DVPN ransomware (Virus Removal Guide) - Improved Instructions
DVPN virus Removal Guide
What is DVPN ransomware?
DVPN ransomware – a file-targeting parasite that provides a ransom message written in the Chinese language
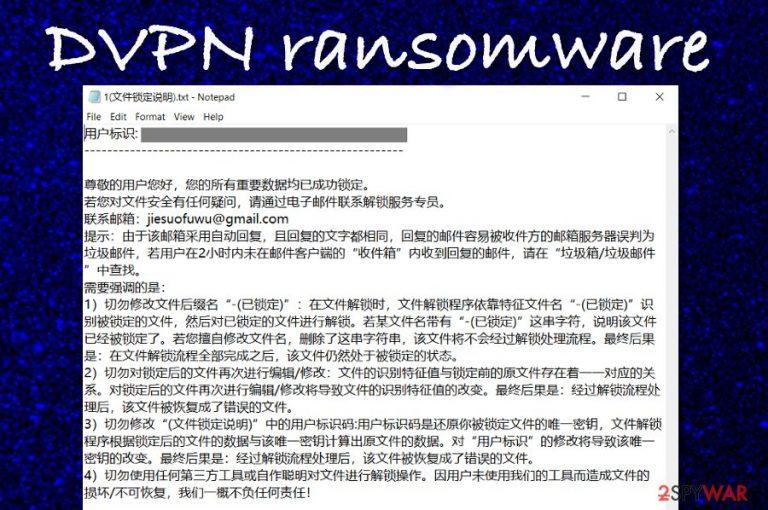
DVPN ransomware is considered to be a data-locking virus that uses the XOR cipher[1] to block files. Since the ransomware attaches an extension in the Chinese language – (已锁定), we have discovered that it can be translated to – (a locked). All files, folders, and documents that are placed on the attacked Windows device fall for the encryption. Then, DVPN ransomware developers provide the ransom message also named in Chinese – 1 (文件锁定说明) .txt, that can be translated to 1 (Description of a locked file) .txt. Criminals urge users to contact them via jiesuofuwu@gmail.com email address and discuss all the matters related to file security and recovery.
When DVPN ransomware travels on a Windows operating system, it does not just stay in one place. The malware can modify various directories such as The Task Manager, Windows Registry, and Control Panel. It is known that the virus brings such files to the computer: dvpn.exe, dstatus.ini, dvpn.dll, .dvpn64.dll, pac.txt some of which can be responsible for the encryption process, disabling antivirus software, executing DVPN ransomware every time the computer is booted, and running other malicious processes in the background.
DVPN ransomware infiltration can happen all of a sudden when you least expect it. However, malicious actors have learned different tactics that allow manipulating users and inserting malicious payload when they lack attention or simple knowledge of cybersecurity. Most of the time ransomware targets regular users and companies through email spam[2] messages that come from a non-existing organization or person. Furthermore, the malware can also be received when RDP configuration gets hacked, the user downloads cracked software such as a key generator, or steps on a malicious ad.
| Name | DVPN ransomware |
|---|---|
| Type/category | Ransomware virus/malware |
| Target | According to the language of the provided extension and the ransom note, this malicious string targets Chinese-speaking people |
| Encryption | The encryption process is performed by employing the XOR cipher. This key can lock all types of files, folders, and documents that are found on the infected Windows machine |
| Extension | When the encryption cipher completes its job, an appendix is added to each filename. Translation to English – (a locked) |
| Ransom note | The name of the translated ransom note is 1 (Description of a locked file) .txt. Here crooks provide the jiesuofuwu@gmail.com email address for making contact and discussing all the conditions for recovering blocked files |
| Related files | The ransomware virus brings these types of files to the computer system: dvpn.exe, dstatus.ini, dvpn.dll, dvpn6e.dll, and pac.txt |
| Spreading | The malicious payload can be carried through email spam messages and the infectious attachments that get clipped to the letters. Also, ransomware is distributed through software cracks, vulnerable RDP configuration, and malicious advertisements |
| Elimination | If you have been looking for a way to get rid of the cyber threat, we recommend using only reliable security software as manual elimination might not be that safe for a process like this one |
| Fix software | Finding some damage related to the malware attack is also possible. If you do not know what to use for the repair process of the corrupted areas, try employing FortectIntego |
As you can see the main target of DVPN virus are Chinese-speaking people, so those who do not speak this language and get infected with the cyber threat will not be able to understand a thing the ransom note says unless they translate it to English. However, we decided to make things easier for all of you and have provided the already translated version:
ID of the User: Q61 + XXXXXXXXXXXXXXXXXXXX / xxxxxxxxxxxxxxxxxxx
———————————— ——————–
Dear user, all your important data is successfully blocked.
