Dont_Worry ransomware (Easy Removal Guide) - May 2018 update
Dont_Worry virus Removal Guide
What is Dont_Worry ransomware?
Dont_Worry ransomware is a virus that threatens victims by encrypting computer files

Dont_Worry ransomware is a crypto-virus that initially emerged from Crypto_Lab and is a part of AMBA virus family. The first version appeared in April 2018, and encrypted files using email_ransom-random_ID{16} file extension, as well as dropped a ransom note called Dont_Worry.txt. The second variant uses.UPS-[random_ID] appendix to lock up files and has a slightly extended message. Both variants use AES/RSA cipher and are not decryptable.
| SUMMARY | |
| Name | Dont_Worry ransomware |
|---|---|
| Type | Crypto-virus |
| Ransom note | Dont_Worry.txt |
| Executable files | dwintl_x64.exe, gwintl.exe ; dwintl.exe |
| Appendix | email_ransom-random_ID{16}; .UPS-[random_ID] |
| Contact email | wog@onionmail.info ; ups@torbox3uiot6wchz.onion |
| Disribution | Spam emails, malicious websites, torrent sites, etc. |
| File recovery | From backup. Otherwise, check for alternative methods below this article |
| Elimination | Download and install FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. Start the program in Safe Mode with Networking |
All the infections occurred in Russia, meaning that Russians are primary targets of this crypto-malware. Nevertheless, that does not mean that the ransomware cannot strike elsewhere – the internet is worldwide. Therefore, do not let your guard down and, if infected, immediately remove Dont_Worry virus from your machine.
Dont_Worry virus enters via contaminated dwintl_x64.exe and gwintl.exethe files and immediately performs malicious changes to the system. Malware implements the following steps to strengthen its presence:
- The version of the virus is easily customizable. Hence, it can be modified for each individual attack, making it harder to extinguish
- The infection starts with data gathering – both anonymous (software and hardware) and private (email, name, passwords, credentials, etc.). This information is used to bypass security and other software that might prevent the virus from executing its malicious tasks
- The virus further changes system's configuration, including a modification to registry entries,[1] boot options, and system parameters
The mentioned changes allow Dont_Worry ransomware to boot up every time the system is launched. Additionally, these modifications can impact computer's performance, making apps freeze or crash, making the machine respond slowly, etc.
Dont_Worry can encrypt various files, including .doc, .xlsx, .pdf, .7zip, .jpg and many others. Nevertheless, there are few formats that the data locker skips, including mp3, .mp4, .avi, .exe, .sys and few others. The ransomware appends the email_ransom-random_ID{16} file extension to each of the files. For example, the file called random.doc would be turned into random.doc.wog@onionmail.info-4668ffbf455b468c.
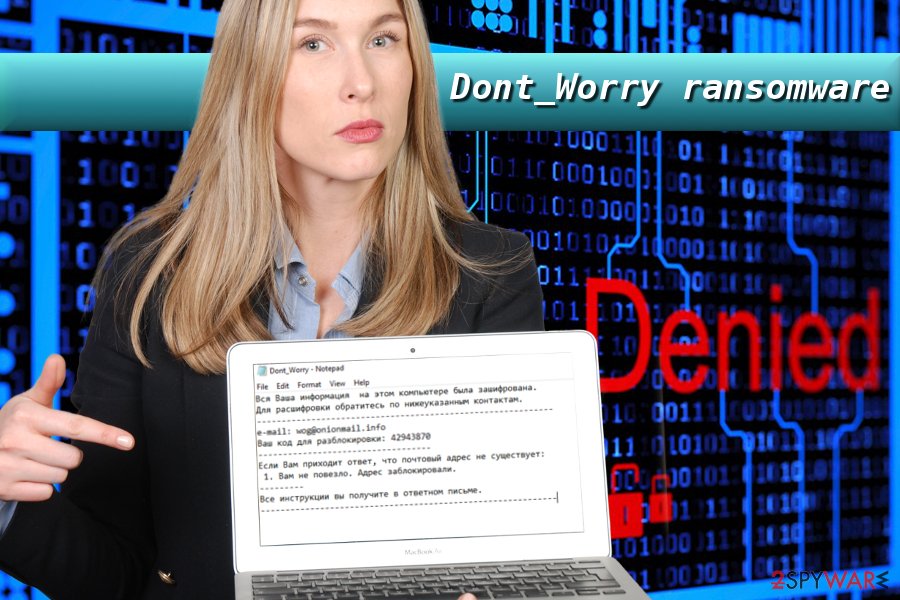
Dont_Worry ransom note states the following:
All your information on this computer has been encrypted.
