Bulwark ransomware (virus) - Free Guide
Bulwark virus Removal Guide
What is Bulwark ransomware?
Bulwark ransomware is a MedusaLocker variant that can be devastating to those affected
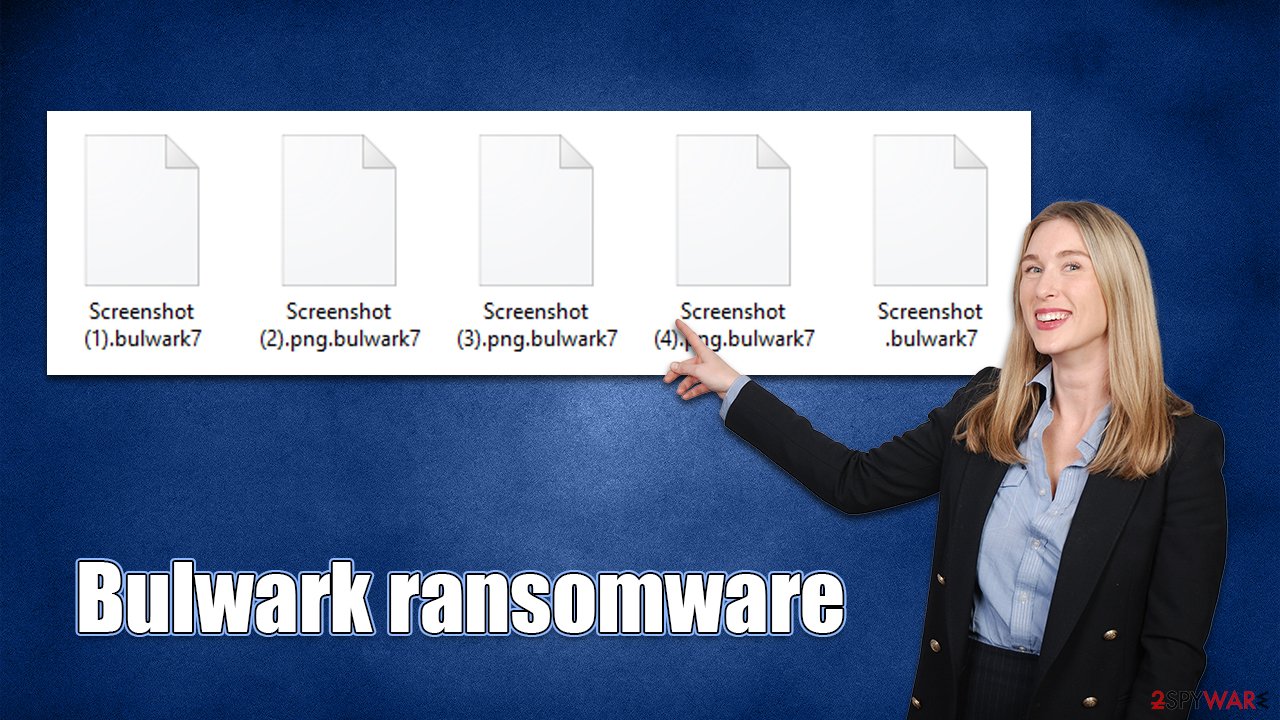
Bulwark is a ransomware-type virus that first emerged in mid-October 2022. It encrypts all personal files on the target machine and holds them hostage so that victims would have to pay them money in exchange for a decryption tool that is meant to restore the data. All personal files are affected, including pictures, documents, and databases, all of which receive the .bulwark7 extension. Just like it's common to MedusaLocker variants, data is encrypted with a combination of AES and RSA encryption algorithms, making a recovery without the key difficult, if not impossible.
After the Bulwark virus encrypts files, it delivers a ransom note !-Recovery_Instructions-!.html, which is opened via the browser window. According to the message, hackers claim that they have hacked the whole network, and victims have only 72 hours for negotiation – they need to write an email to ithelp09@wholeness.business or ithelp09@decorous.cyou to begin talks about the payment. Experts recommend avoiding this and seeking alternative solutions for remediation.
| Name | Bulwark |
|---|---|
| Type | Ransomware, file-locking malware, cryptovirus |
| File extension | .bulwark7 |
| Ransom note | !-Recovery_Instructions-!.html |
| Encryption | AES + RSA |
| Data Recovery | If no backups are available, recovering data is almost impossible. However, we suggest you try the alternative methods that could help you in some cases – we list them below |
| Malware removal | Manual virus removal is not recommended, as it might be difficult for regular users. Instead, SpyHunter 5Combo Cleaner or other anti-malware tools should be used |
| System fix | Malware can seriously impact a Windows computer's performance and stability after it is removed. We recommend scanning the system with FortectIntego to remedy it and avoid significant stability issues |
The data-stealing trick
Some ransomware strains focus on home users (for example, Djvu versions Powz and Adlg) – these attacks are usually high in volume, and more smaller ransoms can be acquired this way. In the case of Bulwark ransomware, its attacks are focused mainly on businesses and organizations. Corporate entities are then demanded large sums of money that most regular people would never be able to pay.
All the details about the attack can be found on a rather extensive ransom note, delivered in an HTML format. The full message reads as follows:
If you get this message, your network was hacked!
After we gained full access to your servers, we first downloaded a large amount of sensitive data and then encrypted all the data stored on them.That includes personal information on your clients, partners, your personnel, accounting documents, and other crucial files that are necessary for your company to work normally.
We used modern complicated algorithms, so you or any recovery service will not be able to decrypt files without our help, wasting time on these attempts instead of negotiations can be fatal for your company.
Make sure to act within 72 hours or the negotiations will be considered failed!
Inform your superior management about what's going on.
Contact us for price and get decryption software.
Contact us by email:
ithelp09@wholeness.business
If you will get no answer within 24 hours contact us by our alternate emails:
ithelp09@decorous.cyou
To verify the possibility of the recovery of your files we can decrypted 1-3 file for free.
Attach file to the letter (no more than 5Mb).
If you and us succeed the negotiations we will grant you:
complete confidentiality, we will keep in secret any information regarding to attack, your company will act as if nothing had happened.
comprehensive information about vulnerabilities of your network and security report.
software and instructions to decrypt all the data that was encrypted.
all sensitive downloaded data will be permanently deleted from our cloud storage and we will provide an erasure log.
Our options if you act like nothing's happening, refuse to make a deal or fail the negotiations:
inform the media and independent journalists about what happened to your servers. To prove it we'll publish a chunk of private data that you should have ciphered if you care about potential breaches. Moreover, your company will inevitably take decent reputational loss which is hard to assess precisely.
inform your clients, employees, partners by phone, e-mail, sms and social networks that you haven't prevent their data leakage. You will violate laws about private data protection.
start DDOS attack on you website and infrastructures.
personal data stored will be put on sale on the Darknet to find anyone interested to buy useful information regarding your company. It could be data mining agencies or your market competitors.
publish all the discovered vulnerabilities found in your network, so anyone will do anything with it.
Why pay us?
We care about our reputation. You are welcome to google our cases up and be sure that we don't have a single case of failure to provide what we promissed.Turning this issue to a bug bounty will save your private information, reputation and will allow you to use the security report and avoid this kind of situations in future.
Your personal ID
Ransomware authors continue to find new methods to extort money from victims. Attacks against corporate networks did not prove as successful before, as companies usually have reliable backup systems installed. As a result, there's no need for the ransom developers to get paid – all the data is simply restored from backups.
Cybercriminals then came up with an idea to steal sensitive corporate information during the attack, which can be used to blackmail victims. As seen in this ransom note, there are plenty of threats about disclosing the information to third parties and underground cybercrime communities, as well as employing DDoS attacks[1] against the company.
Despite this, paying the attackers can be extremely risky. There is no guarantee that they won't publish the data regardless of whether the ransom payment was made or not. Therefore, we recommend avoiding all communication with the attackers and using alternative solutions instead – the recovery begins with Bulwark ransomware removal.
Tackling the infection
During the infection phase, ransomware frequently establishes an internet connection with a remote Command & Control[2] server. This gives the attackers the ability to carry out a number of malicious activities, such as updating their malware or sending additional commands. In order to prevent reinfection, the network connection should also be blocked off. Before beginning the ransomware removal process, disconnect your computer from the network as follows:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
While some ransomware does have a tendency to self-destruct after encrypting data, this isn't always the case. For instance, it frequently spreads alongside other malware, such as data stealers or keyloggers.[3] Therefore, getting rid of all malware components at once is crucial. The simplest approach is using powerful anti-malware software, like SpyHunter 5Combo Cleaner or Malwarebytes – it can locate all the malicious components, quarantine them, and then remove them securely.
In some cases, security software's operation may be hindered by malware, which may result in incomplete removal or other issues. In such a case, you can access Safe Mode and perform Bulwark virus removal from there:
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing the F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.
![Windows XP/7 Windows XP/7]()
Windows 10 / Windows 8
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Recovery Recovery]()
- Select Troubleshoot.
![Choose an option Choose an option]()
- Go to Advanced options.
![Advanced options Advanced options]()
- Select Startup Settings.
![Startup settings Startup settings]()
- Click Restart.
- Press 5 or click 5) Enable Safe Mode with Networking.
Fixing damaged system files
Malware can cause tremendous damage to Windows systems to the point where a full reinstallation could be required. For example, an infection can alter the Windows registry database, damage vital bootup, and other sections, delete or corrupt DLL files, etc. Antivirus software can't repair damaged files, and a specialized app should be used instead.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
Data recovery explained
Although the FBI and security experts generally discourage paying ransoms or even contacting cybercriminals, the victim's choice is always final. But keep in mind that by paying the ransom, you're only encouraging the attackers to create more malware and infect other people because it shows the profitable nature of the illicit business. Maintaining safe data backups, which can be done using reliable services like Google Drive or OneDrive, is the only way to prevent the devastation caused by a ransomware attack. We give recommendations for this below.
As evident, the safest way to restore encrypted files is by using backups. If you don't have working backups or they were encrypted as well, you could try using third-party recovery software or waiting for a decryptor to be developed by security researchers, which may or may not happen.
Getting rid of Bulwark virus. Follow these steps
Restore files using data recovery software
Since many users do not prepare proper data backups prior to being attacked by ransomware, they might often lose access to their files permanently. Paying criminals is also very risky, as they might not fulfill the promises and never send back the required decryption tool.
While this might sound terrible, not all is lost – data recovery software might be able to help you in some situations (it highly depends on the encryption algorithm used, whether ransomware managed to complete the programmed tasks, etc.). Since there are thousands of different ransomware strains, it is immediately impossible to tell whether third-party software will work for you.
Therefore, we suggest trying regardless of which ransomware attacked your computer. Before you begin, several pointers are important while dealing with this situation:
- Since the encrypted data on your computer might permanently be damaged by security or data recovery software, you should first make backups of it – use a USB flash drive or another storage.
- Only attempt to recover your files using this method after you perform a scan with anti-malware software.
Install data recovery software
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.

