Accelers.cloud ads (scam) - Free Guide
Accelers.cloud ads Removal Guide
What is Accelers.cloud ads?
Accelers.cloud promotes scams and attempts to make people download potentially dangerous software

Accelers.cloud ads are something that users usually don't expect to encounter, as they are redirected to this site accidentally. Typically, it happens when people visit high-risk risk sites, such as those that distribute illegal programs or software cracks. In rarer cases, the reason for constant redirects and increased advertisement activity while browsing the web might indicate an infection of adware or another potentially unwanted application.[1]
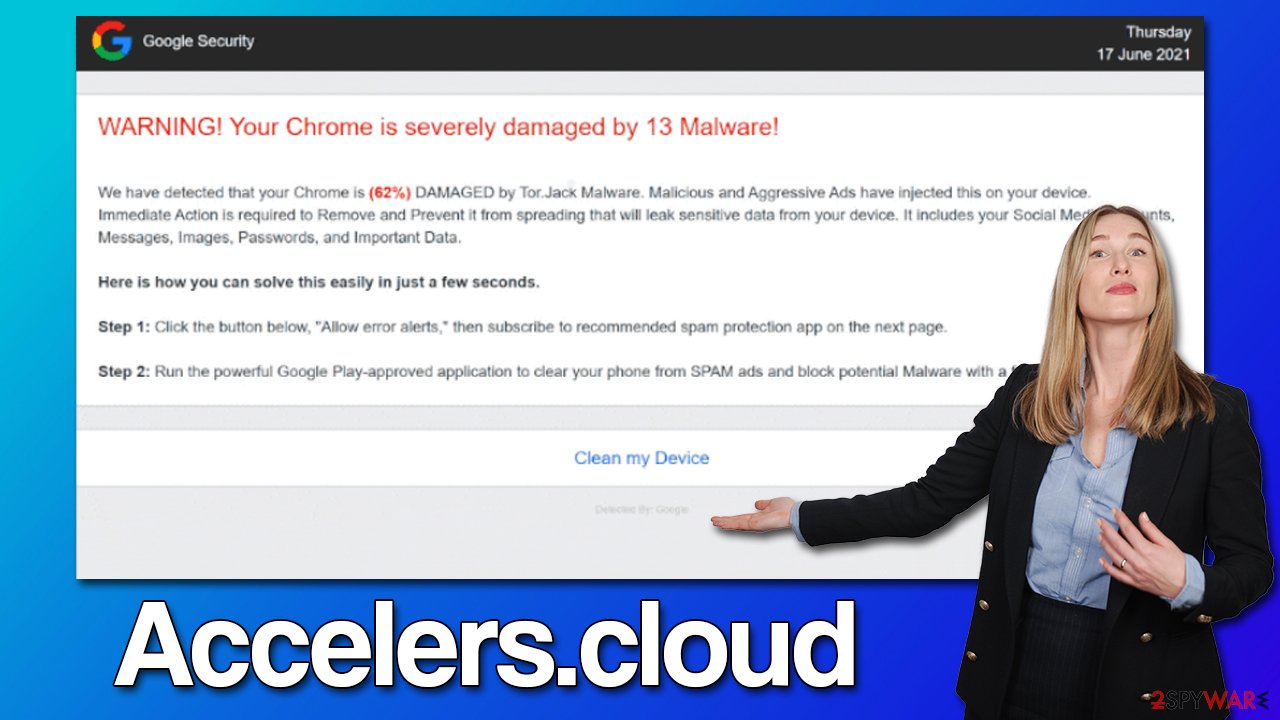
Once on Accelers.cloud, users can be exposed to a variety of scams, although most commonly, they are shown the popular “Your Chrome is severely damaged by 13 Malware” phishing[2] message. They are told that Chrome is damaged by a virus and that special software needs to be downloaded to remediate the situation.