To decrypt refer to the contacts listed below.e-mail: wog@onionmail.info
Your code for unlock: 42943870If you receive an answer that the mailing address does not exist:
1. You are unlucky. The address was blocked.You will receive all instructions in the reply letter.
As evident, hackers rely on Tor browser anonymous email service to communicate with victims. The size of the ransom is not mentioned in the note, so it seems like hackers inform users in the email. Nevertheless, we advise you not to contact cybercriminals as they are often known to ignore victims, even after all their demands are fulfilled.
Dont_Worry ransomware removal should be your first action. We strongly advise using a powerful anti-malware program, such as FortectIntego or Malwarebytes. To avoid damage to system files, we do not recommend manual elimination.
You should only proceed with file recovery after full virus elimination. Unfortunately, the only 100% safe way to recover your files is by restoring them from a back-up, stored on a remote server or externally. Alternatively, we offer other recovery methods – please check below.
Second variant of the Dont_Worry ransomware
The second version of the crypto-malware was spotted by security experts[2] in May 2018. It encrypts files using UPS-[random_ID] file extension and its main executable is dwintl.exe. Despite the ransom note having the same name (Dont_Worry.txt), the new variant of Dont_Worry virus brings a more detailed explanation of what exactly has to be done in order to obtain the decryptor from cybercriminals.
Victims are asked to download and install Tor browser[3], create a new email account and contact bad actors using ups@torbox3uiot6wchz.onion email address. As usual, we advise users to refrain from communicating with hackers and fulfilling their demands.
The ransom note states the following[translated from Russian]:
All of your information on this computer was encrypted.
For decryption, you will have to do the following:
1. Download and install Tor browser:
https://www.torproject.org/download/download-easy.html
2. Open Tor browser, go to the following address to register a new email account:
http://torbox3uiot6wchz.onion/signup-en.php
3. Enter the mailbox:
http://torbox3uiot6wchz.onion/sm/
4. Write a letter to the following address:
e-mail: ups@torbox3uiot6wchz.onion
Write your ID for file decryption: ***
5. Wait for an answer.Note that we will not be able to get emails from usual addresses, apart from those in the following list:
http://torbox3uiot6wchz.onion/relay-en.php
Only two infections were spotted so far, but that does not mean that the virus will not spread further. Both victims were from Russia, suggesting that the second variant of Dont_Worry is still targeting Russian-speaking users.
![Dont_Worry UPS-[random_ID] extension Dont_Worry UPS-[random_ID] extension](https://www.2-spyware.com/news/wp-content/uploads/virusai/dont-worry-ransomware-ups-random-id_en.jpg)
The way malware is distributed
Most prominent ransomware distribution method is via spam emails. This allows hackers to trick users into opening a malicious file and infecting the system instantaneously. Thus, this method is quick and efficient and widely used. Security experts[4] warn that all the emails coming from unknown sources should be ignored and deleted immediately. Finally, recognizing suspicious emails is critical too so you should check out some examples[5] online.
Other distribution methods of ransomware:
- Torrent and other peer-to-peer websites;
- Hacked sites;
- Exploit kits;
- Repacked and infected installers;
- Keygens, etc.
Remove Dont_Worry ransomware from your computer and then attempt file recovery
As we already mentioned, we highly discourage users from attempting manual Dont_Worry removal. Crypto-virus is a complicated code that is embedded deep within system files. Tampering with those files might lead to permanent software damage.
Therefore, we urge you to remove Dont_Worry virus by using security software – FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes. These programs can find and eliminate the threat immediately. Do not attempt file recovery before you fully delete the virus as all the files will get encrypted again.
Getting rid of Dont_Worry virus. Follow these steps
Manual removal using Safe Mode
If Dont_Worry virus prevents security software from starting, enter your computer in Safe Mode with Networking:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Dont_Worry using System Restore
You can try to eliminate the threat using System Restore. Simply follow these instructions:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Dont_Worry. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Dont_Worry from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.You can safely recover your files from an external HDD or a remote server. However, if you did not have the back-up you should try the following options.
If your files are encrypted by Dont_Worry, you can use several methods to restore them:
See if Data Recover Pro can assist you with file recovery
This tool is used to recover corrupted or deleted files. Nevertheless, it can sometimes help to recover files affected by ransomware.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Dont_Worry ransomware;
- Restore them.
Windows Previous Versions feature could be an option
If you had System Restore enabled before the attack, you can return your files back using this method:
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try ShadowExplorer
Shadow volume copies are used to automatically copy your files by Windows. Therefore, if the Dont_Worry virus left these intact, you are in luck:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryptor is not available yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Dont_Worry and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Structure of the Registry. Microsoft. Windows Dev Center.
- ^ MalwareHunterTeam. Twitter. Social Network.
- ^ What is Tor Browser?. Tor Project. Official download page.
- ^ Ioys. Ioys. Greek security experts.
- ^ Charles Johnson. 15 Examples of Phishing Emails from 2016-2017. EDTS. Knowledge in Technology.





















