“It’s Unpleasant To Start The Conversation With Bad News” email scam (Free Instructions) - scam
“It’s Unpleasant To Start The Conversation With Bad News” email scam Removal Guide
What is “It’s Unpleasant To Start The Conversation With Bad News” email scam?
“It's Unpleasant To Start The Conversation With Bad News” is an email scam that attempts to extort bitcoin from innocent users

“It's Unpleasant To Start The Conversation With Bad News” is a typical extortion scam that spreads via email. Crooks behind it claim that they have hacked users' computers and now have full access to various personal information, including browsing history and even camera access. It goes without saying that email is a mere bluff, and the main goal of cybercriminals is to make people transfer digital currency to them.
“It's Unpleasant To Start The Conversation With Bad News” belongs to the category of scams known as sextortion.[1] The main goal is to shame victims and make them believe that a recording of them was made whenever they visited an adult-oriented website. Allegedly, if they refuse to pay, a copy of a video would be sent out to all their contacts for everyone to see.
This is not the first and not the last email scam that attempts to run this scheme – “Unfortunately, there are some bad news for you,” or “Your device was compromised” are just a few examples we have previously covered. If you have received an email of this kind, please do not panic and check out the information below that should help you deal with this.
| Name | “It's Unpleasant To Start The Conversation With Bad News” |
| Type | Phishing, scam, fraud, fake email, sextortion |
| Distribution | Malspam – the attackers send thousands of emails in bulk to extort as much money as possible |
| Operation | Cybercriminals claim that they hacked the system and that access to personal information was acquired. They say that a video of victims visiting porn sites was recorded, and if they don't want it to be disclosed publically, they should transfer bitcoin to a provided crypto wallet controlled by cybercriminals |
| Ransom size | $1,370, to be sent in bitcoin to the provided crypto wallet |
| Dangers | Financial losses, virus infections |
| Removal | As a precautionary measure, scan your device with anti-malware software |
| Other tips |
How it all works, and why shouldn't you respond/pay
Sextortion scams have a long history – they have been around even before the internet was commonly used. The main goal of criminals is to acquire victims' compromised material, which would allow blackmailing them by claiming that it would be exposed to their loved ones or colleagues/friends.
We have previously seen plenty of attempts to monetize users' anxiety about such things. Each of such emails is written in various ways, although the main principle remains the same, which is to make people believe that a video of them visiting -rated websites has been recorded and that they need to pay a particular sum of money in bitcoin to avoid being exposed.
These scam emails are usually quite lengthy and include a lot of information about the allegedly installed virus and how it all works. Here's an example of the “It's Unpleasant To Start The Conversation With Bad News” email scam message:
Subject: Don't forget to pay the tax within 2 days!
Hi. How are you?
I know, it's unpleasant to start the conversation with bad news, but I have no choice.
Few months ago, I have gained access to your devices that used by you for internet browsing.
Afterwards, I could track down all your internet activities.Here is the history of how it could become possible:
At first, I purchased from hackers the access to multiple email accounts (nowadays, it is a really simple thing to do online).
As result, I could easily log in to your email account (-).One week later, I installed Trojan virus in Operating Systems of all devices of yours, which you use to open email.
Frankly speaking, it was rather straightforward (since you were opening the links from your inbox emails).
Everything ingenious is quite simple. (o_0)!My software enables me with access to all controllers inside devices of yours, like microphone, keyboard and video camera.
I could easily download to my servers all your private info, including the history of web browsing and photos.
I can effortlessly gain access to all your messengers, social networks accounts, emails, contact list as well as chat history.
Virus of mine constantly keeps refreshing its signatures (because it is driver-based), and as result remains unnoticed by your antivirus.Hence, you can already guess why I stayed undetected all this while.
As I was gathering information about you, I couldn't help but notice that you are also a true fan of adult-content websites.
You actually love visiting porn sites and browsing through kinky videos, while pleasuring yourself.
I could make a few dirty records with you in the main focus and montaged several videos showing the way you reach orgasm while masturbating with joy.If you are still uncertain regarding the seriousness of my intentions,
it only requires several mouse clicks for me to forward your videos to all your relatives, as well as friends and colleagues.
I can also make those vids become accessible by public.
I honestly think that you do not really want that to happen, considering the peculiarity of videos you like to watch,
(you obviously know what I mean) all that kinky content can become a reason of serious troubles for you.However, we can still resolve this situation in the following manner:
Everything you are required to do is a single transfer of $1370 USD to my account (or amount equivalent to bitcoin depending on exchange rate at the moment of transfer),
and once the transaction is complete, I will straight away remove all the dirty content exposing you.
After that, you can even forget that you have come across me. Moreover, I swear that all the harmful software will be removed from all devices of yours as well.
Make no doubt that I will fulfill my part.This is really a great deal that comes at a reasonable price, given that I have used quite a lot of energy to check your profile as well as traffic over an extended period of time.
If you have no idea about bitcoin purchase process – it can be straightforwardly done by getting all the necessary information online.Here is my bitcoin wallet provided below: 1NYCdN9eBXhT4tPSpu4EhpjC9gHXLzipLL, 1N5J73F3gYPgZ8zkbnUhoryrYjQcqsA7St, 1JfnsTBvRQYNvzxYFTQBtEUgojmPy2vd6F, 19Ya5oeV6zqsHa9TSyurpeF1LpYJqm84Yv, 17BSLhc597GybEuZ4DyFpdtceY3Moi3nWo, 1CDLcxiYqWBhDsxriEP92aFTLe9gyyRS4L
You should complete the abovementioned transfer within 48 hours (2 days) after opening this email.
The following list contains actions you should avoid attempting:
#Do not try replying my email (email in your inbox was generated by me alongside with return email address).
#Do not try calling police as well as other security forces. In addition, abstain from sharing this story with your friends.
After I find out (be sure, I can easily do that, given that I keep complete control of all your devices) – your kinky video will end up being available to public right away.
#Do not try searching for me – there is absolutely no reason to do that. Moreover, all transactions in cryptocurrency are always anonymous.
#Do not try reinstalling the OS on your devices or throwing them away. It is pointless as well, since all your videos have already been uploaded to remote servers.The following list contains things you should not be worried about:
#That your money won't reach my account.
– Rest assured, the transactions can be tracked, hence once the transaction is complete,
I will know about it, because I continuously observe all your activities (my trojan virus allows me to control remotely your devices, same as TeamViewer).
#That I still will share your kinky videos to public after you complete money transfer.
– Trust me, it's pointless for me to continue troubling your life. If I really wanted, I would make it happen already!Let's make this deal in a fair manner!
Owh, one more thing…in future it is best that you don't involve yourself in similar situations any longer!
One last advice from me – recurrently change all your passwords from all accounts.
When dissecting this message, it becomes evident that there are a lot of things crooks are talking about that could actually happen under certain circumstances. For example, some malware can indeed run in a similar manner as a driver – on a kernel level, which prevents antivirus from detecting it in most cases – this type of malware is known as a rootkit.[2] However, there are plenty of security tools that are particularly designed to scan for rootkits and remove them effectively.
The description of the monitoring aspect is also correct, as certain malicious programs are designed to harvest various user data or even steal personal files or emails. The main difference here is that all these claims are mere bluff and the “It's Unpleasant To Start The Conversation With Bad News” scam authors only try to frighten users and make them pay.
A lot of information is being fed to users in order to make them believe that they are dealing with a real hacker that has compromised their system. In some cases, people are even shown their (usually outdated) password of some account as “proof” that the hack is real. In reality, these passwords are acquired by scammers on the underground forums for a few dollars, and they don't really know the password.
Therefore, whenever you receive an email or see a similar message on a random website, never interact with it, and don't be frightened – in most cases, all the claims are completely fake, and crooks do not have any compromising material of yours. Simply ignore the message entirely and report it to your local authorities dealing with cybercrime:
- USA – Internet Crime Complaint Center IC3
- United Kingdom – ActionFraud
- Canada – Canadian Anti-Fraud Centre
- Australia – ScamWatch
- New Zealand – ConsumerProtection
- Germany – Polizei
- France – Ministère de l'Intérieur

