Gujd file virus (Free Instructions) - Virus Decryption
Gujd file virus Removal Guide
What is Gujd file virus?
Gujd ransomware – a cyber threat focused on file encoding and blackmail
Gujd file virus is developed to encrypt all personal data on the infected computer, modify the system files and settings to establish persistence, and demand a ransom when the previous two deeds are accomplished. Since we've been helping people get out of sticky situations for over 20 years, we don't recommend forwarding any money to the criminals behind ransomware attacks. This article will help you remove the infection, repair affected system sectors, and suggest the best data recovery options.
The article's culprit belongs to the Djvu ransomware family, which is responsible for more than half of cyberattacks of such type globally. The main distribution method of file-lockers from this lineage is via file-sharing platforms, especially the most popular torrent websites.
Gujd, Wwka, Zqqw, and payload files of other variations are usually camouflaged as the latest game cracks.[1] But they could also be uploaded as illegal activation tools for any software or practically any other file on these high-risk sites. Refrain from using them if you value your privacy and security.
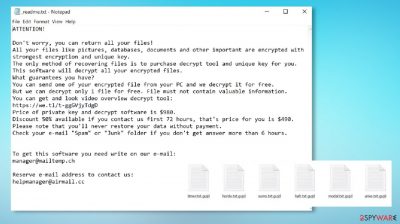
It's pretty easy to determine whether your Windows computer is infected with the article's culprit as all your personal files, including documents, databases, pictures, videos, etc., are appended with the .gujd extension, and you cannot access them. On the desktop and in some affected folders, you'll also find a ransom note, titled _readme.txt, that reads:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-fhnNOAYC8Z
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don't get answer more than 6 hours.To get this software you need write on our e-mail:
manager@mailtemp.chReserve e-mail address to contact us:
helpmanager@airmail.ccYour personal ID:
As you can see, the assailants are trying to scare and convince you into purchasing their decryption software. They offer free decryption of one locked file from the infected machine and provide a link to a video where the supposed software is seen in action. These actions should provide proof that the criminals really have the necessary tool in their possession.
Developers of Gujd ransomware even show their benevolence by offering a 50% discount for victims that reach out to them via the provided emails (manager@mailtemp.ch, helpmanager@airmail.cc) within three days of the attack. That would lower the ransom amount from $980 to $490. But please don't get pushed into making rash decisions.
The criminals might never send the required decryption software, or it might not work. Thus you would lose your money and your data. Besides, by succumbing to the criminals' demands, you would encourage them to spread their dirty business by attacking more innocent people and developing new cyber infections and ways to spread them.
After the virus infects your computer and encrypts non-system files, the only responsible action is to remove it immediately. Since you came to us for help, we'll guide you through this process. In this article, you'll find comprehensive, illustrated instructions that will help with ransomware removal, data recovery, and PC repair. Here's a brief summary of the infection:
| name | Gujd virus |
|---|---|
| Type | Ransomware, file-locker |
| Family | Djvu/STOP ransomware |
| Infection symptoms | Personal data is renamed and inaccessible; a text file with instructions and demands from the criminals appears on the desktop and in affected folders; can't launch anti-malware software; can't reach security-related websites |
| Appended file extension | .gujd |
| Ransom note | _readme.txt |
| Distribution | File-sharing platforms, malicious file attachments from emails, other threats |
| Data recovery | All viable methods are presented either in the article or in the instructions section |
| Virus elimination | To remove this threat once and for all, use recommended security software and manual provided below |
| System health check | Ransomware does all kinds of modifications to the system files and settings. Revert them by using the FortectIntego system diagnostics tool |
The particular version that users already encounter all over the world creates issues with the machine and aims to get money from people. This is the newer version of the DjVu ransomware family and is one of those more advanced and improved variants. Decryption is no possible since the threat relies on online IDs and unique key development.
It is possible to restore some files with the tool designed for media files. However, not all affected pieces get restored with these options. The decryption program previously was helpful, but nowadays these viruses cannot be that easily decoded. You need to rely on proper tools for Gujd virus termination instead.
The best first step is to eliminate the infection itself. It is common for malware like this to spread around with other infections, so anti-malware tools can show you the list of infections active on the system. Those detection names[2] can show various names, but you must remove all infections to get back to a properly working machine.
- Infostealer/Win.SmokeLoader.R431600
- Win32:DropperX-gen [Drp]
- Ransom.Win32.STOP.ko!se60163
- Trojan.MalPack.GS
- Ransom:Win32/STOP.BS!MTB
- BScope.Exploit.ShellCode
- etc.
First focus: Gujd file virus removal and repair damaged system
We're delighted you decided to remove Gujd ransomware instead of increasing the wealth of the criminals responsible for spreading it. Manual removal is not an option as the infection might have spread its components throughout the system, and it would be impossible to find all of them.
Luckily, there's a bunch of tools that can help you with that. Many users are raving about the efficiency and cyber protection level offered by the Malwarebytes security tool. Users with the real-time protection feature of this anti-malware tool are protected against severe malware.[3]
It also stops you from installing any potentially unwanted programs (PUPs) and prevents you from entering (or being redirected to) any high-risk websites with harmful content. All you have to do is update its virus definitions at least a couple of times per week and regularly perform system scans.
It can also be used to remove Gujd file extension virus. The SpyHunter 5Combo Cleaner and the aforementioned security software have exceptional virus detection rates. Nonetheless, the article's culprit will most likely block you from installing these apps or from launching them. Therefore, you'll have to reboot your infected Windows PC in Safe Mode with Networking to complete this process, and that's how that's done:
- Right-click on the Start button and select Settings.
