Lukitus ransomware / virus (Decryption Steps Included) - Jul 2021 update
Lukitus virus Removal Guide
What is Lukitus ransomware virus?
Lukitus ransomware is the version of a known threat focused on the dangerous money extortion technique
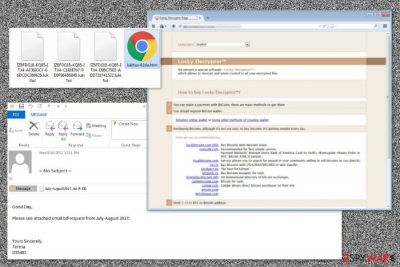
Lukitus is a new variant of the Locky virus that has been spotted spreading via malicious spam emails in August 2017. This ransomware-type program uses RSA-2048 and AES-128 ciphers to encrypt files and mark them with .lukitus file extension. Then it installs two new files – lukitus.bmp and lukitus.htm that inform about the only expensive data recovery option – the necessity to purchase Locky decryptor.
The virus not only encrypts files but renames them, as well. Just like a few weeks ago emerged Diablo6 version,[1] the recent cyber threat follows the same scheme to change filenames. The name of the corrupted file includes numbers of the victim’s ID and random characters:
[first 8 characters of ID]-[next 4 characters of ID]-[next 4 characters of ID]-[4 characters]-[12 characters].lukitus
When targeted data is locked with a strong cipher, the ransomware replaces the computer’s desktop picture with lukitus.bmp file. The new wallpaper includes a short but threatening message from the cybercriminals. They learn about data encryption and are urged to check the ransom note for more information about data recovery.
| Name | Lukitus ransomware |
|---|---|
| Type | Cryptovirus, file-locker |
| File marker | It includes a long victim identification number and ends with .lukitus appendix. The line comes after the original name of the encoded piece |
| Related | Locky virus version |
| Distribution | Malicious files can be added to emails or included on pirated software packages |
| Removal | The best tool for malware is the antivirus tool. This application checks the computer and terminates any detected pieces |
| Recovery | The virus damage that ransomware leaves behind can be fixed using FortectIntego |
The HTM file includes the victim’s ID number and notes that the only way to decrypt files – to purchase Locky Decryptor for 0.49 Bitcoins. However, it’s a huge sum of money that equals about $2.000. We do not recommend paying it because it may lead to money loss only.
Just like other Locky variants, Lukitus uses the same ransom note template and payment website. That proves that cybercriminals standing behind this malicious program are consistent with their work.
Unfortunately, malware removal won’t help to recover corrupted files. Neither Locky nor its variants are decryptable. However, the elimination of crypto-malware is necessary because this malicious program makes critical system changes and might put your data or privacy at risk. Therefore, as soon as you learn about the attack, you have to obtain reputable security software and remove Lukitus from the PC. For this task, we suggest using Malwarebytes or SpyHunter 5Combo Cleaner.
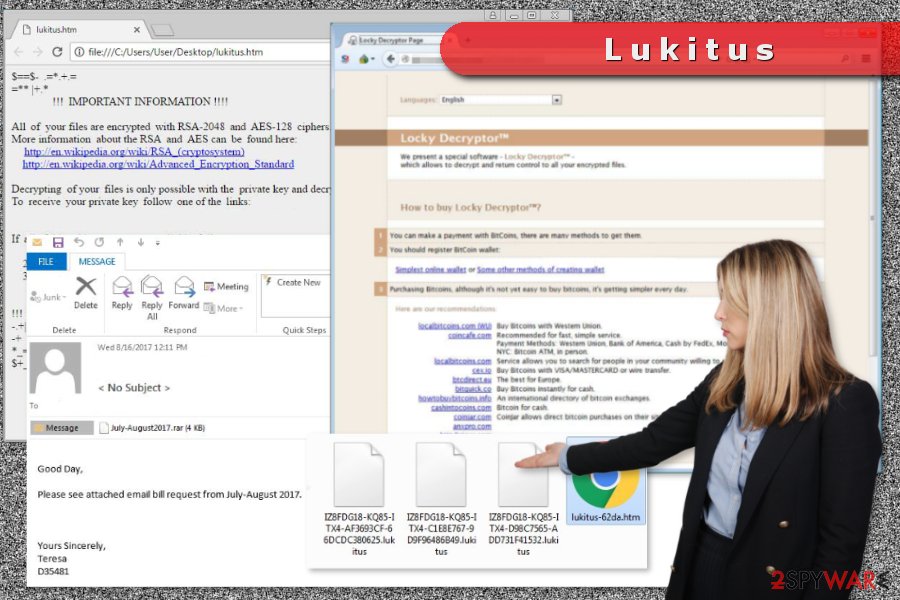
Malicious spam campaign hits victims with a new ransomware variant
According to the malware researcher Rommel Joven, developers of the Locky virus remain faithful to the traditional ransomware distribution method – malicious spam emails. Malspam campaign that spreads Lukitus includes ZIP or RAR attachments with JS files. As soon as a user opens such a dangerous archive, malware executable is dropped to the system.
