I-Record adware (Free Instructions)
I-Record adware Removal Guide
What is I-Record adware?
I-Record is a video recorder that shows intrusive ads while browsing the web
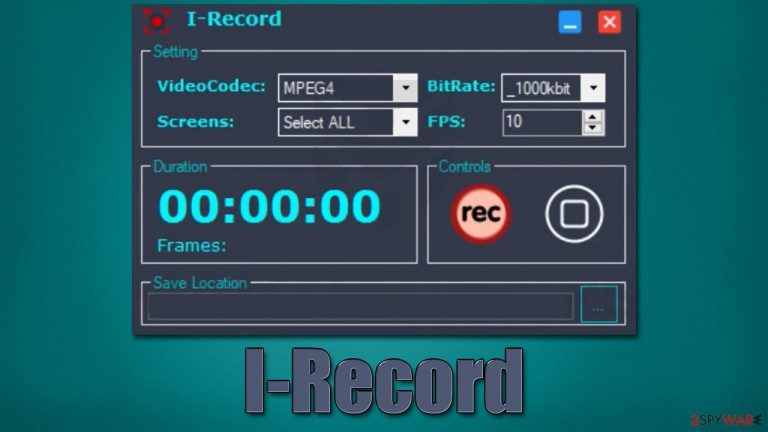
I-Record adware may seem like your regular application designed for screen capture in various formats. The recording software is relatively common, and many users employ it to capture tutorials, video game footage, and other content. However, not all applications of this kind are harmless, so it's very important not to install a recorder that could compromise Windows security and increase the risks of other infections.
Besides allowing users to record their screens, I-Record also delivers pop-ups, in-text links, banners, and other types of intrusive advertisements and increases the chances of encountering phishing material while browsing the web. Likewise, the app is also distributed using suspicious methods – it can be downloaded from pirated software distributors or via misleading advertisements on various malicious sites. These two traits are the main reason I-Record is considered adware you should get rid of as soon as possible.
| Name | I-Record adware |
|---|---|
| Type | Adware, potentially unwanted program |
| Platform | Windows |
| Distribution | Software bundles, third-party websites, deceptive ads, fake Flash Player updates |
| Symptoms | Installed unknown browser extension or application; intrusive deals, coupons, discounts, offers, and other advertisements; redirects to ad-filled, scam, phishing, and other dangerous websites |
| Dangers | Redirects to malicious websites can result in unwanted site notifications, personal information disclosure to unknown parties (cybercriminals), monetary losses, installation of other potentially unwanted programs/malware |
| Elimination | To remove unwanted apps manually, you can follow our removal guide below. For an automatic solution, scan the system with the SpyHunter 5Combo Cleaner security app |
| other steps | Malware or adware infections can diminish the performance of your computer or cause serious stability issues. Use FortectIntego to remediate your device and ensure that the virus damage is fixed |
Adware distribution: how to avoid infections
As mentioned, I-Record adware is spread using suspicious distribution methods, although users may also install it themselves when looking for an app to record their screens.
It is vital to do some research before installing applications of questionable origins – user reviews and forum posts can be a great help when deciding whether or not the app is trustworthy. Also, avoiding dubious distribution channels such as those that spread software cracks is mandatory – malware infection can be imminent when downloading dangerous installers.
When dealing with third-party software distribution websites that are not inherently malicious, always assume that installers would offer you additional software at some point. Therefore, choose Advanced or Custom settings instead of Recommended/Quick ones and check every step of the installation carefully – remove marks from pre-ticked checkboxes, read the fine print, and do not accidentally click the “Accept offer” or similar button, etc.
Alternatively, people might install the app after being misled by a fake advertisement, e.g., a fake Flash Player installer. The misleading software installation prompts that claim something is outdated or missing are always bad news, so please stay away from those. Flash Player, for example, is no longer supported by its developer and has been discontinued. In general, when it comes to software updates, always visit official websites and download updates from there.
Infection symptoms
While initially, it may seem that I-Record is just a simple screen recorder that allows choosing video format, framerate, and other parameters, it is much more than that. Those affected would start immediately noticing that their browsers would lead them to dubious websites and show more ads on websites that they visit.
Additional symptoms include multiple files of the software dropped into the Program Files and AppData folders and an “I-Record app :copyright: 2022” and “I-Record tech Copyright :copyright: All rights reserved” process running in the background. Note that the installer and the app are detected by numerous security vendors under names such as “Trojan/Win.Generic.R442534,” “Spyware.FFDroider,” “Trojan-Banker.Win32.Passteal.ph,” “Trojan:Win32/Floxif.AV!MTB,” and others.[1]
I-Record adware removal explained
Whenever adware is installed on the system level instead of the browser, its capabilities are drastically enhanced. For example, the virus may start making background connections to remote servers, generating advertising revenue in the process. This could start affecting internet speed and even compromise users' privacy.
While it may not be immediately evident that I-Record adware is causing intrusive ads and redirects, it is vital to find the culprit and eliminate it at once. If you aren't quite sure how to perform manual elimination, we recommend instead relying on automatic solutions and scanning the system with SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable security software.
1. Get rid of the main application
To uninstall applications from a Windows system, you have to access Control Panel and then reach the Programs and Features section as follows:
Windows 10/8
- Enter Control Panel into the Windows search box and hit Enter or click on the search result.
- Under Programs, select Uninstall a program.