- Scroll down to pick Update & Security.
- On the left side of the window, pick Recovery.
- Now scroll down to find the Advanced Startup section.
- Click Restart now.
![Reboot Reboot]()
- Select Troubleshoot.
- Go to Advanced options.
- Select Startup Settings.
- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.
![Enable safe mode Enable safe mode]()
After accessing this Windows OS mode, copy all (or essential) encrypted files from your infected computer to a USB, SSD, or other removable, offline storage. Then download one of the recommended security tools and install them. Afterward, update the virus definition database of your chosen security app and perform a full system scan.
It should reveal all components of Gujd ransomware and recommend removing it. Please comply with the anti-malware tool's recommendations on which files and entries should be terminated. Please remember to keep this software updated so it could prevent the latest cyber infections from breaking into your device. Then restart your computer in normal Windows mode and download the FortectIntego PC repair software.
That's one more tool crucial to use after Djvu ransomware removal because infections from this lineage cause various system damages by modifying its files and settings. That's why you couldn't open your security tools, and some websites couldn't be reached.
By using this system diagnostics software, you will ensure that the computer doesn't exhibit any abnormal behavior such as freezing, severe lag, BSoDs, program, or system failures. It's offer with a free trial, so you shouldn't hesitate and scan your device with it:
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process
- The analysis of your machine will begin immediately
![Reimage scan Reimage scan]()
- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.
![Reimage results Reimage results]()
By employing the FortectIntego system diagnostics tool, which's also recommended by European cybersecurity specialists,[4] you can rest assured that the overall health of your computer is taken care of. All essential system files and settings are monitored and kept at bay, and all tracking cookies, meant to spy on your browsing activities are properly deleted.
After Gujd file virus is removed and the PC system repaired, it's safe to recover the backups of your files if you kept them. The infection won't renew itself and won't encrypt the recovered data. If you don't have backups, please proceed to the next step, where we provide illustrated instructions of the best options to decrypt your locked data and regain access to it.
Illustrated instructions for encrypted file recovery
This chapter of the article contains comprehensive guides of the two best options to recover .gujd files. We used to suggest Djvu victims use the Shadow Explorer to retrieve old file versions. However, since ransomware evolved, it now deletes Shadow Volume Copies during the infection, disabling this option.
Nonetheless, there are plenty more options. One of them is to use the free decryption software from Emsisoft. This company strives to help victims of this particular strain to get their data back without losing a dime, so the criminals behind it would go bankrupt, and the attacks would stop.
Recover Gujd files by:
- Downloading the app from the official Emsisoft website.
- After pressing the Download button, a small pop-up at the bottom, titled decrypt_STOPDjvu.exe, should appear – click on it.
![Gujd file virus Gujd file virus]()
- If User Account Control (UAC) message shows up, press Yes.
- Agree to License Terms by pressing Yes.
- After Disclaimer shows up, press OK.
- The tool should automatically populate the affected folders, although you can also do it by pressing Add folder at the bottom.
![Gujd file virus Gujd file virus]()
- Press Decrypt.
![Gujd file virus Gujd file virus]()
Please note that there's no guarantee that this free decryptor will unlock your files. If you see the “Decrypted!” message – congratulations, your files are once again accessible. Please, from now on, keep backups and use SpyHunter 5Combo Cleaner or Malwarebytes to protect your computer from millions of infections lurking on the internet.
If no one has yet presented the security company with samples of a normal and encrypted file, the “Error: Unable to decrypt a file with ID:” prompt will appear. From here, you can either do nothing and wait or send the two copies to the company so it could crack the algorithm and produce the necessary software.
When the Emsisoft tool is not able to decrypt your files, you will be presented with the “This ID appears to be an online ID, decryption is impossible” message. Nonetheless, you shouldn't lose hope, as the next tool might help you to restore the files encrypted by the Gujd ransomware.
It's impossible to determine whether this tool will help you with data recovery or not since the article's culprit is a brand new file-locking parasite. Nevertheless, it has helped numerous ransomware victims. You can try it out by following these instructions:
- Download Data Recovery Pro.
- Double-click the installer to launch it.
![Gujd file virus Gujd file virus]()
- Follow on-screen instructions to install the software.
![Install program Install program]()
- As soon as you press Finish, you can use the app.
- Select Everything or pick individual folders where you want the files to be recovered from.
![Select what to recover Select what to recover]()
- Press Next.
- At the bottom, enable Deep scan and pick which Disks you want to be scanned.
![Select Deep scan Select Deep scan]()
- Press Scan and wait till it is complete.
![Scan Scan]()
- You can now pick which folders/files to recover – don't forget you also have the option to search by the file name!
- Press Recover to retrieve your files.
![Recover files Recover files]()
Suppose none of these methods helped to restore .gujd files, you can wait for the plausible decryption software and store some of the files on a separate external drive. You must remove the threat if you want to use the machine and do not rush into file recovery since you can lose your files this way. If you have any questions about any removal, repair, or recovery steps, please feel free to contact us. Our staff will be more than happy to assist you with whatever you need.
Getting rid of Gujd file virus. Follow these steps
Manual removal using Safe Mode
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Gujd file using System Restore
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Gujd file. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Gujd file and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Software cracking. Wikipedia. The free encyclopedia.
- ^ Virus detection rate. VirusTotal. Online malware scanner.
- ^ Darren Allan. What is malware and how dangerous is it?. Techradar. Latest technology news and reviews.
- ^ Viruset. Viruset. Spyware news and security.
































