Defenceprogramm.com ads (scam)
Defenceprogramm.com ads Removal Guide
What is Defenceprogramm.com ads?
Defenceprogramm.com shows misleading ads to make people spend money on useless software
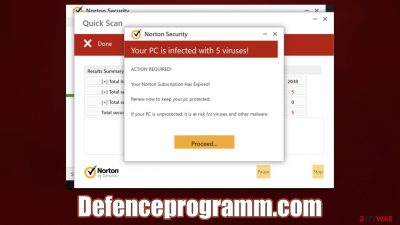
Defenceprogramm.com is a malicious website you might encounter whenever you browse high-risk websites and click on a misleading or malicious link. Alternatively, some users might be already infected with adware or other malware, which would cause unexpected browser redirects to malicious websites.
Soon after reaching the Defenceprogramm.com site, users would be shown a fake virus scan process, which would be branded by Norton. They would then be shown several pop-ups and what seems to be various file checkups. A brief few moments later, visitors would be shown an alarming warning, which states:
Norton Security
Your PC is infected with 5 viruses!
ACTION REQUIRED!
Your Norton Subscription Has Expired!
Renew now to keep your pc protected.
If your PC is unprotected, it is at risk for viruses and other malware.
Many users might fall victims to this scam due to various social engineering[1] techniques used. First of all, people might trust the message because it represents a well-known security vendor Norton. However, the scam page has nothing to do with it, and malicious actors are trying to earn affiliate money by using phishing messages.
| Name | Defenceprogramm.com |
| Type | Scam, phishing, redirect, adware |
| Operation | Claims that viruses have been found and that the anti-malware software license has expired. Asks to upgrade fake license |
| Distribution | Redirects from other malicious websites, adware |
| Risks | Installation of PUPs or malware, sensitive information disclosure, financial losses |
| Removal | Do not interact with links or other content of a scam site. Instead, check your system with SpyHunter 5Combo Cleaner security software |
| Other tips | Third parties can employ cookies to continue tracking your online activities, so we recommended clearing browser caches and other leftover PUP files with FortectIntego |
Scammers goals
Soon after users are presented with the fake message on Defenceprogramm.com, they would either believe it or not. Those who do might click the “Proceed” button which would redirect to the anti-malware software sale site via the affiliated link. This means that scammers would receive a commission each time a user purchases a license.
However, it is also important to note that these types of scams can never be trusted. They might lead to spoofing websites,[2] where they would provide their credit card information or other data, which would immediately be disclosed to cybercriminals.
They could then sell it on the underground forums or use it for other malicious means. Thus, if you have provided any personal information on any scam website, expect more phishing attempts coming your way – especially calls or emails (depending on what you have provided).
Alternatively, users could be prompted to download fake versions of security software, which would actually infect their machines. If you have downloaded and installed a program from a scam website, you should immediately uninstall it and check the system with security software.
Is my system now infected?
Since many users encounter scam messages absolutely unexpectedly, they are often caught off guard. Some people immediately believe the claim due to seeing a similar name in the security industry or due to other reasons. Nonetheless, most people aren't quite sure about these messages and often start seeking help on how to deal with the whole ordeal.
Upon encountering the Defenceprogramm.com scam, users often ask whether their systems are infected because they have entered the website in the first place. The truth is, it is extremely unlikely for you to get infected with some kind of malware just by entering a particular website without interacting with links or downloading/executing files.
The only way how this would be possible is if you would have a software vulnerability[3] present on your machine and the website would host an exploit that would correlate with it. To mitigate this type of attack, we always recommend users ensure that all their programs are regularly updated with the latest security patches.
How to check the device for infections
While the Defenceprogramm.com message is fully fabricated and bears no merit, you should not fully discard the probably of the computer infection. Users infected with adware, in particular, are known to encounter phishing material online more often, as well as suffer from numerous ads while browsing the web.
Even if you are not experiencing any infection symptoms, we strongly recommend you check your device regardless, as malware is extremely good at hiding its presence. The easiest way to do so is by performing a full system scan with SpyHunter 5Combo Cleaner, Malwarebytes, or another powerful anti-malware.
Alternatively, you could also check for adware and other potentially unwanted programs manually. You could start by removing suspicious applications installed on the system level:
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
While moving apps into Trash is usually how you delete most normal applications, adware tends to create additional files for persistence. Thus, you should look for .plist and other files that could be related to the virus. If you are not sure, skip this step entirely.
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
Next, you could check the browser for the installed extensions. Adware is commonly spread as browser extensions as it is easy to produce. You can quickly and easily get rid of the unwanted add-ons by clicking the “Extensions” button next to the menu of your browser. You can then clean your web browsers and repair damaged system files with FortectIntego.
Remove push notifications
A push notification prompt is always shown to users who visit the Defenceprogramm.com site. While most users are unlikely to accept this request, some people might simply click the “Allow” button by accident.
Those who agree to this request would permit the website to send information to users' screens without any restrictions. Push notifications would show all kinds of misleading ads and links to malicious websites. We recommend not interacting with these pop-ups and instead blocking the website via browser settings:
Google Chrome
- Open the Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate the Privacy and security section and pick Site Settings > Notifications.
- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.
![Stop notifications on Chrome PC 2 Stop notifications on Chrome PC 2]()
Mozilla Firefox
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.
- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.
![Stop notifications on Mozilla Firefox 2 Stop notifications on Mozilla Firefox 2]()
Safari
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.
![Stop notifications on Safari Stop notifications on Safari]()
MS Edge (Chromium)
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.
![Stop notifications on Edge Chromium Stop notifications on Edge Chromium]()
How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Social Engineering. Imperva. Application and data security.
- ^ Website spoofing. Wikipedia. The free encyclopedia.
- ^ What is a Software Vulnerability?. JFrog. Software Supply Chain.