- From the list, find the entry of the suspicious program.
- Right-click on the application and select Uninstall.
- If User Account Control shows up, click Yes.
- Wait till uninstallation process is complete and click OK.

Windows 7/XP
- Click on Windows Start > Control Panel located on the right pane (if you are Windows XP user, click on Add/Remove Programs).
- In Control Panel, select Programs > Uninstall a program.

- Pick the unwanted application by clicking on it once.
- At the top, click Uninstall/Change.
- In the confirmation prompt, pick Yes.
- Click OK once the removal process is finished.
2. Clean your browsers
Once the main application is deleted, you should also make sure that browser caches[2] are cleared. Adware is known to rack user data with the help of cookies[3] and similar technologies, which are stored locally. Even after the elimination of the unwanted application, these components may remain and continue their activities. Therefore, ensure you either use the FortectIntego maintenance utility or follow the manual steps to thoroughly remove browser caches.
Google Chrome
- Click on Menu and pick Settings.
- Under Privacy and security, select Clear browsing data.
- Select Browsing history, Cookies and other site data, as well as Cached images and files.
- Click Clear data.

Mozilla Firefox
- Click Menu and pick Options.
- Go to Privacy & Security section.
- Scroll down to locate Cookies and Site Data.
- Click on Clear Data…
- Select Cookies and Site Data, as well as Cached Web Content, and press Clear.

MS Edge (Chromium)
- Click on Menu and go to Settings.
- Select Privacy and services.
- Under Clear browsing data, pick Choose what to clear.
- Under Time range, pick All time.
- Select Clear now.

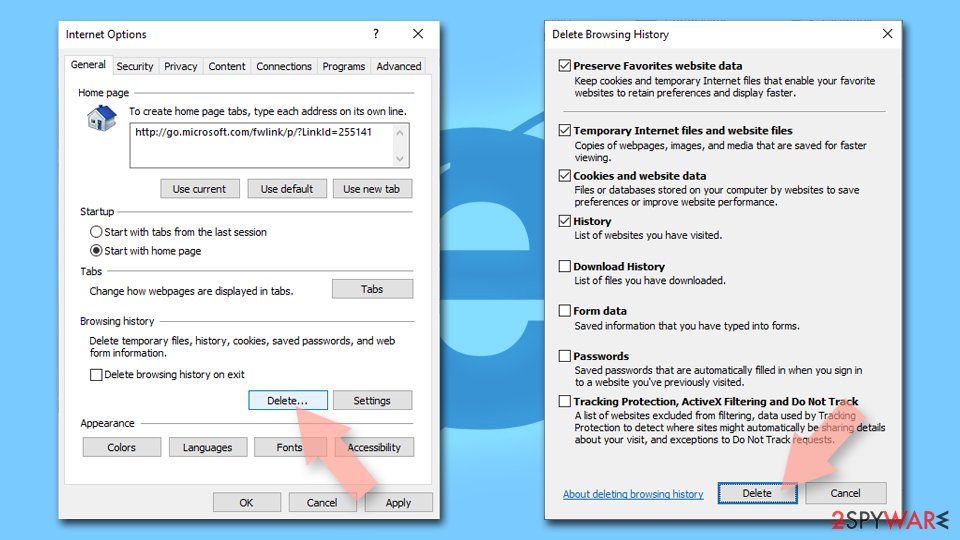
Internet Explorer
- Press on the Gear icon and select Internet Options.
- Under Browsing history, click Delete…
- Select relevant fields and press Delete.
How to prevent from getting adware
Do not let government spy on you
The government has many issues in regards to tracking users' data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Backup files for the later use, in case of the malware attack
Computer users can suffer from data losses due to cyber infections or their own faulty doings. Ransomware can encrypt and hold files hostage, while unforeseen power cuts might cause a loss of important documents. If you have proper up-to-date backups, you can easily recover after such an incident and get back to work. It is also equally important to update backups on a regular basis so that the newest information remains intact – you can set this process to be performed automatically.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware strikes out of nowhere. Use Data Recovery Pro for the data restoration process.
- ^ e4b23ebeb82594979325357ce20f14f70143d98ff49a9d5a2e6258fbfb33e555. Virus Total. File and URL analysis.
- ^ Browser cache. PCMag. The Latest Technology Product Reviews, News, Tips.
- ^ Cookies and Web Beacons. NTT. NTT Communications.
