Black Basta ransomware (virus) - Free Guide
Black Basta virus Removal Guide
What is Black Basta ransomware?
Black Basta ransomware is a malicious program designed to encrypt all files on Windows systems
Black Basta is a ransomware-type virus that was created by cybercriminals for money extortion purposes. First spotted at the end of April 2022, malware has already hit some major targets, including American Dental Association (ADA). The ransomware is just one of many strains that focuses on big game hunting attacks, targeting high-profile entities while threatening to leak their data if the ransom is not paid in time.
| Name | Black Basta virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .basta |
| Ransom note | readme.txt |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
Black Basta virus infection and data encryption
As soon as the infection manages to breach and compromise the network and individual machines, it begins the data encryption process immediately. It locates and locks all pictures, documents, databases, and other files with the help of a combination of strong algorithms known as RSA and AES. Suchlike files then all end up being marked with the “.basta” extension and lose their default file icons.
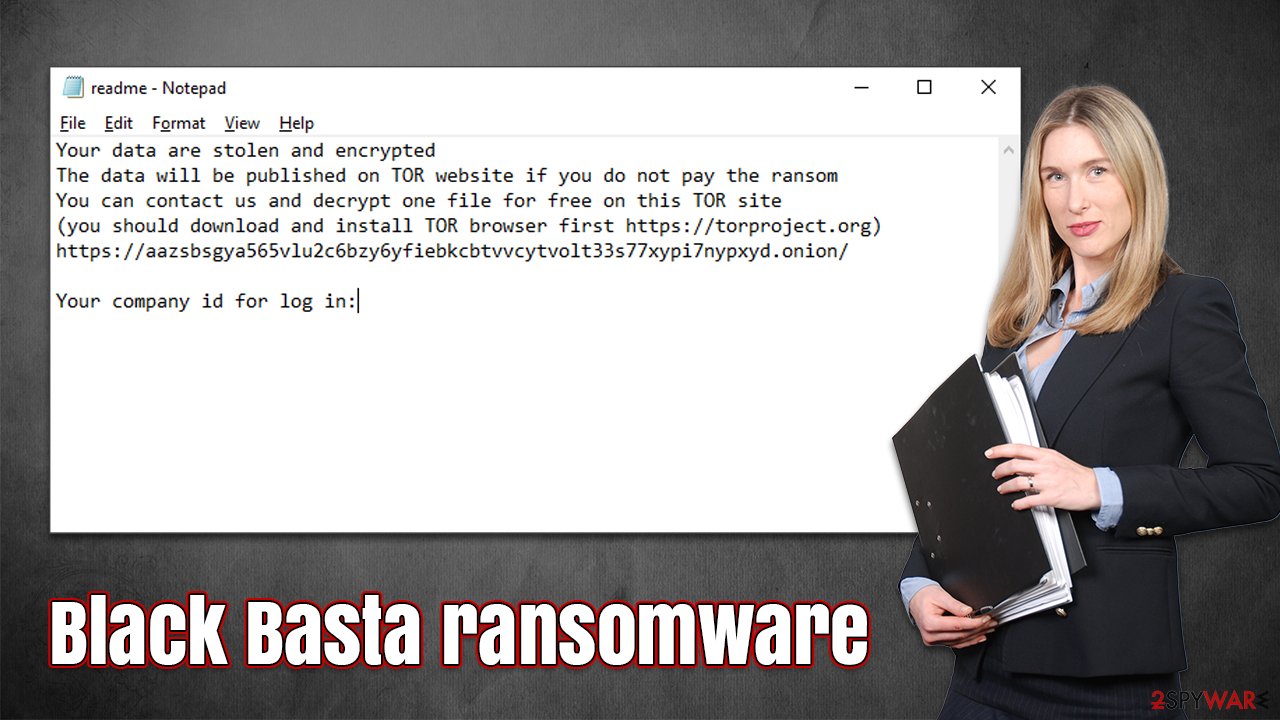
After this, Black Basta ransomware changes the background of the affected machine and also opens a ransom note file named “readme.txt,” which includes basic information and demands from cybercriminals. Attacks on corporations usually result in larger ransom demands, which can reach millions (depending on the company size). Message example:
Your data are stolen and encrypted
The data will be published on TOR website if you do not pay the ransom
You can contact us and decrypt one file for free on this TOR site
(you should download and install TOR browser first https://torproject.org)
https://aazsbsgya565vlu2c6bzy6yfiebkcbtvvcytvolt33s77xypi7nypxyd.onion/Your company id for log in:
If contacted through the provided means, cybercriminals explain victims have seven days before stolen sensitive information would begin to be leaked or sold to the highest bidder.
