Defenderfordevice.com ads (Free Guide)
Defenderfordevice.com ads Removal Guide
What is Defenderfordevice.com ads?
Defenderfordevice.com promotes scam messages to profit from ad revenue
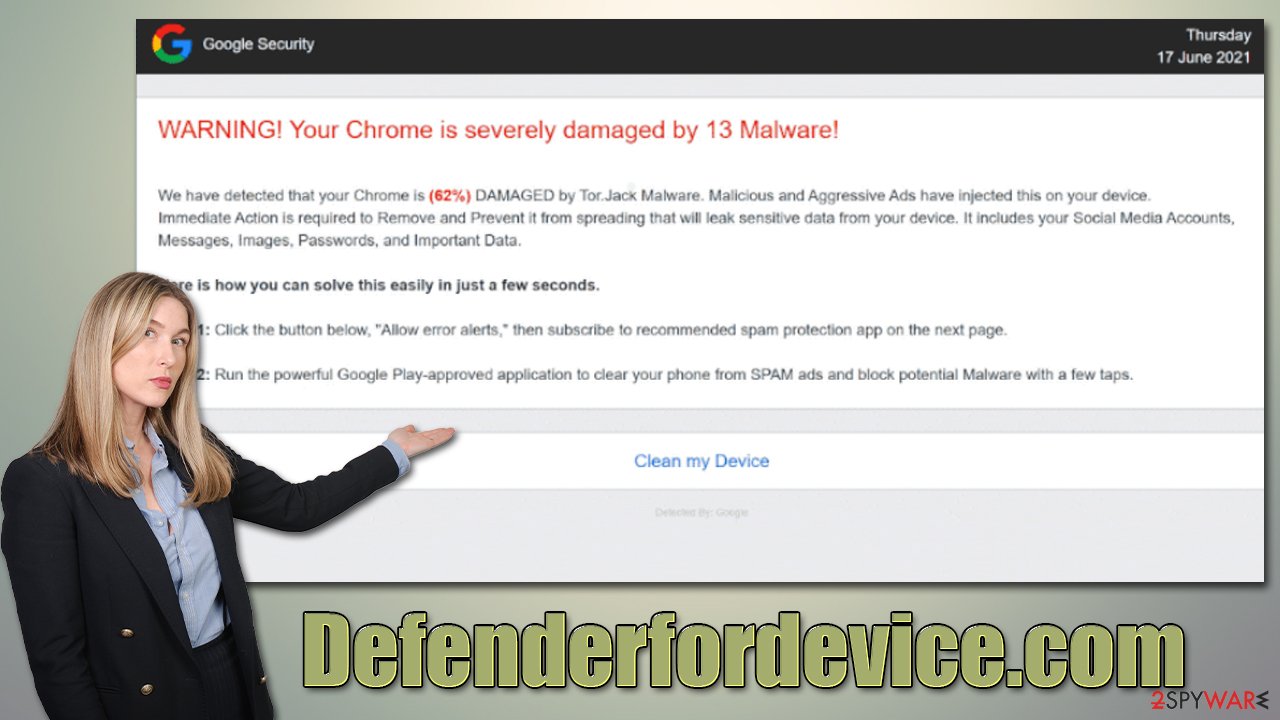
Defenderfordevice.com is a malicious website designed by crooks to fool users in various ways. It may promote various fake messages, but the most commonly-encountered one is the “Your Chrome is severely damaged by 13 malware” scam, which claims that the browser has been damaged by malware known as Tor.Jack. The name of the virus is fabricated, and it simply does not exist in real anti-virus databases.
The main goal of scammers is to use scare tactics and make people believe that their systems are infected, ultimately offering a “solution” for this fake problem, which is to download and install apps of unknown origins. Please stay away from such promotions, as scam websites may advertise nothing more than potentially unwanted programs or even malware.
It is also important to note that, despite the Defenderfordevice.com message being fake, you should not exclude the possibility of the adware[1] infection, which is one of the reasons why you may have ended up on a scam website in the first place. Below we explain how to tackle the scam and adware effectively.
| Name | Defenderfordevice.com |
| Type | Redirect, scam, phishing, adware |
| Distribution | Software bundling, redirects, misleading ads |
| Operation | Claims that Chrome browser has been damaged by malware. It then asks users to download a fake security tool to remove it. Also asks to enable push notifications |
| Risks | Fake messages usually aim for users to download potentially unwanted or malicious programs, steal their personal information or trick them into subscribing to useless services |
| Removal | Do not interact with scam content; if you did, uninstall the unwanted browser extension and check your system for other infections with SpyHunter 5Combo Cleaner anti-malware |
| Other steps | Remove caches and other web data to prevent data tracking – use the FortectIntego repair and maintenance tool. You can also repair damaged system components with it |
Criminals' goal is to make users frightened
When it comes to online fraud, malware infection notifications are nothing new. Due to their lack of IT expertise (which may induce anxiety after being told that there's a PC problem or malware infection), vulnerable groups are more readily tricked by these scams. For this reason, it's crucial to investigate before drawing any quick conclusions about a website or message displayed online.
Defenderfordevice.com is a hoax that tries to resemble Google, which is well-known to everyone who has ever used the internet. The website tries to hide its true origins by copying and portraying itself as a well-known brand. The message you can see when you enter is as follows:
WARNING! Your Chrome is severely damaged by 13 Malware!
We have detected that your Chrome is (62%) DAMAGED by Tor.Jack Malware. Malicious and Aggressive Ads have injected this on your device.
Immediate Action is required to Remove and Prevent it from spreading that will leak sensitive data from your device. It includes your Social Media Accounts, Messages, Images, Passwords, and Important Data.Here is how you can solve this easily in just a few seconds.
Step 1: Click the button below, “Allow error alerts,” then subscribe to recommended spam protection app on the next page.
Step 2: Run the powerful Google Play-approved application to clear your phone from SPAM ads and block potential Malware with a few taps.
This phishing[2] message was not actually created by Google. Additionally, no website can determine whether malware is already installed on your computer; only system-installed anti-malware software is able to accomplish that. When in doubt, always scan the system using a reliable security program rather than relying on messages from dubious websites.
How to deal with the Defenderfordevice.com scam
