LambdaLocker ransomware / virus (Removal Instructions) - Aug 2017 update
LambdaLocker virus Removal Guide
What is LambdaLocker ransomware virus?
LambdaLocker virus is finally defeated – decrypt your files now
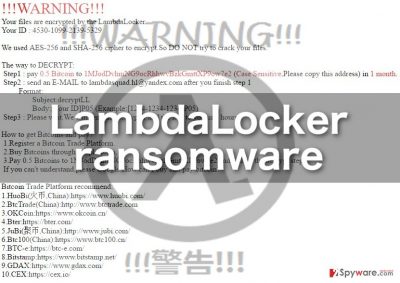
LambdaLocker is a virus written in Python that functions as a file-encrypting tool. Cybercriminals use to extort computer users. The latest version presents the ransom demand in UNLOCK_guiDE.tXT file. Interestingly, the author of this malware seems to be a fan of American band rock band as it appends .MyChemicalRomance4EVER file extension and presents atlantis.cf@yandex.com email address for the contact purposes.
The malware authors are quite greedy as they demand 6000 and 700 yuan ($1040) in exchange of the data.
The first versions of Lambda Locker have been detected on January 2017, but after half a year, the developers attempt to revive the threat again. Speaking of the original version, it functions as an ordinary crypto-malware targeting Windows OS[1] and employing AES-256 encryption method to block the most valuable cyber possessions – personal data. In particular, such viruses infiltrate computers by stealth and encrypt files with asymmetrical AES and RSA algorithms [2].
This variation specifically targeted Chinese-speaking countries[3]. In the ransom note, READ_IT.hTmL, the perpetrators demand 0.5 bitcoins which at the amount amounts to $1352.40. This version marks the files with .lambda_l0cked file extension. The virus suggests writing to lambdasquad.hl@yandex.com after paying the ransom.
The data decryption key is stored on a remote server, where the victims would not be able to reach it and use it to decrypt their files. Then comes the time for the LambdaLock creators to offer their solution to the problem. The victim is offered to redeem the files by transferring some Bitcoins to an indicated Bitcoin wallet address [4]. Frankly, the victims are proposed to pay for what is already theirs. That’s what earns this parasite a name of a ransomware virus.
If you are ever in a situation where you are being coaxed into collaborating with anonymous hackers, or more importantly, sending them money for questionable tools, do not lose your cool and remove LambdaLocker from your computer. FortectIntego or Malwarebytes will be of assistance in this process. 
Of course, you should keep in mind that this will not help recover the files but merely delete the virus and its components from the computer. Nevertheless, when the virus is fully eliminated from the computer, you can then employ alternative data recovery techniques to restore some of your important files without a risk of losing your money.
Frankly, the victims are proposed to pay for what is already theirs. That’s what earns this parasite a name of a ransomware virus. If you are ever in a situation where you are being coaxed into collaborating with anonymous hackers, or more importantly, sending them money for questionable tools, do not lose your cool and remove LambdaLocker from your computer.
Of course, you should keep in mind that this will not help recover the files but merely delete the virus and its components from the computer. Nevertheless, when the virus is fully eliminated from the computer, you can then employ alternative data recovery techniques to restore some of your important files without a risk of losing your money.
Like most viruses of the kind, Lambda Locker crypto-ransomware has specific features that make it unique and help us to differentiate it from other ransomware. For instance, from the .lambda_l0cked extension that it appends to the infected files you can already tell what kind of virus has infected your computer and start taking certain steps towards its removal.
Besides, you will also notice the READ_IT.hTmL file that will be added to your desktop and every other computer folder that contains encrypted documents. This file is a ransom note which will try to convince users to pay the 0.5 Bitcoin ransom for the data decryption. It is interesting that the note is written in English and Chinese, so we can presume that the ransomware is specifically targeted toward English and Chinese-speaking countries.
Nevertheless, that does not limit the parasite from spreading to other parts of the world. So, no matter where you live, you might one day find that your pictures, audio/video files, Office documents, and archives have been encrypted and that you are in need of a good LambdaLocker removal advice. In such a case, we suggest continue reading the article and learn more about the virus extermination techniques.
Good news: Victims of Lambda Locker ransomware can now recover their files for free. Avast has created an efficient data decryption tool that works on files with .MyChemicalRomance4EVER file extensions. Please follow the instructions we provided (you can find them below the virus removal guide) and restore your files without paying a cent.