If you have any questions about the security of your file, please contact a specialist unlock service by email.
Contact email-address: jiesuofuwu@gmail.com
TIP: If your mailbox uses automatic replies, the reply message can easily be wrongly marked as spam email-server of the recipient. If the user does not receive a response in the “Incoming” mail client after 2 hours, when you answer, look at the shopping cart / Spam.
What we need to emphasize is this:1) Do not change the file extension ” – (a locked) “: when you want to unlock the file, the program will unlock the files using typical file name ” – (a locked) ” to identify the locked file, and then unlocks the file. If the file name contains the string “- (locked)”, it means that the file is locked. If you change the file name without permission and remove this line, the file does not pass the unlock process. The end result will be that after the unlocking process, the file will remain locked.
2) Do not edit the / do not change a locked file: there is a to-one correspondence between the characteristics of recognition and source files to lock. Re-editing / changing a locked file will change the file recognition characteristics. The end result: the file after unlocking process is restored to the wrong file.
3) Do not change the user ID in the “(Description of a locked file)”: user ID is a unique key to restore a locked file. File release program reads the original on the basis of the data locked file, and the unique key. File data. Change the “User ID” will change the unique key. The end result: the file after unlocking process is restored to the wrong file.
4) Do not use any third-party tools and do not use their own smart devices to unlock the files. We accept no liability for damage / irreplaceable files, caused by the fact that users do not use our tools!
Cybercrooks who spread DVPN ransomware urge people not to touch (rename or edit) the locked files as the decrypter will not be able to properly recover the data if any alterings are made to it. Furthermore, hackers state that they will not take any responsibility if the victim employs a secondary program to unlock the files and they get corrupted during the process.
Keep in mind that cybercriminals are trying to scare you and make you run out of solutions for file recovery so you will decide to purchase the decryption tool from them at the end. DVPN ransomware aims to lock up all the files and documents that appear on the Windows device during the activation process of the malicious payload.
Afterward, crooks store both encryption and decryption keys on remote servers that are reachable for the creators only. This way you have decreased chances of recovering your files. However, this still does not mean that you have to listen to everything that DVPN ransomware provided message says and rush to pay the demanded ransom price.
Even though DVPN ransomware does not outline any particular requirements for the payment, they will likely be provided to you when you contact the crooks via email. These people can urge for an inadequate price anywhere from $100 to $2000 or more. Of course, they will ask for a cryptocurrency transfer such as Bitcoin, Monero, Litecoin, Ethereum, etc.
DVPN ransomware is likely to demand cryptocurrency payments as this is a way to remain anonymous from tracking. However, you should avoid paying the stated price and these are the reasons why:
- Crooks can not provide you with a key and run off with your money.
- Hackers can give you a fake tool and you will notice it when it is too late.
- You might get increased ransom payments after the first money transfer and will have to pay a very big price to receive the decryption tool.
- There are other alternative tools that you can try rather than paying a ransom.
DVPN ransomware might try to harden the data recovery process for you by deleting the Shadow Volume Copies of your encrypted data through PowerShell commands. This way you will be prevented from using third-party software that relies on safe and undamaged Shadow Copies. However, this is not your only option for file restoring.
Of course, you should remove DVPN ransomware before you start trying to recover your files and documents, otherwise, the process might be unsuccessful. Employ reliable security software that will take care of the entire process and do not try to get rid of the parasite on your own. If there is some damage you need to fix, try repairing things with FortectIntego.
