Bit Search redirect (Removal Instructions) - updated Dec 2019
Bit Search redirect Removal Guide
What is Bit Search redirect?
Bit Search – a browser hijacker that can set the web browser's search engine to only-search.com
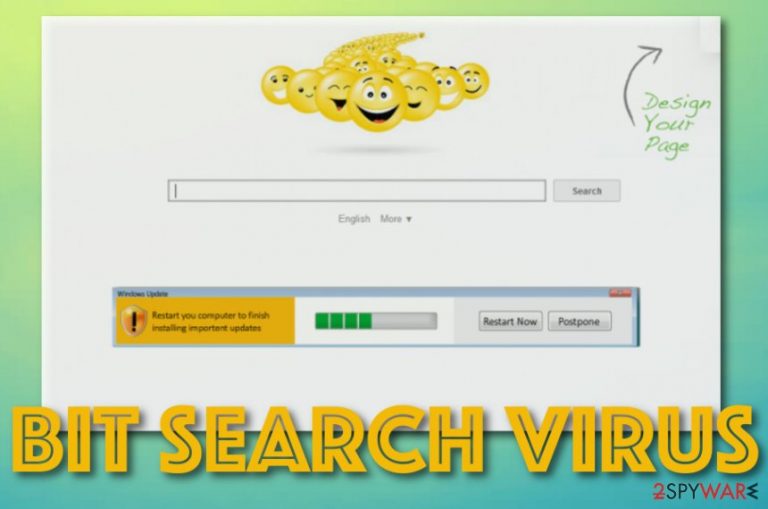
Bit Search is a search engine that has been getting increasingly popular on the Internet, but, unfortunately, not in a positive way. Security experts started noticing that it is acting in a misleading manner and seeks to infiltrate random computers without being noticed. Later on, they have found out that this suspicious search engine is employed by suspicious third parties in order to take over users' search sessions and make them visit predetermined websites. That is why various reputable security vendors have labeled Bit Search as a browser hijacker[1] and a potentially unwanted program.
If you are reading this article due to the fact that you have found Bit-Search.com as your homepage, new tab URL bar, and search engine, then you should take needed actions to restore DNS settings of your web browsers. Besides, this browser hijacker is capable of setting the search engine to another unreliable one named only-search.com.
| Name | Bit Search |
|---|---|
| Type | Browser hijacker/potentially unwanted program |
| Danger level | Low. It does not destroy the computer or lock files. However, redirects can take you to potentially malicious locations |
| Search engine | This browser-hijacking app can set the default search engine to Bit-Search.com or to only-search.com |
| Activities | Besides modifying major browser settings, the PUP can load the user's browser sessions with unwanted advertisements, redirects, and collect information related to the user's browsing history |
| Removal | You can use automatical or manual removal guidelines to get rid of this potentially unwanted program. Employ reliable software or go to the end of this article and check the step-by-step instructions there |
| Fixing | If you have discovered some system compromisation after the browser hijacker attack, you can try recovering the machine with the help of software such as FortectIntego |
You should never rely on search engines that you are not familiar with, especially the ones that have infiltrated your computer without being noticed and Bit Search is definitely one of them. As we have already mentioned, this rogue app has been created in order to serve third-parties and increase their page rank or sales.
That is why you can expect to receive altered search results from this plug-in. It may deliver you sponsored links in the priority and you may not even suspect that you are visiting suspicious websites. Bit Search can get you easily involved in redirecting sessions some of which might accidentally force you to land on a malware-laden location.
By the way, when people use this search provider willingly, it becomes an easy task for its developers to investigate users' search queries, websites that they visit and other personally non-identifiable information without asking the user's permission. Be aware that Bit Search might be capable of collecting the following information:
- Commonly visited websites;
- Hyperlinks and ads accessed;
- Bookmarks[2] saved;
- Offers and deals searched;
- Your IP address;
- Geolocation.
In some cases, Bit Search might get the hold of your email address and you might start receiving dozens of spam messages in your email's Spam section. The main goal of collecting information that we mentioned before is to get users involved in targeted advertising where the developers can benefit from each click.
Bit Search can provide you with various bogus offers and deals that force you to believe in needing a particular product or service when you truly do not need them. You might also be provided with offers to purchase rogue security products which you have to deny, otherwise, you will end up spending money for a completely useless app.
