| Name | iPhone virus | ||||
| Versions | Redirect virus | Browser hijacker | Tech support scam | Ransomware | Spyware |
| Examples |
|
||||
| Danger | Medium | Low | Medium | High | High |
| Distribution | Malicious sites, bundling | Malicious sites, bundling | Malicious sites, bundling | Spam, illegal software | Phishing |
| Symptoms | Redirects to dubious websites, sponsored ads, etc. | Fake ads offering to contact the fake tech support | System changes, redirects to dubious websites, sponsored ads, etc. | Encrypted files, the ransom note demanding a certain fee |
Excessive spying
|
| Removal | Use FortectIntego to identify malicious files on the system. In rare occasions, you may need to opt for factory reset, so the device is completely restored to a previous state | ||||
iPhone malware may be an extremely rare issue since there is a general belief that macOS and iOS are immune to cyber threats. There are many issues with third-party software and content that are distributed online. There is no easy way to control the traffic and the possible risks when it comes to the material on random online sources.
Apple devices have restrictions when it comes to apps that can be downloaded, so iPhone virus is not the one that can be easily caught. However, jailbreaking[2] can help to bypass these issues, so you download anything you want. But such behavior also triggers issues with unwanted installations and malware infections.
Mac and iOS users are convinced that their devices are immune to iPhone virus due to a few reasons:
- limited access to system files;
- fragmented OS;[3]
- restricted permit for third-party apps.
Unfortunately, iPhone devices are just as vulnerable as other devices. If you are not paying appropriate attention to your browsing habits and safe browsing practices, you can get infected with ransomware, adware, or a browser hijacker within several hours of unsafe browsing. The consequences of getting a virus on the iPhone can vary from finding your search preferences mixed up to discovering that your important data was locked.
Let us review the types of malware below. If you are wondering what should you do to perform iPhone virus removal, jump to the last paragraph of this post.
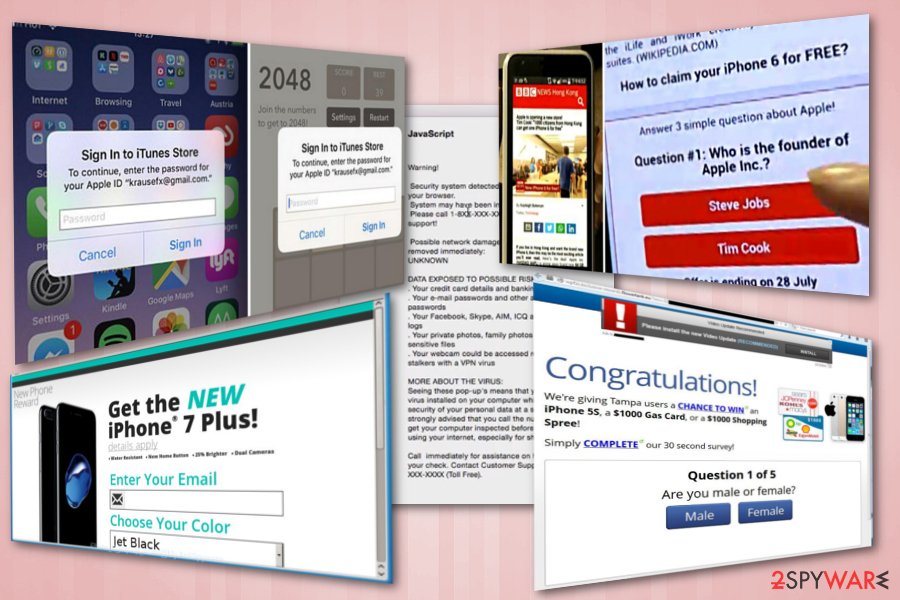
Apple products are targeted by potentially unwanted programs
At the moment, troublesome adware programs and scripts are one of the most prevalent PUPs on the Internet. However, while Windows users report about unstoppable ads on their web browser, iPhone users report about suspicious tech support alerts.[4][5]
Typically, these tech support scams inform their victims that their device was occupied because of a virus that is capable of stealing their data. Additionally, such an iPhone virus offers to contact the special tech support team via a certain phone which is nothing but a straight way to reach a group of hackers trying to swindle people's money. Note that Apple does not display such notifications in random messages nor displays a phone number offering its users to contact its team.
