Cusj.xyz ads (scam) - Free Instructions
Cusj.xyz ads Removal Guide
What is Cusj.xyz ads?
Cusj.xyz shows misleading information in order to make users download extensions for Chrome
Entering and URL into the Omnibox on the browser would direct you to the destination you have expected. However, when it comes to links encountered on various websites, the result can be quite a bit different – and that's precisely how most people end up entering Cusj.xyz. Usually, unexpected redirects to phishing[1] and similar malicious websites can be encountered in high-risk places, where booby-trapped links or invisible scripts are present.
As soon as users access the site, they are shown a misleading message that allegedly, an extension called Search Verified installed on the browser is out of date. This notification shows up regardless of whether or not the app is actually installed, which might confuse some users and proceed with the instructions provided. Fake statements like that are misleading at best and malicious at worst, so we strongly discourage you from proceeding with the installation.
After Cusj.xyz-promoted browser extension is installed, users would soon notice that their browsers have significantly changed, although modifications are not only visual. In reality, the extension would hijack the web browser (primarily Google Chrome, although this can happen on all compatible browsers such as MS Edge). Note that the name of the extension does not necessarily match, and you might be prompted to download various unknown apps.
Thus, if you have encountered this scam, we recommend you not interact with it, as you might end up infecting your system. If you have already installed something, we provide detailed instructions on how to get rid of it below. Even if you did not interact with the scam, you should still check your device for adware and other possible infections just to be safe.
| Name | Cusj.xyz |
|---|---|
| Type | Redirect, scam, phishing, adware |
| Distribution | Software bundles, third-party websites, redirects |
| Symptoms | Redirects to suspicious websites that hold plenty of commercial or scam content; fake messages offer to download malicious software; ads plague every visited website; unknown extension or program installed on the system |
| risks | Installation of other potentially unwanted software or malware, personal information disclosure to cybercriminals, financial losses due to scams, etc. |
| removal | You should not interact with the contents shown by a scam website and instead, check your system for adware or malware infections with SpyHunter 5Combo Cleaner security software |
| Other tips | Cleaning web browsers is one of the secondary things you should do after PUP/malware removal to secure your privacy. You can use FortectIntego to do it quicker and more effectively |
How scammers trick users into downloading software
The element of surprise is very powerful in all life situations, and scammers are well aware of that. For example, messages that claim that a deadly virus has been detected on the computer and that personal information has been stolen would frighten some people to take action immediately and follow the instructions provided on the said message. This would later result in them spending money on fake security software paying for fake tech support services to scammers (millions of users are scammed every year this way).
Other types of scams, such as Cusj.xyz is promoting, are relatively less aggressive or damaging in the grand scheme of things. However, it is important to note that software promoted in deceptive ways should never be trusted, as anything could be hiding behind a seemingly useful request to install a new app or extension.
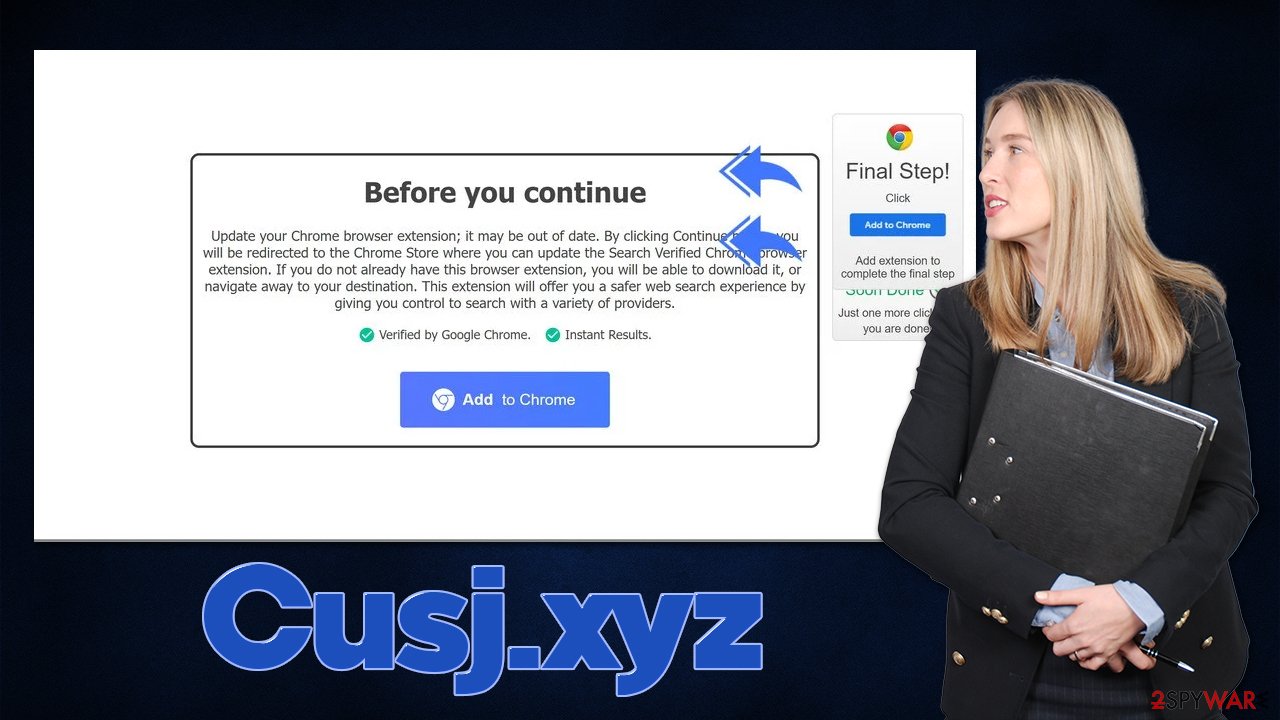
Here's the whole message that people are shown as soon as they are redirected to the site:
Before you continue
Update your Chrome browser extension; it may be out of date. By clicking Continue below, you will be redirected to the Chrome Store where you can update the Search Verified Chrome browser extension. If you do not already have this browser extension, you will be able to download it, or navigate away to your destination. This extension will offer you a safer web search experience by giving you control to search with a variety of providers.Verified by Google Chrome.
Instant Results.
As mentioned before, the offering to install an extension is not the problem; the issue is when deliberate statements are made in order to mislead users and make them confused. This way, more people would install the promoted extension, which would result in larger payouts thanks to schemes such as pay-per-install.[2]
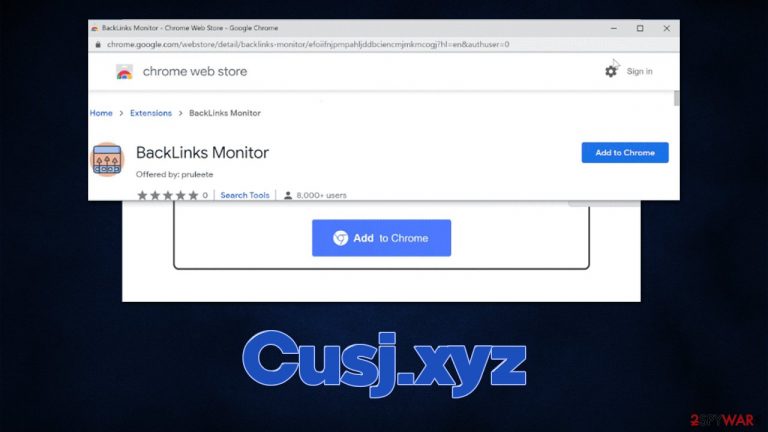
Note that the promoted extension might vary. For example, you might be asked to install BackLinks Monitor, which is considered to be a browser hijacker. It would change your browser settings, including a new tab and homepage address, swap to an alternative provider, and insert ads into search results. PUPs are also known for their data tracking capabilities.
What to do after encountering Cusj.xyz or a similar site?
Simply because you have encountered a scam website such as Cusj.xyz, it doesn't mean that your system is automatically infected. If you don't click anything and don't install anything, you should be safe. Nonetheless, redirects to suspicious websites might be caused by adware that is already running in the background, so regardless if you have been tricked by the fake message or not, you should check your system as explained below.
1. Uninstall unwanted apps
Since Cusj.xyz usually promotes browser extensions, we recommend starting from there. Usually, you can remove add-ons easily by clicking the “Extensions” button available on almost any other browser, this might not always be possible. In that case, you should check the installed application list within browser settings. Keep in mind that there could also be additional apps that could cause your browser to display ads and direct you to scam sites, so make sure you check this section carefully.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.

Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.

MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.

Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.

If you have not found anything suspicious in the extensions department, you might want to check applications installed on the system level. On Windows, you should access the Control Panel and then reach Programs & Features section, and then remove everything suspicious:
Note: skip this step if you aren't sure
- Enter Control Panel into Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.

If you are using a Mac, removal of applications might seem very easy, as most of them can be uninstalled by moving them to Trash. However, when it comes to adware,[3] it might insert additional items, files, settings, and other components in order to increase persistence. Therefore, we recommend performing additional steps on a Mac:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)

To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
2. Perform other checks
After you find unwanted programs installed on your browser or system and remove them, you should also ensure that more stealthy malware is also removed. Cybercriminals use all sorts of obfuscation techniques in order to increase the persistence of malicious programs. If not eliminated in time, other malware could be downloaded and installed on the system without you noticing or your personal data stolen.
Therefore, we strongly advise you to perform a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful security software. Anti-malware tools can also be a great help when facing malicious content online, as they would warn users about imminent danger. What is crucial is that the warnings should never be ignored, especially if they show up when trying to download repacked or cracked software.
Finally, you should clean your browsers from cookies and other web data to ensure no data tracking by third parties is performed. To make this step quicker, we recommend employing the FortectIntego tool (which can also fix various system damage due to infections), although you can also follow the manual steps below:
Google Chrome
- Click the Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ What is Pay-Per-Install?. Codefuel. Monetization solutions for websites, apps, extensions and search engines.
- ^ Adware. Wikipedia. The free encyclopedia.
