.locky file extension virus (Removal Guide) - Sep 2017 update
.locky virus Removal Guide
What is .locky file extension virus?
.locky file extension virus continues attacking computer users in sneakiest ways
Infamous Locky virus is alternatively known as .locky file extension virus. There’s no doubt that this name is based on the appended file extension to the targeted files. The virus has been active since February, 2016. Over time, its developers released new versions using different file extensions, including Diablo6 and Lukitus. The sophistication of the malicious software and hundreds of failed attempts to create a decrypter for it makes it very similar to the infamous Cerber ransomware.
Sadly, since it’s appearance on February 2016, malware is still undecryptable. Its distribution scale, unbreakable encryption, and periodically released versions made Locky ransomware the most popular and dangerous cyber threat of the year.[1] In 2017, the virus emerged and disappeared regularly, but only to release more dangerous and complex versions and test new distribution techniques. The new wave of the virus struck hit the virtual community in August 2017 with Diablo6 and Lukitus virus versions.
Ransomware, together with its other variants Aesir, Thor, Osiris, Zepto, Odin, and others continues spreading actively in 2017. The malicious email with malware payload might be sent straight to your email box. Cyber criminals mostly distribute .locky file extension ransomware via fraudulent emails that include a malicious attachment (obfuscated Word document).
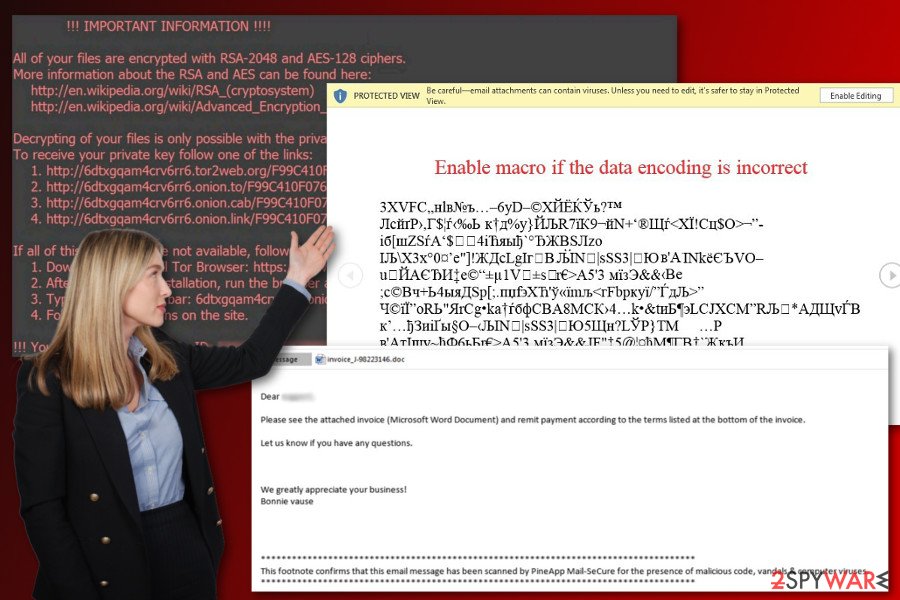
This Word file contains a code that gets activated immediately in case the user has Macros function enabled in Word. In case Macros is disabled, the user sees a message above a distorted text: “Enable macro if the data encoding is incorrect.”
However, Microsoft reacted to the increase of Macro-based ransomware and presented new features in Office 2016 that should help to decrease chances for malware to infiltrate the computer. [2] During virus evolution, developers launched new spam email campaigns that include malicious HTA, JS, and WSF files, but that’s not all. The virus stepped inside Facebook and employed Trojans to infect computers.
As we have mentioned above, Macros activates the code, which is designed to download and run an executable .locky file extension virus file from a remote server. This disastrous program then scans the computer system, detects victim’s personal files and encrypts them using RSA-2048 and AES-128 encryption methods, and appends .locky file extension.
Encrypted data becomes inaccessible; in such way, this virus puts the victim in an invidious position. Obviously, every computer user keeps important data on its computer, so such deprivation of files can cause desperation and stress.
However, malware leaves ransom notes in every folder that holds the encrypted data and this note explains how the victim can retrieve his/her personal records. It must be noted that different versions of the virus might drop differently named files. Below, you can see a list of names that Locky uses for for ransom notes:
- _HELP_instructions.html, _HELP_instructions.txt;
- diablo6.htm;
- lukitus.htm;
- _WHAT_is.html, _[random numbers]_WHAT_is.html;
- _Locky_recover_instructions.txt;
- recover.txt;
- _[2 chars]_HELP_instructions.html;
- HOWDO_text.html;
- _[set of chars]-INSTRUCTION.html;
- OSIRIS-[4 symbols].html.