We should not also forget a common online scam that offers iPhone devices for free.[6] In this case, scammers collect people's personal information by involving them in nonexistent surveys and contests.
Frustrating pop-ups is yet another common form of the iPhone virus. Since they function via a web-script planted into the browser, they might bother you from time to time popping up or bother you every time you launch the browser. Some of them happen to be quite persistent as you need to shut down Safari by force.
Browser hijackers also exist for Apple users. One of the recent samples is search.stuckopoe.com hijacker. While it looks like an ordinary search engine, it collects non-personal information about its users and uses it for “service improvement” purposes. While it displays pop-ups once in a while, the most negative aspect is related to its elimination.
When you enter the page with removal instructions, it offers to install the elimination tool called Uninstaller.dmg file. The problem is that it is infected with macOS:Genleo-BQ adware. If you use a standard version of Safari on your iPhone, beware of such hijackers. To remove viruses from iPhone, you might need to resetting your device. To know more, jump to the removal guide that you can find at the end of this post.

There is no antivirus software for iPhones. True or false?
The term iPhone virus is not correct in its broad sense. In fact, there's no software that would conform to an internationally agreed description of a virus. Typically, iOS is attacked by potentially unwanted programs (PUPs), such as adware, browser hijackers, or other browser-based apps. However, practice shows that malware for iOS can sometimes be much more intrusive and difficult to deal with than those dedicated to Windows.
Those who are not fully convinced about Mac immunity to viruses must have noticed that there are no antivirus programs for iPhone or other Mac software. While people can ding Trend Micro, McAfee, Symantec, BitDefender, and other reputable vendors' products for finding lost iPhones, backing up the data, protecting online browsing, or privacy, there's actually no AV tools.
One the one hand, the absence of iPhone virus removal tools on the Mac app store and other sources means that there's no need for such tools, at least not yet. Up till now, Macs are much less vulnerable to viruses and malware, so the need for AV for Mac is yet an open question.
On the other hand, some experts claim that the iPhone virus does exist and that these devices can be affected by FBI scams, as well as ransomware (WannaCry, Petya)[7]. Indeed, cybercriminals are getting more and more sophisticated, so it's only a matter of time when Mac users will start suffering from the attacks of dangerous viruses. Thus, the absence of the AV suite for iPhones becomes a worrisome fact.
Jailbreaking your iPhone leaves it more vulnerable to iPhone virus
There are many ad-supported applications in the wild targeting iPhones. However, it has been noticed that most vulnerable iPhones are the ones that have been jailbroken. If you have an original iPhone, iPod, or iPad, you can feel pretty safe from malware attacks.
This procedure not only violates Apple's Terms and Conditions, but also exposes the iPhone to various risk, security vulnerabilities, and stability issues[8].
People who jailbreak their own phones save cybercriminals a lot of time and effort, putting their device at risk.
Different versions of iPhone scams
As Apple devices are highly valued, multiple iPhone-themed scams started flooding the internet recently. The primary goal of crooks behind these scams is to make victims believe, that they are eligible for a gift from Apple – typically, the newest iPhone, iPad or other devices. Let's check what scammers are up to and dig into the description of each of the frauds.
