“Your device was compromised” email scam (Free Instructions)
“Your device was compromised” email scam Removal Guide
What is “Your device was compromised” email scam?
“Your device was compromised” email – a scam demanding $1650 to be sent in Bitcoins
“Your device was compromised” email is sent out in tens of thousands. If you've received it, please don't believe a word in it. The scammers are trying to trick you into believing that your device has malware installed on it and that they've gathered various information about you. It is categorized as an extortion scam.
Within the email, they state that they've been watching you through your webcam and eavesdropping on your conversations via the microphone for months. That's not true. If you haven't downloaded any questionable email attachments, didn't click on suspicious links or deceptive ads, there's nothing wrong with your device. There's no malware on it.
The “Your device was compromised” scam is trying to scare gullible people into forwarding $1650 to the criminals for imaginary collected data and non-existent malware removal from their devices. If the scam email contains any of the passwords that you use, the scammers might have gotten it from various hacked sites. In that case, all you need to do is change the passwords immediately for all your accounts, including the email clients to which you've received the scam.
| name | “Your device was compromised” |
|---|---|
| Type | Scam, sextortion, fake webcam blackmail[1] |
| Fake Claims | Videos, images, and audio recordings will be sent out to all contacts if the ransom isn't paid |
| Ransom amount | $1650 |
| Preferred payment method | Bitcoins |
| Precautionary measures | Change passwords on all accounts. Protect your devices from various malware by using a reliable anti-malware tool |
| System repair | Delete tracking cookies and repair system-related irregularities by performing system diagnostics with the time-proven FortectIntego software |
There are tons of similar extortion scams roaming around the internet. Under no circumstances should you contact the cyber thieves or, even worse, send them the demanded amount. If you do, they would be encouraged to send out scam emails to more people.
Remove “Your device was compromised” scam email as its distributors don't have any information on you, no videos, audio recordings, or images. And they definitely didn't infect your device with any malware. The only thing that they might have manages to come up with is a password for an internet service that you might use.
Cybercriminals are constantly breaching various websites and stealing login credentials. They either use the information themselves for various scams/attacks or sell the stolen information to third parties. You can check if your email or phone ended up in the wrong hands on Haveibeenpwned.
If your device exhibits any strange behavior such as crashing, freezing, BSoDs, or other system failures, you have to check it for malware and PUP infections. If a reliable tool such as the Malwarebytes doesn't find anything, keep it to protect your device from various cyber infections lurking on the internet for insufficiently protected devices.
Nowadays, threat actors are getting more and more elaborate on how they can spread their vile creations. They can hack popular websites and place malware directly in their scripts. When you open such a website, malware would be automatically installed through the drive-by downloading[2] technique.
Also, please refrain from clicking any ads on high-risk websites and don't use file-sharing platforms as they're a hotbed for various cyber infections. For example, Djvu family ransomware, considered to be the most prevalent one globally, is spread specifically through torrent websites.
But refraining from visiting high-risk sites, not opening suspicious email attachments, and taking other precautionary measures while browsing the net might not be enough. Therefore, get yourself a trustworthy anti-malware solution such as the SpyHunter 5Combo Cleaner and use it at least twice a week to scan your device for infections.
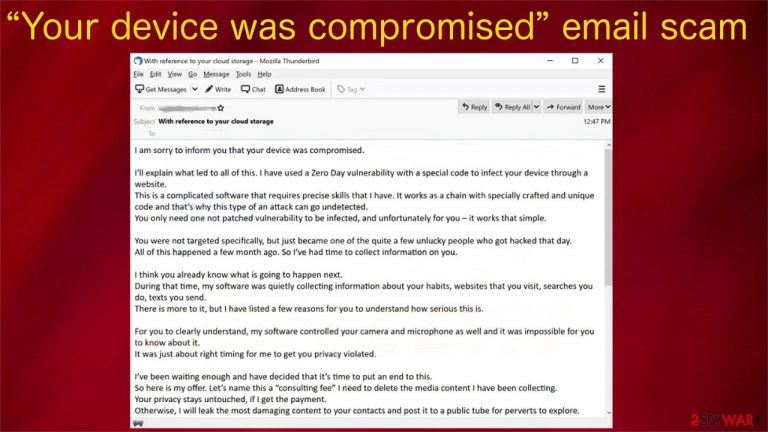
The message within “Your device was compromised” scam email states:
Subject: With reference to your cloud storage
I am sorry to inform you that your device was compromised.
I’ll explain what led to all of this. I have used a Zero Day vulnerability with a special code to infect your device through a website.
This is a complicated software that requires precise skills that I have. It works as a chain with specially crafted and unique code and that’s why this type of an attack can go undetected.
