Zepto virus (Free Instructions) - 2021 update
Zepto virus Removal Guide
What is Zepto virus?
Zepto ransomware is an alternative version of the infamous Locky file-encrypting virus
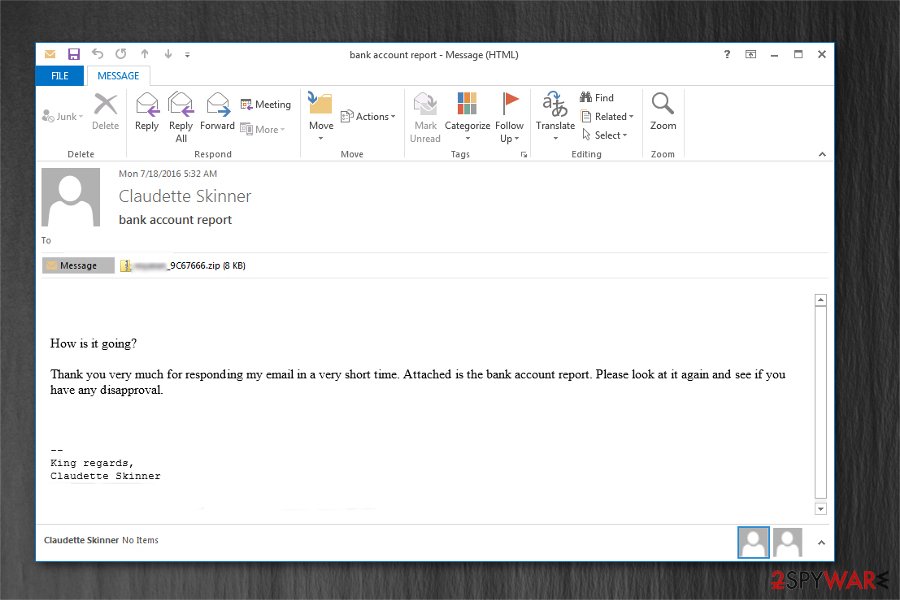
Zepto ransomware is one of the dangerous Locky virus versions which performs data encryption. This ransomware family is considered to be one of the most hazardous cyber threats of 2016 and spreads via malicious spam emails[1] – he malspam campaign is detected spreading via Necurs botnet. Precisely, malicious JavaScript files are packed inside of .zip or .docm (macro-embedded MS Word documents) files which, once opened, begin the infection routine of a Windows machine. According to the researchers, approximately 150 thousand emails were holding the obfuscated payload of Zepto virus as an attachment[2].
There are several major difference between Locky and Zepto ransomware, however. Malware uses the combination of AES 128 and RSA 2048 algorithms to encode information, and not only appends .zepto extension, but also modifies the rest of the file name components. Each file is changed in the following way: [8 digit hexadecimal string]-[4 digit hexadecimal string]-[4 digit hexadecimal string]-[12 digit hexadecimal string].zepto. Malware then delivers _HELP_instructions.html ransom note which asks to pay ransom in bitcoin. Additionally, desktop wallpaper is also swapped by a _HELP_instructions.bmp image.
Researchers do not recommend contacting ransomware virus authors, as there is a working decryption tool that should be able to remove .zepto extension for free, and allow to use data once again. But before that, make sure you clean your computer from the infection and malicious files – find out how below.
| Type | Ransomware |
|---|---|
| Precursor | Locky |
| Cryptography | AES 128; RSA 2048 |
| Latest versions | Lukitus; Ykcol |
| Extension | .zepto; example of an encrypted file: “046AFC44-82B1-2EAA-28049E244EDF.zepto” |
| Ransom note | _[2 chars]_HELP_instructions.html; _[2 chars]_HELP_instructions.txt |
| Distribution | Spreads as .7z email attachments but might employ other distribution methods as well (exploits, botnets, etc.) |
| Decryption | You can decrypt files with .zepto extension using the professional decryption software. Find it at the end of this article |
| Removal | Uninstall ransomware by running a full system scan with powerful security software |
| System fix | After malware elimination, you might face after-effects of the infection, such as system crashes, errors, BSODs, lag, and similar stability issues. If that is the case, you can attempt to fix and remediate your Windows with FortectIntego repair software automatically |
The latest versions detected of Zepto ransomware are Lukitus and Ykcol. Users are tricked into downloading an infected .zip or .docm attachment by tempting subject lines, such as the following:
- Please, see the attachment;
- To the head of sales;
- Scanned image;
- etc.
