ICursor adware (spam) - Free Instructions
iCursor adware Removal Guide
What is iCursor adware?
iCursor is a bogus browser extension that causes ads, banners, and even redirects
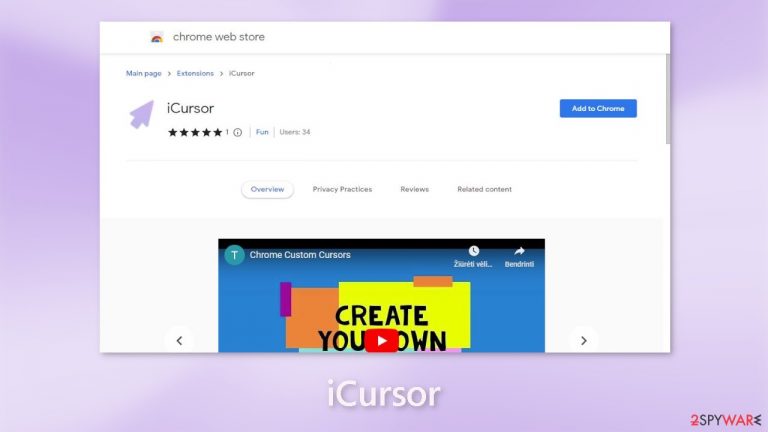
iCursor is a fraudulent browser extension that functions as adware.[1] It increases the amount of commercial content, such as pop-ups, banners, and redirects. It is marketed as a browser extension that allows users to customize their cursor in the browser, but it has no useful functions. Even when the browser is closed, pop-ups may appear.
The primary goal of such apps is to generate revenue through pay-per-click advertising. They may also use rogue advertising networks[2] to place advertisements that lead to dangerous websites. People who click on links embedded in advertisements may end up on scam pages that attempt to obtain personal information, trick them into downloading PUPs (potentially unwanted programs), and even malware.
Users typically begin seeing advertisements for bogus antivirus software, software deals, adult websites, surveys, giveaways, and dubious dating platforms. If anyone else is using the affected machine, especially children, this intruder must be removed as soon as possible.
| NAME | iCursor |
| TYPE | Browser hijacker; adware |
| SYMPTOMS | The extension starts generating intrusive advertisements and may change the main settings |
| DISTRIBUTION | Shady websites; deceptive ads, freeware installations |
| DANGERS | The ads may lead to dangerous websites controlled by crooks who try to take advantage of less IT-savvy users |
| ELIMINATION | Remove the extension through browser settings |
| FURTHER STEPS | Use FortectIntego to clear your browsers and fix any remaining damage |
Distribution methods
Fake “Downloader” pages frequently take advantage of social engineering.[3] You may receive messages requesting that you install a browser extension in order to “continue to the website” or for security purposes. However, to access content on a legitimate website, you should never have to install any plugins or programs.
When installing extensions, we recommend only using official web stores and developer websites. Apps that are listed on digital marketplaces must go through a rigorous review process. However, since this fake browser extension is listed on the Chrome web store, you should always conduct research and read the reviews, ratings, and number of users. Choose apps that have plenty of positive feedback and downloads.
Freeware installations
Adware is also frequently distributed via freeware distribution platforms. They covertly include extra programs in the installers. Most people skip the installation process, so they are unaware of the additional files. We understand that purchasing software licenses can be costly, but you may save money in the long run by keeping your system running smoothly.
You should also always select the “Custom” or “Advanced” installation methods, as well as read the Privacy Policy and Terms of Use to learn how your data will be used. The most important step is to go through the file list and untick any unrelated applications.
Remove iCursor adware
iCursor adware is most likely attached as an extension to your browser that causes push notification spam, banners, surveys, redirects, and other commercial content. You should go to your browser settings and look at the extension list. We recommend removing plugins one by one to see if you notice any changes.
How to prevent from getting adware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ Adware. Wikipedia, the free encyclopedia.
- ^ Zeljka Zorz. How does a rogue ad network function?. Helpnetsecurity. Cybersecurity News and Analysis.
- ^ What is Social Engineering?. Webroot. Security for business.










