How to remove Defray777 ransomware
Defray virus Removal Guide
What is Defray ransomware virus?
Defray777 is malicious ransomware virus that keeps targeting the health-care industry

Defray ransomware (alternatively known as Defray777) is a dangerous crypto extortionist that seeks to gain profit from various companies (health care industry in particular) and home users by encrypting their data and demanding ransom. After being discovered in 2017, Defray virus came back at the end of 2018 and continued its activity in 2019 with a few new distinct features. This highly-targeted cryptovirus is using both AES-256 and RSA-2048 encryption algorithms. Once it finishes its encryption, Defray777 displays a personalized !!!_Read_Me_How_To_DeCrypt_Files_!!!.txt ransom note. The most interesting part of the attack is that the text in the ransom note, extension, and email address are tailored to each victim separately.
| Name | Defray; Defray777 |
|---|---|
| Type | Ransomware |
| Also called | Defray 2018 ransomware; Company_Name ransomware |
| First detected | 2017 |
| Main Targets | Health Care industry, companies, businesses, home users |
| File extension | .***777, .[company name]777 or random characters containing victim's identification |
| Ransom amount | $5000 |
| Ransom note | !!!_Read_Me_How_To_DeCrypt_Files_!!!.txt; FILES.txt,HELP.txt |
| Encryption method | AES-256 and RSA-4096 |
| Elimination | Use antivirus and remove Defray ransomware |
In the beginning, the ransomware was spreading only in the UK[1] and the US countries. Its main features included the following:
- encrypts data with the combination of AES-256 and RSA-2048 algorithms;
- demands $5000 in ransom;
- targets preselected companies, education institutions, and hospitals;
- spreads via .doc files;
- disables startup recovery and monitors Task Manager commands;
- deletes shadow volume copies.[2]
Furthermore, the cybercriminals present three email addresses to contact them for files' recovery:
- glushkov@protonmail.ch,
- glushkov@tutanota.de,
- igor.glushkov.83@mail.ru.
Though email domains suggest that perpetrator might be a Russian speaker, it might be only a diversion as the ransom note is written in the sophisticated and correct English manner. Despite the warnings noted in the ransom message, we urge you to remove Defray ransomware. FortectIntego might be of assistance in this process and PC repair.
Since the malware does not target all companies globally, but only a selected number of them, it is likely that the perpetrator or a group of them are seeking to extort money rather than cause global chaos as it has been with the cases of WannaCry and Petya viruses. However, there is no doubt that you should take care of Defray removal right after it reveals about itself on your computer system.
Defray ransomware functionality
After a targeted user clicks on the infected .doc file, he or she sees a counterfeited message supposedly containing an integrated video message. To activate Defray777, the victims have to launch the video. Since the malware targets hospitals, the file was called “Patient Report.”[3] The malware gained its name due to the request command to defrayable-listings.000webhostapp[.]com. However, it is not likely to append any exceptional file extensions.
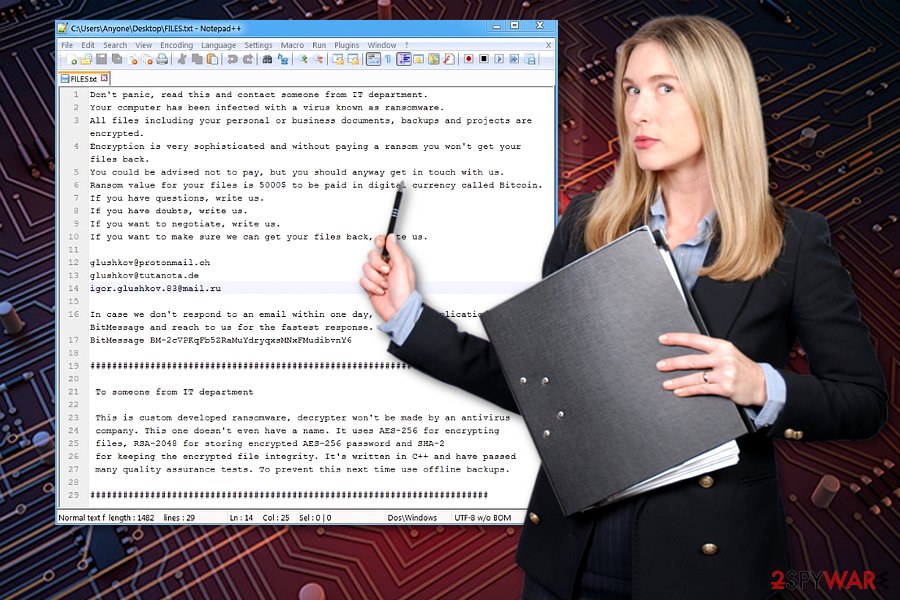
Defray ransomware also leaves two files – FILES.txt and HELP.txt — with the identical content. The message does not contain any exaggerated warning. Here are two different extracts of it:
Don’t panic, read this and contact someone from IT department.
Your computer has been infected with a virus known as ransomware. All files including your personal or business documents, backups and projects are encrypted.