Similarly to Bart ransomware, this virtual infection attempts to deceive users into executing a JavaScript file or enabled macros. Once it's done, it encodes files with RSA-2048 and AES-128 ciphers. As a result, they get blocked bearing .zepto extension. At the end of the encryption process [3], ransomware changes the desktop picture with an image that presents information about the virus and a request to pay a ransom. If this menace has befallen you, you should still remove Zepto. You might also try this free Zepto Decrypter afterward.
Now the attention might be directed to Lukitus and Ykcol versions, which hide in .7z email attachments. Though the virus was most active at the end of 2016, even now, some companies report getting infected with this version. Since the cyber criminals shuffle Locky variations, it would not be surprising if you can get infected with malware after opening the .7z attachment.
Take into consideration that hackers apply emotional pressure to persuade users to hurry with the payment [4]. Likewise, they succeeded in collecting more than $100,000 with the help of ransomware. Let us assure you that there are ways to complete virus removal. The most effective of them is to use SpyHunter 5Combo Cleaner or Malwarebytes security software. Additionally, experts also recommend performing a full system scan with FortectIntego after the elimination to restore the Windows system back to normal.
Like in the previous versions, ransomware activates via the dll file, which is executed by the rundll32.exe file. The latter is a legitimate system process. Likewise, it allows escaping users' intervention. Just as other ransom-demanding viruses, this malware leaves one of the following ransom notes:
- _[2 chars]_HELP_instructions.html
- _[2 chars]_HELP_instructions.txt
Zepto ransomware states that there is no other way to decrypt files but to pay a ransom and receive a private key and a decryption program. We highly discourage you from purchasing the tool promoted by the perpetrators as it seems a malicious software as well.
Instructions on how to access payment site are also provided by this virus. During the investigation process, we discovered that the payment site advertises Locky decrypter which was used by another ransomware called Locky. Now it can be purchased for 4 Bitcoins (approximately 2541 USD).
Of course, you should never think of that because you can be left without both, your files and your money. To recover your data, you should remove ransomware first and then restore your files from a backup. Take a look at the ransom note by the virus:
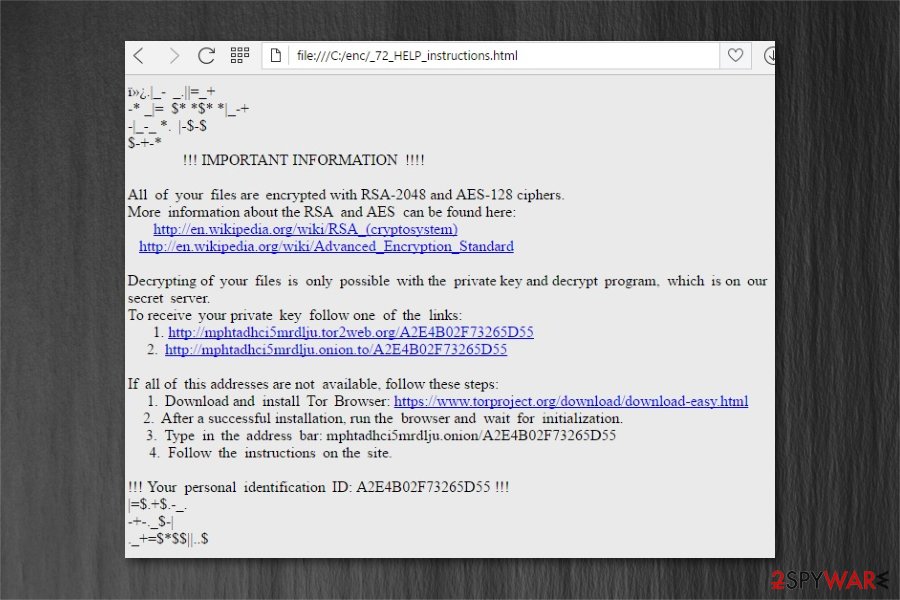
!!! IMPORTANT INFORMATION !!!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
hxxps://en.wikipedia.org/wiki/RSA_(cryptosystem)
hxxps://en.wikipedia.org/wiki/Advanced_Encryption_StandardDecrypting of your files is only possible with the private key and decrypt program, which is on our secret server.
