BazarLoader malware (Removal Guide) - Free Instructions
BazarLoader malware Removal Guide
What is BazarLoader malware?
BazarLoader malware – dangerous backdoor operated by Trickbot cybercriminal group

BazarLoader is a malicious program categorized as a Trojan and a backdoor – it is designed to infiltrate Windows machines and grant the attackers secret access to them. Once installed, the malware can perform various malicious functions, although the main purpose of the threat is to deliver other malware. While the final payload is not defined and can be literally anything, cybersecurity experts observed a deployment of Ryuk ransomware, which encrypts all personal files on all the computers connected to the network and then demands a ransom for the decryption tool.
BazarLoader malware has been used by the same cybercriminals who were actively spreading the infamous Trickbot Trojan, usually delivered via spam email campaigns. Phishing emails might be highly targeted or sent to random users and include various topics, including COVID-19 pandemic, business inquiries, fake customer complaint forms, etc.
| Name | BazarLoader malware |
| Type | Trojan, Backdoor |
| Distribution | Malware was found |
| Additional payload | Malware delivers Ryuk ransomware as a final payload |
| First spotted | April 2020 |
| Functionality | BazarLoader virus is relatively simple yet effective Trojan and a backdoor that allows malicious actors to deliver other malware on the infected computer |
| Removal | To delete malware from your system, you should employ powerful security solutions. Access Safe Mode with Networking if the elimination process is unsuccessful in normal mode |
| System fix | Malware can seriously tamper and change Windows system files, to the point where the OS might become hardly operational after malware elimination. To avoid Windows reinstallation, we recommend first attempting to fix virus damage with FortectIntego |
The cybercriminal gang behind BazarLoader malware chose this malware due to its simplicity and increased obfuscation. Trickbot, which is considered one of the most prevalent Trojans in the world, has been analyzed by many leading security research groups, hence became much easier to detect and stop.
Despite this, many security solutions can detect and remove BazarLoader virus before it manages to cause any harm. One of the observed malicious email attachment samples (Print_Preview.exe) is detected as follows on Virus Total:[1]
- Trojan.GenericKD.43838874
- Backdoor:Win64/Zarab!MSR
- Trojan.Trickster.Gen
- Win64:CrypterX-gen [Trj]
- Win/malicious_confidence_100% (W)
- Trojan.Bazar
- A Variant Of Win64/Kryptik.CAK, etc.
The initial attack of BazarLoader malware starts with a phishing email that is often highly targeted. Many security researchers that analyzed the campaign uncovered that most of the emails are presented as customer complaints. Here is one of the examples:[2]
Why i can't reach you on the phone? I am on my way to XXX.
Because of customer complaint #7592 on you from last Friday, we will process termination process.
here is the copy in PDF: [Google docs link]Please call me back till i will process additional debit from your acc.
HR Manager
Since the link is directing to Google Docs, victims are more likely to proceed. Once the link is clicked, they are redirected to a web-based PDF document, which includes another link. This time, by clicking on it, users would begin the installation of the BazarLoader malware.
As soon as the infection process is complete, the virus will install the BazarBackdoor part of the payload, which would inject malicious components into legitimate Windows processes, such as cmd.exe, explorer.exe, and svchost.exe. During this time, a scheduled task is also established on the system for the malware to start with each Windows boot.[3] After performing some more downloads, BazarLoader malware will finally deploy Ryuk ransomware.
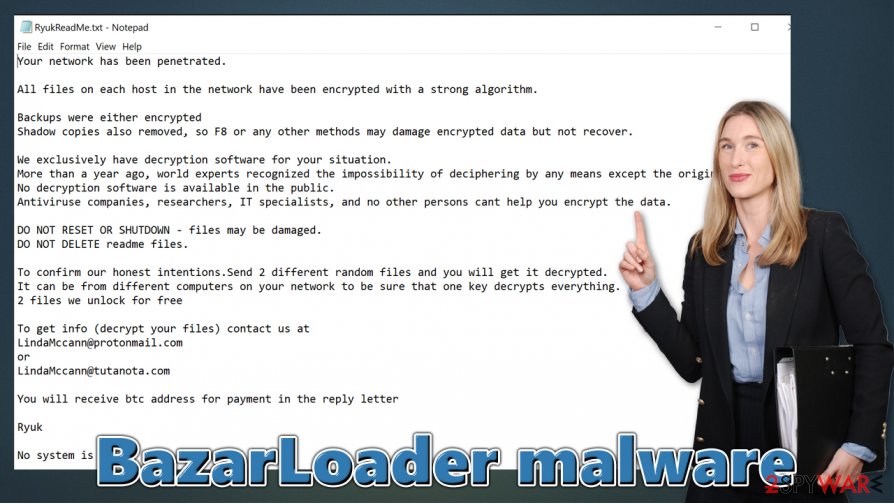
Once that is complete, malicious actors can ask victims for high sums as ransoms (typically, 10 to 50 bitcoin – approx. $114k – $570k at the time of the writing) for data recovery. Thus, BazarLoader seems like a great choice for cybercriminals due to low detection rates, which also guarantees high profits due to the ransomware component within the campaign.