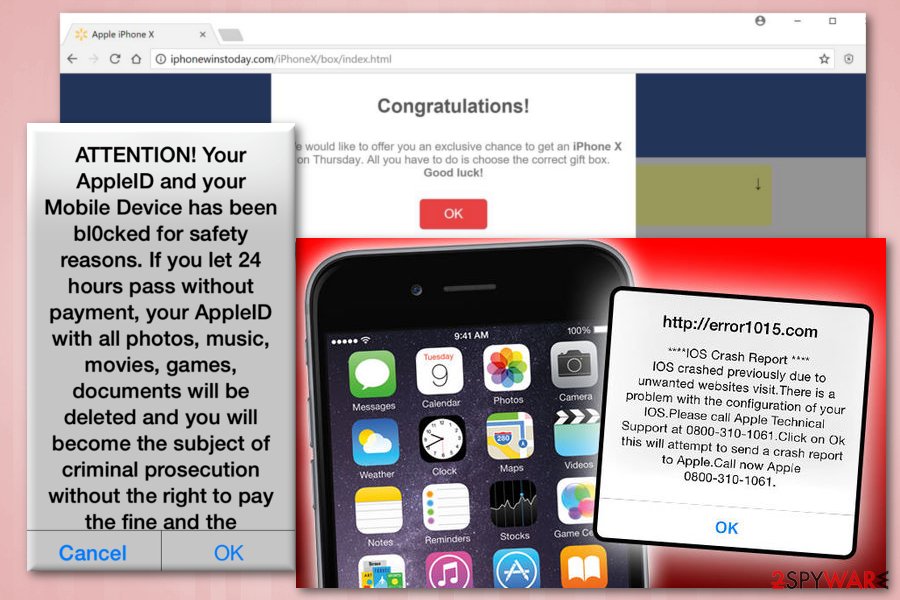
The new iPhone X from $1
The new iPhone X for $1 is the scam offering a free iPhone X which is nonexistent. All they have to do is pay the delivery fee that costs $1. It seems like a great deal! However, it is obviously a fake and users will not get the promised device.
The message is designed to look legitimate as the logos and theme used looks just like the ones from Apple. However, after proceeding, users are redirected to several websites and are finally asked to fill in some personal details and agree to terms of service of the competition. What users do not realize is that they have just subscribed to an expensive music service which costs $49.99 a month. Unless they manually decline the offer, their credit card will be charged monthly because of iPhone virus.
Win an iPhone X
Win an iPhone X is Similar to the above-described scam. This fake message also promises users an iPhone X. Victims might fall into this trap easily, especially those who never encounter digital scams before. The price for this expensive gift is minimal – users merely have to pick the “correct” gift box.
Unsurprisingly, every guess made is always correct (nevertheless, each of the users does not know that and think that they are fortunate). Soon after “guessing correctly” users are congratulated and prompted to enter personal details, such as bank account details, name, phone number, and similar data. This information might be used for such serious crimes like identity theft as you can never be sure who you are disclosing your personal data to.
Iphonewinstoday.com scam
Iphonewinstoday.com scam is caused by an adware-type virus which keeps redirecting users to this website. Nonetheless, users are also asked to open the “correct” gift box which gives them a chance to win a brand new iPhone X. Not surprisingly, the gift box is correct again! Then, victims are led to a page where they are required to enter personal details. It is explained that the e-mail address will be used in case the “lucky guest” wins the prize. However, it is merely a trick to extort personal information and use it for illegal purposes, such as identity theft.
Additionally, iPhone virus redirects its victims to iphonewinstoday.com and similar websites that might also promote other fake gifts, such as Samsung Galaxy phones, expensive gift vouchers and similar. Regardless of the prize, none of these false alerts should be trusted.
You've been selected to test iPhone 9
You've Been Selected To Test iPhone 9 is the newest scam which started spreading in March 2018. This hoax offers users a possibility of testing the newest – iPhone 9 – version of iPhone before it reaches public eyes. It is not surprising that any Apple supporter would be extremely excited about such an opportunity. What is more, crooks suggest a change of obtaining 128GB iPhone X for free! All they have to do is merely participate in a short survey and answer a few questions.
It is evident that questions asked by iPhone virus are only there to create the illusion that participants are actually doing something in exchange for the gift. Soon after finishing the survey, victims are requested to enter their full name, address, email address and telephone number.
It is clear that Apple is not behind these messages and would never look for participants in such a way. Thus, do not trust this fake pop-up if you encounter it.
