DeroHE ransomware (Improved Instructions) - 2021 update
DeroHE virus Removal Guide
What is DeroHE ransomware?
DeroHE ransomware – a virus that spreads via hacked IObit emails
DeroHE ransomware is a cryptovirus that encrypts personal data, renames it by appending .DeroHE extension to original filenames and demands a payment in cryptocurrency Dero to get the locked files back. It also generates ransom notes titled READ_TO_DECRYPT.html and FILES_ENCRYPTED.html. These files contain the message that demands money directly from victims and lists all the instructions needed for Dero cryptocurrency transfers.
This virus's first campaign involved email hacking, and the payload was installed when people clicked that free membership offers from emails. Since the infection spreads quickly, people only notice already encrypted files, not the infection itself, so there are a few solutions from there. There are no details about DeroHE ransomware decryption options, and the best options for the removal, and file recovery remain AV tools and data backups.
If you've received an email from webmaster@iobit.com offering you a free one year license, please DON”T OPEN IT! IObit was recently hacked, and emails containing the ransomware virus were sent out to tens of thousands of IObit clients all over the world. If you are one of the victims, then we're glad you came straight to us. This article explains how this ransomware infected your devices, how to prevent that in the future, and how to eliminate this cyber threat.
| name | DeroHE ransomware |
|---|---|
| type | Ransomware |
| Distribution | Spam emails from webmaster@iobit.com offering a free one year license |
| Appended file extension | Original filenames are appended.DeroHE extension |
| Ransom note | READ_TO_DECRYPT.html, FILES_ENCRYPTED.html |
| Ransom amount | 200 Dero coins (approx. $100) |
| Criminals crypto wallet | dERiqiUutvp35oSUfRSTCXL53TRakECSGQVQ2hhUjuCEjC6z SNFZsRqavVVSdyEzaViULtCRPxzRwRCKZ2j2ugCg5r9T1Bf8Wh79tRctx8vg7 |
| Criminals Tor Website | deropayysnkrl5xu7ic5fdprz5ixgdwy6ikxe2g3mh2erikudscrkpqd.onion |
| Detection names | Program:Win32/Wacapew.C!ml, Artemis!E93FC5B53299, ML.Attribute.HighConfidence, etc.[1] |
| Additional information | Victims are urged to push IObit to send the assailants $100,000. If the company would do that, the hacker would allegedly decrypt all infected computers for free |
| Virus removal | All types of malware should be eliminated properly with trustworthy anti-malware applications. You can find additional tips for such a procedure below |
| System Repair | Almost always, malware infections corrupt certain system files and settings. To restore your machine back to normal, use the powerful FortectIntego system repair tool |
Our research suggests that for the time being, the ransomware is distributed exclusively through a hack of IObit, a company that specializes in various Windows tune-up tools. The cyber infection is delivered by spam emails originating from a legitimate IObit email address – webmaster@iobit.com.
In no way does that mean that later on, this malware can't be delivered in other ways, such as file-sharing platforms, deceptive ads, and so on. To protect devices from such perils, users must have a professional anti-malware tool, like SpyHunter 5Combo Cleaner or Malwarebytes running on the machines from time to time.
DeroHE ransom note is long and very informative. Usually, cybercriminals prefer Bitcoins as a payment method. Developers of this cryptovirus are asking for Dero coins. And they're urging their victims to contact IObit. If the company forwards $100,000 in Dero coin to the assailants, they promise to decrypt everyone's computer for free.
Otherwise, creators of ransomware are asking for 200 Dero coins, which equals almost $100, to be sent to their crypto-wallet – dERiqiUutvp35oSUfRSTCXL53TRakECSGQVQ2hhUjuCEjC6z SNFZsRqavVVSdyEzaViULtCRPxzRwRCKZ2j2ugCg5r9T1Bf8Wh79tRctx8vg7.