After DVPN ransomware removal, you can try using some data recovery techniques that have been provided at the end of this article. You should pick the method that suits you the most in order to reach the best results possible. Remember that it is not worth to pay the demanded ransom price to the crooks as there is a high chance of getting scammed.
However, data recovery is not the only reason why you should hurry up to uninstall DVPN ransomware from your Windows machine. The cyber threat might also open backdoors for other dangerous infections and you can easily get infected with a trojan or another type of malware that can harvest personal data, damage software, and force the entire PC to crash.
If you find out that your antivirus software cannot detect DVPN ransomware, this might be because the malware is blocking your antimalware product. To diminish such malicious settings and be able to remove the virus properly, you should reboot your computer in Safe Mode with Networking as shown in the instructions at the end of this article.
Email spam and software cracks are closely related to ransomware attacks
Technology specialists from Virusai.lt[3] claim that a lot of tricky email messages are sent by hackers who are looking forward to distributing ransomware-related payload to a big variety of users. Crooks pretend to call themselves by the name of a trustworthy company to create a look of reliability. The user receives the email spam message together with an attachment that holds the malicious payload. Do not open the clipped files without scanning them with antimalware!
Furthermore, hackers are likely to spread ransomware infectious through cracked products such as key generators that end up on peer-to-peer networks[4] such as The Pirate Bay, BitTorrent, and eMule. We recommend using only official and well-known sources for downloading software, services, and other needed products.
To continue, the malicious payload can also enter computer systems when hackers connect to the machine remotely by abusing vulnerable RDP configuration. Regarding this fact, always remember to secure the RDP with a reliable and complex code.
Also, malicious advertisements (malvertising) can be the distribution source of ransomware. What you have to do is avoid clicking on every ad that you see on the Internet, install an adblocking tool on your browser, and purchase reliable security software that will alert if something dangerous is waiting for you on a particular website.
Get rid of malicious payload brought by DVPN ransomware
Using reliable antimalware software is the best option you have for DVPN ransomware removal. First, check if your antivirus program is capable of detecting the malware. If not, the ransomware might be blocking your tool by initiating a malicious task. To diminish all hazardous processes and deactivate the virus from renewing them, you should boot the machine in Safe Mode with Networking.
Afterward, you can successfully continue to remove DVPN ransomware from your Windows device. Do not try to use the manual technique as this type of complex process should be left for professional tools to handle. When the parasite is gone, scan your computer system for possible damage with software such as SpyHunter 5Combo Cleaner or Malwarebytes. If these products find any compromised areas, you can try repairing them by employing FortectIntego.
Getting rid of DVPN virus. Follow these steps
Manual removal using Safe Mode
If you want to deactivate the malicious processes that are operating in the background of your computer system, you should try booting the machine in Safe Mode with Networking.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove DVPN using System Restore
Try to diminish all suspicious changes and disable the ransomware virus itself by using the below-provided guidelines for activating the System Restore feature.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of DVPN. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove DVPN from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by DVPN, you can use several methods to restore them:
Employ Data Recovery Pro and get some of your files back.
If you have been searching for a tool that would help you with reversing your files back to normal, you can give this piece of software a try.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by DVPN ransomware;
- Restore them.
Use Windows Previous Versions feature to restore at least some data.
If you have enabled the System Restore mode in the past and the ransomware virus did not kill any restore points, you can absolutely try this method.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
The impact of Shadow Explorer on files might be a big positive one.
Following all the steps that are required in order should let you reach good results with this tool. However, you should be sure that the ransomware virus did not eliminate the Shadow Volume Copies of your encrypted files before using the software.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, cybersecurity specialists are still working on the official decrypter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from DVPN and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ XOR cipher. Wikipedia. The free encyclopedia.
- ^ Margaret Rouse. Email spam. Search Security. Tech Target.
- ^ SAUGUMO IR VIRUSŲ NAUJIENOS. Virusai. Security and spyware news.
- ^ What is a P2P network?. Quora.com. Relevant questions and answers.