The truth is that the authors of the scam are attempting to sell software in illegal ways – by misleading users by showing false statements. To make matters worse, websites like Accelers.cloud are also known to redirect users to other malicious websites that would ask to enable push notifications, download more PUPs, or disclose personal information.
| Name | Accelers.cloud |
| Type | Phishing, scam, adware, browser redirect |
| Operation | Claims that Chrome browser has been damaged by malware. It then asks users to download a fake security tool to remove it |
| Risks | Installation of potentially unwanted programs or malware, personal information disclosure to unknown parties/cybercriminals, monetary losses |
| Removal | You should not interact with the contents shown by a scam. Instead, check your system for adware or other malware with SpyHunter 5Combo Cleaner security software |
| Other tips | Employ FortectIntego to clean your system from PUP leftover files and fix any damage done by the virus |
How to recognize scam messages
The fake messages can be encountered in numerous locations online, including on hacked websites that are injected with malicious scripts,[3] links embedded within malicious websites, or malware could be causing these redirects. What matters the most here is people are exposed to scams unexpectedly, and it greatly affects how they react to them.
Besides, tech support and similar scams are known to abuse people who are less familiar with how computer infections work. The main goal of such fake messages is to frighten people and make them do actions they otherwise wouldn't – download potentially dangerous software or disclose their personal details.
Accelers.cloud hosts a variety of scams, and this is one you could be shown right after entering the site:
WARNING! Your Chrome is severely damaged by 13 Malware!
We have detected that your Chrome is (62%) DAMAGED by Tor.Jack Malware. Malicious and Aggressive Ads have injected this on your device.
Immediate Action is required to Remove and Prevent it from spreading that will leak sensitive data from your device. It includes your Social Media Accounts, Messages, Images, Passwords, and Important Data.Here is how you can solve this easily in just a few seconds.
Step 1: Click the button below, “Allow error alerts,” then subscribe to recommended spam protection app on the next page.
Step 2: Run the powerful Google Play-approved application to clear your phone from SPAM ads and block potential Malware with a few taps.
It is claimed that the system has been infected with the so-called Tor.Jack malware and that immediate action is required to fix the situation. In reality, such malware simply doesn't exist (even the name is fake), and the reason for rushing people is to trick them. It is simply impossible for a website to determine whether or not your system is infected unless it is riddled with vulnerabilities that the site has exploited. It is not what's happening on Accelers.cloud.
The best thing to do is to close down the tab that is showing the misleading content and not interacting with any of the buttons or links. Downloading software from such sites might result in malware infection or privacy issues, so you should stay away from it. If you have already installed something, you can easily fix the issue if you follow the instructions below.
Recovery instructions
Regardless of whether you have or haven't interacted with the scam material, you should make some system checks. Adware is one of the main reasons why you might be exposed to excessive ads and redirects to phishing websites.
The best solution for this is to scan the system with SpyHunter 5Combo Cleaner or Malwarebytes security software, as it can find and remove all the malicious programs and files automatically. Additionally, we recommend cleaning web browsers as explained below; if you choose automatic removal, you can skip the checks of extensions and installed programs.
Clean your browsers
Your first task is to find the unwanted extensions installed on your browser. The easiest way to access the list is by clicking the “Extensions” button next to the menu/settings panel and then selecting Remove/Uninstall.
To stop the unwanted tracking activities, you should remove cookies and other trackers from your computer. To do that, you should access browser settings or employ a powerful PC maintenance tool FortectIntego, which can also be used to fix any virus damage if such has occurred.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Remove suspicious programs
Adware could also be installed on the system level, and to address this, you would have to access Control Panel (Windows) or Applications (Mac) to get rid of it. It is worth noting that you shouldn't uninstall anything you have doubts about being useful – if you are not sure, simply leave this job for security software, as it would remove anything malicious installed on the device automatically.
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
While moving apps into Trash is usually how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Potentially unwanted program. Wikipedia. The Free Encyclopedia.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ Josep Albors. Malicious scripts in compromised websites and how to protect yourself. WeLiveSecurity. ESET security blog.