Emails that bring this crypto-malware have two subject lines:
- < No Subject >
- Emailing – CSI-034183_MB_S_7727518b6bab2
The content of the message politely asks to open the attached document due to a particular date. However, we want to point out that if you do not expect to receive any files or documents, you should never open unknown emails.
The name “Lukitus” means “Locky” in Finnish. However, it does not say that this variant aims at computer users in Finland[2] only. The malicious emails are written in English and can be delivered to any inbox all over the world.
Before opening any received files or the links in the email, you should:
- double-check the information about the sender;
- scan attachments with security tools in order to make sure that they are not infected;
- lookup for grammar or spelling mistakes that might reveal cybercriminals.
For ransomware protection,[3] you should also keep all the programs installed on your PC updated, avoid clicking suspicious content or visit high-risk sites and install professional antivirus. Of course, data backups are a must!
September 2017 update: the ransomware uses a set of different themes for spam emails
Locky's authors are now using the old Dropbox-themed phishing emails to deliver the latest Lukitus ransomware variant. Security experts have discovered a brand new spam campaign that rapidly distributed deceptive messages to over 23 million potential victims in just 24 hours. It is believed to be one of the largest malicious spam campaigns seen in the second half of 2017.
Facts about the latest Lukitus distribution campaigns:
- Criminals are rapidly distributing the latest Locky variant to victims via email. Typically, they are Dropbox-themed and suggest verifying email via a provided phishing link.
- Clicking the provided link redirects the victim to legitimate web pages or hosting accounts that have been compromised by criminals. Usually, the link will contain a dropbox.html at the end of it.
- The dropbox.html file opens a phishing website that looks like a legitimate DropBox page. However, at the same time a VBS file downloads and launches the virus on the victim's system.
- At the same time, criminals are also using a quite simple malspam technique and sending double-zipped VBS files or JS files. Once launched, these files download Lukitus from particular domains.
- Virus' authors are using the following subject lines in this malspam campaign: “Please print,” “pictures,” “images,” “scans,” “documents” or “photos.” The message body contains a basic message inviting you to view the content of the attached file – “Download it here.”
- Criminals are also using FreeFax-themed spam as well as deceptive voice messages to lure unsuspecting victims into compromised websites ending with .fax.html. These emails usually contain “FreeFax From:[random digits]” or “Voice Message from [random digits] in the subject line and suggest clicking a provided link to download the fax or listen to the voice message.
- Once redirected to a compromised website, the user receives a suggestion to open a .js file which might be named in such format: Fax_Message_[random digits].js or similar. Opening the file instantly installs Lukitus on the system.
- The latest spam campaign distributes Micorosft Store-themed spam. Fraudsters are using “Microsoft Store E-invoice for your order #[random digits]” in the subject line and suggest downloading the Invoice by clicking on an attached link. Just like we previously explained, the link leads to a compromised site containing a malicious MS_INV_[random digits].7z file which was previously uploaded by virus' developers.
It is clear that Locky virus' developers are working hard to distribute the Lukitus ransomware version as widely as possible. Therefore, you have to stay vigilant and not allow this ransomware to outwit you.
Remove Lukitus file virus and recover your files
The proper ransomware removal must be performed using reputable security software. Automatic elimination assures that all malicious files and processes are stopped and deleted without damaging the system. Ransomware viruses are complicated, so attempts to uninstall malicious components manually may end up with irreparable system damage.
If you are looking for a tool to remove Lukitus from the PC, we suggest choosing one of these programs: SpyHunter 5Combo Cleaner, or Malwarebytes. However, malware might prevent installing or accessing security tools. So, you may need to reboot the computer to Safe Mode with Networking as shown below. You can also benefit from the scan with a tool like FortectIntego that helps with virus damage and affected system parts.