Encryption is very sophisticated and without paying a ransom you won’t get your files back.
You could be advised not to pay, but you should anyway get in touch with us.
Ransom value for your files is 5000$ to be paid in digital currency called bitcoins.
If you have questions, write us.
If you have doubts, write us.
If you want to negotiate, write us.
The new version Defray777 is tailoring extensions and email addresses to each victim
The latest version of Defray, Defray777 ransomware, was discovered in November of 2018. It differs from the previous ransomware variant because it uses a few distinct features to the mix:
- adds .***777 file marker to encoded data;
- targets companies in various industries;
- the most recent version focuses on the health-care industry;
- the ransom added on the system Read_Me_How_To_DeCrypt_Files !!!__!!!.txt;
- the email is named according to the victim with the @yandex.ru;
- the ransom message is also personalized to each victim.
The ransom note displays the following:
Hello, [XXXXXX]!
Don't panic, read this and contact someone from IT department.
Your computer has been infected with a virus known as ransomware.All files including your personal, confidential or business documents, backups and projects are encrypted.
We have also downloaded all information about your clients including their personal data.If you want to restore all your files, avoid harm to your reputation (which may lead you to bankrupt), save your Intellectual property and personal data of your clients, you need to make the payment.
Otherwise, all you files including your customer's information, will be posted on the Internet.We can decrypt for you one of the files (about 50kb) for free, so you have no doubts in data security and possibility to restore the files any time.
After the full payment, all data will be restored on all computers of your network.
We accept payments in Bitcoin.
Make sure to make payment as soon as possible to avoid any penalty.Don't hesitate to contact us.
Our e-mail: [XXXXXX]@yandex.ru
In case we don't respond to an email within one day, download application called BitMessage and reach to us for the fastest response.
BitMessage identity: BM-2cXL8BPGoPKnTvoUVGDwFXmUoQmkVdzsGm
BitMessage homelink: https://bitmessage.org#########################################################################
This is custom developed ransomware, decrypter won't be made by an antivirus company.
This one doesn't even have a name.
It uses AES-256 for encrypting files, RSA-4096 for storing encrypted AES-256 password.
It's written in C and have passed many quality assurance tests.#########################################################################
IN ORDER TO PREVENT DATA DAMAGE:
– DO NOT MODIFY ENCRYPTED FILES
– DO NOT CHANGE DATA BELOW
Employ reputable anti-malware tools and make sure that Defray777 removal is performed properly. You cannot decrypt encoded files, so delete this malware and then try data backups to replace affected files with safe ones. Also, you can check data recovery methods below the article. We have a few tips on virus termination too.
Ransomware has mostly been spread via email attachments
Ransomware is a threat that uses silent infiltration techniques and starts malicious processes immediately after infection. It spreads mainly through spam emails. Thus, beware that the file containing this malware might be named as the file supposedly sent from an official institution.
The file may also be named as an invoice. Such emails also contain a lack of proper credentials or typos, but the primary information can be disguised as official PayPal, Amazon or eBay notice with financial documents attached to the email.
Remember that other malware can also be responsible for cyber infections like this. Trojans may get on the system via the same malicious macros in MS document. However, many hackers design trojans as ransomware payload distributors.
Eliminate Defray777 malware and fix virus damage
All ransomware developers will warn you not to use any third-party data recovery tools. However, there are alternatives. Indeed, due to the sophistication of this malware, there is no decryption tool available yet. You need a complete Defray777 removal instead.
To remove Defray777 ransomware you need reputable anti-malware tools like FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. In case you cannot launch the malware removal utility, you will benefit from the below instructions.
Though the threat deletes shadow volume copies, you might restore the data from backup copies[4]. At the very bottom of the page, you might find some of the recommended tools to be of use.
Getting rid of Defray virus. Follow these steps
Manual removal using Safe Mode
In case the malware prevents you from launching malware elimination program, reboot Windows in Safe Mode and complete Defray removal./GI]
[GI=method-2]As an alternative option, try System Restore feature in Defray777 removal
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Defray from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Defray, you can use several methods to restore them:
What is Data Recovery Pro?
This tool is designed to assist users in retrieving damaged and lost files. It might be helpful in recovering the files affected by Defray virus as well.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Defray ransomware;
- Restore them.
Windows Previous Version feature is yet another alternative for file backups that you can freely use
If System Restore was enabled before, you could restore files using Windows Previous Versions feature
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
The official Defray777 decryptor is not possible
As long as the official Defray777 decryptor is not available, use your file backups to recover encrypted files.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Defray and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Eliminate computer malware. Novirus. News and malware removal guides.
- ^ Chris Brook. Defray ransomware seen targeting education, healthcare industry . ThreatPost. The first stop for security news.
- ^ Defray - New Ransomware Targeting Education and Healthcare Verticals. Proofpoint. The Leader in Cyber Security Solutions.
- ^ Linas Kiguolis. The Importance of Plan B: Why Data Backups are Necessary. TecoReviews. The Ultimate Destination for News and Reviews.
