Cyberone ransomware (Quick Decryption Solution) - Free Guide
Cyberone virus Removal Guide
What is Cyberone ransomware?
Cyberone ransomware is a malicious program made for data encryption
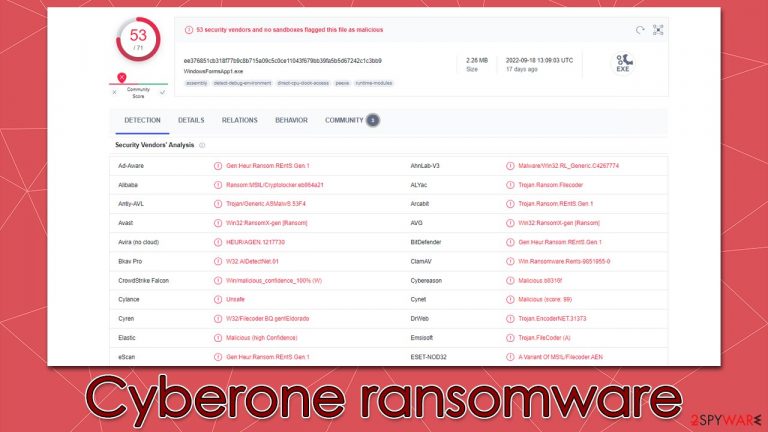
Cyberone is a ransomware-type malware that attacks victims unexpectedly and starts demanding money from them. The moment it gets inside, it infects the system and starts getting ready to lock data using complex encryption[1] algorithm. Soon after infiltration, the extension .cyberone is added to all photos, documents, databases, videos, and other types of files in this manner once they have been encoded.
As a result, users can no longer modify or even open their files, rendering them useless. It is important o note that the data has not been corrupted but simply locked using a unique key consisting of a long string of alphanumeric characters, which is precisely what's needed to recover encrypted files.
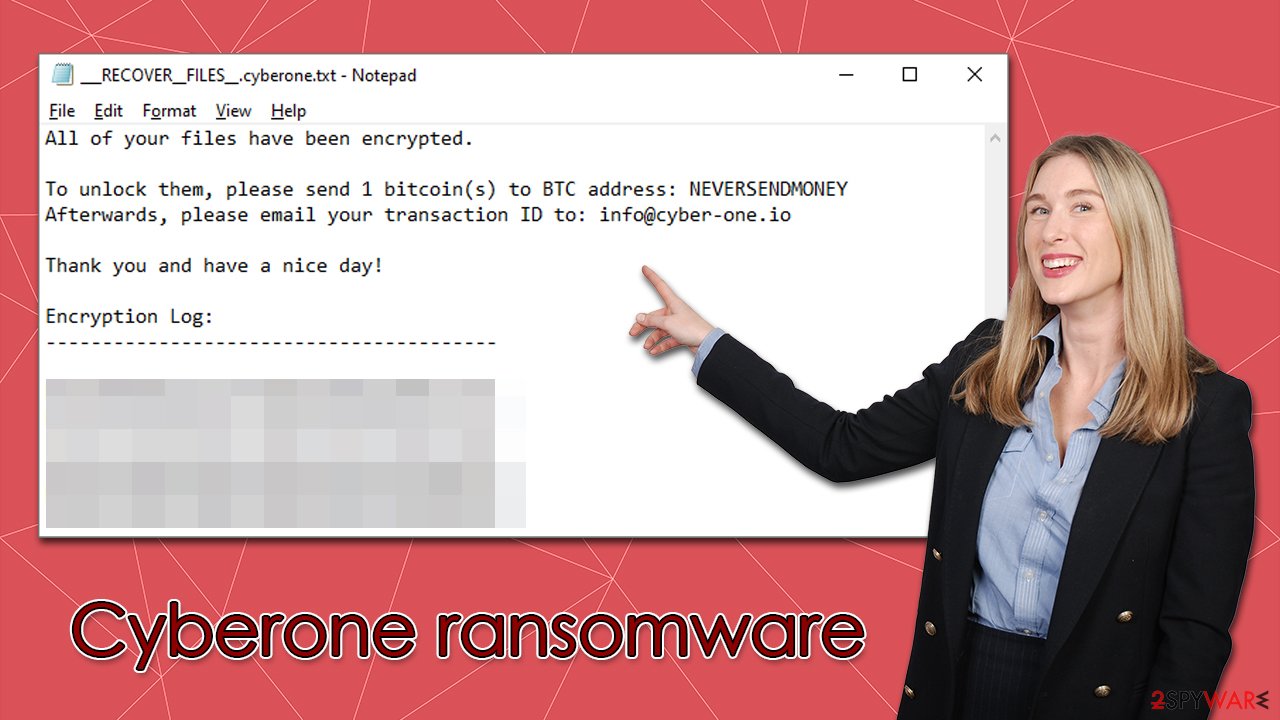
According to the Cyberone ransomware developers, users have to pay a ransom in order to restore their files. There's a pop-up window titled “Lol” and a note ___RECOVER__FILES__.cyberone.txt, which is meant to inform users about what happened o their files and how to restore them. Crooks also provide contact email info@cyber-one.io, which victims are supposed to use after transferring 1 bitcoin to the provided crypto-wallet.
| Name | Cyberone virus |
|---|---|
| Type | Ransomware, file-locking malware |
| File extension | .Cyberone appended to all personal files, rendering them useless |
| Ransom note | ___RECOVER__FILES__.cyberone.txt |
| Contact | info@cyber-one.io |
| Ransom size | 1 BTC |
| File Recovery | A free decryptor is available from Avast (info below) |
| Malware removal | After disconnecting the computer from the network and the internet, do a complete system scan using the SpyHunter 5Combo Cleaner security program. |
| System fix | As soon as it is installed, malware has the potential to severely harm some system files, causing instability problems, including crashes and errors. Any such damage can be automatically repaired by using FortectIntego PC repair |
