Yourdatasecurityservice.com ads (virus) - Free Guide
Yourdatasecurityservice.com ads Removal Guide
What is Yourdatasecurityservice.com ads?
Yourdatasecurityservice.com is a scam website that shows misleading messages about virus infections
Yourdatasecurityservice.com may be encountered when visiting websites of dubious content, including torrents or illegal video streaming ones. In rarer cases, users are also likely to encounter phishing[1] websites due to adware installed on their systems, which they are usually not aware of.
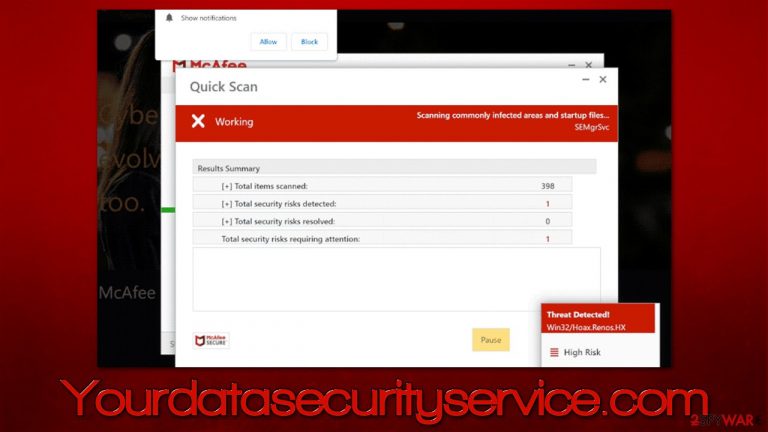
Upon website entry, people are shown what seems like a virus scan by a popular security vendor McAfee. Even though this process is performed on the web page, some people might confuse it with a real scan from anti-malware software, as imitation is rather believable.
After the fake scan is complete, Yourdatasecurityservice.com shows the misleading results of computer infection and claims that security software has expired. This way, visitors are inclined to proceed – they might download and install the suggested security software that allegedly could get rid of all the found threats.
In reality, this is all a scam and the main goal of crooks behind it is to make people download software that they get a commission for. There is no guarantee that the advertised security application is safe, as it could be a fake version or a completely unrelated, potentially unwanted or malicious program.
| Name | Yourdatasecurityservice.com |
|---|---|
| Type | Scam, phishing, adware, redirect virus |
| Goal | Make people provide personal information, subscribe to useless services, download malicious software or subscribe to push notifications |
| Distribution | Redirects from other malicious websites, adware |
| Dangers | Those who have malicious software installed on their systems are more likely to encounter dangerous websites, resulting in financial losses, malware infections |
| Removal | You should not interact with the contents shown by a scam website and instead, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Other steps | After eliminating all PUPs from your system, clean your web browsers and repair system files. You can do that automatically with FortectIntego or refer to our manual guide |
Scam techniques
Online scams are extremely common, although certain circumstances make users be more susceptible to them. For example, those who visit potentially dangerous websites are more likely to click on a fake link and be redirected to Yourdatasecurityservice.com or a similar fake site. What is clear is that nobody enters the website intentionally – they are redirected to it.
The scammers count on users' lack of understanding of malware and the IT field, and they try to imitate what otherwise would look like a scan from a legitimate antivirus provider. Using well-known elements from around the internet and well-known retailers can often provide a false sense of legitimacy, making users believe that what they see is legitimate.
