Flow for Chrome browser extension (virus) - Free Instructions
Flow for Chrome browser extension Removal Guide
What is Flow for Chrome browser extension?
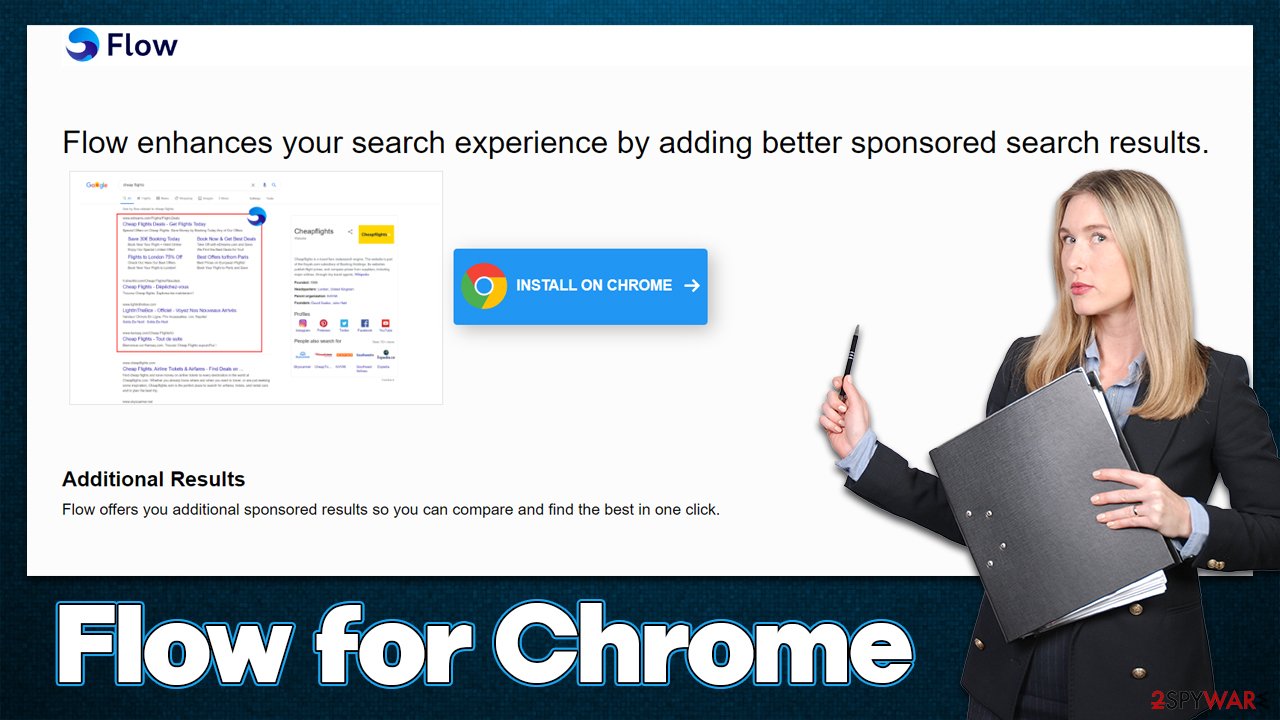
Flow for Chrome is an extension that shows alternative search results to feed ads to users
Flow for Chrome is a browser-hijacking application that could be installed on your browser without your permission. This usually happens because the app might be spread using deceptive distribution methods, including misleading advertisements or software bundling. In some cases, people might install it intentionally due to its alleged functionality. While it's implied that the extension is for Google Chrome, other compatible browsers, such as Chromium MS Edge, might also be affected.
Once installed, Flow for Chrome would immediately change the web browser settings from the default ones. This usually means that the search function and the displayed results are altered by the hijacker the way it was programmed to do. For example, users might see that their searches are being forwarded through a suspicious web address, such as Search.platformkey.com or Alexius-ber.com.
Likewise, hijackers can change the provider that the search results are generated through, which can alter which websites users visit in the first place. The produced results at the top are actually nothing more than ads and sponsored links, which may not always be accurate or even safe to click on.
| Name | Flow for Chrome |
|---|---|
| Type | Browser hijacker, potentially unwanted browser extension |
| Distribution | Software bundling, malicious ads, redirects from other websites |
| Symptoms | Unknown extension installed on the browser; intrusive ads at the top of search results; redirects to potentially dangerous websites; homepage and a new tab is set to tailsearch.com, which forwards searches to Yahoo |
| risks | Redirects to malicious websites can result in intrusive notifications, personal information disclosure to cybercriminals, financial losses, installation of other potentially unwanted programs/malware |
| Uninstall | To remove the unwanted browser extension, you should access your browser's settings section. Checking the system with SpyHunter 5Combo Cleaner security software can also ensure that there is no adware or malware running in the background |
| additional tips | After you eliminate the hijacker, you should also clean your web browsers to avoid tracking and other issues. Take care of it quickly with FortectIntego |
What are the effects of the Flow for Chrome hijack?
