COVID-19 Pandemic email virus (Virus Removal Guide) - updated Aug 2020
COVID-19 Pandemic email virus Removal Guide
What is COVID-19 Pandemic email virus?
COVID-19 Pandemic email virus is a term used to describe malware and scams included in phishing emails related to coronavirus pandemic
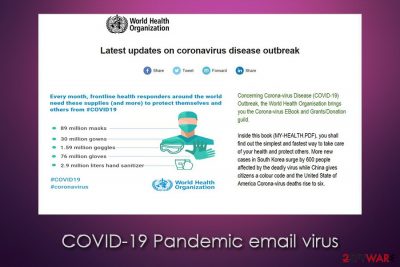
COVID-19 Pandemic email virus is a malicious program that users might install on their machines after being tricked by a phishing email. During the coronavirus outbreak, the number of phishing emails allegedly coming from such organizations like WHO (World Health Organization) or CDC (Centers for Disease Control and Prevention) grew rampant,[1] as multiple malicious actors are seeking to gain financial benefit. By boobytrapping malware inside, COVID-19 Pandemic email virus authors deliver such infections like FormBook Trojan – its main goal is to steal a variety of sensitive information on users' machines.
In this article, we will explain how to the Trojan can affect your computer system and your personal safety, and how to remove COVID-19 Pandemic email virus from your system for good. Additionally, you can also check on some tips on how to prevent being infected via coronavirus-themed scams.
| Name | COVID-19 Pandemic email virus |
| Type | Malware, phishing email |
| Associated malware | Once executed, the email attachment installs the data-stealing Trojan FormBook |
| Related | New Order.img, MY-HEALTH.PDF, MY-HEALTH.exe, Untitled attachment 00012.zip |
| Infiltration | Spam emails that come from alleged global health organizations or known companies |
| Symptoms | While Trojans are designed to remain unnoticed on the system, users might find some traces of the info-stealing malware, such as strange browser behavior (slowness, redirects, inability to access particular sites), software or system crashes, unknown processes running in the background, etc. |
| Risks | Significant monetary losses, identity theft, data compromise, other malware infection |
| Removal | In some cases, termination of malware might be tricky, as Trojans might use several security tool disruption techniques to remain unnoticed. Nonetheless, the most up-to-date anti-malware software should be able to find and eliminate all malicious files placed by the virus – you can find more details in the bottom section of the article |
| System fix | Trojans can disrupt the normal operation of the Windows system, even after its termination. Thus, if you experience system crashes, lag, or other stability issues after you get rid of the virus, employ FortectIntego to repair it promptly |
Phishing campaigns have been prevalent since pandemic's begging, as the issue is extremely sensitive and, thanks to mass media, is extremely relevant. It is no surprise that threat actors are trying to abuse the worldwide trends and even a pandemic in order to infect people with malware, and the COVID-19 Pandemic email virus is one of them.
The phishing campaign of the COVID-19 Pandemic email virus was first spotted in early March 2020, and there are also a few different versions of it available. Despite that, all of the variants focus on a pandemic and carry the malicious payload within the attachment of the email.
Victims are presented with an email that overall looks legitimate, as it includes information about the COVID-19 pandemic. The sender, which seems to be the WHO from the first sight, sends the email with “high importance” and titled it as “Coronavirus Updates.” The message looks very professional, so it is not surprising that many users can get caught off guard and install the COVID-19 Pandemic email virus unintentionally.
The contents of the COVID-19 Pandemic email are as follows:
Latest updates on coronavirus disease outbreak
Concerning Corona-virus Disease (COVID-19) Outbreak, the World Health Organisation brings you the Corona-virus EBook and Grants/Donation guild.
Inside this book (MY-HEALTH.PDF), you shall find out the simplest and fastest way to take care of your health and protect others. More new cases in South Korea surge by 600 people affected by the deadly virus while China gives citizens a colour code and the United States of America Corona-virus deaths rise to six.
In reality, the so-called MY-HEALTH.PDF is not actually a PDF but an .EXE file, which, once clicked, will begin to infect the computer with malware. Note that there are also several spelling mistakes within the text – yet another reason to be suspicious.
