Grt ransomware (Recovery Instructions Included) - Free Instructions
Grt virus Removal Guide
What is Grt ransomware?
Grt ransomware is a malicious Windows program designed to encrypt all user files
Grt is a ransomware-type computer virus that seeks to encrypt all pictures, videos, documents, databases, and other files, which results in users not being able to access them anymore thanks to a sophisticated encryption algorithm[1] used during this process. Also, each of the affected files is appended with a specific extension – .[ID].[ghost@mm.st].grt.
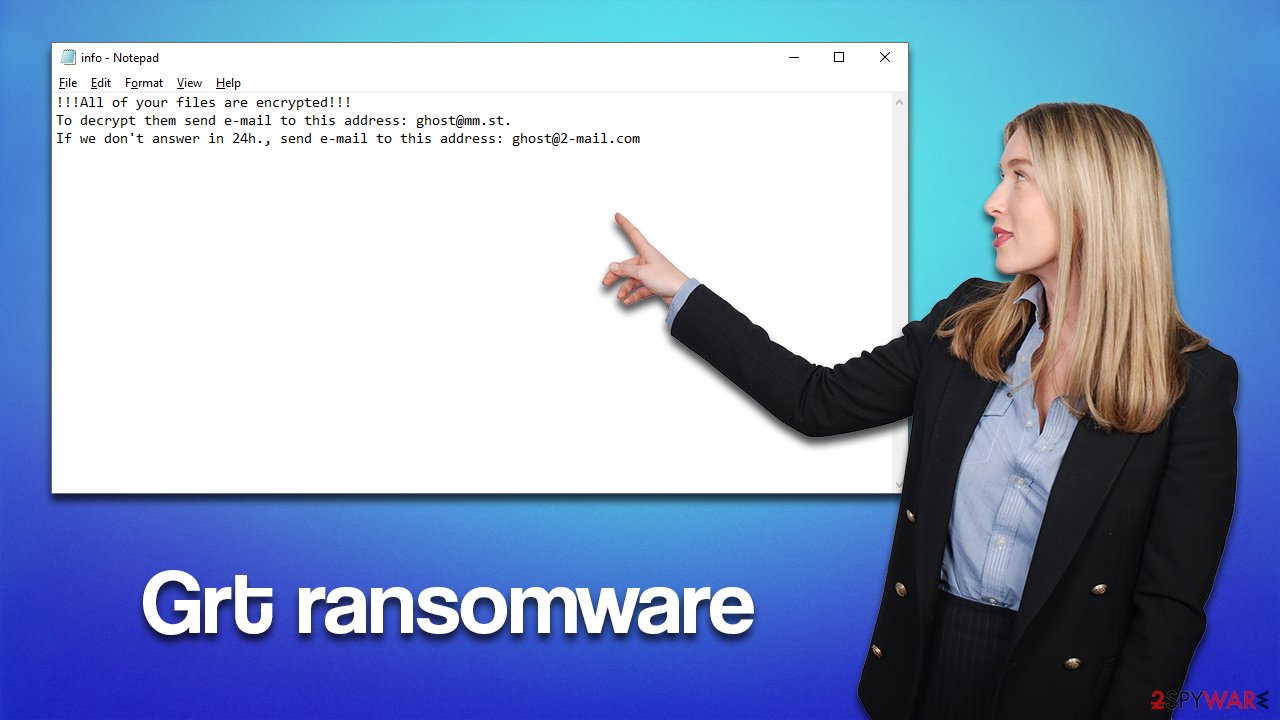
Right after the data is locked, the Grt virus delivers two ransom notes: info.txt, which shows the contact details of the criminals, and a pop-up window titled “encrypted.” The main goal of these files is to provide enough information to users so that the ransom payment is made, which security experts advise not to do.