BazarLoader malware removal is not the hardest process as long as adequate security software (such as SpyHunter 5Combo Cleaner or Malwarebytes) is used, although the encrypted files or a data leak can be the most devastating side-effects of the infection. Once you delete malware from the system, experts also recommend scanning the device with a repair tool such as FortectIntego to prevent reinstallation of the operating system. Below you will also find alternative ways for data recovery.
How to spot phishing emails and prevent malware infection
Email spam is among the most prominent methods for malware delivery. While the principle remains the same from many years ago, cybercriminals employ new techniques to make fake emails more believable and can obfuscate them from automatic scanners. For example, Gmail and other reputable email providers scan each of the received emails, put the suspicious ones in the Junk folder, and mark it as “Dangerous.” Despite these efforts, many users still believe that the warning is a false-positive and proceed with clicking on attachments or the embedded links.
As previously mentioned, BazarLoader virus authors exploit the most relevant topics, such as coronavirus pandemic or the typical scare tactics. Besides, since they often include a link to Google Docs, many users are more inclined to click on it. Nonetheless, it is also known that cybercriminals employ malicious documents. In such a case, by enabling content within an attachment (DOC, PDF, and similar formats), victims would immediately begin the infection process.
There are several experts' tips[4] that could prevent the devastating infection from occurring:
- Never allow documents attached to emails to run macro function (“Allow Content”);
- Employ additional email protection solutions;
- Upload attachments to Virus Total or similar analysis tools;
- Watch out for suspicious sender address;
- Do not give into fear and click on links/files without examining them.
Keep in mind that the sender's address, buttons, links, and other attributes can be faked by skilled criminals, so the most important criteria here is not to rush things and practice extreme caution when dealing with unexpected emails.
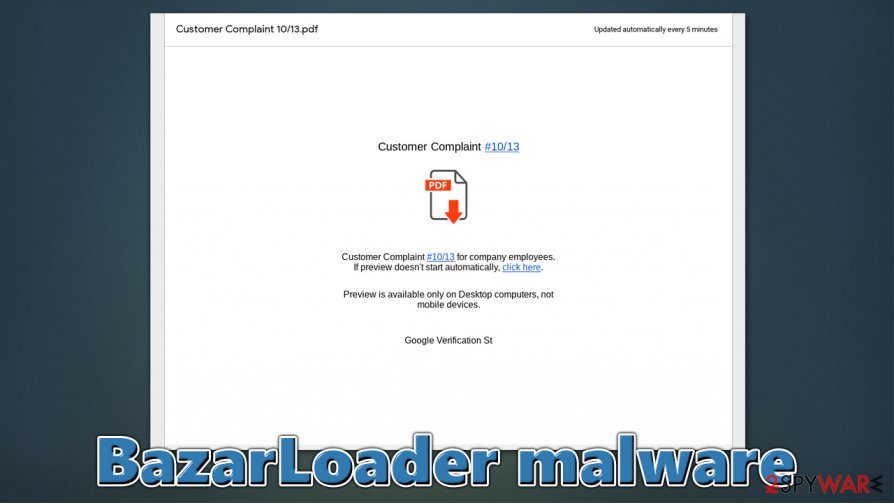
BazarLoader malware removal steps
It is important to note that BazarLoader malware removal is not the only payload that you have to eliminate from the system. As previously mentioned, the virus would also deliver ransomware as a secondary payload. And while the elimination process for it does not differ much than the other malware's, its consequences are much more sinister. All the pictures, music, videos, documents, and other personal files will be locked even after you fully remove BazarLoader and Ryuk from the computer.
If your files were encrypted and you have no backups, make a copy of the data for the possible solution in the future. Then, download and install SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable anti-malware and perform a full system scan – accesses Safe Mode if required. After getting rid of the BazarLoader virus and Ryuk ransomware, attempt to fix Windows system damage with FortectIntego repair tool. Finally, follow the data recovery instructions we provide below, although keep in mind that the success rate of retrieving data fully is relatively low.
Getting rid of BazarLoader malware. Follow these steps
Manual removal using Safe Mode
Access Safe Mode with Networking if malware is tampering with your security tools:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove BazarLoader malware using System Restore
System Restore can also be effective when trying to remove malicious programs:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of BazarLoader malware. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove BazarLoader malware from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by BazarLoader malware, you can use several methods to restore them:
Employ Data Recovery Pro for file restoration
In some cases, Employ Data Recovery Pro could recover at least some of the affected files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by BazarLoader malware ransomware;
- Restore them.
Windows Previous Versions feature might be useful
In case malware failed to delete Shadow Copies, you can attempt to recover files one-by-one.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Take control of your files with ShadowExplorer
This tool can automate data recovery if Shadow Copies are still present on the PC.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from BazarLoader malware and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting backdoors
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ 34cc67888cd38da7aeb52508b48ad71287c402aecb72bccca7cbd3a0cd8fe985. Virus Total. File and URL analysis.
- ^ BazarLoader Campaign with Fake Termination Emails. Hornet Security. Threat research blog.
- ^ Lawrence Abrams. BazarLoader used to deploy Ryuk ransomware on high-value targets. Bleeping Computer. IT and cybersecurity.
- ^ Senzavirus. Senzavirus advice and malware insights.





