When the payment is received, they will provide a decryption tool. Here's the full message from the READ_TO_DECRYPT.html:
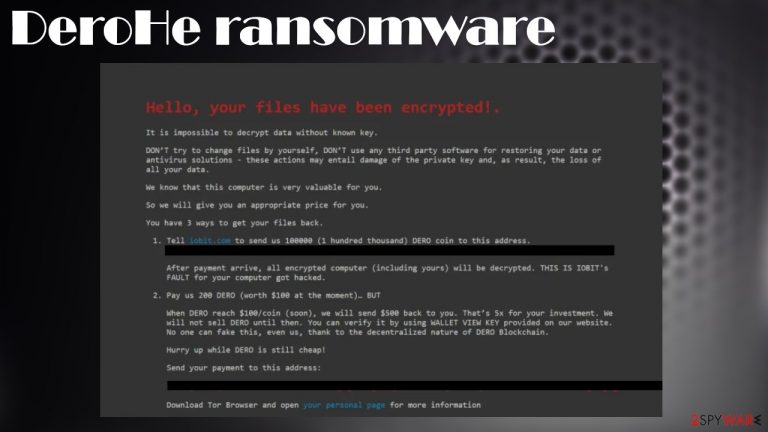
Hello, your files have been encrypted!.
It is impossible to decrypt data without known key.DON’T try to change files by yourself, DON’T use any third party software for restoring your data or antivirus solutions – these actions may entail damage of the private key and, as result, the loss of all your data.
We know that this computer is very valuable for you.
So we will give you an appropriate price for you.
You have 3 ways to get your files back.
Tell iobit.com to send us 100000 (1 hundred thousand) DERO coin to this address. dERopYDgpD235oSUfRSTCXL53TRakECSGQVQ2hhUjuCEjC6z SNFZsRqavVVSdyEzaViULtCRPxzRwRCKZ2j2ugCg26hRtLziwu
After payment arrive, all encrypted computer (including yours) will be decrypted. THIS IS IOBIT's FAULT for your computer got hacked.
Pay us 200 DERO (worth $100 at the moment)… BUT
When DERO reach $100/coin (soon), we will send $500 back to you. That’s 5x for your investment. We will not sell DERO until then. You can verify it by using WALLET VIEW KEY provided on our website. No one can fake this, even us, thank to the decentralized nature of DERO Blockchain.
Hurry up while DERO is still cheap!
Send your payment to this address:
dERiqiUutvp35oSUfRSTCXL53TRakECSGQVQ2hhUjuCEjC6z SNFZsRqavVVSdyEzaViULtCRPxzRwRCKZ2j2ugCg5r9T1Bf8Wh79tRctx8vg7
Download Tor Browser and open your personal page for more information
Don’t have $100 to invest?
We have some free, easy task for you to do (online social network activity). Once your works meet our requirements you will get your files back for free. Please visit our website for more information.
FAQ:
Do you accept bitcoin, monero or others crypto currencies?No. We want DERO only. Because we believe DERO is true and the best privacy coin. It's fast and secure. You don't need to wait hours to send your payment, only seconds. Soon DERO dev team will release Private Smart Contract powered by Homomorphic Encryption. To learn more about DERO, visit twitter.com/deroproject
Where I can buy DERO?
You can buy your Dero at: tradeogre.com or kucoin.com at the moment.
Do I have to enter payment id?
No. Your provided address is already included payment id to it (integrated address).
Can I make multiple payment?
Yes. You can send multiple payment. Your balance will be added up. When your balance >= required balance, you will get your decryption key. It RECOMMEND that you send a test payment with small amount first to make sure everything work perfectly.
How do I get decryption tool?
Download Tor Browser and open our website, paste your unique payment address and click check button
DERO IS THE NEXT BITCOIN
Threat actors behind ransomware attacks should never be trusted. Paying the cybercriminals could lead to a lose-lose situation with any of these scenarios coming to life:
- No decryption tool is delivered.
- The delivered tool doesn't work.
- Assailants ask for more money.
- More malware is sent instead of the decryption software.