Since companies almost always store data backups, file encryption becomes much less effective, so hackers came up with additional extortion techniques by transferring sensitive files over to their servers. Due to this, each major ransomware attack is now considered a company's data breach.
Attack on ADA
The 22nd of April was a memorable day for American Dental Association – not in a good way, as it was hit by the Black Basta ransomware attack. ADA is a major association of dentists that provides training courses for more than 175k members. While the association does not fully disclose the scope of the attack, an email sent to all employees pains a much clearer picture:[1]
On Friday, the ADA fell victim to a cybersecurity incident that caused a disruption to certain systems, including Aptify and ADA email, telephone and Web chat. Upon discovery, the ADA immediately responded by taking affected systems offline and commenced an investigation into the nature and scope of the disruption,
The attack left ADA without its vital systems – communication emails, web chat, phones, and various online services had to be shut down. The official website was also inoperational, with the message stating that ADA is experiencing technical difficulties. The attack is now under investigation. According to some sources, the stolen information consisting of 2.8GB of data has already been published on the underground forums for sale.
Ransomware removal
The first task after a ransomware attack is making sure that network communications are removed as soon as possible, which includes disconnecting every machine connected to a network. To do that, follow these steps:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Once you are sure that the system is no longer connected to the network, you should use reputable anti-malware software to perform a full system scan with it. Security software, such as SpyHunter 5Combo Cleaner or Malwarebytes, can find and remove all the malicious components from the system at once, along with any secondary payloads that might be present on the system.
Data recovery
One of the first things to try when trying to recover encrypted data is employing software designed for similar situations. If you have no backups for your encrypted files, it is vital that you copy the encrypted files onto another medium before you proceed. Otherwise, the files might get corrupted and would be irretrievable even with a working decryptor.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Black Basta ransomware Black Basta ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Security experts are known to work on decryption tools for major ransomware strains. In some cases, bugs[2] within the encryption process can be found or criminals' servers seized by authority agencies. In any case, you could look for decryptors on the following websites, although keep in mind it might take a while until there's a working one made.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
System fix
Malware can cause tremendous damage to Windows systems to the point where a full reinstallation could be required. For example, an infection can alter the Windows registry[3] database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Antivirus software can't repair damaged files, and a specialized app should be used instead.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
We recommend reporting the incident to your local authorities that deal with fraud.
Getting rid of Black Basta virus. Follow these steps
Report the incident to your local authorities
Ransomware is a huge business that is highly illegal, and authorities are very involved in catching malware operators. To have increased chances of identifying the culprits, the agencies need information. Therefore, by reporting the crime, you could help with stopping the cybercriminal activities and catching the threat actors. Make sure you include all the possible details, including how did you notice the attack, when it happened, etc. Additionally, providing documents such as ransom notes, examples of encrypted files, or malware executables would also be beneficial.
Law enforcement agencies typically deal with online fraud and cybercrime, although it depends on where you live. Here is the list of local authority groups that handle incidents like ransomware attacks, sorted by country:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Lawrence Abrams. American Dental Association hit by new Black Basta ransomware. Bleeping Computer. Technology news and support.
- ^ Software bug. Wikipedia. The free encyclopedia.
- ^ Tim Fisher. What Is the Windows Registry?. Lifewire. Tech News, Reviews, Help & How-Tos.