Find a working decryptor for your files
File encryption is a process that is similar to applying a password to a particular file or folder. However, from a technical point of view, encryption is fundamentally different due to its complexity. By using encryption, threat actors use a unique set of alphanumeric characters as a password that can not easily be deciphered if the process is performed correctly.
There are several algorithms that can be used to lock data (whether for good or bad reasons); for example, AES uses the symmetric method of encryption, meaning that the key used to lock and unlock files is the same. Unfortunately, it is only accessible to the attackers who hold it on a remote server – they ask for a payment in exchange for it. This simple principle is what allows ransomware authors to prosper in this illegal business.
While many high-profile ransomware strains such as Djvu or Dharma use immaculate encryption methods, there are plenty of failures that can be observed within the code of some novice malware developers. For example, the keys could be stored locally, which would allow users to regain access to their files without paying. In some cases, ransomware does not even encrypt files due to bugs, although victims might believe the opposite due to the ransom note that shows up right after the infection and data encryption is completed.
Therefore, regardless of which crypto-malware affects your files, you should try to find the relevant decryptor if such exists. Security researchers are in a constant battle against cybercriminals. In some cases, they manage to create a working decryption tool that would allow victims to recover files for free.
Once you have identified which ransomware you are affected by, you should check the following links for a decryptor:
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors

If you can't find a decryptor that works for you, you should try the alternative methods we list below. Additionally, it is worth mentioning that it sometimes takes years for a working decryption tool to be developed, so there are always hopes for the future.
Create data backups to avoid file loss in the future
One of the many countermeasures for home users against ransomware is data backups. Even if your Windows get corrupted, you can reinstall everything from scratch and retrieve files from backups with minimal losses overall. Most importantly, you would not have to pay cybercriminals and risk your money as well.
Therefore, if you have already dealt with a ransomware attack, we strongly advise you to prepare backups for future use. There are two options available to you:
- Backup on a physical external drive, such as a USB flash drive or external HDD.
- Use cloud storage services.
The first method is not that convenient, however, as backups need to constantly be updated manually – although it is very reliable. Therefore, we highly advise choosing cloud storage instead – it is easy to set up and efficient to sustain. The problem with it is that storage space is limited unless you want to pay for the subscription.
Using Microsoft OneDrive
OneDrive is a built-in tool that comes with every modern Windows version. By default, you get 5 GB of storage that you can use for free. You can increase that storage space, but for a price. Here's how to setup backups for OneDrive:
- Click on the OneDrive icon within your system tray.
- Select Help & Settings > Settings.

- If you don't see your email under the Account tab, you should click Add an account and proceed with the on-screen instructions to set yourself up.

- Once done, move to the Backup tab and click Manage backup.

- Select Desktop, Documents, and Pictures, or a combination of whichever folders you want to backup.
- Press Start backup.

After this, all the files that are imported into the above-mentioned folders will be automatically backed for you. If you want to add other folders or files, you have to do that manually. For that, open File Explorer by pressing Win + E on your keyboard, and then click on the OneDrive icon. You should drag and drop folders you want to backup (or you can use Copy/Paste as well).
Using Google Drive
Google Drive is another great solution for free backups. The good news is that you get as much as 15GB for free by choosing this storage. There are also paid versions available, with significantly more storage to choose from.
You can access Google Drive via the web browser or use a desktop app you can download on the official website. If you want your files to be synced automatically, you will have to download the app, however.
- Download the Google Drive app installer and click on it.

- Wait a few seconds for it to be installed.

- Now click the arrow within your system tray – you should see Google Drive icon there, click it once.

- Click Get Started.

- Enter all the required information – your email/phone, and password.

- Now pick what you want to sync and backup. You can click on Choose Folder to add additional folders to the list.
- Once done, pick Next.

- Now you can select to sync items to be visible on your computer.
- Finally, press Start and wait till the sync is complete. Your files are now being backed up.
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What is a DDoS attack?. Cloudflare. The Web Performance & Security Company.
- ^ Command and Control [C&C] Server. Trend Micro. Security blog.
- ^ Keystroke logging. Wikipedia. The free encyclopedia.





