Our cybersecurity team recommends all affected users to remove DeroHE ransomware from their devices. Use any of the aforementioned anti-malware software or similar tools to properly eliminate the cyber infections with all of its particles that could be spread out through the system.
Typically, malware infections make various changes to the system files and settings, which might lead to system instabilities, such as freezing, severe lag, crashing, BSoD, and others. To restore your system back to normal after ransomware removal, we highly advise using the FortectIntego system repair tool.
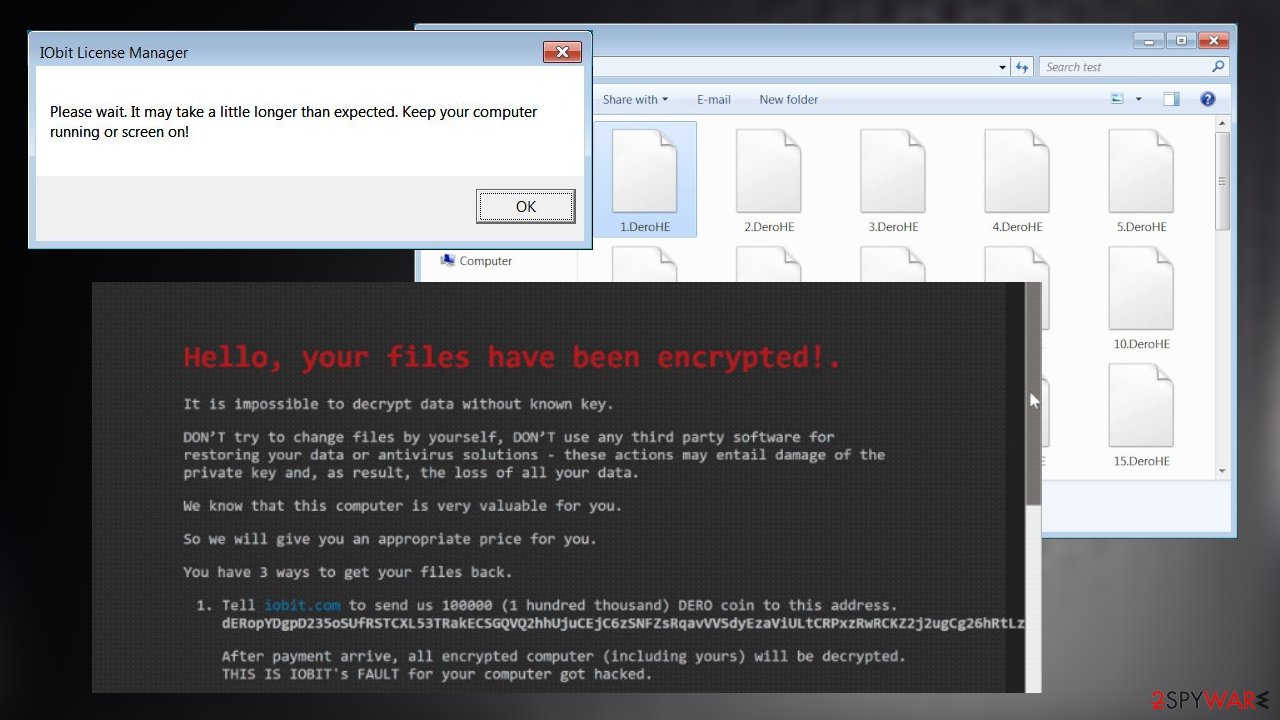
The widespread attack used to distribute malware involves IObit hack
IObit forum members received emails with claims that these messages are from the company. Offers for a free one year license to the software and special perks of being a forum member included particular Get It Now links that redirected to promo links. Those sites no longer exist, but pages were distributing malicious zip files with the payload of this threat.
Digitally signed data got packed into that zip file, and one of those files – malicious DLL version. Once executed, the IObit License Manager.exe file launched the DLL file that installed DeroHe ransomware on the targeted machine.