Sadly, Locky removal won’t rescue corrupted data. Cyber criminals demand to pay the ransom of 0.5 Bitcoins. It is advisable not to pay the ransom. No matter how much you pay, cyber criminals only care to make a profit. There is absolutely NO guarantee that they will send you decryption key to recover your personal files.
Do not support cyber criminals this way. Otherwise, you take a risk losing your files AND your money. Besides, cyber criminals will know that they can scare you and might try to send another virus for you in the future. Thus, in case of the attack, you should remove .locky file virus from the computer.
Malware is not only a threat for your records but your computer’s security as well. While it stays inside, it might help other cyber infection to enter the system and cause more damage. We highly recommend terminating this pest with FortectIntego. If you cannot install or run this tool, please scroll down to the end of this article and follow the step-by-step guide.
Locky distribution techniques
During the lifetime, the developers of .locky virus applied different distribution and infiltration strategies. Starting from the Macro-based attacks, they also used JavaScript files, trojans, and botnets. The ransomware has affected huge countries such as U.S., France[3], Germany, China, India, and others.
- Macro-based attacks. The first malicious email campaigns included Word documents that asked to enable Macro commands. This infected file is presented as an important document, such as an invoice. Such malware attacks were not as popular as there are now, so users were easily tricked to open the attachment. If victims are using old versions of MS Office, it is enough to open the document and malware managed to get inside the system. However, new Office versions ask to activate the Macro content. If they agree to do that and click the button, the malware is executed and ran on the system. In addition, criminals might send you a safe-looking PDF file with an embedded Word document in them. The same macro trick is used to install malware on the computer.
- Obfuscated HTA, JSA, and WSF files. Later .locky file virus started distributing camouflaged HTA, JSA, and WSF files via emails. These misleading emails also inform about the necessity to open the attachment. Mostly, the virus is spread via the MRI6219316107.js file. This coded JavaScript file look like the ordinary Word document which is often added in the ZIP file.
- Nemucod Trojan. Developers of the infamous Locky used Nemucod to infiltrate the system. The trojan tricks users that it’s a safe file. However, it actually carried a .lnk file that helped malware to get inside the system without getting caught by antivirus software.
- Necurs Trojan. At the beginning of summer 2016, Locky ransomware has been spreading actively with the help of Necurs. This trojan helps not only to infect computers with ransomware but also connects them into the biggest botnet in the world.
- Facebook. Authors of the Locky were the first who managed to bypass Facebook’s security.[4] The malicious SVG file has been spread via Facebook Message. This file looked like a link sent by one of the Facebook friends. Though, when people clicked on it, they were redirected to the website that asked to install a particular plugin. Instead of installing plugin necessary to watch the content, they installed the virus.
- ZIP archives with .vbs or .js files in them. The virus was and is distributed via malicious spam that delivers archived .vbs or .js file. If the victim unknowingly extracts the ZIP file and executes the malicious file inside of it, the dangerous script connects to a remote domain and downloads Locky into the system.
As you can see, cyber criminals might install ransomware on your computer using different strategies. It seems that they use advanced techniques and have excellent social engineering skills that allow creating brilliant misleading email campaigns.
Protect your PC from this disastrous virus
The most important thing to do is to regularly backup your data.[5] We recommend you to store copies of important data on an external drive because some ransomware viruses can access online file storage clouds via your Internet connection.
- Install a reputable anti-malware software (for instance, FortectIntego, SpyHunter 5Combo Cleaner) on your computer to keep it protected from ransomware and other dangerous viruses.
- Whenever you download files or programs, choose “Save” option instead of “Run/Open.” This way, you give some time for computer security software to check whether the file is safe or not.
- Keep all your software up-to-date and enable automatic software updates if possible. Cyber-criminals can exploit vulnerabilities in outdated software and enter your system without your knowledge.
- Avoid visiting high-risk websites and download software only from verified and secure download sites.
- Before opening email attachments, always double-check the information about the sender and carefully look through the message. Look for the typos, grammar or spelling mistakes. Take a look at the email address. Maybe, it looks suspicious. What is more, if you do not expect to receive such email, do not open the attached file or provided links.[6]
Remove .locky file extension virus
It is important to remove .locky file extension malware as soon as you notice its presence. If you notice its existence soon enough, you might be able to stop the encryption process in time and save some of your files.
