FormBook virus (Removal Instructions) - updated May 2020
FormBook virus Removal Guide
What is FormBook virus?
FormBook is a from grabbing software that can take screenshots, log keystrokes, and analyze auto-fill to steal user's credentials
FormBook is a data-stealing malware that belongs to the group of form grabbing trojans. Although its developer introduced it as a legitimate Internet monitoring application, it has been sold on hacking forums and distributed as an information-stealing trojan since 2016. Typically, is spreads via malicious spam emails. If a user is tricked into opening an obfuscated email attachment, the virus payload is dropped and executed on the system. The latest FormBook related malspam campaign has been revealed in Spring 2020 by Fortinet[1]. This time, crooks disguise under the World Health Organization (WHO) supposedly spreading information and recommendations related to the current Coronavirus (COVID-19) pandemic. During the lifetime, a malicious program caused most of the problems for users in the United States and South Korea.[2]
| Summary | |
|---|---|
| Name | FormBook |
| Type | Malware, keylogger, info-stealer |
| Release year | 2016 |
| Danger level | High. Makes system changes and steals sensitive data |
| Distribution method | Malicious spam emails attachments (PDF, XSL, DOC, ZIP, etc.) |
| Symptoms | Sluggish computer performance, sudden system shutdowns, delivery of errors |
| Most affected countries | The United States and South Korea |
| To uninstall FormBook, install SpyHunter 5Combo Cleaner and run a full system scan. Upon virus removal, run a scan with a powerful optimization utility to fix trojan damage. We recommend using FortectIntego. | |
FormBook malware mostly targets businesses and organizations in aerospace, defense contraction, and manufacturing sectors. Hence, home computer users are not the main targets of malware.
The FormBook virus is known at least since 2016. A few years ago, creators of malware started advertising it in the dark web and hacking forums. The program was advertised as:
<…> advance internet activity logging software
coded in low level language ASM/C which means it does not require any dependency to work perfectly on all version of windows.
FormBook is designed with aim to give you extensive and powerful internet monitoring experience
with its ultimate stability alongside flexibility that is above the edge of all existing monitoring/spy tools.
Therefore, FormBook operates not only as a data-stealing virus but malware-as-a-service too. The price for its license starts with $29 per month and ends with $299 for “Pro” version.[3] Though, any evil-minded programmer can obtain a program and try to cause problems for computer users. Meanwhile, developers of original malware generate passive income.
As we have already mentioned, the virus spreads via malicious spam emails and enters the system when a user opens an infected file. Once inside, malware connects to Command and Control (C&C) and starts its malicious tasks.
First of all, it makes system changes and downloads all malicious components in order to perform the following operations:
- keylogging;
- taking screenshots,
- stealing passwords saved in a web browser and email clients;
- clipboard monitoring;
- stealing forms information;
- grabbing network requests.
The loss of sensitive information definitely has a negative impact on the company’s and people’s privacy and security. It’s unknown how and when aggregated might be used. However, it’s important to take security measures as soon as you learn about the cyber attack. It goes without saying that FormBook removal has to be your priority.
The complexity of the virus requires using reputable malware removal software to clean the device and fix its damage. We suggest victims remove FormBook with SpyHunter 5Combo Cleaner or Malwarebytes. Additionally, after virus elimination, people must change their passwords and monitor possible suspicious activities on their accounts.
Malicious email attachments spread data-stealing malware
Just like many similar malicious programs, FormBook spreads via malicious emails and gets into the system when a user opens an obfuscated file. This cyber threat was noticed spreading via archives that included a deadly exe file, such as:
- ZIP;
- RAR;
- ACE;
- ISOs.
However, malware payload was also noticed spreading via PDF with download links, and DOC and XLS files that contain malicious macro commands. The latter campaign was very active in 2017 and targeted computers in the U.S and South Korea.