If your country is not listed above, you should contact the local police department or communications center.
Make sure you clean your browsers and scan your system
As we have already said many times, the crooks behind the “It's Unpleasant To Start The Conversation With Bad News” email are simply bluffing, and they are unlikely to have any videos of you. However, it is vital to make sure that the system is checked thoroughly as a precautionary measure, as malware could be involved in some cases (for example, your email could have been leaked due to malware infection in the first place).
The very first thing you should do is scan your system with powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. This would ensure that all the malware and its malicious components, if present, are found and removed effectively. Don't forget to clean your web browser as well, as crooks may hijack cookies[3] in some cases, which could result in personal account compromise and other privacy issues. Likewise, removing cookies would stop any type of third-party tracking.
You can quickly and easily delete cookies and repair any malware damage with FortectIntego repair software. If you would rather perform this step yourself, you have to access your browser settings as follows:
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

Safari
- Click Safari > Clear History…
- From the drop-down menu under Clear, pick all history.
- Confirm with Clear History.

Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
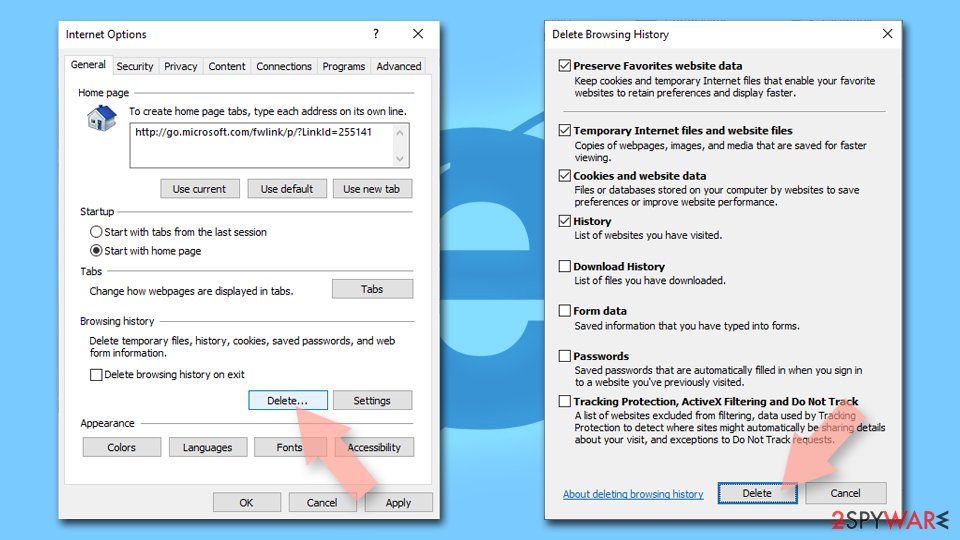
- Select relevant fields and press Delete.
How to prevent from getting spam tools
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Sextortion emails: how to protect yourself. NCSC. National Cyber Security Centre.
- ^ Rootkit malware. CrowdStrike. Data breach prevention and security.
- ^ Session hijacking. Wikipedia. The free encyclopedia.