Regardless of which scam you encounter – never participate in it. Remember, when the deal sounds too good to be true – it usually is. All crooks want is your money or personal data. Thus, ignore these scams and uninstall adware causing these messages.
Calendar virus
Calendar virus is one of the most prevailing iPhone virus variants, which has been disturbing iPhone users for many years already. It's a scam technique used by criminals to make people visit suspicious third-party websites, generate pay-per-click revenue, or promote Mac malware.
The iPhone Calendar virus is closely related to adware, which exceptionally targets the Calendar app. Upon successful infiltration, the legitimate Calendar app is filled with scheduled tasks, which contain a link, short description, and a picture (a gift or exclamation mark in most cases).
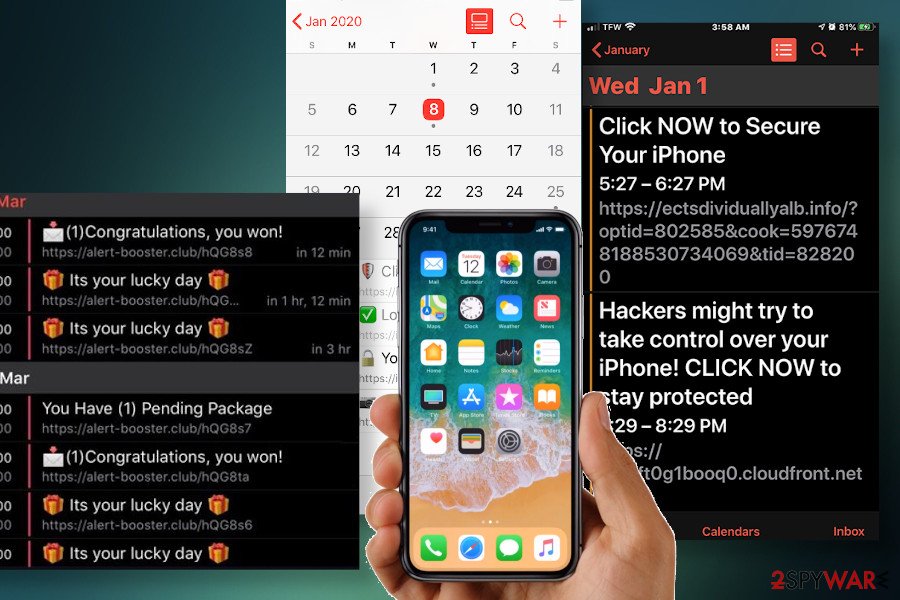
Not only the Calendar virus is intrusive. The links that people are represented can redirect to suspicious or even dangerous websites, from x-rated domains to malware download websites. Therefore, if you see links (list provided below) among the Calendar app events, look for malware on your iPhone and delete it. If you cannot clean your device manually, you may need to reset it to default settings.
- Try Apple news + free
- Your iPhone may be exposed to 4 viruses
- Click now to secure your iPhone
- You are exposed online, click to fix
- Virus alert – check protection now
- (1) Congratulations – you won!
- It's your lucky day
- You have (1) pending package
- iPhoneXs is ready, pick it up, or choose delivery!
- iPhone security pack discount
- Hackers might try to take control over your iPhone! CLICK NOW to stay protected.
There's no option to disabled the Calendar virus pop-ups or permanently stop the intrusive links from emerging without removing the ad-supported application from the machine. It may be problematic to eliminate it, though try to follow the guide provided at the end of the article to get rid of it.
Pegasus malware practices excessive spying on Apple users
This spying software is one of the best illustrating samples that Apple, especially iOS devices, can be infected with malware and, in fact, one of the most daunting. It has been spotted in August 2016. The malware is suspected to have been developed by an Israeli company NSO group[9] which has been notoriously known for developing spyware.
The malware does not target random targets, but only selected users. They receive deceptive SMS messages with links. If clicked, they would download the spyware designed for non-jailbroken iPhone devices. It functions on the basis of three zero-day day vulnerabilities.