Ransom notes
As a rule, malware creators want users to find out about payment and contact information in order to receive their money. This is most likely why cybercriminals send out two ransom notes: a text file and a pop-up window, as is the case with the Cyberone virus. Most often, ransomware employs TXT files for ransom notes, however.
A note is delivered right after the data locking process is finished – it uses a text format and can be opened with Notepad. It reads the following:
Your files (count: ) have been encrypted!
In order to recover your data…Please send 1 Bitcoin(s) to the following BTC address:
NEVERSENDMONEY
Next, E-mail your transaction ID to the following
info@cyber-one.io
In addition, another ransom note is shown immediately after the infiltration, which makes it more likely for users to view it first, as it is shown in a pop-up window titled “Lol.” Essentially, it does not differ much from the text file, although it has a minor difference in tone:
All of your files have been encrypted.
To unlock them, please send 1 bitcoin(s) to BTC address: NEVERSENDMONEY
Afterwards, please email your transaction ID to: info@cyber-one.ioThank you and have a nice day!
Hackers have the nerve to wish victims a good day right after encrypting their files – almost like they are mocking them. Remember that these people are not your friends, and they can't be trusted. Even if you send one BTC to their wallets, there is no guarantee that they will reply or provide a working tool.
Instead, remove Cyberone ransomware from your system first, as we explain below, and then use decryption software to recover your files for free.
Malware removal
It's crucial to carry out appropriate measures in the right order to avoid permanently losing your data. As earlier mentioned, it is not a good idea to trust hackers because doing so sometimes results in more losses. As your first step in the remediation process, you should ensure that malware no longer has an active connection to the network or internet. Either remove the Ethernet cable from the PC, turn off your WiFi or carry out the following actions:
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet

