Hydra ransomware (Virus Removal Guide) - Improved Instructions
Hydra virus Removal Guide
What is Hydra ransomware?
Hydra ransomware – malware that comes camouflaged as Mozilla Firefox
Hydra ransomware is a cyber infection that threatens victims to delete their files if they do not meet the ransom demands. The malware attack starts with a secret infiltration process through an infected email spam attachment or a cracked piece of software that the user has downloaded from a torrenting network. Afterward, Hydra virus runs the encryption module by using a cipher such as AES or RSA[1] and targets all the data that is saved on the computer system.
Files that have been normally operating cannot be accessed properly anymore and end up with the .HYDRA appendix. Coming from the Jigsaw ransomware family, this malware displays a pop-up window that carries the ransom demands. The authors of the message say that they are interested in playing a game that includes deleting a few files the first day, a hundred the second day, and a few thousand the third day if the ransom demands are still not met.
Hydra ransomware is kind of delicate and requires only $10 of payment that is asked to be transferred via PayPal and by contacting crooks through JIGSAW3363@gmail.com email address. The level of inexperience of the hackers is accurate as they urge for a payment in dollars that can easily get tracked.
| Name | Hydra ransomware |
|---|---|
| Type | Ransomware virus/malware |
| Appendix | After the encryption with a cipher such as RSA or AES, the ransomware virus applies the .Hydra extension to each filename |
| Ransom demands | The ransomware virus displays a pop-up window that is the ransom note and includes the criminals' email address JIGSAW3363@gmail.com and ransom demands that are $10 via PayPal for file recovery |
| Family | This malware resides from the Jigsaw ransomware family |
| Danger level | Regarding its complex operating principle and the encryption activity it performs, the ransomware virus holds the danger level of high. Nevertheless, it can relate to the installation of other malicious strings such as trojans |
| Distribution | Most of the time ransomware infections are distributed with the help of email spam messages and their malicious attachments. Also, this particular malware gets on users' computer systems by installing as a software crack on torrenting websites |
| Elimination | You should take the removal process of the ransomware virus seriously. Employ trustworthy antimalware software and do not risk deleting the cyber threat on your own |
| Recovery | If you are looking for ways to recover your encrypted data, you should try using alternative tools that are added to the end of this article rather than meeting the ransom demands |
| Fix tip | If you have discovered any damage on your Windows computer system, try fixing it with a specific repair tool such as FortectIntego |