If you plan to import data from the external backup drive, make sure you entirely remove virus first, as this threat is capable of accessing and encrypting data on every device plugged into the computer as well. We strongly recommend using an automatic malware removal tool for Locky removal, for instance, FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
f malware prevents from installing security program, please follow our prepared guidelines and reboot device to the Safe Mode with Networking. Talking about data decryption options, it is nearly impossible to decrypt files that were encrypted by this malicious computer threat.
The only one way to recover your files is to import them from an external drive. If you did not create any data backups earlier, then you can try additional data recovery methods presented at the end of the article or try one of the following tools to decrypt your files – Photorec, Kaspersky virus-fighting utilities or R-Studio.
Answers to questions about .locky ransomware
Question: Today, I have received a suspicious email. The subject is: ATTN: Invoice J-98223100. This email also has a file attached to it, which is named invoice_J-98223100.doc. I believe that this email is untrustworthy and that I shouldn’t open it… However, how can a Word file be dangerous? Can you explain what should I do about this email? Should I open the attachment or should I send this email to Trash?
Answer: Do NOT open the attachment! You have received an email from cyber-criminals related to Locky ransomware. This fraudulent email delivers infectious Word document that can download a virus to your computer.
Locky virus uses a new technique to download and run virus executable file – it sends a malicious code in a Word document, which gets activated if Word Macros function is toggled on. You should send this email to Trash immediately.
Getting rid of .locky virus. Follow these steps
Manual removal using Safe Mode
Safe Mode with Networking allows disabling the virus. It might be needed if the virus blocks access to the security programs and prevents the automatic removal. Thus, follow the steps below. When in Safe Mode, install and update malware removal program. Then scan the system several times.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove .locky using System Restore
System Restore methods also helps to disable the virus in order to access to the antivirus program or malware removal utility. We recommend running a full system scan with professional security tool in order to delete all malicious components.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of .locky. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove .locky from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.The only safe and effective way to get back encrypted files is to use data backups. However, if you do not have them, you can only try alternative recovery methods. We cannot promise that these options will restore all corrupted files; however, you should at least try. It's better to rescue at least some of your documents, pictures and other data.
Windows Previous Versions feature allows accessing and copying earlier saved versions of the encrypted files. Indeed, this method allows traveling back in computer's time. However, this function is only available if System Restore has been enabled before the ransomware attack.
Otherwise, you won't be able to copy the most important files. What is more, if you have a bunch of files you need to rescue, this method might not be convenient. You can only copy individual files.
If your files are encrypted by .locky, you can use several methods to restore them:
Try Data Recovery Pro to restore files encrypted by .locky file extension virus
Originally, Data Recovery Pro has been created to restore corrupted or damaged files after system wreckage, and accidentally deleted files.
However, the increase of ransomware attacks motivated developers to update this tool and help victims of the ransomware to restore at least some of the encrypted files. Hopefully, this tool will be helpful for you too.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by .locky ransomware;
- Restore them.
Try Windows Previous Versions feature in order to restore files encrypted by .locky file virus
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try ShadowExplorer to restore files encrypted by .locky virus
ShadowExplorer can restore files from Shadow Volume Copies of the encrypted files. Thus, in order to use this method, you need to make sure that the ransomware hasn't deleted them.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Locky decryptor
If you are looking for decryption software that would be able to rescue your files from the .locky file extension, we do not have good news.
Malware researchers are still working on a decryptor. Hence, you just need to be patient, try alternative recovery methods, and wait for the software. Please, do not consider purchasing the Locky decryptor from the cyber criminals. You may lose your money or receive a malicious program.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from .locky and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Olivia Morelli. Top 6 most dangerous computer viruses of 2016. NoVirus. How to get rid of computer viruses.
- ^ New feature in Office 2016 can block macros and help prevent infection. Microsoft. Microsoft Malware Protection Center Blog.
- ^ LesVirus. LesVirus. Spyware and Malware Removal Tutorials.
- ^ Locky ransomware goes on Facebook: malware started spreading via instant messages. Esolutions Blog. The blog about latest news about malware, viruses and cyber security.
- ^ Rich Castagna. Ransomware protection best served by backing up your data. TechTarget. Includes tips, webcasts, and other advice in a variety of focused enterprise technology channels.
- ^ How to Tell if an Email Attachment Is Malware. HelloTech Blog. Reviews, Tips, and Latest News on Tech Products.





















