Gw3w ransomware (Free Instructions) - Removal Guide
Gw3w virus Removal Guide
What is Gw3w ransomware?
Gw3w ransomware – one of B2DR virus versions demanding a ransom after files' encryption
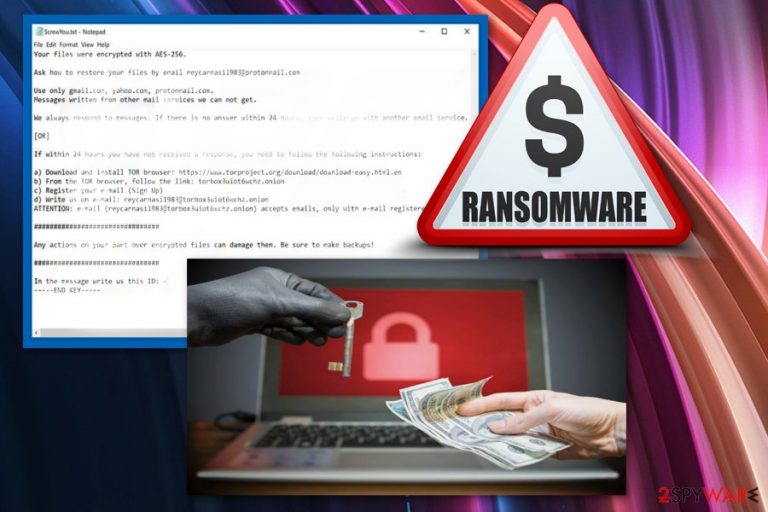
Gw3w is a high-risk ransomware that is designed to infiltrate the system unknowingly. The research has shown that it's one of the versions of B2DR ransomware. This virus uses AES-256 encryption algorithm and appends “.reycarnasi1983@protonmail.com.gw3w” file extension to targeted data. Previous versions add “.ssananunak1987@protonmail.com.b2fr”; “.bronmerkberpa1976@protonmail.com.b2dr”; “.setimichas1971@protonmail.com.b4wq” suffixes. When ransomware locks files, it demands to contact criminals using email or TOR network.
| Name | Gw3w |
|---|---|
| Type | Ransomware |
| Previous versions | B2fr; B2dr; B4wq |
| Extensions |
.reycarnasi1983@protonmail.com.gw3w; |
| reycarnasi1983@protonmail.com | |
| Encryption method | AES-256 |
| Ransom file | ScrewYou.txt |
| Distribution | Insecure spam email attachments |
| Elimination |
Gw3w virus usually gets into Windows computer when a user opens a malicious email attachment. Once malware payload is dropped and executed, it starts making system changes in order to boot on system startup and remain as soon as possible on the device.
Furthermore, Gw3w ransomware begins the most important task – file encryption. It scans the system looking for the targeted data. It locks all files strong AES encryption and makes them useless. After the successful encryption virus places ransom message file “ScrewYou.txt“ on every folder that has encrypted files:
Ask how to restore your files by email reycarnasi1983@protonmail.com
Use only gmail.com, yahoo.com, protonmail.com.
Messages written from other mail services we can not get.We always respond to messages. If there is no answer within 24 hours, then write us with another email service.
As you can see from the extract, creators of Gw3w ask to contact them via email and promise to respond immediately. However, they also give alternative solution for those who are willing to do what they ask but did not receive the answer in one day time:
If within 24 hours you have not received a response, you need to follow the following instructions:
a) Download and install TOR browser: [link removed]
b) From the TOR browser, follow the link: [link removed]
c) Register your e-mail (Sign Up)
d) Write us on e-mail: [link emoved]
ATTENTION: e-mail (reycarnasi1983@torbox3uiot6wchz[.]onion) accepts emails, only with e-mail registered in the TOR browser at torbox3uiot6wchz[.]onion
Virus developers suggest you contact them by the given email address and then you can allegedly receive your decryption key. Interesting the fact that these cybercriminals want you to use specific email services. Although, do not contact developers of Gw3w ransomware virus in any way because they can take your money and ignore you after. This means that you lose your money and can be at risk for other malicious malware.
This virus is not just a scam,[1] it can do severe damage. After the cyber attack, your computer becomes vulnerable, so other cyber threats might easily sneak into the system. This is the biggest reason you should remove Gw3w ransomware ASAP. Additionally, while the virus resides on the system, you cannot safely plug in any external drives because malware can affect them too. Hence, you may lose copies of the important files too.
Cybersecurity specialists from Uirusu.jp[2] recommend you to use proper tools for Gw3w ransomware removal. Anti-malware programs like FortectIntego can be the best solution here because malware like this can contain other tools or applications that change your Windows system Registry key or even more. 
Be careful with received emails – they might be spreading malware
Usually, you can spot potentially dangerous spam emails by their shady or aggressive commercial offers. However, macro viruses,[3] such as ransomware-type cyber threats, can be hidden in safe-looking files, f.e., Microsoft Word documents. This means that when you open an attachment from letters like this, you immediately get malware on the system. It is essential to be cautious while browsing through your emails.
Even so, you should delete all of those suspicious emails without opening and clean your email boxes occasionally. That clickable content, deals, offers are mostly there to grab your attention and trick into installing malicious content on your machine. We want to remind about the importance to double-check the information before opening any file added to the email.
Get rid of Gw3w ransomware and try to recover your files
You should use anti-malware tools if you want to remove Gw3w ransomware correctly. This fact is important because professional tools can eliminate every little ransomware addition and piece of malware that may have been brought to your PC. Trusting programs like FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes can be vital here.
We highly recommend focusing on Gw3w ransomware removal instead of immediately looking for the ways to decrypt or restore data. However, decryption tools are not available. The only possibility to restore your files is to use backups. Do not plug in any drive to a computer that has not been cleaned yet. You should back all of your data occasionally because if you do not, file recovery can get very difficult. We have a couple of alternative methods that might help down below.
Getting rid of Gw3w virus. Follow these steps
Manual removal using Safe Mode
First step you can do when dealing with ransomware is rebooting your PC in Safe Mode with Networking
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Gw3w using System Restore
You can also try System Restore feature
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Gw3w. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Gw3w from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by Gw3w, you can use several methods to restore them:
Data Recovery Pro is a tool created for file restoring
If you accidentally deleted your files or they are encrypted you need to try to restore them using Data Recovery Pro
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Gw3w ransomware;
- Restore them.
Windows Previous Versions feature is a good choice for individual file recovery
If System Restore feature was enabled prior Gw3w ransomware attack you can recover your individual files using Windows Previous Versions feature
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Restore your files using ShadowExplorer
If this ransomware that got your files encrypted did not delete Shadow Volume copies you can recover your files using ShadowExplorer
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Gw3w decryptor is not released yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Gw3w and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ What is scam?. Business dictionary. Business education.
- ^ Uirusu. Uirusu. Spyware news.
- ^ Macro virus. Wikipedia. The free encyclopedia.







