Zareus ransomware (virus) - Free Instructions
Zareus virus Removal Guide
What is Zareus ransomware?
Zareus ransomware is a malicious Windows program that seeks to gain profits after locking users' files
Zareus is a ransomware-type virus that can be extremely dangerous to your personal files, as it encrypts them with a sophisticated encryption algorithm. This allows the attackers to ask for a ransom if victims want to restore their files to a previous, healthy state.
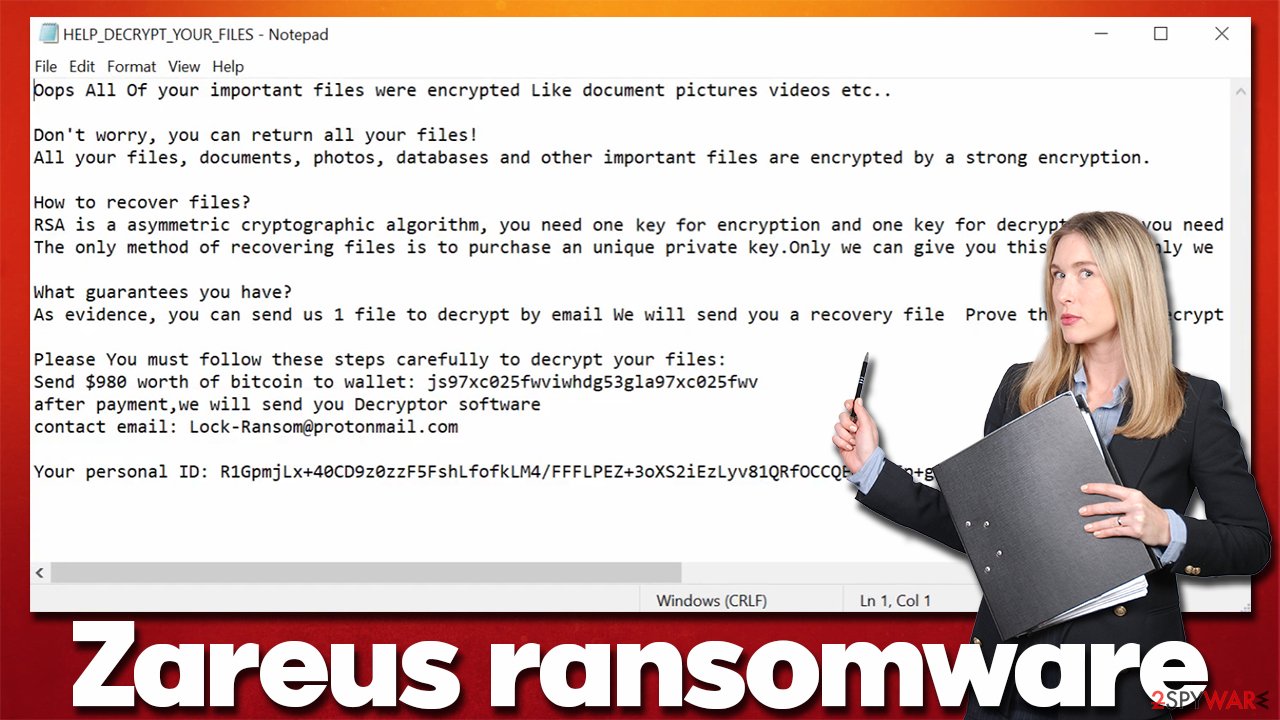
Of course, crooks are unwilling to provide a free description tool, as they explain in the ransom note titled HELP_DECRYPT_YOUR_FILES.txt, which is dropped right after malware finishes the data locking process. In the note, cybercriminals explain that users have to pay $980 worth of Bitcoin to the provided crypto-walled and then contact them via the Lock-Ransom@protonmail.com email.
If you have files that were appended with .ZareuS extension, recovering them without paying might be difficult. Nonetheless, we do not recommend contacting cybercriminals, as they might never send you the required decryption tool. Instead, follow the instructions below that should help you with ransomware removal and alternative data recovery methods.
| Name | Zareus virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .ZareuS |
| Malware family | LockDown ransomware |
| Ransom note | HELP_DECRYPT_YOUR_FILES.txt |
| Contact | Lock-Ransom@protonmail.com |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
Zareus virus analysis
Zareus stems from a relatively old malware strain known as LockDown, previous versions of which we have already covered – Bondy and Sext are among them. It is not as prevalent as some other widespread ransomware strains, although it periodically infects users whenever a new variant shows up. While the operation of malware is very similar, there are some differences in the ransom amount, contact email, and other peculiarities between variants.
