Chromnius.com browser hijacker (Free Guide)
Chromnius.com browser hijacker Removal Guide
What is Chromnius.com browser hijacker?
Chromnius is a potentially unwanted application that sets itself as the default browser to promote sponsored content and show ads

If you have spotted that any links you click are opened on a different browser than you're used to, and the homepage is set to the Chromnius.com URL, you have a potentially unwanted application installed on your system. Namely, a browser that is presented as an alternative to Google Chrome, Mozilla Firefox, MS Edge, or another used one at the time.
The application operates like any other browser hijacker, except it's using its own browser to do the job. You could have downloaded it via its official website or completely by accident whenever you installed freeware or shareware from third-party sources (software bundling). Likewise, you may have come across ads online that could have convinced you.
Once on the system, the hijacker would search the homepage and new tab to Chromnius New Tab, which would also alter the search engine and its results. You are then would be forced to search via the hijacker's search engine, which would use search.yahoo.com as a provider. These results would not be accurate and would be filled with sponsored links at the top. Likewise, ads are more likely to encounter while using this browser.
| Name | Chromnius.com |
| Type | Browser hijacker, potentially unwanted program |
| Distribution | Bundled software, third-party websites, official app site |
| Symptoms | An alternative browser Chromnius is set to be default whenever using the internet; the homepage and the new tab are set to be of the app; an altered homepage and search box produce ad-filled results |
| Risks | Data tracking from various third parties, exposure to malicious ads, redirects to phishing sites |
| Removal | You can remove the unwanted program manually, but you should scan your system with security software to ensure it isn't infested with additional viruses |
| Other tips | After removing all potentially unwanted applications, we recommend you employ the FortectIntego utility to clean your web browsers and repair any damaged system files |
How Chromnius spreads and how to avoid it
As mentioned, there are three ways one could download and install this potentially unwanted application:
- Software bundling[1]
- Official website
- Advertisements
If you have intentionally installed the app as an alternative to Chrome or another browser, you should consider going back to your original one. With so many choices available, it is not surprising that some of the apps may turn out to be potentially unwanted applications, and users may install them without realizing this fact.
The most likely cause of having Chromnius.com installed is due to software bundling – the technique is extremely common when it comes to potentially unwanted application distribution. Typically, third-party websites that distribute freeware are known for this, so if you frequent sites like that, you should be much more careful when dealing with them.
One of the main points to pay attention to when dealing with bundles is the tricks used there. Most commonly, users are tricked by pre-ticked checkboxes, fine print text, misplaced buttons, and similar. Therefore, you should never rush the installation process of new programs from these sites and use Advanced/Custom mode instead of Recommended/Quick whenever it's possible.
It is worth noting that you should stay away from websites that distribute pirated software, cracks, and similar. These websites can be operated by cybercriminals to spread malware to as many users as possible. For example, you may get infected with Aamv ransomware[2] if you execute files downloaded from torrent sites.
How to effectively remove the potentially unwanted app
If you have Chromnius installed on your device and you are not happy with the changes it made due to ads and other issues, we recommend you remove it from your system. Since it's a browser, it had to be installed on the system level, so you can remove it by checking the installed program section on Windows or Mac systems.
Before you proceed with these instructions, we recommend you make a thorough check with SpyHunter 5Combo Cleaner or Malwarebytes security software to ensure that there are no other potentially unwanted applications or malware running in the background without your knowledge. Having a reputable security app on your device would also prevent future malware attacks.
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Mac
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.

Once you have finished Chromnius.com removal, we would also recommend cleaning browser caches to ensure no data tracking taking place. Third-party programs often put cookies[3] and similar tiny items within your browser caches, which ensures the collection of various data, such as search queries, links clicked, websites visited, interactions with ads, and similar. You can stop this by removing browser caches – you can either do it automatically with FortectIntego or by following the instructions below:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Internet Explorer
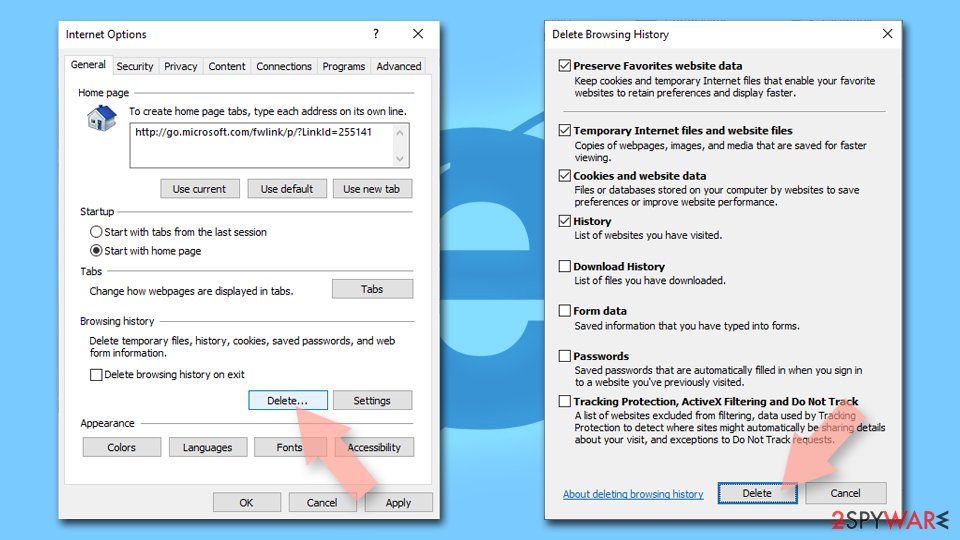
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
R
How to prevent from getting browser hijacker
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Bundled software. Computer Hope. Free computer help.
- ^ Ransomware. Imperva. Application and data protection.
- ^ HTTP cookie. Wikipedia. The free encyclopedia.