One of the most critical aspects of the scam scheme is the actions taken by the visitor. In essence, those who do not click any links, fill in personal information, or subscribe to useful services should be safe from malicious actors. If you have done at least one of these things, it is important you follow the steps below to remediate the situation.
Note that if you have provided your contact details, such as email or phone number, you may be a target of further scam campaigns. For example, you may receive a call where you would be addressed by your name since you've provided it. At this point, users are again intimidated, usually by fines or claims that they've done something wrong. Please ignore these calls and emails – always contact official numbers if you get anything like that.
Manual solution
You should start by checking the list of the installed programs on the system level. If you aren't sure about this step, you can instead rely on automatic removal which we discuss later.
Windows
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.
![Uninstall from Windows 1 Uninstall from Windows 1]()
- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till the uninstallation process is complete and click OK.
![Uninstall from Windows 2 Uninstall from Windows 2]()
Mac
Moving the unwanted application to Trash is not enough, as adware and malware commonly use persistence mechanics. Therefore, you might have to clean the leftover files as follows:
- From the menu bar, select Go > Applications.
- In the Applications folder, look for all related entries.
- Click on the app and drag it to Trash (or right-click and pick Move to Trash)
![Uninstall from Mac 1 Uninstall from Mac 1]()
To fully remove an unwanted app, you need to access Application Support, LaunchAgents, and LaunchDaemons folders and delete relevant files:
- Select Go > Go to Folder.
- Enter /Library/Application Support and click Go or press Enter.
- In the Application Support folder, look for any dubious entries and then delete them.
- Now enter /Library/LaunchAgents and /Library/LaunchDaemons folders the same way and terminate all the related .plist files.
Browser extensions could also be the cause of unwanted redirects and intrusive ads. In order to eliminate suspicious add-ons, simply click the “Extensions” button at the top-right corner of your browser and then select three dots > Uninstall or Remove.
Finally, you should stop the trackers, such as cookies,[3] that were likely placed on your system by adware or other unwanted software. You should do that by going to your browser's settings or using a strong PC maintenance program FortectIntego, which may also be used to repair virus damage if it has occurred.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
![Clear cookies and website data from Safari Clear cookies and website data from Safari]()
Quick automatic solution
You should run certain system checks whether or not you have engaged with the scam content. Adware is one of the biggest causes of excessive advertising and redirection to phishing websites. In this case, the best course of action is to scan the system with SpyHunter 5Combo Cleaner or Malwarebytes security software, which can detect and automatically delete all dangerous applications and files. Anti-malware is one of the best tools that can keep you from further malware infections, so make sure you have it running at all times and have it updated to the latest version whenever possible.
Remove push notifications from malicious websites
Users that visit the Defenderfordevice.com website are prompted to activate push notifications. Those who agree to them may subsequently see annoying pop-up ads that appear right on their desktops – they would often incorporate various malicious links and further phishing messages claiming virus infections, security software expirations, free gift card claims, and more. Fortunately, you may easily eliminate them by changing your browser settings, as we explain below.
Getting rid of Defenderfordevice.com ads. Follow these steps
Stop browser notifications
Remove unwanted notifications from Google Chrome (desktop):
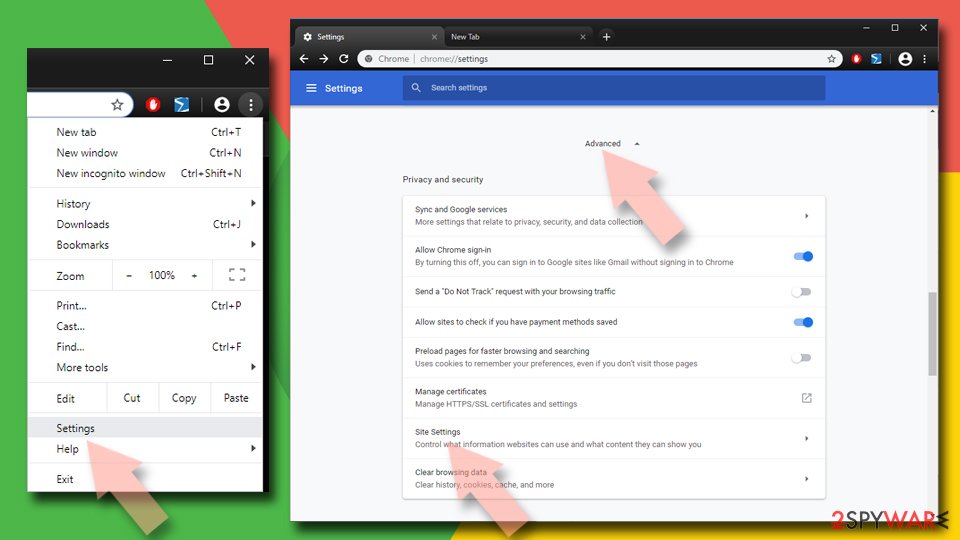
- Open Google Chrome browser and go to Menu > Settings.
- Scroll down and click on Advanced.
- Locate Privacy and security section and pick Site Settings > Notifications.

