ISpy Keylogger (Virus Removal Instructions)
iSpy Keylogger Removal Guide
What is iSpy Keylogger?
What is iSpy Keylogger virus and what can it do?
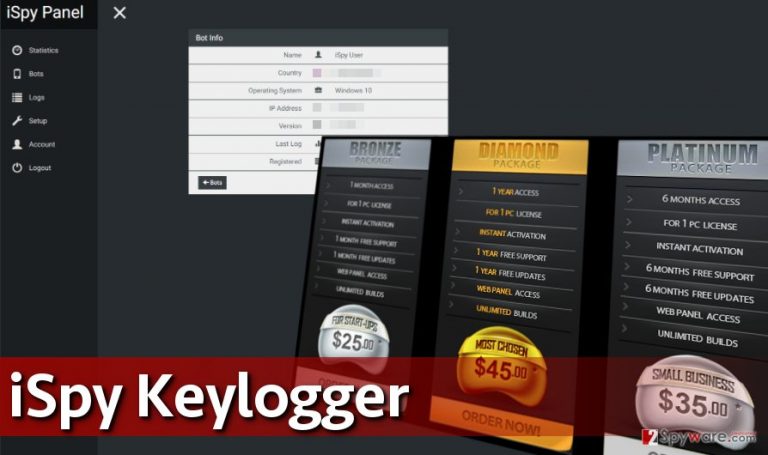
iSpy Keylogger virus is a malicious tracking software that can record keyboard strokes without computer user’s permission. This illegal software is being sold on the dark web, and its price ranges from 25 to 45 USD. After successful infiltration, this keylogger gathers information about the victimized computer and sends such information to the Command & Control server. This keylogger is powerful, because it does not only record everything the victim types on a keyboard, but also screenshots, takes pictures using victim’s computer camera, records Skype conversation, swipes legal software license keys, and steals auto-saved passwords stored in victim’s web browsers, and other valuable information. On top of that, it can install additional malware, block access to legitimate websites, display scam alerts, disable Task Manager, Registry Editor and Command Prompt (CMD).
In order to function without interruptions, it obfuscates itself and also disables anti-virus programs to avoid detection. All information that this malicious software gathers is encrypted and transferred to remote Command & Control (C&C) servers via FTP, HTTP Or SMTP protocols. Reportedly, cyber criminals use collected data to initiate identity theft, rob victim’s bank account, blackmail the victim and sell collected license keys in the dark market. The only way to protect your PC from such malicious malware is to install a proper security software, for example, FortectIntego or SpyHunter 5Combo Cleaner, and install important updates on time. To remove iSpy Keylogger, use one of these or another malware removal software, but do not try to eliminate this parasite manually. Follow iSpy Keylogger removal guidelines we present below, otherwise, you might fail to launch the anti-malware tool (the virus blocks it!).
How does this Trojan horse infect victim’s PC?
iSpy Keylogger payload is delivered to victims the same way ransomware viruses are delivered. It is mainly distributed via malicious emails, which contain infectious JavaScript or Word document that downloads the malware as soon as the victim opens it. The malware typically arrives in the form of a compressed file, which is written in .NET, Visual Basic 6.0, or AutoIt. The packer utilizes an XOR-based method to decode the malicious payload; besides, it is filled with a bogus code that is used to mislead malware analysts.
If you have received a new email that is sent by a person or organization that you do not know nor have any business with, do not open it. Typically, scammers use email addresses that look official and send messages that contain eye-catching subjects. If you ever get an email stating that you have to pay 500$ for some reputable organization because you are in debt, do not believe it before checking the facts. Do not open email attachments before actually contacting the company (do not call the number that is provided in the email message – better look it up online). Remember that criminals manage to conceal malicious files in the form of .DOC, PDF, .ZIP or .JS files, which do not look suspicious at all.
How to remove iSpy Keylogger?
iSpy Keylogger virus is hard to remove. It is a sophisticated virus, and it knows how to avoid detection. Please do not try to delete it manually – rely on software created by malware researchers who know what they are doing. To remove iSpy Keylogger malware, use FortectIntego or SpyHunter 5Combo Cleaner software, but in order to download and launch it, you need to enter Safe Mode with Networking first. To do that, follow these iSpy Keylogger removal directions:
Getting rid of iSpy Keylogger. Follow these steps
Manual removal using Safe Mode
You might want to have these instructions printed before you do this, or just open this web page via your phone so that you can look at them. Reboot your computer using instructions provided below, and then install/launch anti-malware program.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from iSpy Keylogger and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting keyloggers
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