To receive your private key follow one of the links:If all of this addresses are not available, follow these steps:
1. Download and install Tor Browser:
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar:
4. Follow the instructions on the site.
After Locky rampaged in the virtual world for a couple of months, soon afterward, the cyber campaign of Zepto was launched. It reached its peak in July. Ordinary and corporate users all around the world were assaulted by ransomware. Thus, even if you reside in Sweden[5], which is regarded as the country with the lowest malware rate, stay vigilant.
As previously mentioned, the threat employs a swift [XXX|XXXX].js file for a disguise. By pretending to be a financial report or invoice, it captures victims' attention. Opening the attachment enables ransomware to start its mischief in thousands of computers. After sending HTTP GET requests, the threat can get important information about victims' computers. This also enables the .zepto file extension virus to infect a larger amount of computers.
By planting its wscript.exe executable [6] among the registry files, ransomware keeps the device in its claws even if you reboot it. Moreover, the virus has been updated to such an extent that even Windows Defender fails to block it. Therefore, it is of crucial importance that your security applications are updated daily.
Moreover, ODIN ransomware appeared as a backup to the original version of the threat. It seems that the felons do not intend to step aside.
Criminals keep releasing updates of the crypto-malware
Despite all the new variants of Locky ransomware, the Zepto virus is still detected spreading worldwide. Researchers note that this file-encrypting cyber threat reached its distribution peak of 150% from July to September in 2017. Nonetheless, since then, though the spam campaign of this particular version subsided slightly, IT specialists spot its variations once in a while. The recent version disguised under the luainstall.dll file. It also disguised under the following names:
- UFDFcTFN2.dll.3904.dr;
- LPwBHJjO2.dll;
- nvFjEHFele2.dllCrTqhHDO3.dll;
- BsTVXmdKk1.dll;
- 3_FILE.exe
- oqmCxkcjyFG1.dll[7].
Malware actively targets European countries, the United States, South America, and East Asian regions. Lately, virus researchers spotted that Locky ransomware, as well as its newest version – .aesir file extension virus, stepped on Facebook. Malware started spreading via Facebook’s messages by sending a malicious SVG image file. Victims, who clicked on it, were redirected to a suspicious domain that looked like YouTube.
However, they were asked to install the plugin to play the video. This bogus plugin is Nemucod Trojan which is responsible for activating malware on the affected computer. Malware analysts expect ransomware to spread on Facebook or other social networks as well. Therefore, chances to encounter this cyber menace remain high. The only free and safe data recovery solution is backups.
The peculiarities of the original Locky ransomware
The precursor of ransomware, known as Locky virus, has numerous versions which are regularly released in the cyberspace. The original version of the file-encrypting virus was first discovered in February. Attackers keep upgrading the malware to ensure that decryption tools by security firms would be disabled. Additionally, the updates help to improve the security of cybercriminals and help them remain anonymous.