- Look at the Allow section and look for a suspicious URL.
- Click the three vertical dots next to it and pick Block. This should remove unwanted notifications from Google Chrome.

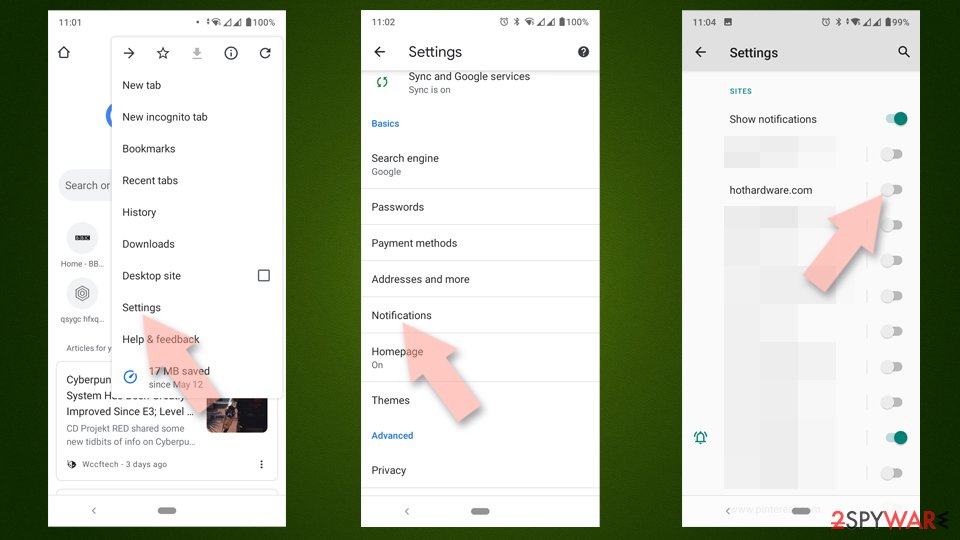
Remove unwanted notifications from Google Chrome (Android):
- Open Google Chrome and tap on Settings (three vertical dots).
- Select Notifications.
- Scroll down to the Sites section.
- Locate the unwanted URL and toggle the button to the left (Off setting).