Hydra ransomware attack starts with the modification of entries in the Windows Registry and by adding malicious processes to the Windows Task Manager section. The malware brings an executable to the system that allows to boot up its module every time when the computer is turned on. Some other features might allow the ransomware virus to scan the computer for encryptable files once in a while or even disable antivirus protection to avoid getting detected.
One of the most interest facts regarding Hydra ransomware is that it ends up on the computer as Mozilla Firefox, so you can mix it with your web browser and not know anything suspicious at first. However, when files are encrypted and the .HYDRA appendix is added, you will notice that something is wrong when you cannot properly load your files. Besides, you will also receive this ransom note in a pop-up window slightly after your data is locked with the cipher:
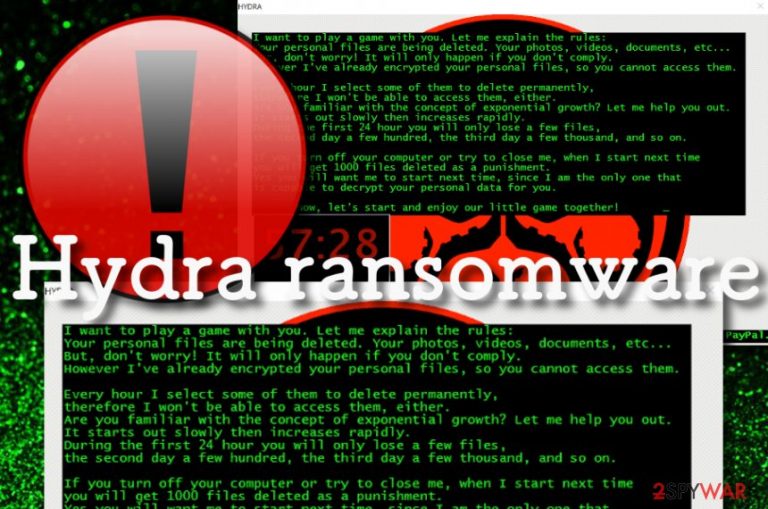
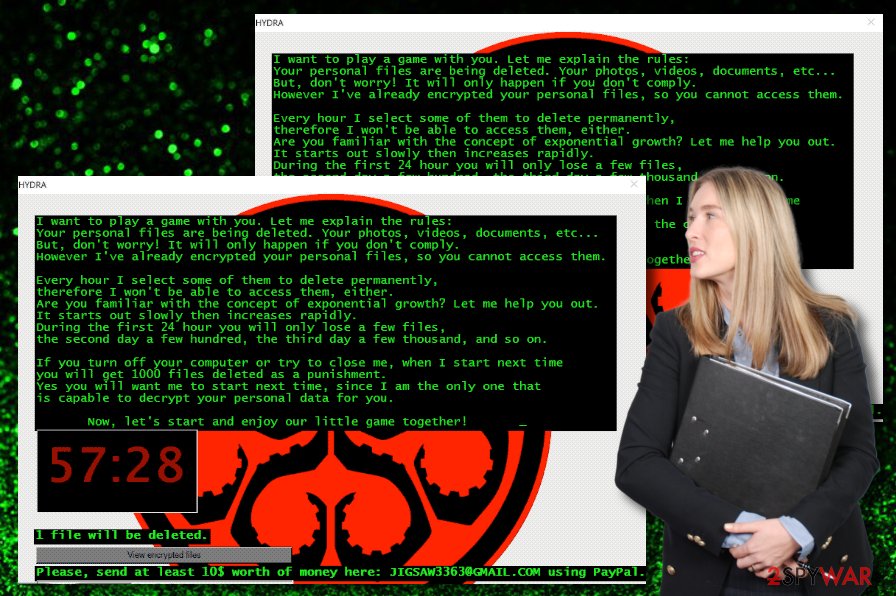
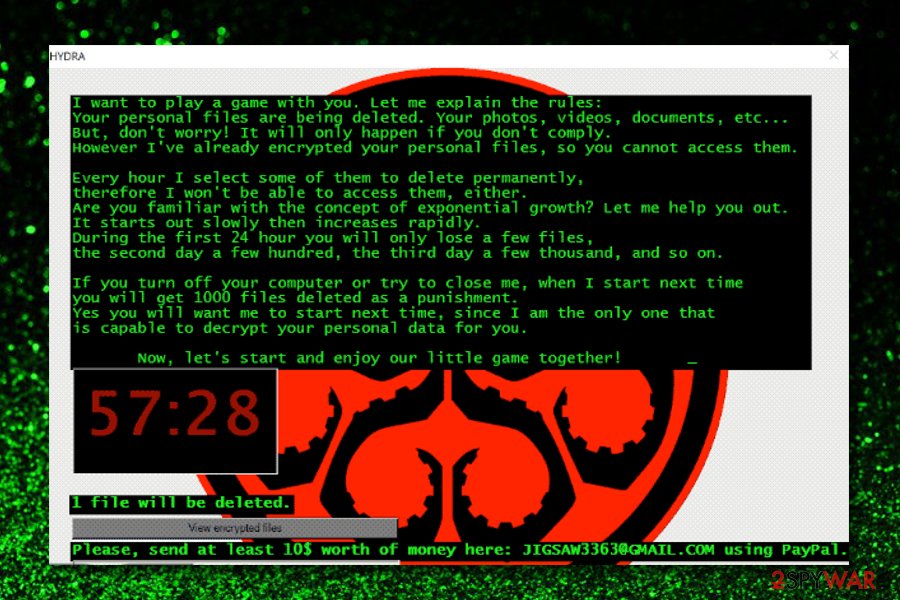
I want to play a game with you. Let me explain the rules:
Your personal files are being deleted. Your photos, videos, documents, etc…
But, don't worry! It will only happen if you don't comply.
However I've already encrypted your personal files, so you cannot access them.Every hour I select some of them to delete permanently,
therefore I won't be able to access them, either.
Are you familiar with the concept of exponential growth? Let me help you out.
It starts out slowly then increases rapidly.
During the first 24 hour you will only lose a few files,
the second day a few hundred, the third day a few thousand, and so on.If you turn off your computer or try to close me, when I start next time
you will get 1000 files deleted as a punishment.
Yes you will want me to start next time, since I am the only one that
is capable to decrypt your personal data for you.Now, let's start and enjoy our little game together!
Bitcoin address: 1Hd3tU8MDmuVotMgGJTJ7svzvPey6bfUgm
Please, send at least 10$ worth of money here: JIGSAW3363@GMAIL.COM using PayPal.
Most of the time malicious actors urge for some type of digital currency payment such as Bitcoin, Ethereum, or Monero. However, Hydra ransomware developers do not seem to bother and go straight for a simple PayPal transfer. However, by asking for $10 as the ransom demand, these people risk exposing themselves for such as small price when cryptocurrency transfers ensure the anonymity of both sides and the criminals stay untrackable.
You should not agree to play the game with these criminals and not get scared because of their promised punishment to eliminate 1000 files if you turn off the computer. Also, you should avoid paying the demanded ransom price even though it is not a big amount. If you transfer the money, you will let the crooks win. Better show these people that you are not scared of them, you can defeat Hydra ransomware and you will search for alternative data recovery solutions.