Getting rid of Lukitus virus. Follow these steps
Identify ransomware affecting your PC
Modern-day ransomware had its roots in the early 2010s when cybercriminals began to understand the potential it has for money extortion. Over the years, thousands of new ransomware strains have been developed and spread all over the world, infecting regular consumers, small businesses, and high-profile organizations.
Because of the lucrative nature of ransomware, cybercriminals are creating new ransomware versions in the hopes of establishing themselves in this illegal business. Ransomware often uses different extensions, ransom notes, and other attributes that it can be identified by. However, quite often, this information can overlap or simply not be available, so identifying the threat might be difficult.
In order to deal with ransomware infection effectively, you must first identify it. Here are a few examples of how to determine the precise ransomware you are dealing with:
File extension
Almost all modern ransomware viruses are using extensions that are appended at the end of the original filenames. However, this is not a rule, and in some cases, cybercriminals change the name by replacing it with randomly generated characters, add the marker before the file name, or do not visually change the name of the file at all.
Here you can see an example of a unique extension .hhmgzyl that belongs to the Snatch ransomware family:
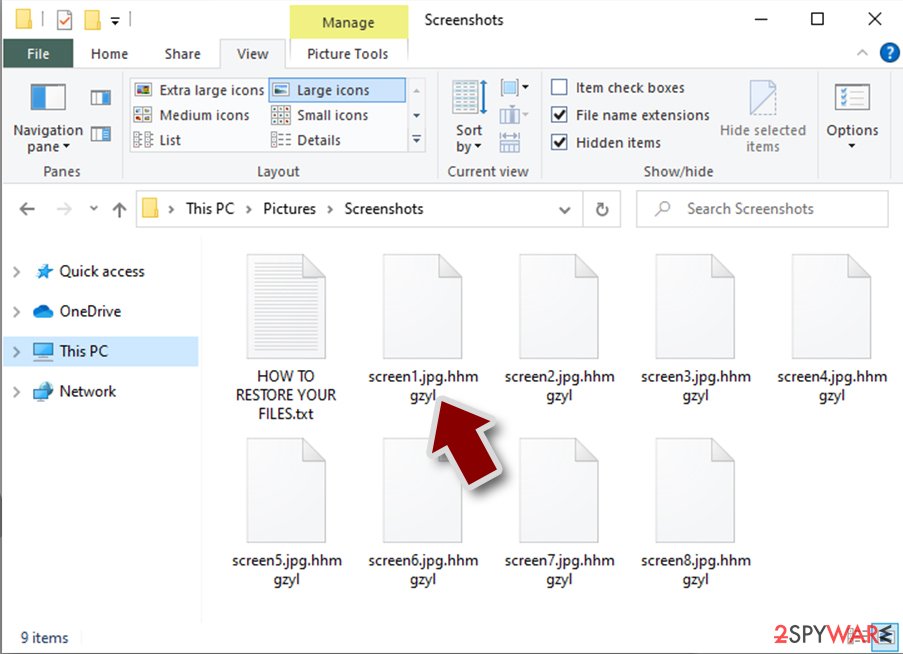
If your files are appended with .exe, .locked, .encrypted, or other broadly-used extensions that are difficult to identify, proceed with the next step.