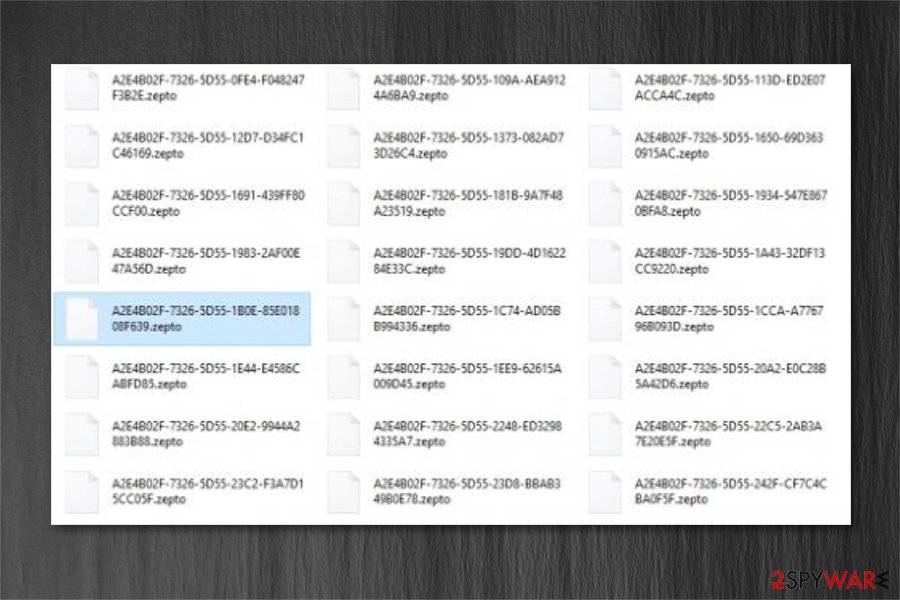
Zepto is not as advanced as its previous version. However, security experts have already started making the virus decryption tool which should be quite similar to Locky decrypter and should show up anytime soon. This virus was, and still is, one of the most powerful ransomware variants and none of the malware researchers attempts’ to create a decryption tool for it were successful.
Unfortunately, it seems that these cybercriminals know what they are doing, and they do take advantage of their programming skills because their malicious programs appear to be uncrackable. If you are reading this article and your computer is not infected yet, please follow these rules to protect your computer from this ransomware and avoid a need to deal with removal:
- Install anti-malware software on your computer to keep it protected from malicious viruses;
- Keep all your software up-to-date. Our tip is to enable automatic updates;
- BACK UP your files. In fact, this is the only way to secure your data from encryption. You have to create file copies and save them on a removable storage drive, and then unplug it from your computer. You can use backups in case your computer gets hit by ransomware;
- Never open suspicious emails or files attached to them! Cybercriminals distribute this virus by sending deceptive letters to thousands of email accounts, claiming that they deliver invoices, phone bills, speeding tickets, CV, or similar documents.
Ransomware spreads similarly to other cyber threats
This dangerous file-encrypting virus is distributed using well-known tactics — malicious spam emails which are holding deceptive attachments. Usually, the bogus scripts are embedded into .zip or .docm files. Hackers also employ social engineering methods to disguise the payload of the ransomware under innocent-looking file names.
Such malicious code can be activated via Word Macros function or by launching a JavaScript file, so make sure you don’t do that in case you see a scrambled text after opening a Word document that you have received via email.
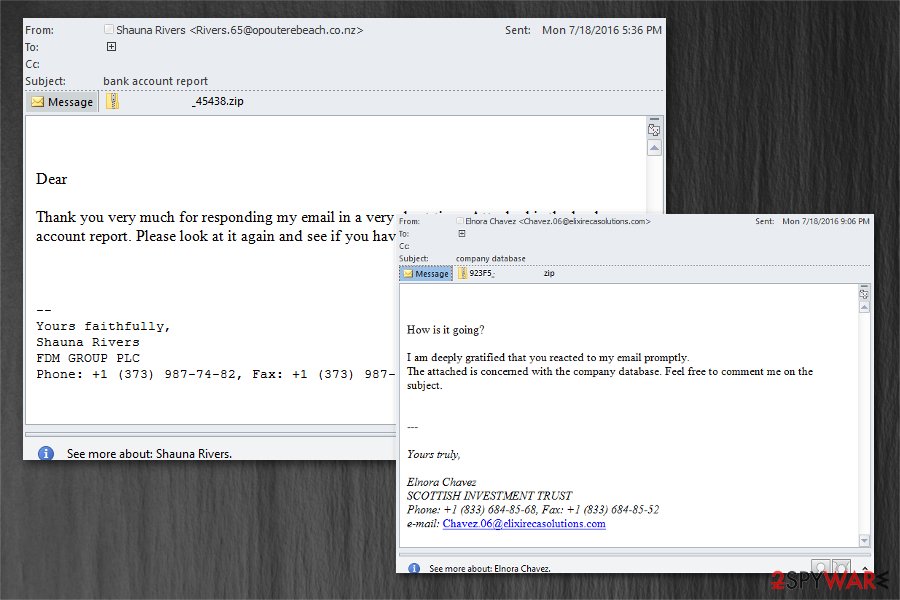
Criminals also send JS files, which can be activated just by opening them. Also, though such a method is not widely practiced, but beware of exploit kits. They might be trojans, rogue malware, or any malignant files.