Regarding the frequency of the activities that are promoted by Bit Search, your web browsers might start struggling to perform search queries and experience constant freezes. The same might happen to your computer if the browser hijacker starts overusing your system's resources such as the CPU's[3] energy.
Bit Search removal is a way to prevent these things from happening. The potentially unwanted program should be eliminated not only from the computer system but also from web browser apps such as Google Chrome, Mozilla Firefox, Internet Explorer, Microsoft Edge, and Safari that might be filled with PUP-related objects.
When you remove Bit Search completely, you can start looking for system compromisation signs. Due to the fact that PUPs can bring other PUPs or even malware to the computer, some system objects of yours might have gotten affected by this factor. If there is some damage to fix, try repairing it with software such as FortectIntego.
The appearance of browser hijackers
If you are one of those users who do not pay enough attention to the installation process of free programs, it is very likely that one day you will find your default search engine and homepage modified too questionable new ones. Browser-hijacking products are inseparable from various freeware and shareware installations.
The PUP comes as an optional download to various download managers, video and audio players, PDF converters, and other similar programs that are promoted on various download websites for free, for example, cnet.com, download.com, softonic.com, soft32.com. This so-called “bundling” distribution method is misleading and very frequently tricks people into accepting various PUPs without even noticing them.
If you want to avoid this, always select the Advanced or Custom installation and follow the process with extreme carefulness. Deselect all unfamiliar programs that may be suggested to you and under any circumstance do not accept to install any unrecognizable plug-ins and modify your web browser's DNS settings.
Continuously, browser hijackers might appear on third-party websites injected into specific advertisements, hyperlinks, or fake software updates. According to cybersecurity specialists from LesVirus.fr,[4] you should prevent yourself from visiting unsecured pages and always have reliable antimalware protection running that will inform you if some type of threat is trying to invade your computer system.
Removing Bit Search virus
It is always recommended to get rid of Bit Search virus and similar hijackers, adware and other PUPs automatically because they may have inserted various registries into your computer system. These components might be difficult to detect sometimes by the human eye as they can be deeply hidden. However, if you are not fond of using additional software, you can follow the guidelines that are below and remove Bit Search by using your own effort.
Keep in mind that manual Bit Search removal requires a big variety of activities that includes not only deleting the program from your Windows or Mac computer. The browser hijacker probably filled your browser apps with unwanted content such as extensions, plug-ins, and add-ons. If you want to get rid of the cyber threat properly, you will have to clean browsers such as Google Chrome, Mozilla Firefox, Safari, Microsoft Edge, and Internet Explorer.
You may remove virus damage with a help of FortectIntego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
Getting rid of Bit Search redirect. Follow these steps
Uninstall from Windows
To eliminate the bogus app from your Windows PC, apply the following guiding steps.
Instructions for Windows 10/8 machines:
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

