Have you heard about Pegasus email scam (fake) - Free Instructions
Have you heard about Pegasus email scam Removal Guide
What is Have you heard about Pegasus email scam?
“Have you heard about Pegasus” is an email scam that attempts to manipulate you into paying ransom
“Have you heard about Pegasus” email is a typical example of a sextortion scam, designed to incite fear and prompt hasty payments from victims. The scam email falsely claims that the recipient’s mobile device has been infected with the high-profile Pegasus malware, allowing the scammer to record private videos and threaten their release unless a ransom is paid. This scam cleverly utilizes the name of a real piece of spyware, which was originally developed for crime prevention and national security purposes, to lend credibility to the threats made in the email.
| Name | “Have you heard about Pegasus” |
| Type | Email scam, fraud, fake email, sextortion |
| Distribution | Malspam – the attackers send thousands of emails in bulk to extort money from unsuspecting users |
| Operation | The scam operates by falsely claiming that the recipient's device has been infected with the Pegasus malware, using threats of releasing private videos to extort payment |
| Ransom size | $1,600 to be sent in Bitcoin to the provided crypto wallet |
| Dangers | Financial losses, malware infections |
| Removal | Make sure you scan your system with security software SpyHunter 5Combo Cleaner to ensure no malicious software is present |
| Other tips |
Why did you receive the Pegasus email scam?
It's rare that a “Have you heard about pegasus?” email appears in your inbox as a consequence of deliberate action taken against you. Instead, mass email campaigns are usually the result of fraudsters sending the same intimidating message to a large number of email addresses in the hopes that a small percentage of recipients would be intimidated into paying.
Scammers often obtain these email addresses through various means such as breaches of databases, purchasing lists on the dark web, or using software tools that scrape the web for contact information.
Email filters that usually catch and quarantine such scam attempts can sometimes be bypassed. Scammers are continually refining their techniques to evade detection by using less predictable email formats and engaging subject lines that provoke curiosity or urgency. This method increases the chances that their message will land in your primary inbox rather than in spam folders. Here are some examples of previous naming patterns:
- I regret to inform you about some sad news for you
- It’s unpleasant to start the conversation with bad news
- Your device was compromised
Moreover, the scam leverages a known technique of social engineering by invoking the name of a sophisticated malware known to the public, thus exploiting a general lack of detailed technical knowledge among the public.
This scare tactic is designed to create a high-pressure situation where the recipient feels a compromised sense of privacy and a strong urge to resolve the issue quickly by complying with the scammer's demands.
How the scam operates and how crooks attempt to manipulate victims
The email begins with a cold opening that immediately seeks to engage and unsettle the recipient with mentions of the Pegasus malware, claiming the recipient’s phone has been compromised with a “zero-click” attack. This type of attack refers to the capability of some malware to install itself without user interaction, an assertion that adds a layer of authenticity and immediate threat to the message.
Following the introduction, the scammer intensifies the threat by claiming to have used Pegasus’s capabilities to access and record personal moments, asserting possession of embarrassing or damaging footage. The threat escalates with a demand for payment in Bitcoin, setting a strict deadline and warning against seeking help or notifying authorities, which they claim will result in further violation of privacy.
This email uses specific psychological triggers:
- fear
- urgency
- invasion of privacy.
By convincing victims that their most private moments are in someone else's hands, scammers manipulate emotions to override rational decision-making. The mention of real malware like Pegasus adds believability to the claim, leveraging half-truths to enhance the illusion that the threat is genuine.