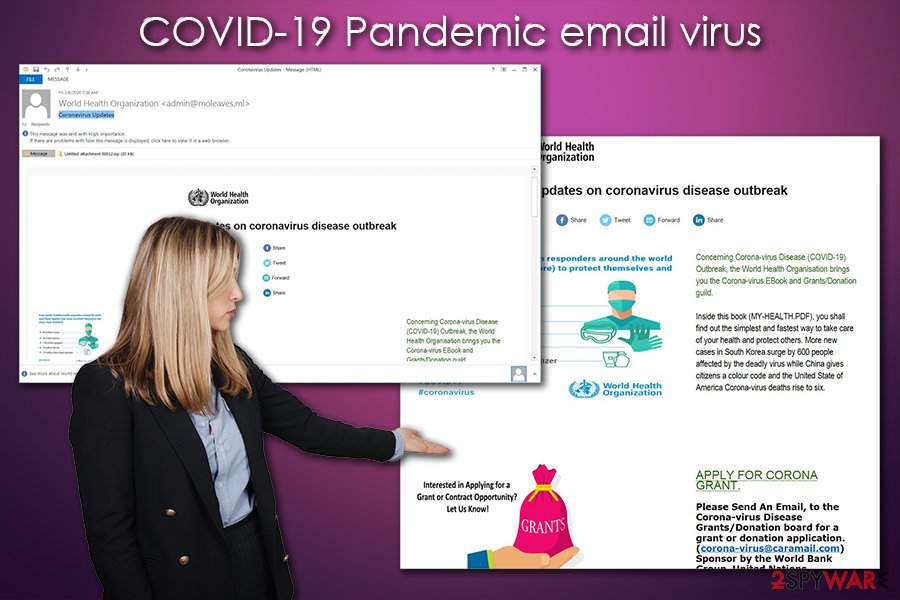
In other cases, users might also be presented as a purchase order that is coming from a well-known organization or another attachment. As research shows, other file types, such as .IMG, .PDF, .DOC, .XLS, .RAR, .ACE, and .ISO, was also used to initiate the infection process of the COVID-19 Pandemic email virus.
FormBook is not a new malware in the cybercriminal scene – it first emerged in early 2016 and since then has been highly advertised on the underground hacking forums. This technique allows all types of cybercriminal groups to rent access to the malicious code and retain all the profits from it.
COVID-19 Pandemic email virus possesses an array of various capabilities, including:
- Taking screenshots
- Keylogging
- Stealing passwords from emails and browsers
- Grabbing information from the clipboard
- Grabbing HTTP/HTTPS/SPDY/HTTP2 forms and network requests
- Updating itself
- Clearing browser cookies
- Removing itself from the infected system
- Downloading additional files, etc.
Security researchers from FireEye, who analyzed the malware in 2017, said the following:[2]
The malware injects itself into various processes and installs function hooks to log keystrokes, steal clipboard contents, and extract data from HTTP sessions. The malware can also execute commands from a command and control (C2) server. The commands include instructing the malware to download and execute files, start processes, shutdown and reboot the system, and steal cookies and local passwords.
Without a doubt, the infection can cause significant financial losses to any victim infected. Besides, disclosure of personal email, name, address, social security number, credit card information, and other data might also eventually lead to identity fraud or theft. In other words, COVID-19 Pandemic email virus removal is a mandatory procedure to prevent unfortunate consequences of a Trojan infection.
Note that, due to process injection, the COVID-19 Pandemic email virus might remain unnoticed for a very long time, performing malicious activities in the background. This is another reason to keep a comprehensive security solution installed on your system at all times. For virus damage fixing, we recommend using FortectIntego or similar repair software.
COVID-19 Pandemic email virus versions
The COVID-19 pandemic caused a surge of emails that promote the alleged compensations for people around the world. Nevertheless, mostly US citizens are targeted by these scams, and names of the well-known organizations, such as the United Nations, World Health Organization, and others, are commonly used to make the hoax more believable.
While there are several versions of the Covid-19 Pandemic email scams, most of them are identical on a fundamental basis: they claim that compensation or relief is due to the global crisis.
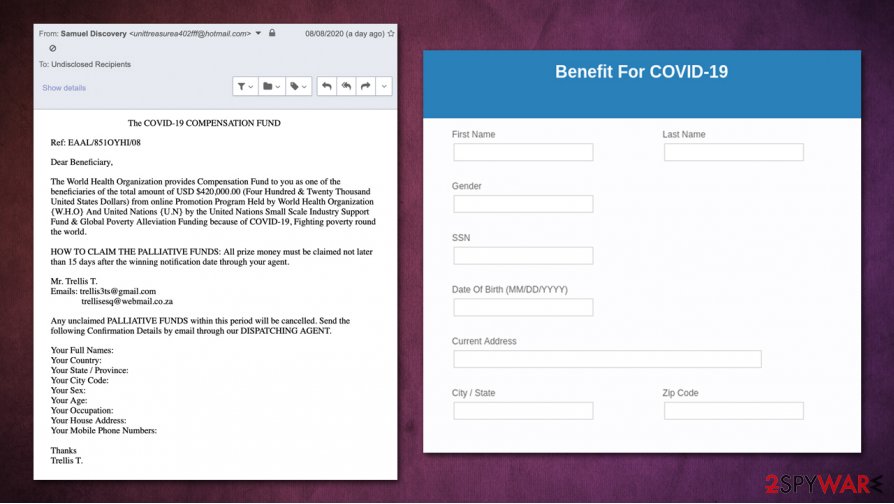
Covid-19 Compensation Fund scam
Covid-19 Compensation Fund scam is an email attempting to exploit the global pandemic to trick users into providing personal data. The message authors claim that users are eligible for a compensation of $420,000, which is provided by the World Health Organization (WHO) and the United Nations (UN). Allegedly, the payout is due to reduce global poverty due to the health crisis worldwide. However, the Covid-19 Compensation Fund email is just a scam and should never be trusted.