Ransom note
Ransomware family might sometimes be identified by the ransom note it uses. In most cases, cybercriminals create a simple .txt file and place it on users' desktops or other places that are easily reachable (typically, where the encrypted data is located). Other times, a pop-up window can also be used, which is launched as soon as the encryption is complete. In some cases, threat actors name the ransomware within this note:
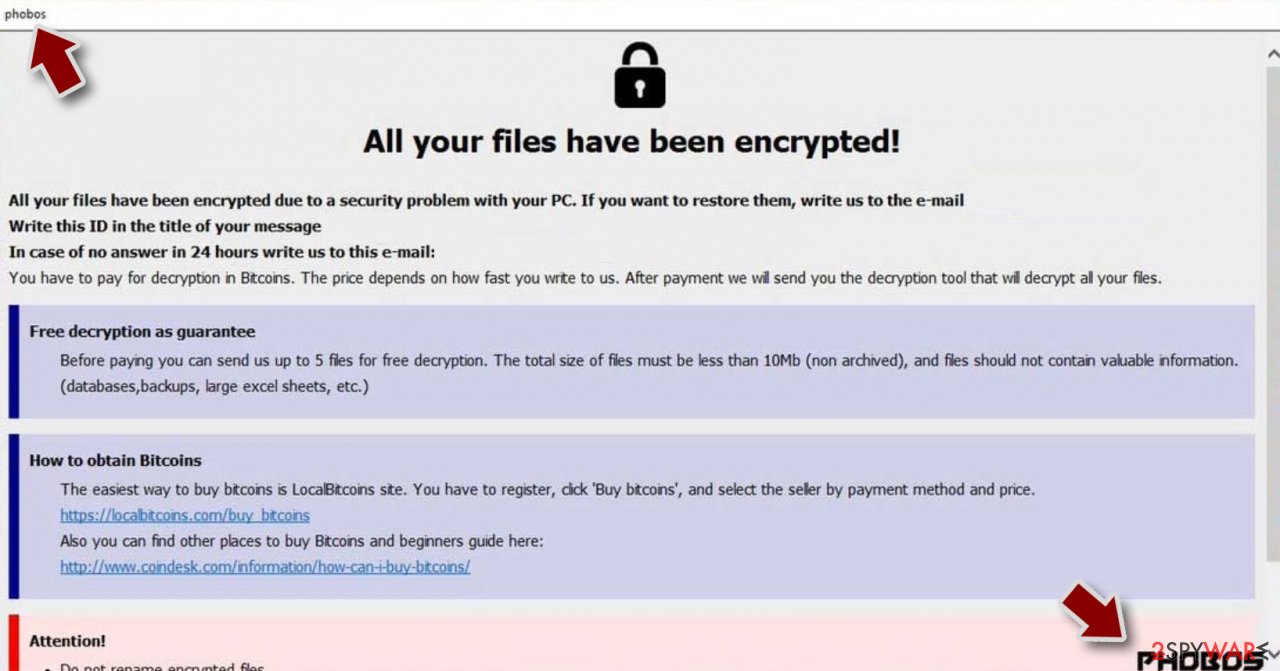
In some cases, it is possible to identify ransomware by its ransom note name, but they are typically very generic (e.g., FILES ENCRYPTED.txt, _readme.txt) and used by different cybercriminals groups.
Free ID Ransomware service
ID Ransomware is a free service that can easily let users identify the precise malware they are dealing with. All you have to do is upload the ransom note that can be found on the desktop and within folders where encrypted files are located and the sample of an encrypted file.
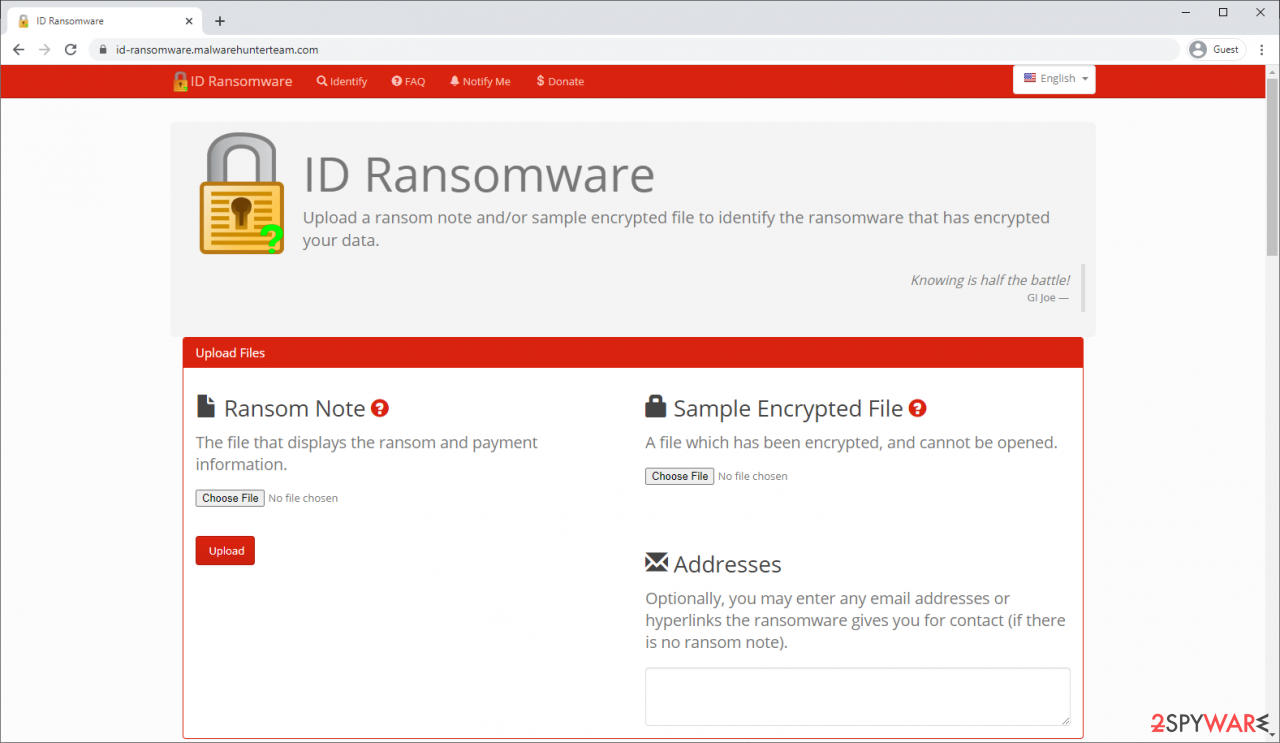
Soon after uploading the required files, you will be provided with all the relevant information, including what family ransomware belongs to and whether or not it is possible to decrypt files.
If none of the above helped you to identify which ransomware you are dealing with, you should use keywords (extension, contact email, ransom note contents, crypto-wallet address, etc.) to find the information on the internet.
Isolate the infected computer
Some ransomware strains aim to infect not only one computer but hijack the entire network. As soon as one of the machines is infected, malware can spread via network and encrypt files everywhere else, including Network Attached Storage (NAS) devices. If your computer is connected to a network, it is important to isolate it to prevent re-infection after ransomware removal is complete.
The easiest way to disconnect a PC from everything is simply to plug out the ethernet cable. However, in the corporate environment, this might be extremely difficult to do (also would take a long time). The method below will disconnect from all the networks, including local and the internet, isolating each of the machines involved.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
If you are using some type of cloud storage you are connected to, you should disconnect from it immediately. It is also advisable to disconnect all the external devices, such as USB flash sticks, external HDDs, etc. Once the malware elimination process is finished, you can connect your computers to the network and internet, as explained above, but by pressing Enable instead.