You only need one not patched vulnerability to be infected, and unfortunately for you – it works that simple.You were not targeted specifically, but just became one of the quite a few unlucky people who got hacked that day.
All of this happened a few month ago. So I’ve had time to collect information on you.I think you already know what is going to happen next.
During that time, my software was quietly collecting c
There is more to it, but I have listed a few reasons for you to understand how serious this is.For you to clearly understand, my software controlled your camera and microphone as well and it was impossible for you to know about it.
It was just about right timing for me to get you privacy violated.I’ve been waiting enough and have decided that it’s time to put an end to this.
So here is my offer. Let’s name this a “consulting fee” I need to delete the media content I have been collecting.
Your privacy stays untouched, if I get the payment.
Otherwise, I will leak the most damaging content to your contacts and post it to a public tube for perverts to explore.I understand how damaging this will be for you, and amount is not that big for you to keep your privacy.
Please dont blame me – we all have different ways of making a living.I have no intention of destroying your reputation or life, but only if I get paid.
I don’t care about you personally, that’s why you can be sure that all files I have and software on your device will be deleted immediately after I receive the transfer.
I only care about getting paid.My modest consulting fee is 1650 US Dollars transferred in Bitcoin. Exchange rate at the time of the transfer.
You need to send that amount to this wallet:The fee is non negotiable, to be transferred within 2 business days.
We use Bitcoin to protect my identity.Obviously do not try to ask for any help from anybody unless you want your privacy to violated.
I will monitor your every move until I get paid. If you keep your end of the agreement, you wont hear from me ever again.Take care.
Avoid data tracking and system issues by using proper repair tools
If you tend to visit high-risk portals, like porn, gambling, file-sharing platforms, and alike, they might be tracking and recording your browsing activities. That's done by placing tracking cookies or beacons on your device in use. The gathered information is usually used to create irresistible ads specifically for you.
Sometimes, this information can be shared with third parties whose intentions might be different from just displaying ads. The collected details are considered non-identifiable as they don't contain names, emails, addresses, etc., only geolocations, visited sites, clicked links, search inquiries, etc.
Still, if these details fell into the wrong hands, you might get yourself in trouble. That's why it's important to clean up your device at least once a week, but cybersecurity experts[3] recommend doing that on a daily basis. If you have numerous browsers, that can take a lot of time.
Therefore, we recommend downloading the time-tested FortectIntego system diagnostics tool that will do the dirty work for you. Moreover, it will automatically detect all system irregularities, whether altered registry values/keys, damaged DLLs, or corrupted system files, and suggest fixing them. It has a free trial, so you have nothing to lose:
- Download the application by clicking on the link above
- Click on the ReimageRepair.exe
- If User Account Control (UAC) shows up, select Yes
- Press Install and wait till the program finishes the installation process

- The analysis of your machine will begin immediately

- Once complete, check the results – they will be listed in the Summary
- You can now click on each of the issues and fix them manually
- If you see many problems that you find difficult to fix, we recommend you purchase the license and fix them automatically.

Please remember that various scams are trying to blackmail you into forwarding money in Bitcoins and other cryptocurrencies. All of them create a sense of urgency and try to push you into making rash decisions. When you receive “Your device was compromised” email or similar scam letters, please check with us for solutions.
How to prevent from getting spam tools
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
- ^ Webcam blackmail. Wikipedia. The free encyclopedia.
- ^ Jareth. Drive-by downloads: Can you get malware just from visiting a website?. Emsisoft. Security blog.
- ^ Novirus. Novirus. Spyware news and security.