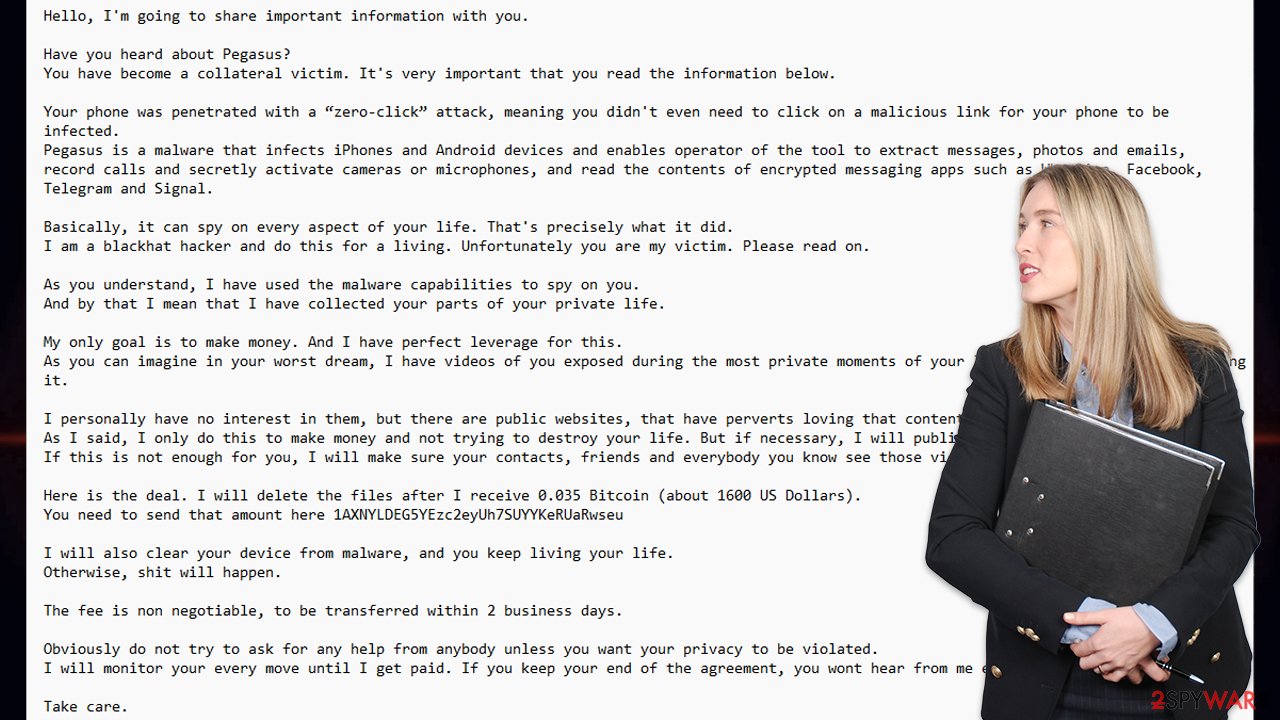
Here's the full message you might get (although keep in mind that this may vary slightly):
Hello, I'm going to share important information with you.
Have you heard about Pegasus?
You have become a collateral victim. It's very important that you read the information below.Your phone was penetrated with a “zero-click” attack, meaning you didn't even need to click on a malicious link for your phone to be infected.
Pegasus is a malware that infects iPhones and Android devices and enables operator of the tool to extract messages, photos and emails,
record calls and secretly activate cameras or microphones, and read the contents of encrypted messaging apps such as WhatsApp, Facebook, Telegram and Signal.Basically, it can spy on every aspect of your life. That's precisely what it did.
I am a blackhat hacker and do this for a living. Unfortunately you are my victim. Please read on.As you understand, I have used the malware capabilities to spy on you.
And by that I mean that I have collected your parts of your private life.My only goal is to make money. And I have perfect leverage for this.
As you can imagine in your worst dream, I have videos of you exposed during the most private moments of your life, when you are not expecting it.I personally have no interest in them, but there are public websites, that have perverts loving that content.
As I said, I only do this to make money and not trying to destroy your life. But if necessary, I will publish the videos.
If this is not enough for you, I will make sure your contacts, friends and everybody you know see those videos as well.Here is the deal. I will delete the files after I receive 0.035 Bitcoin (about 1600 US Dollars).
You need to send that amount here 1AXNYLDEG5YEzc2eyUh7SUYYKeRUaRwseuI will also clear your device from malware, and you keep living your life.
Otherwise, shit will happen.The fee is non negotiable, to be transferred within 2 business days.
Obviously do not try to ask for any help from anybody unless you want your privacy to be violated.
I will monitor your every move until I get paid. If you keep your end of the agreement, you wont hear from me ever again.
Take care.
What (not) to do after receiving the “Have you heard about Pegasus” email
If you receive an email like this, the first step is to remain calm. Do not respond to the email or make any payments. Responding or paying the ransom only confirms to the scammers that they have reached a valid and responsive email address or even a potential repeat target.
Instead, report the email to your local authorities or a cybercrime agency in your country to help them track and possibly act against such threats. Provide as much information as possible, as it will help the investigation.
To ensure your devices are secured, you should scan them with updated security software – like Malwarebytes or SpyHunter 5Combo Cleaner – to ensure that there is malware on your device (it is unlikely to be true but you should better be safe than sorry).
Should you have made a payment, it’s important to contact your bank immediately to report the fraud and discuss any possible actions to retrieve the funds. As a preventative measure, you should change your passwords (especially for the email account and if you have reused passwords before) and enable multi-factor authentication where possible.
How to prevent from getting malware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