Scan your system with anti-malware
If you are a victim of ransomware, you should employ anti-malware software for its removal. Some ransomware can self-destruct after the file encryption process is finished. Even in such cases, malware might leave various data-stealing modules or could operate in conjunction with other malicious programs on your device.
SpyHunter 5Combo Cleaner or Malwarebytes can detect and eliminate all ransomware-related files, additional modules, along with other viruses that could be hiding on your system. The security software is really easy to use and does not require any prior IT knowledge to succeed in the malware removal process.
Repair damaged system components
Once a computer is infected with malware, its system is changed to operate differently. For example, an infection can alter the Windows registry database, damage vital bootup and other sections, delete or corrupt DLL files, etc. Once a system file is damaged by malware, antivirus software is not capable of doing anything about it, leaving it just the way it is. Consequently, users might experience performance, stability, and usability issues, to the point where a full Windows reinstall is required.
Therefore, we highly recommend using a one-of-a-kind, patented technology of FortectIntego repair. Not only can it fix virus damage after the infection, but it is also capable of removing malware that has already broken into the system thanks to several engines used by the program. Besides, the application is also capable of fixing various Windows-related issues that are not caused by malware infections, for example, Blue Screen errors, freezes, registry errors, damaged DLLs, etc.
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

By employing FortectIntego, you would not have to worry about future computer issues, as most of them could be fixed quickly by performing a full system scan at any time. Most importantly, you could avoid the tedious process of Windows reinstallation in case things go very wrong due to one reason or another.
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Lukitus and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Developers of Locky present the update – Diablo6 ransomware virus. Virus Activity. Recent news of computer viruses.
- ^ Virukset. Virukset. Finish website about computer viruses and their removal.
- ^ Arun Thomas. Ransomware: How to protect yourself. NetSentries. Smarter security provider.






