Hydra ransomware might try to harden the file restoring process for you by eliminating the Shadow Volume Copies that are sometimes necessary for third-party data recovery software. Furthermore, the malicious infection might be programmed to damage the Windows hosts files to prevent you from accessing security-related websites. Do not forget to delete these files while dealing with the ransomware, otherwise, the access will still remain blocked.
When you see the first signs of infection that include encrypted files and the ransom note, you should hurry up and complete Hydra ransomware removal as this malware might also be programmed to bring other virtual parasites such as trojans to the Windows computer system. If the file-encrypting threat has been blocking your antivirus, you can try diminishing these malicious changes with the help of Safe Mode with Networking.
You should rely on trustworthy and expert-tested antimalware tools that will properly remove Hydra ransomware for you. If you try to complete the elimination by yourself and leave any malicious content lurking on your computer system, the ransomware might return within the next time you start your computer. Also, if you have discovered any damage related to this cyber threat, you can try repairing the corrupted areas by employing software such as FortectIntego.
Email spam and software cracks are the best malware distributors
Criminals who develop malware such as ransomware[2] want to make sure that the infection reaches its target. For this purpose, they think of various distribution methods that might succeed. Cybersecurity specialists from NoVirus.uk[3] have discovered that ransomware viruses are often spread via email spam.
The malicious payload comes included as an attachment to the message and reaches random people some of whom fall for believing in the received email as hackers pretend to be from reliable-looking companies such as FedEx or DHL and deliver some types of “important notices” that need to be opened immediately.
If you have received an email that you are not sure about, do not hurry to believe in it. First, check if the message is coming from an official address, then, check the entire content for possible grammar mistakes. Lastly, if you have already opted for the downloading process of the attachment, do not open the file without scanning it with reputable antimalware.
Furthermore, malicious payload is also distributed through torrenting networks such as eMule, BitTorrent, and The Pirate Bay. Crooks place the infectious content instead of a game crack,[4] key generator, or as a fake setup and wait for some people to download it. Regarding this fact, get your software from well-known developers only.
The entire elimination process of Hydra ransomware and its malicious payload
Hydra ransomware might have scattered malicious content all over the Windows computer system that needs to be eliminated if you want to get rid of the malware properly. This includes cleaning infecting directories such as the Windows Task Manager, Registry, Control Panel, Desktop, and others.
Also, do not think about performing Hydra ransomware removal with the help of manual technique as this is not a possibility for such a case. The malware is a complex threat to deal with and you have to make sure that it is taken care of properly. Regarding this fact, you should employ only reliable antimalware software.
If you are having a hard time to remove Hydra ransomware from your device, boot it in Safe Mode with Networking and then try again. When the malware is completely gone, you should try searching for damaged areas with the help of SpyHunter 5Combo Cleaner and Malwarebytes. If this software finds anything corrupted, try fixing the altered products with FortectIntego.
Getting rid of Hydra virus. Follow these steps
Manual removal using Safe Mode
For diminishing malicious processes on the infected Windows computer system and deactivating the malicious cyber threat itself, you have to try to reboot your Windows computer in Safe Mode with Networking as shown in the below-provided guidelines
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove Hydra using System Restore
If you have discovered rogue tasks and processes running on your Windows computer and you want to restore your device back to its previous state, System Restore might be a helpful feature in this case. If you do not know how to load this function, take a look below
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of Hydra. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Hydra from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts..HYDRA files are a sign that Hydra ransomware has occupied your computer system and now is waiting for ransom payments. Rather than paying the cybercriminals and risking to get scammed, you should try some other data recovery alternatives like the ones that we have provided below.
If your files are encrypted by Hydra, you can use several methods to restore them:
Data Recovery Pro software might be useful for file restoring
Using this tool can help you to recover at least some of your files. What you have to do is complete each step as required to reach the best results possible. However, there is no 100% guarantee that this piece of software will be successful as it was primarily developed for recovering deleted files
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Hydra ransomware;
- Restore them.
Use Windows Previous Versions feature for data recovery purposes
If the ransomware virus has encrypted your files, folders, and documents, this product might allow you to recover at least some of them. However, this piece of software might not operate correctly if you have not booted your computer in System Restore before the cyber attack emerged
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer is also a data restoring product
You should try using this software if you got your files encrypted by the ransomware virus. Just make sure that the cyber threat has not deleted Shadow Volume Copies of encrypted files, otherwise, the program might not operate properly
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
The original .HYDRA files decrypter is still in the development mode
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Hydra and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ Margaret Rouse. RSA algorithm (Rivest-Shamir-Adleman). Search Security. Tech Target.
- ^ Ransomware. Malwarebytes. Technology information.
- ^ NoVirus. NoVirus. Security and spyware news.
- ^ What does a ‘cracked PC game’ mean?. Quora.com. Relevant questions and answers.