- Click Network and Sharing Center

- On the left, pick Change adapter settings

- Right-click on your connection (for example, Ethernet), and select Disable

- Confirm with Yes.
We advise employing SpyHunter 5Combo Cleaner or Malwarebytes, two reliable antivirus apps, to remove Cyberone ransomware from your computer after it can no longer access the internet. You can be sure that your system is malware-free since antivirus software can find and remove all malicious files at once. After employing security software, you can feel secure because it would find and eliminate malware modules and additional payloads that could have been lingering on your system without your knowledge.
Data recovery
Since many users do not prepare adequate file backups, they usually suffer from severe consequences once infected with ransomware. Once in the system, the virus infects local files and only then performs the encryption process, which is independent. As soon as the system is altered, malware can perform its data-locking task without interruptions – the major difference here is that the virus can be removed while the file-locking process is not reversible.
Luckily, there are a few options that could work for you in this case, and we will tell you about them. However, before you proceed with data recovery, you need to make sure that you don't corrupt the encrypted files in the first place. For that, you should use an external storage device and copy encrypted files there. You could also use any cloud services and transfer the files into virtual storage. As long as you have them copied, you are good to go.
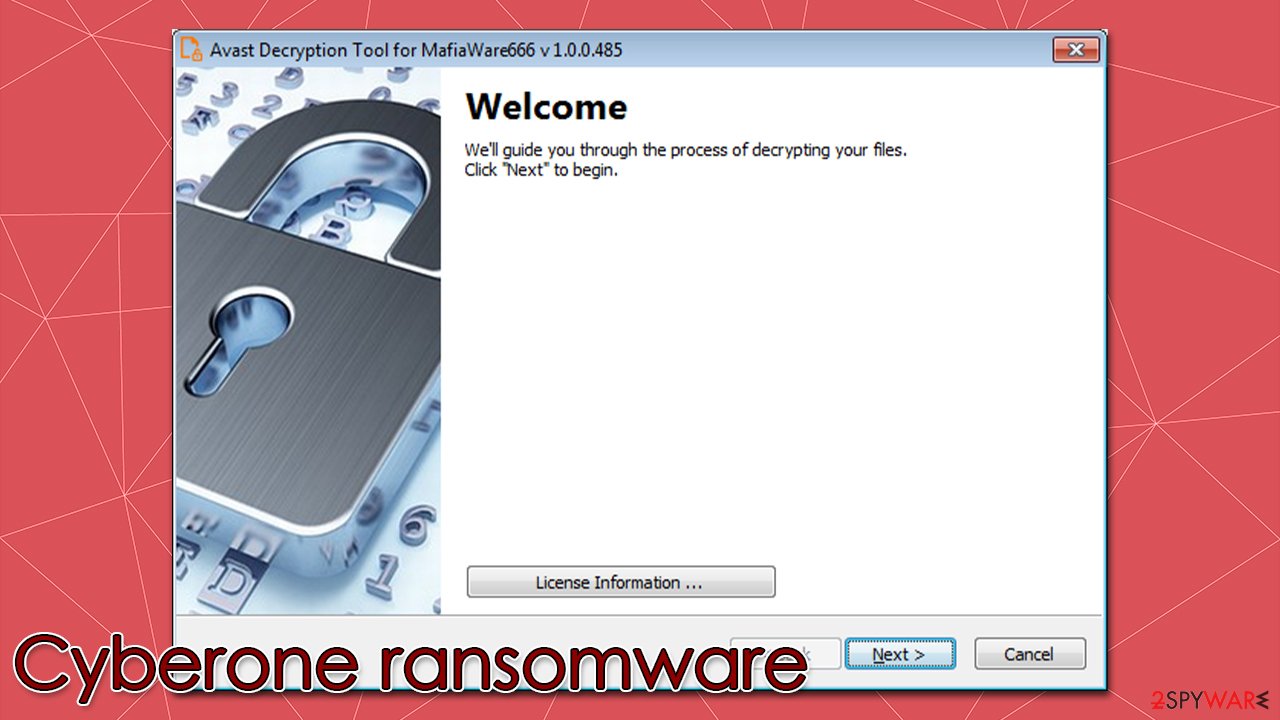
1. Restore files using a free decryptor from Avast
Ransomware is not always capable of encrypting files securely and may fail some of its tasks during the infection process. In other cases, flaws in the programming of malware can be found by security researchers, which results in them being able to create a decryptor, which they usually provide to users for free.
In this case, Avast has created a decryption tool designed for Cyberone and a few other ransomware strains from the same family. You can find all the details on how to use the software and where to download it on the official website.
2. Try data recovery software
In order for the decryptor to work, you would have to have a pair of encrypted and non-encrypted files at your disposal. If you don't, the decryptor may not be successful. If that's the case, you should try using specialized data recovery software, although keep in mind that there's no guarantee it will work for ransomware-locked data.
- Download Data Recovery Pro.
- Double-click the installer to launch it.

- Follow on-screen instructions to install the software.

- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.

- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.

- Press Scan and wait till it is complete.

- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
System fix
A computer's operating system will behave differently if it becomes infected with malware. A virus, for instance, has the ability to remove or corrupt DLL files, change the Windows registry[2] database, harm critical boot-up and other sections, etc.
Malware can damage vital system files, which antivirus software cannot fix. This can lead to performance issues, stability problems, and difficulty using the computer due to BSODs[3] or errors. To avoid this, we recommend using reputable repair software that can easily remediate these issues:
- Download FortectIntego
- Click on the ReimageRepair.exe

- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Encryption. Investopedia. Sharper insight, better investing.
- ^ Blue screen of death. Wikipedia. The free encyclopedia.
- ^ Registry. Computer Hope. Free security help.