Instead, we recommend following the comprehensive guide below that will show you how to remove Grt ransomware and attempt to restore files without paying the ransom to cybercriminals. We also provide additional security tips that would help you remediate your computer after a malware attack.
| Name | Grt virus |
|---|---|
| Type | Ransomware, file-locking virus |
| File extension | .[ID].[ghost@mm.st].grt |
| Ransom note | info.hta and info.txt |
| Contact | ghost@mm.st or ghost@2-mail.com |
| Family | Phobos |
| File Recovery | The only secure way to restore files is by using data backups. If such is not available or were encrypted as well, options for recovery are very limited – we provide all possible solutions below |
| Malware removal | Disconnect the computer from the network and internet and then perform a full system scan with SpyHunter 5Combo Cleaner security software |
| System fix | Once installed on the system, malware might seriously damage some system files, resulting in crashes, errors, and other stability issues. You can employ FortectIntego PC repair to fix any of such damage automatically by replacing system corruption |
The message from the malware authors
Grt ransomware is a member of a broad family known as Phobos. It has been around since at least 2017, giving a lot of time for its authors to release hundreds of its variants, including LIZARD, XHAMSTER, GUCCI, and many others.
The malware drops two ransom notes on the system – one enclosed within the TXT file (a brief message), while the HTA pop-up shows up as soon as data encryption is finished. The HTA[2] ransom note provides much more information about the infection and file encryption, as well as shows contact details:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail ghost@mm.st
Write this ID in the title of your message
In case of no answer in 24 hours write us to this e-mail:ghost@2-mail.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the tool that will decrypt all your files.Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 4Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
As we already mentioned, contacting cybercriminals is not recommended, despite what they are saying. The biggest interest of crooks is to make them seem accessible and friendly so that victims would be more likely to pay. However, this is a big mistake to make, as there have been numerous cases where users never received the promised decryptor even after sending money to the attackers.
While it is true that Grt ransomware encryption is secure and that it is extremely difficult to remediate the files without the decryption tool owned by cybercriminals, not everything is lost. A decryptor might be created in the future, or special recovery software might be helpful in some cases. But first, malware should be removed thoroughly.
Removal and .grt file recovery steps
While many ransomware viruses self-destruct after finishing the encryption process, it might not always be the case. Besides, ransomware is commonly spread along with other malicious programs, so it is vital to perform the elimination process correctly. The first step is disconnecting your PC from any networked connection.
Ransomware often establishes a connection with Command & Control[3] – a remote server controlled by attackers. This is where a decryption tool is held, and various commands can be executed using it remotely. Thus, before you proceed with the virus removal and data recovery, make sure you disconnect your computer from the internet and network.
- Type in Control Panel in Windows search and press Enter
- Go to Network and Internet
![Network and internet Network and internet]()
- Click Network and Sharing Center
![Network and internet 2 Network and internet 2]()
- On the left, pick Change adapter settings
![Network and internet 3 Network and internet 3]()
- Right-click on your connection (for example, Ethernet), and select Disable
![Network and internet 4 Network and internet 4]()
- Confirm with Yes.
Once all networking connections are terminated, malware can no longer be controlled remotely, which is a perfect chance to begin Grt ransomware removal. While manual elimination can be possible, it is strongly not recommended for regular computer users – we recommend employing SpyHunter 5Combo Cleaner or Malwarebytes security software for this job.
As soon as malware is eliminated, it is time to attempt file recovery. It is important to note that before you proceed, you have to make backups of the encrypted files you value since any type of data recovery attempt might permanently damage files. Once you have copied them to an external medium or the cloud service, you are good to go.
Many users believe that they can restore the .Grt files as soon as they scan their systems with anti-malware software. Unfortunately, this is impossible, as security software is simply not designed for that. Instead, specialized recovery applications should be used. Keep in mind that recovering files encrypted by ransomware successfully using this method is rather low, although not impossible.
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Grt ransomware Grt ransomware]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Security experts are known to work on decryption tools for major ransomware strains. In some cases, flaws within the encryption process can be found or criminals' servers seized by the lay authority agencies. In any case, you could look for decryptors on the following pages, although keep in mind it might take a while until there's a working one made.
- No More Ransom Project
- Free Ransomware Decryptors by Kaspersky
- Free Ransomware Decryption Tools from Emsisoft
- Avast decryptors
Repair damaged system files
Malware can damage some system files, making users reinstall the operating system and avoid further stability issues. Instead, we strongly recommend you try using a computer repair tool – it is a perfect solution for Windows remediation after a malware attack.
- Download FortectIntego
- Click on the ReimageRepair.exe
![Reimage download Reimage download]()
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
![Reimage installation Reimage installation]()
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Encryption Algorithm. Techopedia. Professional IT insight.
- ^ HTA File Type. File.org. Everything about file extensions.
- ^ Command and Control server (C&C). Kaspersky. Encyclopedia.