Browser hijacking is a relatively old phenomenon that has been employed by various apps. While previously, these potentially unwanted applications used to be even called spyware, their impact on the users' systems has diminished thanks to regulations of appropriate authorities and tech companies significantly.
Nowadays, most browser hijackers come in the form of extensions and are relatively easy to deal with. They are not considered malicious as Trojans, or other serious infections are, although their presence should never be dismissed as fully harmless – especially if the app was not installed intentionally.
The main goal of hijackers is not to provide some type of useful function to users (despite what is claimed in the marketing material) but instead expose users to as many advertisements as possible. This is why many PUPs' functionality is superficial, and many of them are presented as “search result improvers” or similar tools.
Once installed, the app would take over users browsing activities in many ways – insert its own ads on various visited websites and promote sponsored content during users' browsing sessions. This can completely change the way people browse the web and which websites they visit in the first place. As we already mentioned, the promoted material might not always be safe, and Flow for Chrome might start pushing fake updates or other potentially unwanted programs.
The privacy risks are also there, as almost all browser hijackers tend to gather information, such as device identifiers, location, links clicked, search queries, and much more.
How did Flow for Chrome end up on my browser?
If you have not installed the tension yourself, it is likely you have downloaded it along with other programs from third-party sources. Users are known to rush the installation steps of new programs, and that's why software bundling works so well. Mostly, people believe that the hijacker simply appeared on their systems out of nowhere, which is obviously not the case.
Browser hijackers might use methods that are considered deceptive but never malicious. For example, you won't install a browser hijacker after opening malicious spam email attachments or due to software vulnerabilities[1] present on your system. If you see an unwanted extension on your browser, you have installed it yourself – be it willingly or not.
To avoid this, you should always pay close attention to the freeware installation process.[2] Never rush through steps and read the installation instructions carefully. Also, watch out for pre-ticked checkmarks, fine print, misplaced buttons, and similar tricks commonly used by software distributors.
In other cases, users might also install Flow for Chrome after being tricked by a misleading advertisement. For example, a message on a random website might claim that an extension on your browser is outdated and that you need to update it. Remember that updates to the software should only be installed via the official sources, as otherwise, infection of malware might occur.
Removal steps of the browser hijacker
We recommend you start with a full system scan with SpyHunter 5Combo Cleaner or Malwarebytes security software to exclude the possibility of other infections. In some cases, symptoms might be absent completely, as malware is known to be very stealthy thanks to its obfuscation techniques.
Once you are sure that your system is clean from serious threats, you can proceed with Flow for Chrome removal.
Google Chrome
- Open Google Chrome, click on the Menu (three vertical dots at the top-right corner) and select More tools > Extensions.
- In the newly opened window, you will see all the installed extensions. Uninstall all the suspicious plugins that might be related to the unwanted program by clicking Remove.
![Remove extensions from Chrome Remove extensions from Chrome]()
Mozilla Firefox
- Open Mozilla Firefox browser and click on the Menu (three horizontal lines at the window's top-right).
- Select Add-ons.
- In here, select the unwanted plugin and click Remove.
![Remove extensions from Firefox Remove extensions from Firefox]()
MS Edge (Chromium)
- Open Edge and click select Settings > Extensions.
- Delete unwanted extensions by clicking Remove.
![Remove extensions from Chromium Edge Remove extensions from Chromium Edge]()
Safari
- Click Safari > Preferences…
- In the new window, pick Extensions.
- Select the unwanted extension and select Uninstall.
![Remove extensions from Safari Remove extensions from Safari]()
Finally, it would be best if you also clean your web browsers from cookies,[3] caches, and other web data to finalize the whole process. Potentially unwanted programs can implement small files, which might remain within cache folders on a local machine. Thanks to these files, various third parties might continue data tracking.
You can either choose FortectIntego PC repair and maintenance tool to eliminate these leftover files or proceed with the instructions below if you instead want to do it manually:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies, and other site data, as well as Cached images and files.
- Click Clear data.
![Clear cache and web data from Chrome Clear cache and web data from Chrome]()
Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.
![Clear cookies and site data from Firefox Clear cookies and site data from Firefox]()
MS Edge
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.
![Clear browser data from Chroum Edge Clear browser data from Chroum Edge]()
Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.
How to prevent from getting browser hijacker
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Thomas Holt. What Are Software Vulnerabilities, and Why Are There So Many of Them?. Scientific American. Science Magazine.
- ^ Freeware. Wikipedia. The free encyclopedia.
- ^ What are cookies? | Cookies definition. Cloudflare. The Web Performance & Security Company.