Threat actors are seeking to steal personal information of users for personal gain. In the case of Covid-19 Compensation Fund email scam, they are asked to provide the following data via the emails trellis3ts@gmail.com or trellisesq@webmail.co.za to reclaim the compensation:
- Full name
- Country
- State/Province
- City
- Sex and age
- Occupation
- House address
- Mobile number
If you received such an email, keep in mind that it is a scam, and your personal information will be sold on the dark web, or you can become a target of other scams in the future. It is not uncommon for malicious actors behind Covid-19 Compensation Fund scam to send follow-up emails in order to make users download malware or provide more sensitive information, such as Social Security Number (SSN) or credit card data.
Learn to recognize malicious spam emails
First of all, you should keep in mind that all “big things” that are happening in the world will always attract cybercriminals, and they will keep abusing the popularity of a topic, an application, a company, or the latest video game which spiked in popularity.[3] Therefore, whenever you are dealing with online content, such as various websites and emails, you should keep that point in mind. There are several preventive measures that can be practiced to avoid malware online. Despite that, the most relevant is familiarization with the latest security threats, and attentiveness while browsing the internet.
Phishing emails are particularly dangerous and prevalent attack vectors for malware distribution, mainly because they are easy to use, and are still very effective. Besides, the process can be simplified with the help of botnets that can send thousands of emails automatically on a daily basis. As a result, even if not all malicious emails result in the infections, the small percentage of people that do open the attachment, is still significant enough for threat actors to gain the maximum amount of profits. Luckily, many email providers employ built-in malware scanners, which would immediately send most of the malicious emails to a Spam folder and mark them as potentially dangerous.
In most cases, phishing emails contain a familiar sender name – such as the World Health Organization. However, it is important to now that anybody can use the name of whatever they want. In other words, look at the precise email address instead of the name of the sender. Note that the attackers often use similar email addresses that might look legitimate, but usually have duplicated letters or similar inconsistencies.
Most of the malware payloads are delivered through the attachments, so they are a vital part of the infection chain. These attachments can come in different formats, and function differently. For example, macro-infused .doc and .xls files might ask to “Allow content” to proceed, while other documents may include links to malicious domains. All in all, you should never trust email attachments, even if they come from seemingly secure sources. Thus, simply scan it with anti-malware software or upload it to Virus Total before opening. Finally, equip your computer with anti-malware to protect it from unsolicited intrusions via phishing emails.
Terminate COVID-19 Pandemic email virus and remediate your computer
If COVID-19 Pandemic email virus removal is not performed as soon as possible, it can steal a variety of information from your system. Unfortunately, you might not even notice that the malicious program is running in the background in the first place, as Trojans are designed to be stealthy. However, COVID-19 Pandemic email virus, once inside the system, might show the following symptoms:
- slow operation of the browser
- difficulty to access some websites
- software or/and system crashes
- system lag, errors, bugs, etc.
Regardless if you experience these symptoms or not, you should remove COVID-19 Pandemic email virus with the help of security software only – we recommend using SpyHunter 5Combo Cleaner or Malwarebytes, although there are plenty of other effective tools as well. Nevertheless, since FormBook is a multi-functional Trojan with plenty of evasion capabilities, it is recommended to access Safe Mode with Networking and initiating a full system scan with anti-malware.
Once you eliminate the COVID-19 Pandemic email virus, you should also take additional steps to secure all your accounts – change passwords and monitor your online banking transactions. In case you notice anything suspicious, contact your bank and explain the situation, the stall will be able to assist you with the situation further.
Getting rid of COVID-19 Pandemic email virus. Follow these steps
Manual removal using Safe Mode
In case you are having troubles with malware removal in normal mode, access Safe Mode with Networking as explained below:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from COVID-19 Pandemic email and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Lindsey O'Donnell. Coronavirus ‘Financial Relief’ Phishing Attacks Spike. Threat Post. The first stop for security news.
- ^ Nart Villeneuve, Randi Eitzman, Sandor Nemes, Tyler Dean. Significant FormBook Distribution Campaigns Impacting the U.S. and South Korea. FireEye. Security blog.
- ^ Gary Jones. Valorant Beta Key warning: Stick to Twitch Drops and avoid this scam. Express. British newspaper outlet.