Once it gets activated fully, it would exert complete surveillance on a user. It spies both, easily accessible and encrypted, messages as well as it can listen to audio files. Another problem is that it is capable of self-destructing if it does not connect to a remote Command and Control server for 60 days. The malware developers also designed an Android counterpart of Pegasus malware.
Due to the elaborate behavior and structure, it is quite troublesome to detect this malware. It does not reveal any of its presence signs in the Activity Monitor, let alone iPhone devices which do not have such a tool. You will need to download additional programs for detection and perform certain steps. More information on Pegasus removal is provided here.
Ransomware developers are interested in iOS too
As Android ransomware has become a common trend, one can assume that the time will come for iPhone devices as well. Such suspicions are not completely irrational as a few Mac ransomware samples were already released into the cyberspace. One of them pretends to be a tool called “Patcher” created for pirating software purposes[10]. It is written with the Swift programming language.
The malware was distributed via BitTorrent domains. It operates similarly to Windows-based crypto-malware as it hides in a .zip folder. The malware was not properly programmed as it had “buggy” transparent looks and failed managing decryption keys, which eventually resulted in the loss of decryption possibility.
Unfortunately, it still encrypted users documents and photos. Though such malware samples have been found targeting Mac, iPhone users should become wary as well.
Prevent malware infections on your device
Different malware threats are distributed via different channels. Earlier discussed iPhone adware and hijackers are spread via web scripts. Since they are not visible for ordinary users, detecting them might be troublesome. On the other hand, you can limit the probability of such iPhone virus by avoiding clicking on the links placed in the websites with gaming, gambling or other dubious content.
Regarding more elaborate malware, iPhone users may find this advice useful:
- Update system software once the update is released
- Do not download unnecessary third-party apps.
Delete all threats which could damage your iPhone
If pop-ups plagued your phone, reset the browser and remove virus from iPhone in this way. Don't worry, adware and browser hijackers are not as aggressive as ransomware viruses. In case of a tech support scam, exit the page. If you cannot cancel it, force a shutdown on a browser. In order to cease the redirect from activating itself again, perform these steps:
- Go to Settings;
- Tap on Safari icon;
- Select Clear History and Website Data;
- Close the window.
If dealing with a more serious threat, remove iPhone virus with the help of anti-malware tools. If you notice unusual behavior on your phone, such as crashing apps or locked files, perform iPhone factory reset. For this iPhone virus removal option, use this guide:
- Go to Settings;
- Navigate to General;
- Tap on Erase All Contents option.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of iPhone virus. Follow these steps
Delete from macOS
MacOS users have a certain advantage over iPhone users as they can install certain security apps to delete exquisite malware.
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Delete from Safari
Clear browsing data to cease the annoying iPhone virus pop-ups from appearing again.
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of iPhone registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting mac viruses
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Tom Warren. Apple reveals Windows 10 is four times more popular than the Mac. The Verge. Technology news.
- ^ Elizabeth Montalbano. Apple Jailbreak Zero-Day Gets a Patch. Threatpost. News on IT and security.
- ^ Christopher Budd. iOS is not immune to malware. TrendMicro. Simply Security.
- ^ marlenefromdenver. Safari-Alert ?scam?. Apple Community.
- ^ John Galt. Phony "tech support" / "ransomware" popups and web pages. Apple Community.
- ^ Alice Woods. Beware of free iPhone scams on Facebook and other social media sites. 2-spyware. Security and spyware news.
- ^ Keir Thomas. Can Macs get ransomware and how to stop a ransomware attack. Mac World. Mac-related news, reviews, and tips.
- ^ Kim Porter. Is jailbreaking legal and safe?. US Norton. Official website of security developers.
- ^ John Snow. Pegasus: The ultimate spyware for iOS and Android. Kaspersky Lab official blog. Stay protected from viruses, spyware, hackers, and spam.
- ^ Marc-etienne M.léveillé. New crypto-ransomware hits macOS. WeLIveSecurity. News, views, and insight from the ESET security community.