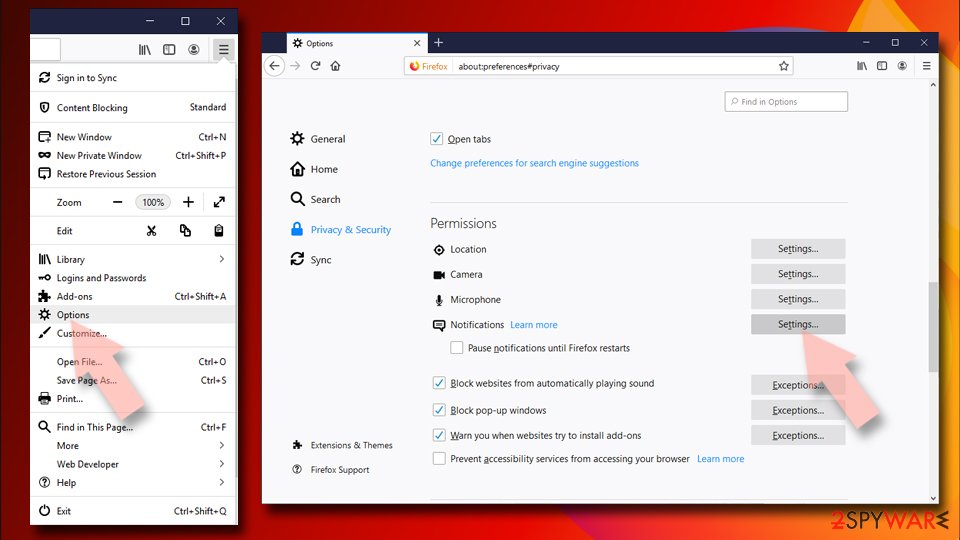
Remove unwanted notifications from Mozilla Firefox:
- Open Mozilla Firefox and go to Menu > Options.
- Click on Privacy & Security section.
- Under Permissions, you should be able to see Notifications. Click the Settings button next to it.

- In the Settings – Notification Permissions window, click on the drop-down menu by the URL in question.
- Select Block and then click on Save Changes. This should remove unwanted notifications from Mozilla Firefox.

Remove unwanted notifications from Safari:
- Click on Safari > Preferences…
- Go to the Websites tab and, under General, select Notifications.
- Select the web address in question, click the drop-down menu and select Deny.

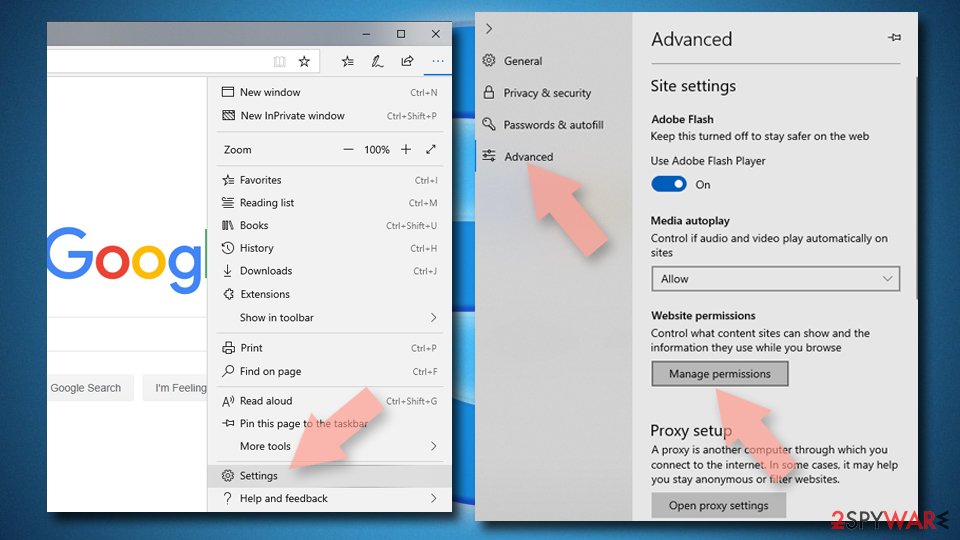
Remove unwanted notifications from MS Edge:
- Open Microsoft Edge, and click the Settings and more button (three horizontal dots) at the top-right of the window.
- Select Settings and then go to Advanced.
- Under Website permissions, pick Manage permissions and select the URL in question.

- Toggle the switch to the left to turn notifications off on Microsoft Edge.

Remove unwanted notifications from MS Edge (Chromium):
- Open Microsoft Edge, and go to Settings.
- Select Site permissions.
- Go to Notifications on the right.
- Under Allow, you will find the unwanted entry.
- Click on More actions and select Block.

Remove unwanted notifications from Internet Explorer:
- Open Internet Explorer, and click on the Gear icon at the top-right of the window.
- Select Internet options and go to the Privacy tab.
- In the Pop-up Blocker section, click on Settings.
- Locate web address in question under Allowed sites and pick Remove.

How to prevent from getting adware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Adware. Investopedia. Source of financial content on the web.
- ^ Phishing attacks. Imperva. Application and data security.
- ^ HTTP cookie. Wikipedia. The free encyclopedia.