New ransomware versions spotted
.MyChemicalRomance4EVER file extension virus seems to be programmed in Python programming language. The ransom message is fully provided in Chinese. In comparison with the original version, the developers are quite greedy they demand 6000 ($885) yuan in exchange for the files. In case a victim fails to transfer the files within the specified amount of time, the amount will increase up to 1000 dollars.
In case affected users encounter any difficulties, they should contact the perpetrators via atlantis.cf@yandex.com. They also provide instructions how to purchase bitcoins. Luckily, there is no need to comply with the demands as the malware is decryptable.[5]
The virtual threat is detected as W32/Trojan.QNSF-9385 or Generic.Ransom.LambdaLocker.7965CD21 (B). It might disguise under VortexVPN.vir.DNvir file. Be vigilant while you are downloading new applications. Do not install programs which are released by “unknown” publishers.
Distribution tricks that help the virus proliferate
We have already mentioned that LambdaLocker is a typical ransomware example and what we mean that it all respects, including its distribution as well. This means that the virus may spread via exploit kits, fake software updates or bundled inside software packages.
Besides, the virus may also be delivered to your email inbox by the malicious spam campaigns [6]. That is why we suggest being careful with the emails you open and the attachments you download to your computer. You never know whether Lambda Locker is not hidden under some legitimate-looking flight confirmation, speeding ticket or even a simple picture [7].
Remove LambdaLocker like a professional
When talking about LambdaLocker removal, we should point out that it is not an easy task. Ransomware viruses are usually designed to fight back and try to stay on the infected computers by all means possible. Thus, even automatic malware elimination tools might sometimes find it complicated to tackle the viruses properly, not to mention manual removal.
One of the major obstacles that anti-ransomware programs face is the blocking of the system scan. When the antivirus cannot scan the system, it cannot locate files of the parasite. Thus, it cannot remove LambdaLocker virus from the computer. Below you will find guidelines that explain how this problem can be overcome. Reboot the system into Safe Mode to get rid of the infection.
Getting rid of LambdaLocker virus. Follow these steps
Manual removal using Safe Mode
In case Lambda Locker blocks your antivirus, follow the instructions provided below.
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove LambdaLocker using System Restore
LambdaLocker can be decontaminated manually using the instructions provided below. You should not forget to scan your computer with a reputable antivirus software after you complete the indicated steps.
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of LambdaLocker. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove LambdaLocker from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.Currently, there is no way to decrypt LambdaLocker encrypted files for free. And the experts might take some time to come up with a free decryption tool as well. Thus, if you are looking for a quick solution, we suggest looking at the alternative data recovery techniques below.
If your files are encrypted by LambdaLocker, you can use several methods to restore them:
Try out Windows Previous Versions feature:
Windows Previous Versions feature may help you recover files. There is one condition, though. For this method to work, the System Restore function has to be enabled on the computer. If it hasn't been activated before the virus attack, the Windows Previous Versions feature method will probably be of little use.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Recover your files with the help of ShadowExplorer
ShadowExplorer is the final option we can suggest for the data recovery. Nevertheless, if the virus deletes Volume Shadow Copies of the encrypted files, the recovery will most likely be unsuccessful. However, you can always give it a try. Here is what you do:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
LambdaLocker Decrypter
Though some of virus versions do not seem to have decrypters yet, you can decrypt files affected by .MyChemicalRomance4EVER malware variation. Before you do, check the above guide how to eliminate the infection.
You can download LambdaLocker fix from here. Follow the instructions provided by the tool to decrypt your files.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from LambdaLocker and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ A short history and evolution of ransomware. KnowBe4 website.
- ^ Michael Higashi. Symmetric vs. Asymmetric Encryption – Which is Best?. CipherCloud. Security blog.
- ^ How to remove computer threats. Wubingdu. Cyber security and spyware news in Chinese.
- ^ Danny Palmer. How Bitcoin helped fuel an explosion in ransomware attacks. ZDNet. Technology news.
- ^ Jakub Kroustek. New version of LambdaLocker Python ransomware. Twitter. Online source for news and communication.
- ^ Nikoletta Szabo. How does a malware/spam campaign work?. Bitninja security blog.
- ^ Maria Korolov . 93% of phishing emails are now ransomware. SCO IT news site.





