The latest attack has been revealed in spring 2020. This time, attackers take advantage of the most escalated topic worldwide, which is a Coronavirus (COVID-19) pandemic. The email pretends to be from the well-known World Health Organization (WHO). It contains a malicious Coronavirus Updates.zip or MY-HEALTH.PDF file, which is highly obfuscated with FormBoom info-stealer trojan dropper and malicious entries.
Once the attachment is opened, it drops a GuLoader malware downloader, which injects its payload into the legitimate Windows wininit.exe process and then unravels the second payload, which is the FormBook trojan.
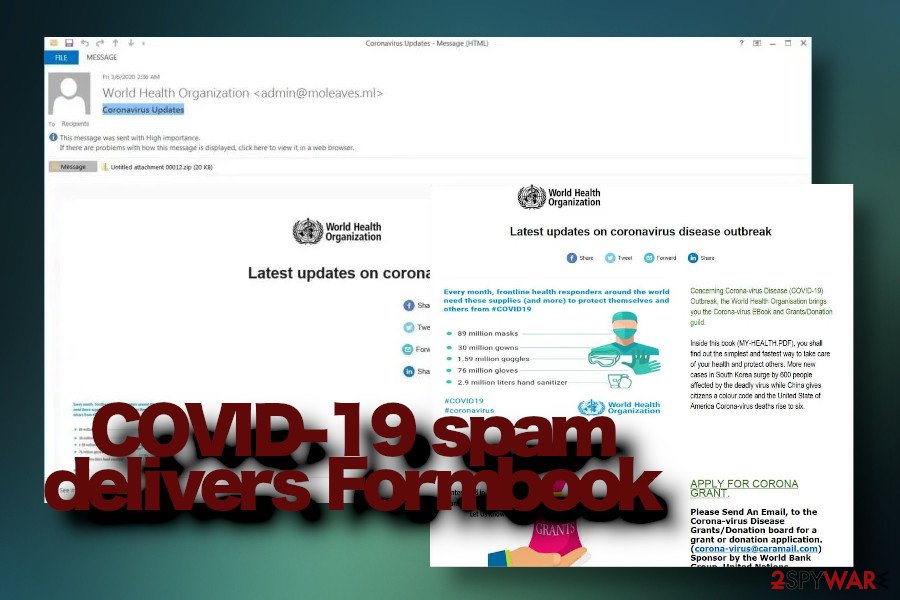
The main tip to avoid the infiltration of data-stealing malware is not to rush opening unknown email attachments. Indeed, phishing emails might be hard to identify, but you should look up for grammar mistakes, missing credentials, or suspicious email addresses.
The golden rule is – if you did not expect to receive such an email, it was not sent to you, and there’s no need to check what is hidden in the attachments. Cybersecurity specialists from Usunwirusa.pl[4] also suggest double-checking the information about the sender, company, or provided issue online before opening the attached files.
The correct way to eliminate FormBook malware
FormBook removal requires using professional and powerful security software. The malware downloads numerous malicious files and can affect the legit system process. Therefore, there’s no way to locate and delete these entries safely.
Tools like Malwarebytes or SpyHunter 5Combo Cleaner can remove FormBook from the affected computer. However, if you have some difficulties, please follow the instructions below. They will explain how to disable the virus and run security software.
We want to remind that you should not forget to change your email, social network, online banking, and other account passwords.
Getting rid of FormBook virus. Follow these steps
Manual removal using Safe Mode
If you cannot run security software to eliminate FormBook, follow these steps to disable it and run security software:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove FormBook using System Restore
This method might also help to activate security software which is needed for malware removal:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of FormBook. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from FormBook and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Fred Gutierrez and Val Saengphaibul. Deconstructing an Evasive Formbook Campaign Leveraging COVID-19 Themes. Fortinet. Network security solutions.
- ^ Tom Spring. FormBook Malware Targets US Defense Contractors, Aerospace and Manufacturing Sectors. Threatpost. Security news.
- ^ Bryan Vale. FormBook Is the Latest Example of Malware-as-a-Service. Opswat. Cyber security and malware protection blog.
- ^ Usunwirusa. Usunwirusa. Polish cyber security news.