By passing themselves off as legitimate files, they might slip into the system and then launch ransomware when the time comes. In order to decrease the possibility of such a malware attack, do not forget to update your security applications daily.
In general, we recommend you to avoid clicking or opening any kind of content online if you are not sure if it is secure. Cybercriminals use numerous techniques to deceive computer users, and it can be hard to keep up with the news and know all sources of infection.
We advise you to protect your computer with anti-malware software, backup your data, and refrain from opening emails sent from strangers. For more information about ceasing Zepto file hijack, take a look at this article — How to protect your computer from Locky? 5 tips for taking control.
Use an official decryption software for data recovery
Users who want to remove ransomware should keep in mind that this cyber threat is highly dangerous. Not only it can trick you into uninstalling essential system files, but also let other malicious programs inside your computer. Thus, follow the instructions to get rid of this file-encrypting virus safely.
Removal requires advanced IT knowledge. Likewise, we recommend you to get help from professional antivirus tools, like SpyHunter 5Combo Cleaner or Malwarebytes. They are designed to identify and locate all ransomware-related components to clean your entire computer system. To ensure that the machine runs just as well as prior to the infection and all the Windows system files are intact again, scan the device with FortectIntego.
Once you get rid of ransomware, you will be able to proceed to data recovery. You can decrypt files with the .zepto extension using an official decryption tool. It is presented at the end of this article alongside alternative solutions to retrieve compromised information.
Getting rid of Zepto virus. Follow these steps
Manual removal using Safe Mode
Ensure that the virus won't block an antivirus software by rebooting your PC into Safe Mode with Networking.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Zepto using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Zepto. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Zepto from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Zepto, you can use several methods to restore them:
Use Data Recovery Pro to recover your files encrypted by Zepto
Originally, Data Recovery Pro was created to retrieve the files after an unexpected system crash or simply after the careless elimination of the files. However, you can also try using it to recover your important files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Zepto ransomware;
- Restore them.
Rely on Windows Previous Versions functionality to recover files affected by Zepto
You should be able to recover the data using Windows Previous Versions feature if the System Restore was enabled on your computer. For that, use the following guide:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Use Shadow Explorer to decrypt encrypted files
One of the main features of ransomware, which helped it to retain the title among ransomware threats, is its ability to locate and delete the volume shadow copies. They are automatically created by the operating system in case a system is crashed unexpectedly. However, you should still try to recover your files encrypted by Zepto with the help of these steps:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption software
You might launch this utility to decode the files affected by ransomware.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Zepto and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Linas Kiguolis. You can now get infected with Locky ransomware through Facebook!. 2-Spyware. Project dedicated to helping people know more about spyware, malware, adware and other dangerous programs.
- ^ Looming Epidemic? Zepto Ransomware Found Spreading Via Massive Spam Campaign. Trend Micro Security News. Regular advisories regarding new viruses, including a guide to avoiding them in the first place.
- ^ Rick Correa. How Fast Does Ransomware Encrypt Files? Faster than You Think. Barkly Endpoint Security Blog. The latest endpoint security news, tips, and actionable insights.
- ^ Haley Sweetland Edwards. A Devastating Type of Hack Is Costing People Big Money. Time. Breaking news and analysis.
- ^ Eliminate computer threats. Virused. IT News and Virus Removal Guides for Swedish users.
- ^ Executable. Oxford Dictionaries. Free English dictionary and thesaurus.
- ^ Zepto virus file. VirusTotal. Free URL analysis service.





