Zareus encrypts all personal files with the help of RSA – a powerful encryption algorithm[1] that locks data with an asymmetric key. This means that you need a unique key that does not match one that was used to encrypt files. There are many more details explained about the attack in the ransom note, which reads:
Oops All Of your important files were encrypted Like document pictures videos etc..
Don't worry, you can return all your files!
All your files, documents, photos, databases and other important files are encrypted by a strong encryption.How to recover files?
RSA is a asymmetric cryptographic algorithm, you need one key for encryption and one key for decryption so you need private key to recover your files. It’s not possible to recover your files without private key.
The only method of recovering files is to purchase an unique private key.Only we can give you this key and only we can recover your files.What guarantees you have?
As evidence, you can send us 1 file to decrypt by email We will send you a recovery file Prove that we can decrypt your filePlease You must follow these steps carefully to decrypt your files:
Send $980 worth of bitcoin to wallet: js97xc025fwviwhdg53gla97xc025fwv
after payment,we will send you Decryptor software
contact email: Lock-Ransom@protonmail.comYour personal ID:
Note that the ransom size can vary from victim to victim, as well as is different from variant to variant. Previously, crooks could ask for $200, $500, or $600 for a decryptor, so it seems that the price is increasing exponentially.
Regardless of how much cybercriminals are asking for, we recommend you refrain from contacting them. There is never a guarantee that ransomware authors will provide the promised key, so you may end up being scammed and lose your money. Besides, paying cybercriminals only supports their malicious deeds and prompts them to infect more users.
Zareus ransomware removal
Right after ransomware finishes the infection and data encryption process, it might establish a connection to a remote C&C server,[2] where the unique key is sent to. If the internet is active, this connection can be sometimes used for other purposes, such as sending additional commands to malware to perform. Thus, your first task is to ensure that the system is disconnected from any type of networking:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Only after you are sure that there's no internet connection on your system can you remove Zareus ransomware. While it is possible to delete malicious files manually, it is not recommended for regular computer users. Instead, you should install SpyHunter 5Combo Cleaner, Malwarebytes, or another robust anti-malware and perform a full system scan. This will ensure that all the malicious files are removed at once, and ransomware will no longer encrypt the incoming data (which is very important).
Alternative data recovery methods
Despite popular belief, the encrypted data would not be reverted to its previous state after malware is eliminated from the system and its affected network. This is because the deciphering process requires a unique key, which is the possession of ransomware creators.
While restoring files successfully without it is quite unlikely, we recommend trying a third-party recovery tool that might work in some cases or restore at least some of the lost data:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Zareus ransomware Zareus ransomware]()
- Follow on-screen instructions to install the software.
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
Decryption tools might also be created for certain ransomware strains thanks to the efforts of security researchers. In some cases, law authorities seize the servers of malicious actors,[3] which allows the keys to be released by the public – reputable security vendors usually do this. Here are a few links you might find helpful:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

Other tips
After you are sure that malware is eliminated from your device, you can take some extra steps to finalize the removal process. First of all, we recommend checking whether the system health is good, as malware is known for damaging system components and files, resulting in crashes, errors, and other stability issues. If you have noticed such behavior, we recommend fixing Windows operating system with the FortectIntego maintenance and repair tool.
Regardless of whether or not you managed to recover, at least some of the .ZareuS files, you should report the incident to authorities. This might help the authorities to capture the perpetrators and possibly release the required keys to victims for free. You can make use of the following links:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Finally, don't forget to prepare backups of your files to prevent the devastating consequences of ransomware attacks in the future. Please follow the instructions below to backup data on OneDrive or GoogleDrive. You can also set up backups on physical drives, although that requires more maintenance.
Getting rid of Zareus virus. Follow these steps
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Encryption Algorithm. Techopedia. Professional IT insight.
- ^ Command and Control Explained. Palo Alto Network. Cyberpedia.
- ^ Europol takes down VPNLab, a service used by ransomware gangs. The Record. Daily breaking news.


