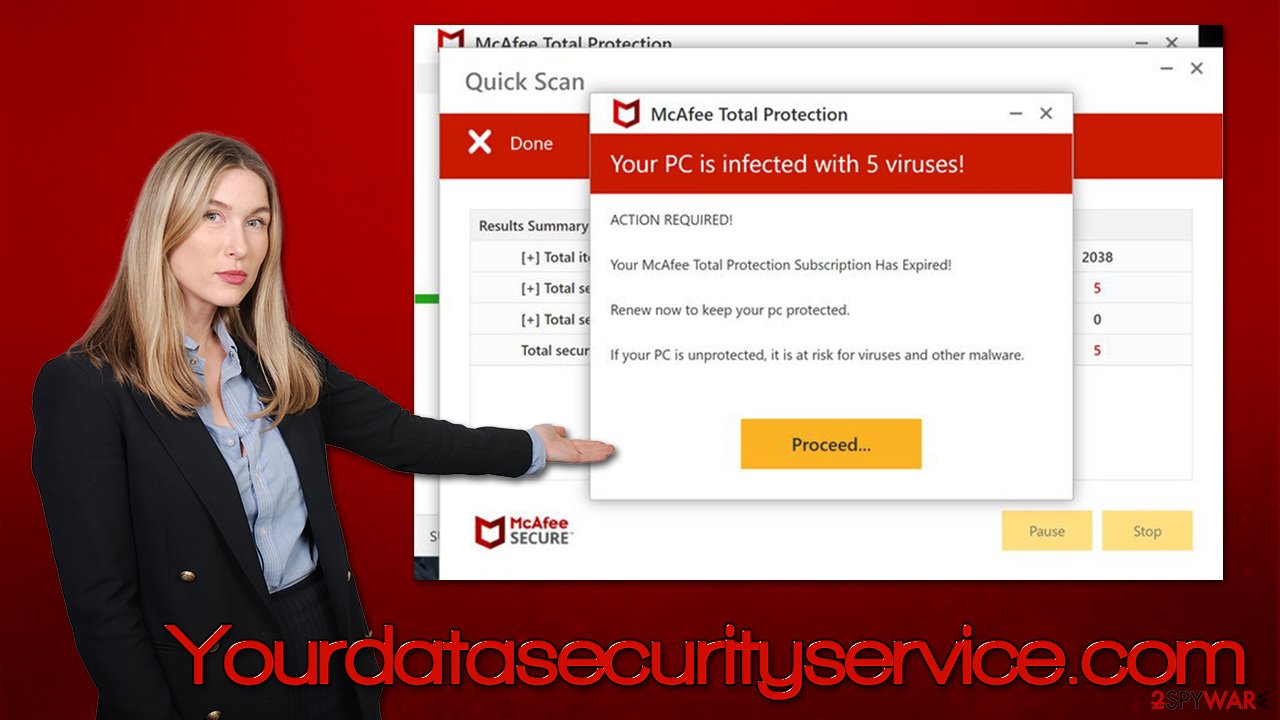
Once the fake scan is finished, they are presented with the following message:
Your PC is infected with 5 viruses!
ACTION REQUIRED
Your McAfee Subscription Has Expired!
Renew now to keep your PC protected.
If your PC is unprotected, it is at risk for viruses and other malware.
However, this is all fake, and you should never download anything that's suggested on such websites, as you could purchase a fake version of the antivirus program, which would end up being malicious, and you would also support cybercriminals who employ such fake schemes.
Always remember that only anti-malware software installed on your system can tell whether or not your system is infected. Also, you should check the URL of the website which shows you the message, as it usually has nothing to do with the brand name of the real company, e.g., Allowpcprotect.com or Playsuperrecentthefile.vip is barely web addresses a reputable anti-malware company would use.
Step 1. Check your system for adware
First of all, the results of the alleged virus scan are always fake – the presented infection names aren't even real. That being said, it would not hurt to check your system thoroughly to ensure that there's no adware or malware involved. If you wonder whether your system got infected or your security got compromised in some other way just by accessing the Yourdatasecurityservice.com site – you should be safe as long as you don't click anything and don't install any programs.
While you can check your system manually, as we explain below, we strongly recommend using SpyHunter 5Combo Cleaner or Malwarebytes anti-malware software first and checking the system for the invisible infections that are difficult to find without adequate computer knowledge.
To remove potentially unwanted extensions, you should click the “Extensions” button which is present next to your profile picture/settings menu, and then uninstall everything you don't recognize. If you are not sure which app is causing problems, you should uninstall them all and then reinstate them one by one.
To check the programs installed on the system level, you should access the list of the installed applications as follows:
Windows
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Mac
While moving apps into Trash is how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
Step 2. Clean your browsers
You should clean your browsers accordingly after you are exposed to an online scam or after unwanted software removal. When you visit websites and enter your passwords or other login details, these preferences are saved in the form of cookies and other elements.
While a lot of this data is encrypted[2] and invisible, cookie hijacking[3] is still possible in some cases. Additionally, third parties use them to track various user data, so removing them from time to time is recommended. We recommend employing FortectIntego repair and maintenance utility instead if you would rather avoid doing so manually.
Google Chrome
- Click the Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

How to prevent from getting adware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Phishing. Wikipedia. The free encyclopedia.
- ^ What is encryption? Data encryption defined. IBM. Security blog.
- ^ Lindsay Pietroluongo. What is Cookie Hijacking? (And How to Prevent It). Elegant Themes. WP Theme and Plugins.