The message appearing on the fake alert stating about the license that masked the encryption and infiltration processes, so the user cannot shut down the computer while ransomware infiltrates:
Please wait. It may take a little longer than expected. Keep your computer running or screen on!
Since those files were signed using IObit's' certificates users, fell for the trick and installed malware instead of the legitimate license that was offered. The attack was aimed at all members of the forum.
Simple steps to prevent malware infections increasing your cybersecurity level
Cybersecurity experts predict[2] that ransomware attacks will cost around $20 billion in 2021. Other malware, such as trojan,[3] keyloggers, etc., developers aren't sleeping either. That's why our IT specialist team compiled a simple list of directions to evade malware by increasing your cybersecurity level:
- Keep backups of all essential files. Store them in two different locations, e.g., cloud, offline storage device.
- Purchase professional anti-malware tool and update its virus database regularly. Also, scan the entire system at least once a week.
- Install all the latest updates to your operating system and other software.
- Maintain system files and settings at bay with system repair tools.
- Refrain from visiting shady websites, file-sharing platforms, like The Pirate Bay, eMule, and others.
- Learn how to identify a spam email. Please don't open any links or download any attachments that urge you to visit a site, download it, etc. Don't get tricked by promos that are too good to be true.
Guide for DeroHE ransomware removal from infected computers
Our research team has stated that spam emails containing virus payload files are coming from the webmaster@iobit.com email address. So whatever you do – don't open these emails or, even worse, download what it's offering.
But who doesn't like free stuff delivered to their doorstep? If you've got tricked into downloading the offered software, and now your files are encrypted and appended with .DeroHE extension, you chose the right cybersecurity portal to help you solve this unpleasant incident.
Manual infection removal is possible, but it's not a walk in the park, so we suggest leaving it to the professionals. Remove ransomware by running a full system scan with reliable anti-malware tools such as SpyHunter 5Combo Cleaner or Malwarebytes and delete the infection with any other suspicious files software detects.
Afterward, experts[4] recommend cleaning up and restoring your system by using a powerful system repair tool in FortectIntego. Users are advised to do that after DeroHe ransomware removal because this type of malware corrupts system files. If left unattended, the system might exhibit abnormal behavior, such as overall performance loss, crashing, freezing, etc.
Getting rid of DeroHE virus. Follow these steps
Manual removal using Safe Mode
Delete computer viruses in Safe Mode with Networking, if they're blocking the use of anti-malware tools in normal mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove DeroHE using System Restore
Computer infections could also be removed with System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of DeroHE. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove DeroHE from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by DeroHE, you can use several methods to restore them:
Using Data Recovery Pro to restore files
This app might help to recover .DeroHE extension files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by DeroHE ransomware;
- Restore them.
Restore individual files with Windows Previous Version feature
Using this feature, users might restore .DeroHE extension files one at a time.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer could also be used for data recovery
Usually, cryptoviruses remove Shadow Volume Copies that Shadow Explorer uses to recover files. If they are still intact then this software might help to restore data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryptor is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from DeroHE and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Access your website securely from any location
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. The best solution for creating a tighter network could be a dedicated/fixed IP address.
If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for the server or network manager that needs to monitor connections and activities. VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world.
Recover files after data-affecting malware attacks
While much of the data can be accidentally deleted due to various reasons, malware is one of the main culprits that can cause loss of pictures, documents, videos, and other important files. More serious malware infections lead to significant data loss when your documents, system files, and images get encrypted. In particular, ransomware is is a type of malware that focuses on such functions, so your files become useless without an ability to access them.
Even though there is little to no possibility to recover after file-locking threats, some applications have features for data recovery in the system. In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
- ^ Detection results. VirusTotal. Online malware scanner.
- ^ Steve Morgan. Global Ransomware Damage Costs Predicted To Reach $20 Billion (USD) By 2021. Cybersecurityventures. Cybersecurity industry magazine.
- ^ Trojan horse (computing). Wikipedia. The free encyclopedia.
- ^ Zondervirus. Zondervirus. Spyware and security news.