If you are Windows 7/XP user, proceed with the following instructions:
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
Delete from macOS
To get rid of unwanted programs from your macOS system, use the below-provided guidelines.
Remove items from Applications folder:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Remove from Microsoft Edge
Delete unwanted extensions from MS Edge:
- Select Menu (three horizontal dots at the top-right of the browser window) and pick Extensions.
- From the list, pick the extension and click on the Gear icon.
- Click on Uninstall at the bottom.

Clear cookies and other browser data:
- Click on the Menu (three horizontal dots at the top-right of the browser window) and select Privacy & security.
- Under Clear browsing data, pick Choose what to clear.
- Select everything (apart from passwords, although you might want to include Media licenses as well, if applicable) and click on Clear.

Restore new tab and homepage settings:
- Click the menu icon and choose Settings.
- Then find On startup section.
- Click Disable if you found any suspicious domain.
Reset MS Edge if the above steps did not work:
- Press on Ctrl + Shift + Esc to open Task Manager.
- Click on More details arrow at the bottom of the window.
- Select Details tab.
- Now scroll down and locate every entry with Microsoft Edge name in it. Right-click on each of them and select End Task to stop MS Edge from running.

If this solution failed to help you, you need to use an advanced Edge reset method. Note that you need to backup your data before proceeding.
- Find the following folder on your computer: C:\\Users\\%username%\\AppData\\Local\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe.
- Press Ctrl + A on your keyboard to select all folders.
- Right-click on them and pick Delete

- Now right-click on the Start button and pick Windows PowerShell (Admin).
- When the new window opens, copy and paste the following command, and then press Enter:
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register “$($_.InstallLocation)\\AppXManifest.xml” -Verbose

Instructions for Chromium-based Edge
Delete extensions from MS Edge (Chromium):
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Clear cache and site data:
- Click on Menu and go to Settings.
- Select Privacy, search and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Reset Chromium-based MS Edge:
- Click on Menu and select Settings.
- On the left side, pick Reset settings.
- Select Restore settings to their default values.
- Confirm with Reset.

Remove from Mozilla Firefox (FF)
Remove dangerous extensions:
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the top-right of the window).
- Select Add-ons.
- In here, select unwanted plugin and click Remove.

Reset the homepage:
- Click three horizontal lines at the top right corner to open the menu.
- Choose Options.
- Under Home options, enter your preferred site that will open every time you newly open the Mozilla Firefox.
Clear cookies and site data:
- Click Menu and pick Settings.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

Reset Mozilla Firefox
If clearing the browser as explained above did not help, reset Mozilla Firefox:
- Open Mozilla Firefox browser and click the Menu.
- Go to Help and then choose Troubleshooting Information.

- Under Give Firefox a tune up section, click on Refresh Firefox…
- Once the pop-up shows up, confirm the action by pressing on Refresh Firefox.

Remove from Google Chrome
To clean Google Chrome from suspicious products, apply these below-provided instructions.
Delete malicious extensions from Google Chrome:
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Clear cache and web data from Chrome:
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Change your homepage:
- Click menu and choose Settings.
- Look for a suspicious site in the On startup section.
- Click on Open a specific or set of pages and click on three dots to find the Remove option.
Reset Google Chrome:
If the previous methods did not help you, reset Google Chrome to eliminate all the unwanted components:
- Click on Menu and select Settings.
- In the Settings, scroll down and click Advanced.
- Scroll down and locate Reset and clean up section.
- Now click Restore settings to their original defaults.
- Confirm with Reset settings.

Delete from Safari
To wipe out unwanted components from Safari, use the following guidelines.
Remove unwanted extensions from Safari:
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

Clear cookies and other website data from Safari:
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Reset Safari if the above-mentioned steps did not help you:
- Click Safari > Preferences…
- Go to Advanced tab.
- Tick the Show Develop menu in menu bar.
- From the menu bar, click Develop, and then select Empty Caches.

After uninstalling this potentially unwanted program (PUP) and fixing each of your web browsers, we recommend you to scan your PC system with a reputable anti-spyware. This will help you to get rid of Bit Search registry traces and will also identify related parasites or possible malware infections on your computer. For that you can use our top-rated malware remover: FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes.
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Margaret Rouse. Browser hijacker (browser hijacking). Search Security. Tech Target.
- ^ Bookmark. Techopedia. Tech terms and definitions.
- ^ CPU. Computer Hope. Free computer help since 1998.
- ^ LesVirus.fr. LesVirus. Security and spyware news.
